Device certificate in nFactor as an EPA component
Important:
Endpoint Analysis is intended to analyze the user device against pre-determined compliance criteria and does not enforce or validate the security of end-user devices. It is recommended to use endpoint security systems to protect devices from local admin attacks.
Device Certificate can be configured in nFactor as an EPA component. Device certificate can appear as any factor as a part of EPA.
Following are the benefits of configuring Device Certificate in nFactor as an EPA component.
-
The failure in device certificate validation does not result in a logon failure. Based on the configuration, the logon can proceed and the user can be placed under groups with limited access.
-
Because the Device Certificate check is policy driven, you can selectively allow or block access of your corporate intranet resources based on Device Certificate authentication. For example, Device Certificate authentication can be used to provide conditional access to the Office 365 application only on the corporate managed laptops.
Device certificate validation cannot be a part of a periodic EPA scan.
Important:
- By default, Windows mandates admin privileges for accessing device certificates. To add the device certificate check for non-admin users, you must install the VPN plug-in of the same version as the EPA plug-in on the device.
- You can add multiple CA certificates to the gateway and validate the device certificate.
- If you install two or more device certificates on the client machines, users must select the correct certificate while logging on to NetScaler Gateway or before the endpoint analysis scan runs.
- When you create the device certificate, it must be an X.509 certificate.
- If you have a device certificate issued by an intermediate CA, then both intermediate and root CA certificates must be bound.
- You must also bind the CA Certificate to the VPN virtual server.
Configure the device certificate in nFactor as an EPA component
To configure the Device Certificate in nFactor as an EPA component by using the CLI:
At the command prompt, type;
add authentication epaAction epa-act -csecexpr sys.client_expr("device-cert_0_0") -defaultgroup epa_pass -quarantine_group epa_fail
<!--NeedCopy-->
To configure device certificate in nFactor as an EPA component for the VPN virtual server by using the GUI:
- In the NetScaler GUI, navigate to Configuration > NetScaler Gateway > Virtual Servers.
- On the NetScaler Gateway Virtual Servers page, select the Virtual server to be modified and click Edit.
-
On the VPN Virtual Server page, click the Edit icon.
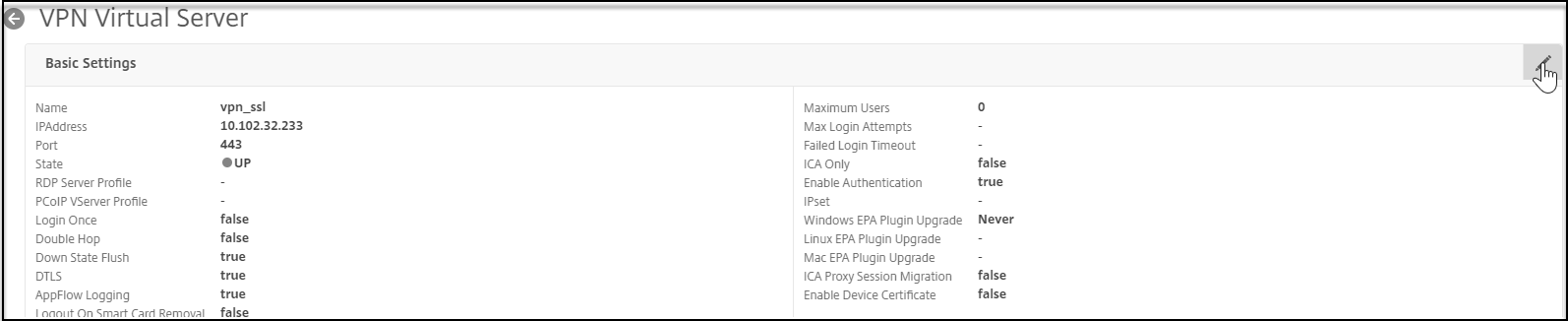
-
Click More.
-
Click + in the CA for Device Certificate section and click OK.
Note:
Do not select the Enable Device Certificate check box. Enabling it enables the Device Certificate validation in the classic EPA.
-
In the NetScaler GUI, navigate to Configuration > Security >AAA – Application Traffic > Policies > Authentication > Advanced Policies > Actions > EPA.
-
On the Authentication EPA Action page, click Add. You can click Edit to edit an existing EPA action.
-
On the Create Authentication EPA Action page, provide the values for the required fields to create an authentication EPA action, and click the EPA Editor link.
-
Select Common from the Expression Editor menu.
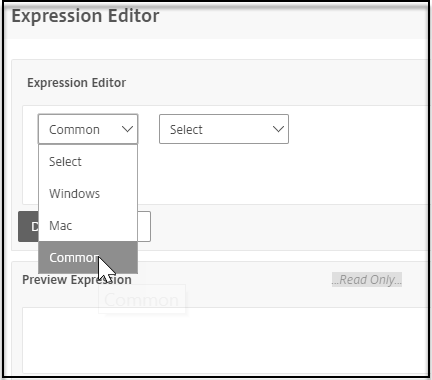
-
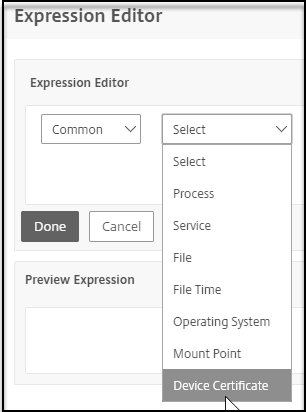
Select Device Certificate from the subsequent menu that appears and click Done to complete the configuration.
To configure Device Certificate in nFactor as an EPA component for the authentication virtual server by using the GUI:
-
In the NetScaler GUI, navigate to Security > AAA-Application Traffic > Virtual Servers.
-
On the NetScaler Gateway Virtual Servers page, select the Virtual server to be modified and click Edit.
- On the Authentication Virtual Server page, click the Edit icon.
-
Click More.
-
Click Add next to the CA for Device Certificate section.
-
Select the certificate to be added and click OK to complete the configuration.
- Repeat step 6 to step 10 to complete the configuration.