nFactor for gateway authentication
nFactor authentication enables a whole new set of possibilities regarding authentication. Administrators using nFactor enjoy authentication, authorization, and auditing flexibility when configuring authentication factors for virtual servers.
Two policy banks or two factors no longer restrict an administrator. The number of policy banks can be extended to suit different needs. Based on previous factors, nFactor determines a method of authentication. Dynamic login forms and on-failure actions are possible by using nFactor.
Important
- Starting from release 13.0 build 67.x, nFactor authentication is supported with Standard license only for Gateway/VPN virtual server, and not for the authentication virtual server. In Standard license, the nFactor visualizer GUI cannot be used to create the EPA in the nFactor flow. Also, you cannot edit the login schema, but must use the out-of-the-box login schema as-is.
- For NetScaler to support nFactor authentication, an Advanced license or a Premium license is required. For more information about nFactor authentication with NetScaler, see nFactor authentication.
Authentication, authorization, and auditing feature licensing requirements
The following table lists the licensing requirements for the available authentication, authorization, and auditing features.
| Standard License | Advanced License | Premium License | ||
|---|---|---|---|---|
| LOCAL authentication | Yes | Yes | Yes | |
| LDAP authentication | Yes | Yes | Yes | |
| RADIUS authentication | Yes | Yes | Yes | |
| TACACS authentication | Yes | Yes | Yes | |
| Web authentication | Yes | Yes | Yes | |
| Client cert authentication | Yes | Yes | Yes | |
| Negotiate authentication | Yes | Yes | Yes | |
| SAML authentication | Yes | Yes | Yes | |
| OAuth authentication | No | Yes | Yes | |
| Native OTP | No | Yes | Yes | |
| Email OTP | No | Yes | Yes | |
| Push notification for OTP | No | No | Yes | |
| Knowledge based question and answer (KBA authentication) | No | Yes | Yes | |
| Self service password reset (SSPR) | No | Yes | Yes | |
| nFactor Visualizer | Yes | Yes | Yes | |
Note
- For steps to configure nFactor for the NetScaler Standard License, see the section Create a virtual server.
- Only a non-addressable authentication, authorization, and auditing virtual server can be bound to a Gateway/VPN virtual server in NetScaler Standard license.
- Customization of LoginSchema is not allowed in the NetScaler Standard license. The nFactor support is basic with only the default and already added login schemas that come with the appliance. The administrator can use them in their configurations, but they cannot add a login schema. Hence the GUI option is disabled.
Use cases
nFactor authentication enables dynamic authentication flows based on the user profile. Sometimes, the flows can be simple and intuitive to the user. In other cases, they can be coupled with securing Active Directory or other authentication servers. The following are some requirements specific to Gateway:
-
Dynamic user name and password selection. Traditionally, the Clients (including Browsers and Receivers) use the Active Directory (AD) password as the first password field. The second password is reserved for the One-Time-Password (OTP). However, to secure AD servers, OTP is required to be validated first. nFactor can do this without requiring client modifications.
-
Multi-Tenant Authentication End-point. Some organizations use different Gateway servers for Certificate and non-certificate users. With users using their own devices to log in, user’s access levels vary on the NetScaler appliance based on the device being used. Gateway can cater to different authentication needs.
-
Authentication based on group membership. Some organizations obtain user properties from AD servers to determine authentication requirements. Authentication requirements can be varied for individual users.
-
Authentication co-factors. Sometimes, different pairs of authentication policies are used to authenticate different sets of users. Providing pair policies increases effective authentication. Dependent policies can be made from one flow. In this manner, independent sets of policies become flows of their own that increase efficiency and reduce complexity.
Authentication response handling
The NetScaler Gateway callback registers handle authentication responses. AAAD (authentication daemon) responses and success/failure/error/dialogue codes are fed to the callback handle. The success/failure/error/dialogue codes direct Gateway to take the appropriate action.
Client support
The following table details configuration details.
| Client | nFactor Support | Authentication Policy Bind Point | EPA |
|---|---|---|---|
| Browsers | Yes | Authentication | Yes |
| Citrix Workspace app | Yes | VPN | Yes |
| Gateway Plug-in | Yes | VPN | Yes |
Note:
- Citrix Workspace app supports nFactor authentication for the supported operating systems from the following listed versions.
- Windows 4.12
- Linux 13.10
- Mac 1808
- iOS 2007
- Android 1808
- HTML5: Supported through Store Web
- Chrome: Supported through Store Web
WebView credential type support for authentication mechanisms
Note:
Blocking expressions (such as ns variable) are not supported in VPN session policies with WebView support. For more information about blocking expressions, contact Citrix Support.
NetScaler authentication supports the AUTHv3 protocol. The WebView credential type in the AUTHv3 protocol supports all types of authentication mechanisms (including SAML and OAuth). The WebView credential type is a part of AUTHv3, which is implemented by the Citrix Workspace app and browser in web applications.
The following example explains the flow of WebView events through NetScaler Gateway and the Citrix Workspace app:
- The Citrix Workspace app negotiates to NetScaler Gateway for AUTHv3 protocol support.
- NetScaler responds positively and suggests a specific start URL.
- The Citrix Workspace app then connects to the specific endpoint (URL).
- NetScaler Gateway sends a response to the client to start the WebView.
- The Citrix Workspace app starts WebView and sends an initial request to NetScaler.
- NetScaler redirects URI to browser login endpoint.
- Once authentication is complete, NetScaler sends a completion response to WebView.
- The WebView now exits and gives control back to the Citrix Workspace app to continue AUTHv3 protocol for session establishment.
Command line configuration
The Gateway virtual server needs an authentication virtual server named as an attribute. Virtual server name as an attribute is the only configuration required for this model.
add authnProfile <name-of-profile> -authnVsName <name-of-auth-vserver>
<!--NeedCopy-->
The authnVsName is the name of the authentication virtual server. The authnVsName virtual server must be configured with advanced authentication policies and is used for nFactor authentication.
add vpn vserver <name> <serviceType> <IP> <PORT> -authnProfile <name-of-profile>
set vpn vserver <name> -authnProfile <name-of-profile>
<!--NeedCopy-->
Where authnProfile is the previously created authentication profile.
Interop challenges
Most of the Legacy Gateway clients, in addition to rfWeb clients, are modeled on responses sent by Gateway. For example, a 302 response to /vpn/index.html is expected for many clients. These clients also depend on various gateway cookies such as “pwcount,” “NSC_CERT.”
Endpoint analysis (EPA)
EPA in nFactor is not supported for the NetScaler authentication, authorization, and auditing module. Hence, the NetScaler Gateway virtual server performs EPA. After EPA, the login credentials are sent to the authentication virtual server using the previously mentioned API. Once authentication is complete, Gateway continues to the postauthentication process and it establishes the user session.
Misconfiguration considerations
The Gateway client sends the user credentials only once. Gateway gets either one or two credentials from the client with the login request. In the legacy mode, there are a maximum of two factors. The passwords obtained are used for these factors. However, with nFactor the number of factors that can be configured is practically unlimited. The passwords obtained from the Gateway client are reused (as per configuration) for configured factors. Care must be taken such that the one-time-password (OTP) must not be reused multiple times. Likewise, an administrator must ensure that the password reused at a factor is indeed applicable to that factor.
Defining Clients
The configuration option is provided to help NetScaler determine browser clients versus thick clients such as Receiver.
A pattern set, ns_vpn_client_useragents, is provided for the administrator to configure patterns for all Clients.
Likewise, binding the “Citrix Receiver” string to the above patset to ignore all Clients that have “Citrix Receiver” in the User-Agent.
Important
Starting from Citrix Secure Access for Android 24.08.1, the format for the User-Agent string in the webview used for nFactor authentication is changed as follows:
CitrixSecureAccess/CitrixVPN <version> (Linux; Android 14; Build/AP31.240426.023; wv) VpnCapable AuthV3Capable NAC/1.0 [ManagedVpn] [custom-user-agent]
CitrixSecureAccess/CitrixVPNis included for backward compatibility to identify Citrix Secure Access client on NetScaler Gateway to filter policies.The
<version>string is replaced by applicable app/OS version number.The
ManagedVpnandcustom-user-agentstrings are optional. TheManagedVpnstring is included only with MDM deployed VPNs. Thecustom-user-agentstring is configured by the MDM admin in the managed VPN configurations.In the previous releases, the User-Agent string in the webview included the legacy Mozilla or WebKit compatibility information.
Restricting nFactor for Gateway
nFactor for gateway authentication does not happen if the following conditions are present.
-
The authnProfile is not set to NetScaler Gateway.
-
Advanced authentication policies are not bound to the authentication virtual server and the same authentication virtual server is mentioned in
authnProfile. -
The User-Agent string in the HTTP request matches the User-Agents configured in
patsetns_vpn_client_useragents.
If these conditions are not met, the classic authentication policy bound to Gateway is used.
If a User-Agent, or portion of it is bound to the previously mentioned patset, requests coming from those user-agents do not participate in the nFactor flow. For example, the following command restricts configuration for all browsers (assuming all browsers contain “Mozilla” in the user-agent string):
bind patset ns_vpn_client_useragents Mozilla
<!--NeedCopy-->
LoginSchema
LoginSchema is a logical representation of the logon form. The XML language defines it. The Syntax of the loginSchema conforms to Citrix’s Common Forms Protocol specification.
LoginSchema defines the “view” of the product. An Administrator can provide a customized description, assistive text, and so forth of the form. The login schema includes the labels of the form itself. A customer can provide the success or failure message that describes the form presented at a given point.
Use the following command to configure a login schema.
add authentication loginSchema <name> -authenticationSchema <string> [-userExpression <string>] [-passwdExpression <string>] [-userCredentialIndex <positive_integer>]
[-passwordCredentialIndex <positive_integer>] [-authenticationStrength <positive_integer>] [-SSOCredentials ( YES | NO )]
<!--NeedCopy-->
Parameter description
-
name - Name for the new login schema. This is a mandatory argument. Maximum Length: 127
-
authenticationSchema - Name of the file for reading the authentication schema to be sent for Login Page UI. This file contains the xml definition of the elements as per the Citrix Forms Authentication Protocol to be able to render the login form. If the administrator does not want to prompt users for other credentials but continue with previously obtained credentials, then
noschemacan be given as an argument. This applies only to loginSchemas that are used with the user-defined factors, and not the virtual server factor.
This is a mandatory argument. Maximum Length: 255
-
userExpression - Expression for user name extraction during login. This can be any relevant advanced policy expression. Maximum Length: 127
-
passwdExpression - Expression for password extraction during login. This can be any relevant advanced policy expression. Maximum Length: 127
-
userCredentialIndex - The index at which the user entered user name must be stored in session. Minimum value: 1, Maximum value: 16
-
passwordCredentialIndex - The index at which the user entered the password must be stored in the session. Minimum value: 1, Maximum value: 16
-
authenticationStrength - Weight of the current authentication Minimum value: 0, Maximum value: 65535
-
SSOCredentials- This option indicates whether current factor credentials are the default SSO (SingleSignOn) credentials. Possible values: YES, NO. Default value: NO
LoginSchema and nFactor knowledge required
Pre-built loginSchema files are found in the following NetScaler location /nsconfig/loginschema/LoginSchema/. These pre-built loginSchema files cater to common use cases, and can be modified for slight variations if necessary.
Also, most single factor use cases with few customizations do not need the login schema configuration.
The administrator is advised to check the documentation for other configuration options that enable NetScaler to discover the factors. Once the user submits the credentials, the administrator can configure more than one factor to flexibly choose and process the authentication factors.
Configuring dual factor authentication without using LoginSchema
NetScaler automatically determines dual factor requirements based on configuration. Once the user presents these credentials, the administrator can configure the first set of policies at the virtual server. Against each policy there can be a “nextFactor” configured as a “passthrough.” A “passthrough” implies that the NetScaler must process the logon using the existing credential set without going to the user. By using “passthrough” factors, an administrator can programmatically drive the authentication flow. Administrators are advised to read the nFactor specification or the deployment guides for further details. See Multi-Factor (nFactor) authentication.
User name and password expressions
To process the login credentials, the administrator must configure the loginSchema. Single factor or dual factor use cases with few loginSchema customizations does not need a specified XML definition. The LoginSchema has other properties such as userExpression and passwdExpression that can be used to alter the user name or password that the user presents.
Login schemas are advanced policy expressions and can be used to override the user input as well. This can be achieved by appending a string for parameters in -authenticationSchema as shown in the following example.
Following are the examples to modify user inputs for user name and for password respectively.
-
Change the user input for user name from
username@citrix.comtousername@xyz.comadd authentication loginSchema user_schema -authenticationSchema LoginSchema/DualAuth.xml -userExpression "AAA.LOGIN.USERNAME.BEFORE_STR(\"@\").APPEND(\"@xyz.com\")" <!--NeedCopy--> -
Consider a scenario where the user provides a password and a passcode in the first factor as part of the login schema configured. To use the passcode provided by the user in the first factor and the password in the second factor, you can modify the existing login schema by using the following commands.
add authentication loginSchema user_schema -authenticationSchema LoginSchema/DualAuth.xml -passwdExpression "AAA.LOGIN.PASSWORD2" <!--NeedCopy-->add authentication loginSchema user_schema_second -authenticationSchema noschema -passwdExpression "AAA.LOGIN.PASSWORD" <!--NeedCopy-->
High-level steps in nFactor configuration
The following diagram illustrates the high-level steps involved in nFactor configuration.
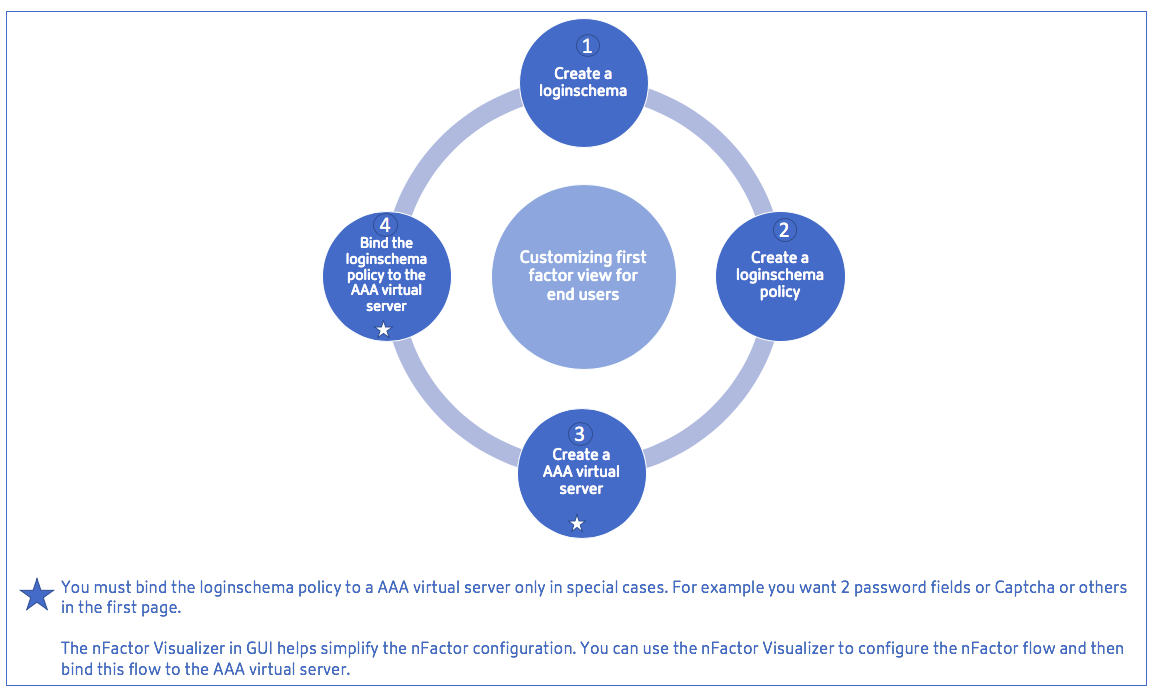
GUI Configuration
The following topics are described in this section:
-
Create a Virtual Server
-
Create Authentication Virtual Server
-
Create Authentication CERT Profile
-
Create an Authentication Policy
-
Add an LDAP authentication server
-
Add an LDAP authentication policy
-
Add a RADIUS authentication server
-
Add a RADIUS Authentication Policy
-
Create an Authentication Login Schema
-
Create a Policy Label
Create a virtual server
-
Navigate to NetScaler Gateway > Virtual Servers.
-
Click the Add button to create a gateway virtual server.
-
Enter the following information and click OK.
Parameter name Parameter description Name Name for the NetScaler Gateway virtual server. Must begin with an ASCII alphabetic or underscore (_) character, and must contain only ASCII alphanumeric, underscore, hash (#), period (.), space, colon (:), at (@), equals (=), and hyphen (-) characters. Can be changed after the virtual server is created. The following requirement applies only to the NetScaler CLI: If the name includes one or more spaces, enclose the name in double or single quotation marks (for example, “my server” or ‘my server’). IP Address Type Select the IP Address or Non-addressable option from the drop-down menu. IPAddress An Internet Protocol address (IP address) is a numerical label assigned to each device participating in the computer network that uses the Internet Protocol for communication. Port Enter the port number for the virtual server. RDP Server Profile Name of the RDP server profile associated with the virtual server. PCoIP VServer Profile Name of the PCoIP virtual server profile associated with the virtual server. Maximum Users Maximum number of concurrent user sessions allowed on this virtual server. The actual number of users allowed to log on to this virtual server depends on the total number of user licenses. Max Login Attempts Maximum number of logon attempts. Failed Login Timeout Number of minutes an account is locked if the user exceeds the maximum permissible attempts. Windows EPA Plugin Upgrade Option to set plug-in upgrade behavior for Windows clients. Linux EPA Plugin Upgrade
Option to set plug-in upgrade behavior for Linux clients.
Note:
- For eLux and IGEL OS, this parameter must always be set to Never.
- The option Essential is not supported in the Citrix Secure Access client for Linux.
Mac EPA Plugin Upgrade Option to set plug-in upgrade behavior for macOS clients. Login Once This option enables or disables seamless SSO for this virtual server. ICA Only
- When set to ON, it implies Basic mode where the user can log on using either the Citrix Workspace app or a browser and get access to the published apps configured at the Citrix Virtual Apps and Desktops environment pointed out by the
Wihomeparameter. Users are not allowed to connect using the Citrix Secure Access client and end point scans cannot be configured. The numbers of users that can log in and access the apps are not limited by the license in this mode.
- When set to OFF, it implies SmartAccess mode where the user can log on using either the Citrix Workspace app or a browser or a Citrix Secure Access client. The admin can configure end point scans to be run on the client systems and then use the results to control access to the published apps. In this mode, the client can connect to the gateway in other client modes namely VPN and clientless VPN. The numbers of users that can log in and access the resources are limited by the CCU licenses in this mode.
Enable Authentication Require authentication for users connecting to NetScaler Gateway. Double Hop Use NetScaler Gateway in a double-hop configuration. A double-hop deployment provides an extra layer of security for the internal network by using three firewalls to divide the DMZ into two stages. Such a deployment can have one appliance in the DMZ and one appliance in the secure network. Down State Flush Close existing connections when the virtual server is marked DOWN, which means the server might have timed out. Disconnecting existing connections frees resources and in certain cases speeds recovery of overloaded load balancing setups. Enable this setting on servers in which the connections can safely be closed when they are marked DOWN. Do not enable DOWN state flush on servers that must complete their transactions. DTLS This option starts or stops the turn service on the virtual server AppFlow Logging Log AppFlow records that contain standard NetFlow or IPFIX information, such as time stamps for the beginning and end of a flow, packet count, and byte count. Also log records that contain application-level information, such as HTTP web addresses, HTTP request methods and response status codes, server response time, and latency. ICA Proxy Session Migration This option determines if an existing ICA Proxy session is transferred when the user logs on from another device. State The current state of the virtual server, as UP, DOWN, BUSY, and so on. Enable Device Certificate Indicates whether the device certificate check as a part of EPA is on or off. 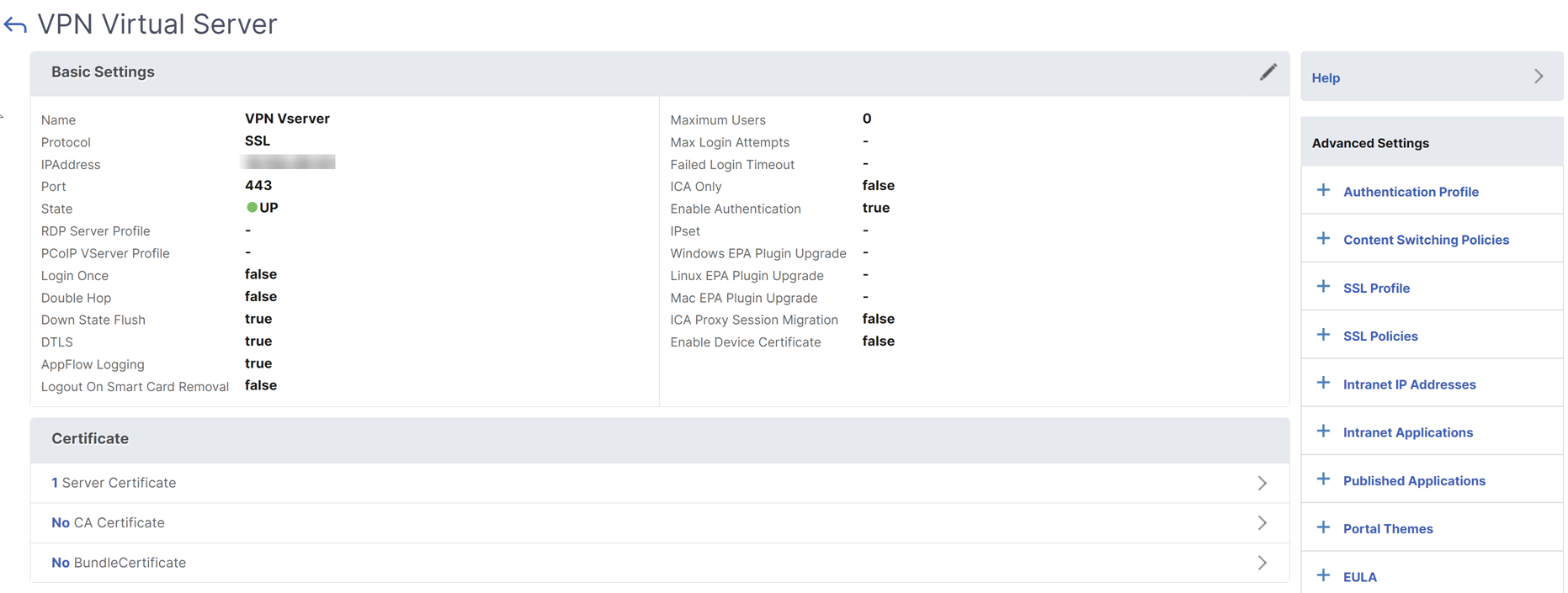
- For eLux and IGEL OS, this parameter must always be set to Never.
-
Select the No Server Certificate section of the page.
-
Click > under Select Server Certificate to select the server certificate.
-
Select the SSL Certificate and click the Select button.
-
Click Bind.
-
If you see a warning about No usable ciphers, click OK
-
Click the Continue button.
-
In the Authentication section, click the + icon in the top right.
Create an authentication virtual server
-
Navigate to Security > AAA – Application Traffic > Virtual Servers.
-
Click the Add button.
-
Complete the following Basic Settings to create the Authentication Virtual Server.
Note: The * sign to the right of the setting name indicates mandatory fields.
-
Enter the Name for the new authentication virtual server.
-
Enter the IP Address Type. The IP Address Type can be configured as Non-addressable.
-
Enter the IP Address. The IP Address can be zero.
-
Enter the Protocol type of the authentication virtual server.
-
Enter the TCP Port on which the virtual server accepts connections.
-
Enter the domain of the authentication cookie set by the authentication virtual server.
-
-
Click OK.
-
Click the No Server Certificate section.
-
Click > under Select Server Certificate.
-
Choose the desired SSL Certificate and click the Select button.
Note: The Authentication virtual server does not need a certificate bound to it.
-
Configure the Server Certificate Binding.
-
Check the Server Certificate for SNI box to bind one or more Cert keys used for SNI processing.
-
Click the Bind button.
-
Create an authentication CERT profile
-
Navigate to Security > AAA – Application Traffic > Policies > Authentication > Basic Policies > CERT.
-
Select the Profiles tab and then select Add.
-
Complete the following fields to create the Authentication CERT Profile. The * sign to the right of the setting name indicates mandatory fields.
-
Name - Name for the client cert authentication server profile (action).
-
Two factor – In this instance the two-factor authentication option is NOOP.
-
User Name Field – enter the client-cert field from which the user name is extracted. Must be set to either ““Subject”” or ““Issuer”” (include both sets of double quotation marks).
-
Group Name Field - enter the client-cert field from which the group is extracted. Must be set to either ““Subject”” or ““Issuer”” (include both sets of double quotation marks).
-
Default Authentication Group - This is the default group that is chosen when the authentication succeeds in addition to the extracted groups.
-
-
Click Create.
Create an authentication policy
Note
If you configure a first factor policy with a policy rule using AAA.login, then the following expression must be configured with OR condition for Citrix Workspace app to support the nFactor deployment.
|| HTTP.REQ.URL.CONTAINS("/cgi/authenticate")
-
Navigate to Security > AAA – Application Traffic > Policies > Authentication > Advanced Policies > Policy.
-
Select the Add button
-
Complete the following information to create an authentication policy. The * sign to the right of the setting name indicates mandatory fields.
a) Name – enter the Name for the advance AUTHENTICATION policy. Must begin with a letter, number, or the underscore character (_), and must contain only letters, numbers, and the hyphen (-), period (.) pound (#), space (), at (@), equals (=), colon (:), and underscore characters. Cannot be changed after the authentication policy is created.
The following requirement applies only to the NetScaler CLI: If the name includes one or more spaces, enclose the name in double or single quotation marks (for example, “my authentication policy” or ‘my authentication policy’).
b) Action Type - enter the type of the Authentication Action.
c) Action - enter the name of the authentication action to be performed if the policy matches.
d) Log Action - enter the name of the message log action to use when a request matches this policy.
e) Expression - enter the name of the NetScaler named rule, or a default syntax expression, that the policy uses to determine whether to attempt to authenticate the user with the AUTHENTICATION server.
f) Comments – enter any comments to preserve information about this policy.
-
Click Create
Add an LDAP authentication server
-
Navigate to Security > AAA – Application Traffic > Policies > Authentication > Basic Policies > LDAP.
-
Add an LDAP server by selecting the Server tab and selecting the Add button.
Add an LDAP authentication policy
-
Go to Security > AAA – Application Traffic > Policies > Authentication > Advanced Policies > Policy.
-
Click Add to add an Authentication Policy.
-
Complete the following information to Create an Authentication Policy. The * sign to the right of the setting name indicates mandatory fields.
a) Name - Name for the advance AUTHENTICATION policy. Must begin with a letter, number, or the underscore character (_), and must contain only letters, numbers, and the hyphen (-), period (.) pound (#), space (), at (@), equals (=), colon (:), and underscore characters. Cannot be changed after the authentication policy is created.
The following requirement applies only to the NetScaler CLI: If the name includes one or more spaces, enclose the name in double or single quotation marks (for example, “my authentication policy” or ‘my authentication policy’).
b) Action Type - Type of the Authentication Action.
c) Action - Name of the authentication action to be performed if the policy matches.
d) Log Action - Name of message log action to use when a request matches this policy.
e) Expression - Name of the NetScaler named rule, or a default syntax expression, that the policy uses to determine whether to attempt to authenticate the user with the AUTHENTICATION server.
f) Comments - Any comments to preserve information about this policy.
-
Click Create.
Add a RADIUS authentication server
-
Navigate to Security > AAA – Application Traffic > Policies Authentication > Basic Policies > RADIUS.
-
To add a Server select the Servers tab and select the Add button.
-
Enter the following to create an Authentication RADIUS Server. The * sign to the right of the setting name indicates mandatory fields.
-
Enter a Name for the RADIUS Action.
-
Enter the Server Name or Server IP Address assigned to the RADIUS server.
-
Enter the Port number on which the RADIUS server listens for connections.
-
Enter the Time-out value in seconds. The NetScaler appliance waits for a response from the RADIUS server until the configured timeout value expires.
-
Enter the Secret Key that is shared between the RADIUS server and the NetScaler appliance. The Secret Key is required to allow the NetScaler appliance to communicate with the RADIUS server.
-
Confirm the Secret Key.
-
-
Click Create.
Add a RADIUS authentication policy
-
Navigate to Security > AAA – Application Traffic > Policies > Authentication > Advanced Policies > Policy.
-
Click Add to create an Authentication Policy.
-
Complete the following information to create an authentication policy. The * sign to the right of the setting name indicates mandatory fields.
- Name - Name for the advance AUTHENTICATION policy. Must begin with a letter, number, or the underscore character (_), and must contain only letters, numbers, and the hyphen (-), period (.) pound (#), space (), at (@), equals (=), colon (:), and underscore characters. Cannot be changed after the AUTHENTICATION policy is created.
The following requirement applies only to the NetScaler CLI: If the name includes one or more spaces, enclose the name in double or single quotation marks (for example, “my authentication policy” or ‘my authentication policy’).
-
Action Type - Type of the Authentication Action.
-
Action - Name of the authentication action to be performed if the policy matches.
-
Log Action - Name of message log action to use when a request matches this policy.
-
Expression - Name of the NetScaler named rule, or a default syntax expression, that the policy uses to determine whether to attempt to authenticate the user with the AUTHENTICATION server.
-
Comments - Any comments to preserve information about this policy.
-
Click OK. The authentication policy that you created is listed in the list of policies.
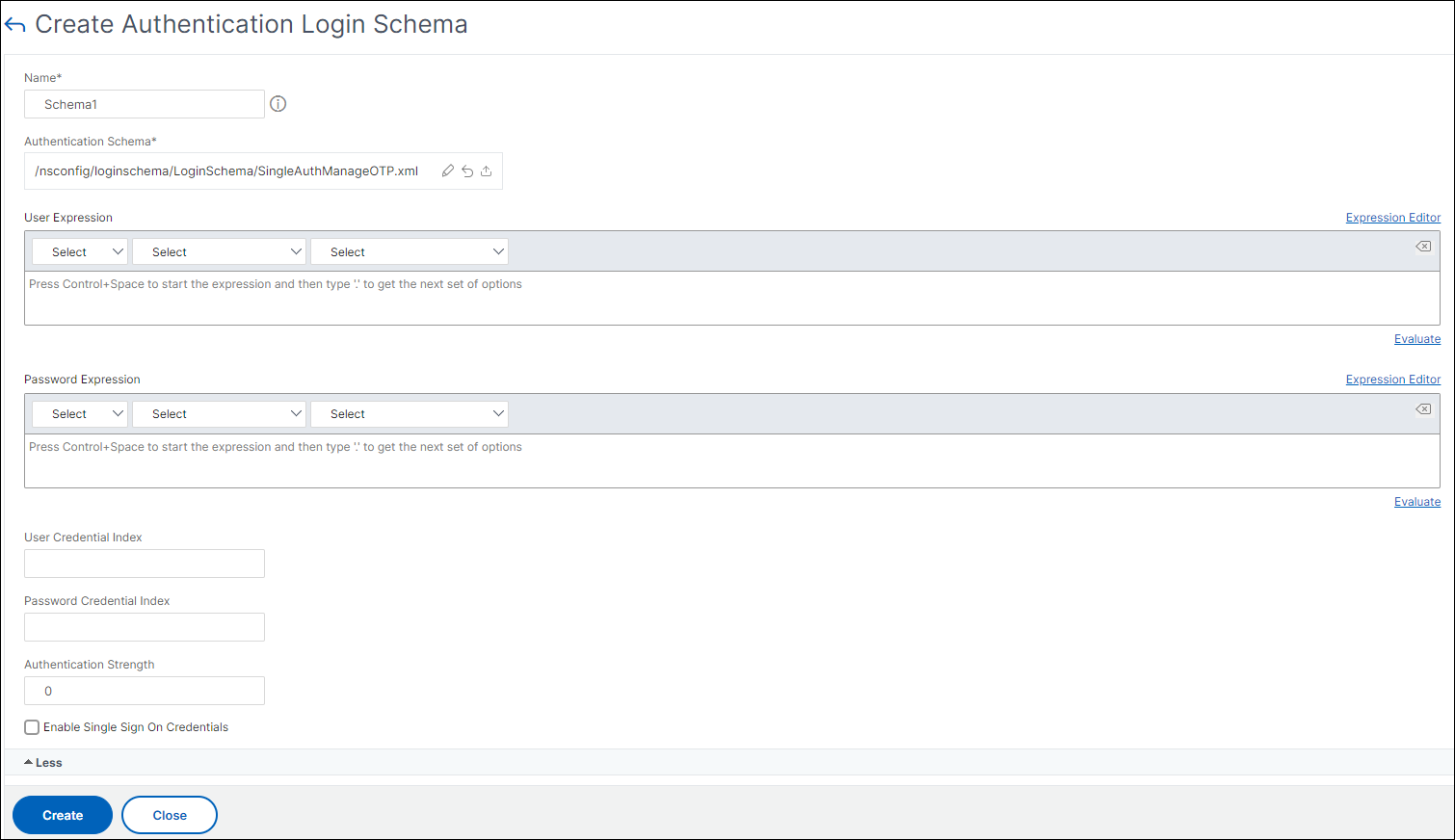
Create an Authentication Login Schema
-
Navigate to Security > AAA – Application Traffic > Login Schema.
-
Select the Profiles tab and Click the Add button.
-
Complete the following fields to create an authentication login schema:
-
Enter Name – Name for the new login schema.
-
Enter Authentication Schema - Name of the file for reading the authentication schema to be sent for Login Page UI. This file must contain the xml definition of the elements as per the Citrix Forms Authentication Protocol to be able to render a login form. If an administrator does not want to prompt users for more credentials but continue with previously obtained credentials, then “
noschema” can be given as an argument. This applies only to loginSchemas that are used with user-defined factors, and not the virtual server factor -
Enter User Expression - Expression for user name extraction during login
-
Enter Password Expression - Expression for password extraction during login
-
Enter User Credential Index - An index at which the user entered user name is stored in the session.
-
Enter Password Credential Index - An index at which the user entered password must be stored in the session.
-
Enter Authentication Strength - Weight of the current authentication.
-
-
Click Create. The login schema profile that you created must appear in the login schema profile list.
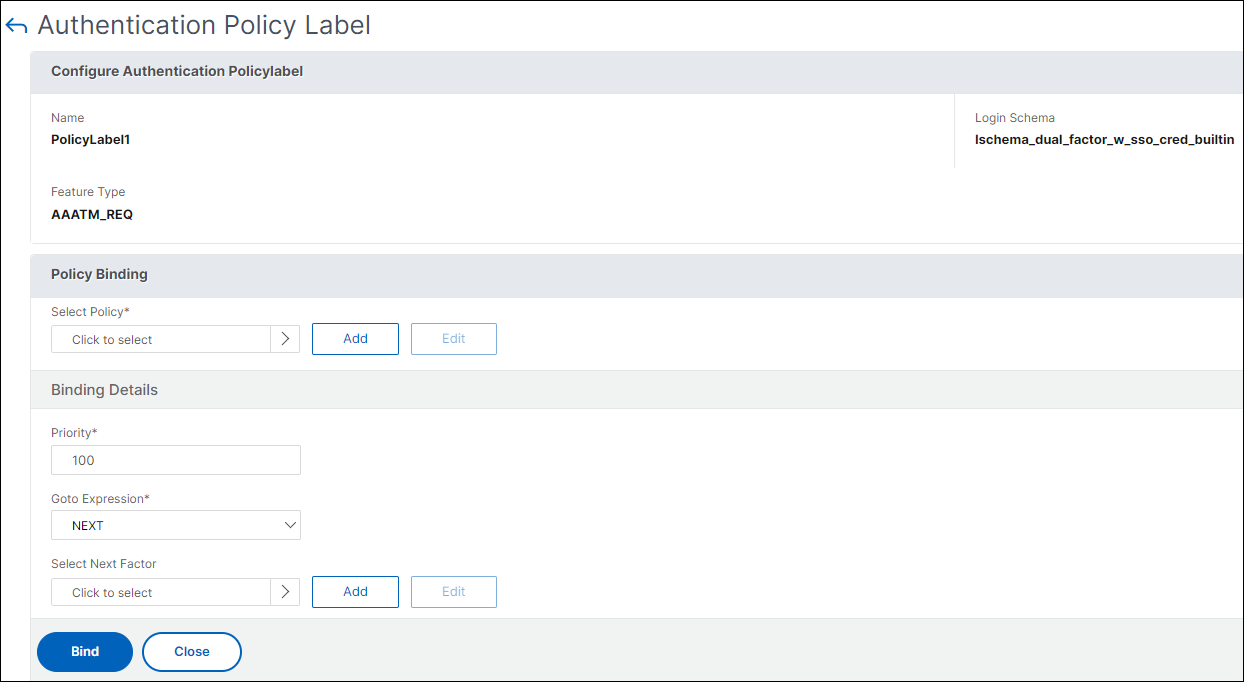
Create a policy label
A policy label specifies the authentication policies for a particular factor. Each policy label corresponds to a single factor. The policy label specifies the login form that must be presented to the user. The policy label must be bound as the next factor of an authentication policy or of another authentication policy label. Typically, a policy label includes authentication policies for a specific authentication mechanism. However, you can also have a policy label that has authentication policies for different authentication mechanisms.
-
Navigate to Security > AAA – Application Traffic > Policies > Authentication > Advanced Policies > Policy Label.
-
Click the Add button.
-
Complete the following fields to create an authentication policy label:
-
Enter the Name for the new authentication policy label.
-
Enter the Login Schema associated with the authentication policy label.
-
Click Continue.
-
- Select a Policy from the drop-down menu.
-
Choose the desired Authentication Policy and click the Select button.
-
Complete the following fields:
-
Enter the Priority of the policy binding.
-
Enter the Goto Expression – the expression specifies the priority of the next policy that will be evaluated if the current policy rule evaluates to TRUE.
-
-
Select the desired Authentication Policy and click the Select button.
-
Click the Bind button.
-
Click Done.
- Review the Authentication Policy Label.
re-Captcha configuration for nFactor authentication
Starting from NetScaler release 12.1 build 50.x, NetScaler Gateway supports a new first class action ‘captchaAction’ that simplifies Captcha configuration. As Captcha is a first class action, it can be a factor of its own. You can inject Captcha anywhere in the nFactor flow.
Previously, you had to write custom WebAuth policies with changes to the RfWebUI as well. With the introduction of captchaACtion, you do not have to modify the JavaScript.
Starting from NetScaler release 14.1 build 47.46, Google re-Captcha v3 is also supported in nFactor authentication in addition to re-Captcha v2. Google re-Captcha v3 offers an advanced authentication method that assesses login requests without requiring user interaction. It assigns a score between 0.0 and 1.0 to each request, with higher scores suggesting safer requests. NetScaler can then use this score to determine whether to authenticate the user or not.
Starting from release 14.1 build 51.x, NetScaler includes support for Google re-Captcha v3 Enterprise console. Previously, re-Captcha v3 support was limited to the Admin console, which has a fixed limit on the number of requests it can handle. In contrast, the Enterprise console allows for an increased request limit based on the subscription plan.
NetScaler currently supports the following re-Captcha configurations:
-
re-Captcha v2 for Admin console
-
re-Captcha v3 for Admin console
-
re-Captcha v3 for Enterprise console
Important:
If re-Captcha is used along with the user name or password fields in the schema, the Log On button is disabled until re-Captcha is met.
re-Captcha configuration
re-Captcha configuration involves two parts.
- Configuration on Google for registering re-Captcha.
- Configuration on NetScaler to use re-Captcha as part of the login flow.
re-Captcha configuration on Google
re-Captcha configuration for Admin Console (re-Captcha v2 and v3)
Register a domain for re-Captcha at https://www.google.com/recaptcha/admin#llist.
-
When you navigate to this page, the following screen appears.
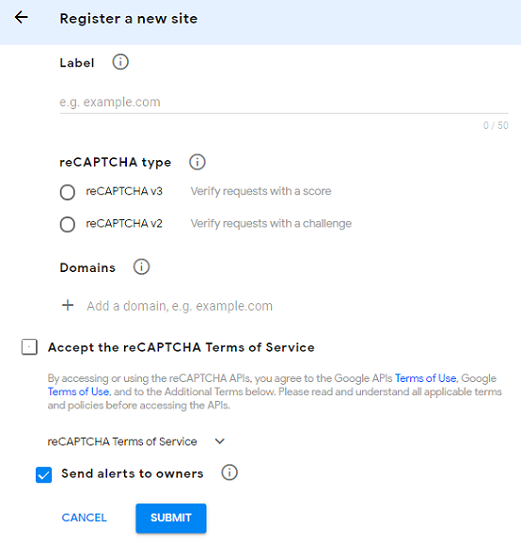
Note
For NetScaler release 14.1 build 47.46 and later, select either reCAPTCHA v2 or reCAPTCHA v3 as required. Previous releases support reCAPTCHA v2 only.
-
After a domain is registered, the “SiteKey” and “SecretKey” are displayed. Note the displayed “SiteKey” and “SecretKey”.
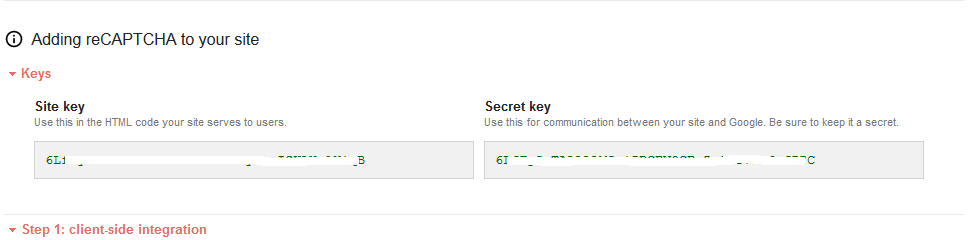
Note
The “SiteKey” and “SecretKey” are grayed out for security reasons. “SecretKey” must be kept safe.
re-Captcha configuration for Enterprise Console (re-Captcha v3)
-
Sign in to https://console.cloud.google.com/ by using a gmail account and create a project.
-
Go to https://console.cloud.google.com/security/recaptcha and create the site key. Note the created site key. For more information, see the Google re-Captcha document.
-
Go to https://console.cloud.google.com/apis/ and create an API key. Note the created API key. For more information, see the Google re-Captcha document.
-
Go to https://console.cloud.google.com/security/recaptcha and copy the server URL from the assessment API (copy till the term “assessments”). Save the copied server URL.
For example, if the assessment API is “https://recaptchaenterprise.googleapis.com/v1/projects/tactile-reason-455709-p6/assessments?key=API_KEY”, you must copy the portion up to “assessments”, which is “https://recaptchaenterprise.googleapis.com/v1/projects/tactile-reason-455709-p6/assessments”. This extracted URL is used as the server URL in the
captchaActioncommand.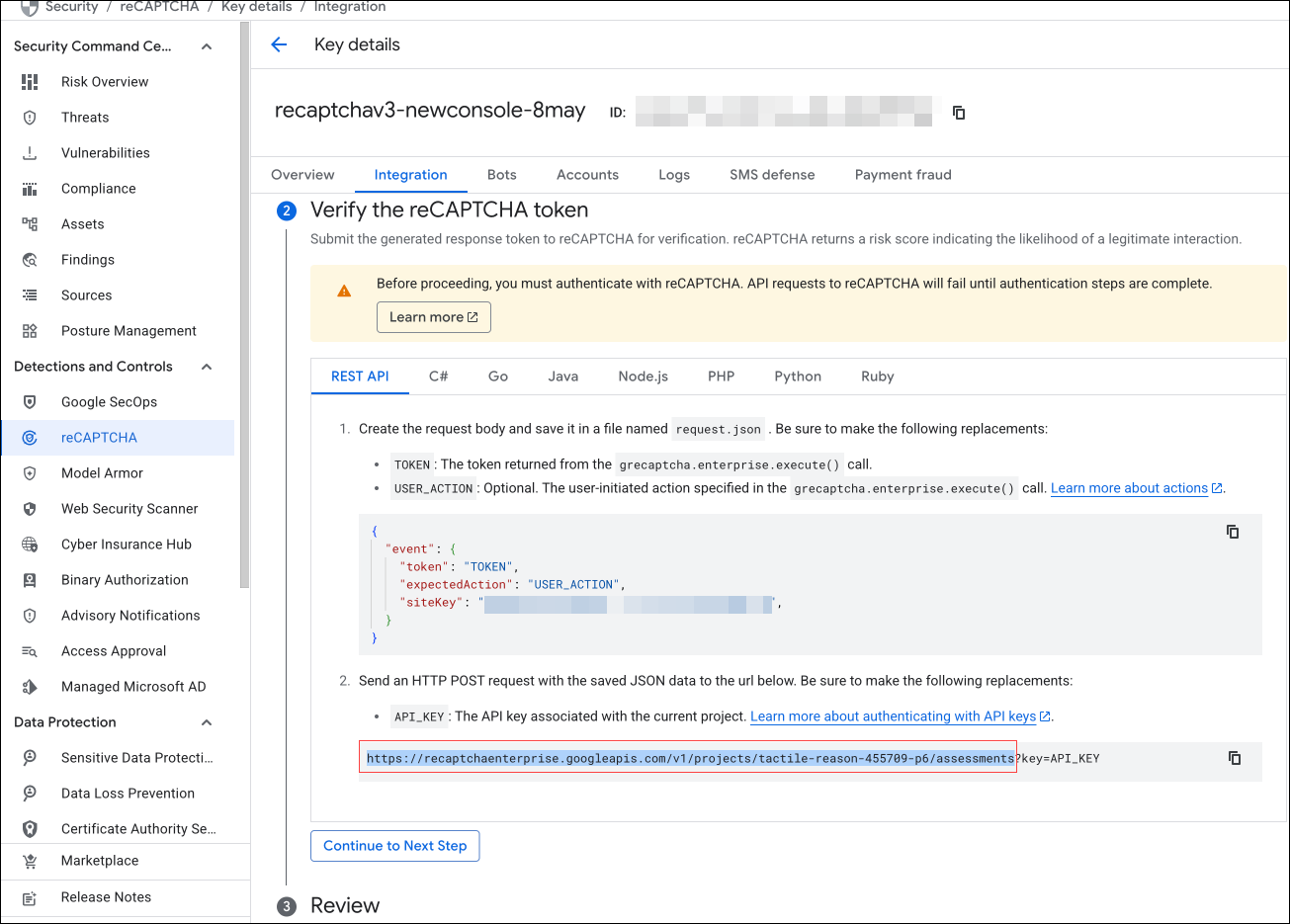
re-Captcha configuration on NetScaler
The re-Captcha configuration on NetScaler can be divided into three parts:
- Display re-Captcha screen
- Post the re-Captcha response to the Google server
- Configure LDAP as the second factor for user logon
Display re-Captcha screen
The login form customization is done through the following login schemas:
-
SingleAuthCaptcha.xmlfor re-Captcha v2 for Admin console -
SingleAuthCaptchav3.xmlfor re-Captcha v3 for Admin console -
SingleAuthReCaptchav3Enterprise.xmlfor re-Captcha v3 for Enterprise console
The customization is specified in the authentication virtual server and is sent to the UI for rendering the login form. The built-in login schema is in the /nsconfig/loginSchema/LoginSchema directory on NetScaler.
Important
- The login schema can be used when LDAP is configured as the second factor.
- You can customize the existing schema based on your use case. For example, you can modify it to include only the re-Captcha factor (without user name or password) or dual authentication with re-Captcha.
- If any custom modifications are done or the file is renamed, we recommend copying all the loginSchemas from the
/nsconfig/loginschema/LoginSchemadirectory to the parent directory,/nsconfig/loginschema.
To configure display of re-Captcha by using the CLI
re-Captcha v2:
add authentication loginSchema singleauthcaptcha -authenticationSchema /nsconfig/loginschema/SingleAuthCaptcha.xml
add authentication loginSchemaPolicy singleauthcaptcha -rule true -action singleauthcaptcha
add authentication vserver auth SSL <IP> <Port>
add ssl certkey vserver-cert -cert <path-to-cert-file> -key <path-to-key-file>
bind ssl vserver auth -certkey vserver-cert
bind authentication vserver auth -policy singleauthcaptcha -priority 5 -gotoPriorityExpression END
<!--NeedCopy-->
re-Captcha v3:
add authentication loginSchema singleauthcaptcha -authenticationSchema /nsconfig/loginschema/SingleAuthCaptchav3.xml
add authentication loginSchemaPolicy singleauthcaptcha -rule true -action singleauthcaptcha
add authentication vserver auth SSL <IP> <Port>
add ssl certkey vserver-cert -cert <path-to-cert-file> -key <path-to-key-file>
bind ssl vserver auth -certkey vserver-cert
bind authentication vserver auth -policy singleauthcaptcha -priority 5 -gotoPriorityExpression END
<!--NeedCopy-->
In the preceding command, use the following login schemas for <login_schema> parameter:
-
SingleAuthCaptcha.xmlfor re-Captcha v2 for Admin console -
SingleAuthCaptchav3.xmlfor re-Captcha v3 for Admin console -
SingleAuthReCaptchav3Enterprise.xmlfor re-Captcha v3 for Enterprise console
Post the re-Captcha response to the Google server
After you have configured the re-Captcha that must be displayed to the users, the admins add the configuration to the Google server to verify the re-Captcha response from the browser.
Prerequisites:
NetScaler contacts https://www.google.com/recaptcha/api/siteverify to validate the Captcha information. So, ensure that the site is reachable from NetScaler.
To verify if the Google site is reachable, run the following script:
curl -vvv https://www.google.com/recaptcha/api/siteverify
NetScaler contacts https://www.google.com/recaptcha/api/siteverify to validate the Captcha information.
To verify re-Captcha response from the browser for the Admin console
The “SiteKey” and “SecretKey” generated during registration of a domain in Google server must be used in the following CLI command.
re-Captcha v2:
add authentication captchaAction myrecaptcha -sitekey <sitekey-copied-from-google> -secretkey <secretkey-from-google>
add authentication policy myrecaptcha -rule true -action myrecaptcha
bind authentication vserver auth -policy myrecaptcha -priority 1
<!--NeedCopy-->
re-Captcha v3:
add authentication captchaAction -siteKey <sitekey> -secretKey <secretKey> -scoreThreshold <0 to 10>
add authentication policy myrecaptcha -rule true -action myrecaptcha
bind authentication vserver auth -policy myrecaptcha -priority 1
<!--NeedCopy-->
The default value of scoreThreshold is 5.
To verify re-Captcha response from the browser for the Enterprise console
The “site key”, “API key”, and “server URL” generated during registration of a domain in Google server must be used in the following CLI command:
add authentication captchaAction -siteKey <sitekey> -secretKey <APIkey> -scoreThreshold<0 - 10> -serverurl <serverURL>
add authentication policy myrecaptcha -rule true -action myrecaptcha
bind authentication vserver auth -policy myrecaptcha -priority 1
<!--NeedCopy-->
The default value of scoreThreshold is 5.
Configure LDAP as the second factor for user logon
Note:
If LDAP authentication is not required, customize the following login schemas to remove the user name and password labels:
SingleAuthCaptcha.xmlfor re-Captcha v2 for Admin console
SingleAuthCaptchav3.xmlfor re-Captcha v3 for Admin console
SingleAuthReCaptchav3Enterprise.xmlfor re-Captcha v3 for Enterprise console
The LDAP authentication happens after re-Captcha, if you add it as the second factor.
add authentication ldapAction ldap-new -serverIP x.x.x.x -serverPort 636 -ldapBase "cn=users,dc=aaatm,dc=com" -ldapBindDn adminuser@aaatm.com -ldapBindDnPassword <password> -encrypted -encryptmethod ENCMTHD_3 -ldapLoginName sAMAccountName -groupAttrName memberof -subAttributeName CN -secType SSL -passwdChange ENABLED -defaultAuthenticationGroup ldapGroup
add authenticationpolicy ldap-new -rule true -action ldap-new
add authentication policylabel second-factor
bind authentication policylabel second-factor -policy ldap-new -priority 10
bind authentication vserver auth -policy myrecaptcha -priority 1 -nextFactor second-factor
<!--NeedCopy-->
The administrator must add appropriate virtual servers depending on whether a load balancing virtual server or NetScaler Gateway is used for access. The administrator must configure the following command if a load balancing virtual server is required:
add lb vserver lbtest HTTP <IP> <Port> -authentication ON -authenticationHost nssp.aaatm.com
<!--NeedCopy-->
**nssp.aaatm.com** – Resolves to authentication virtual server.
User validation of re-Captcha
re-Captcha v2:
After configuring re-Captcha, you see the following UI.
-
Once the authentication virtual server loads the login page, the logon screen is displayed. Log On is disabled until re-Captcha is complete.
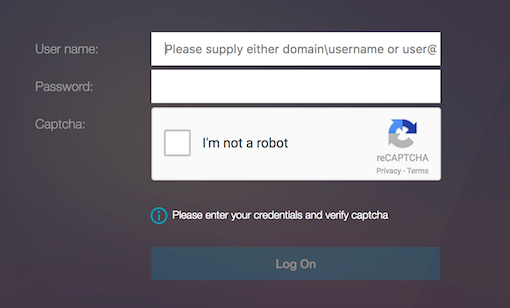
-
Select I’m not a robot. The re-Captcha widget is displayed.

- You are navigated through a series of re-Captcha images, before the completion page is displayed.
-
Enter the AD credentials, select I’m not a robot, and click Log On. If authentication succeeds, you are redirected to the desired resource.
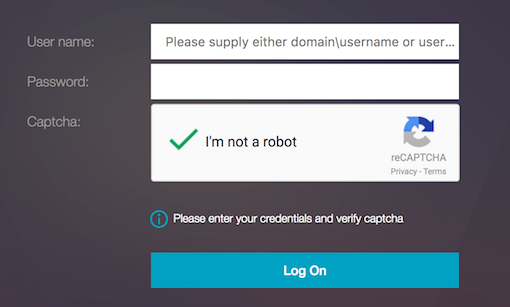
Notes:
- If re-Captcha is used with AD authentication, the Submit button for credentials is disabled until re-Captcha is complete.
- The re-Captcha happens in a factor of its own. Therefore, any subsequent validations like AD must happen in the
nextfactorof re-Captcha.
re-Captcha v3 (Admin console and Enterprise console):
After configuring re-Captcha v3, you see the following UI.
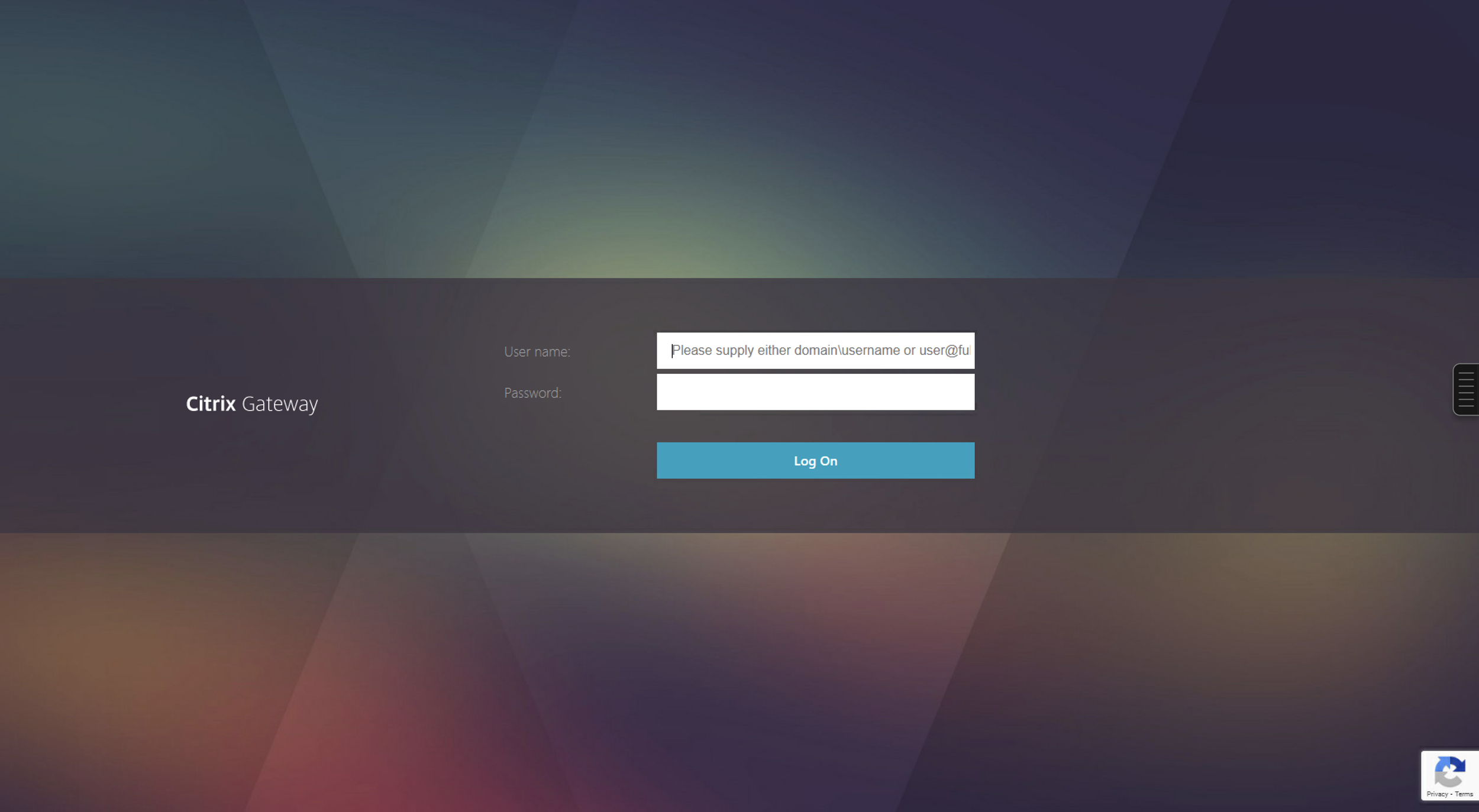
Note:
If re-Captcha v3 is configured, the Log On button is enabled when the captcha response is received from the Google server. When the user clicks the Log On button, the authentication is successful only if the score generated by the re-Captcha service is within the configured scoreThreshold parameter.
Create a Gateway virtual server for nFactor authentication in NetScaler Standard license
- Navigate to NetScaler Gateway > Virtual Servers.
- On the NetScaler Gateway Virtual Servers page, click Add.
- Enter the following details on the VPN Virtual Server page, click OK, and click Continue.
- Name - Name of the NetScaler Gateway virtual server
- Protocol - Select SSL
- IP Address - IP address of NetScaler Gateway virtual server
- Port - Enter 443
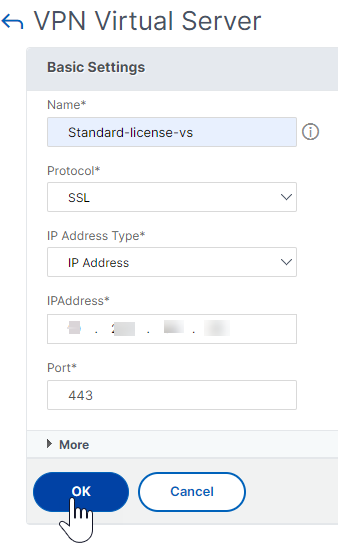
-
On the VPN Virtual Server page, click the plus icon next to Authentication Profile.
-
Click Add to configure the authentication profile.
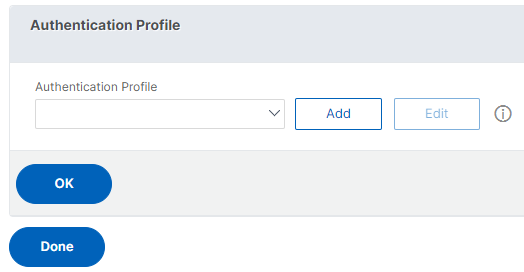
-
Enter a name for the authentication profile and click Add.
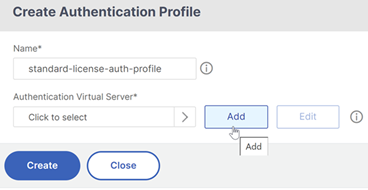
-
Enter the following details on the VPN Virtual Server page, click OK, and click Continue.
- Name - Name of the authentication, authorization, and auditing virtual server
- Protocol - Select Non Addressable. Only a non-addressable authentication, authorization, and auditing virtual server can be bound to a Gateway/VPN virtual server in NetScaler Standard license.
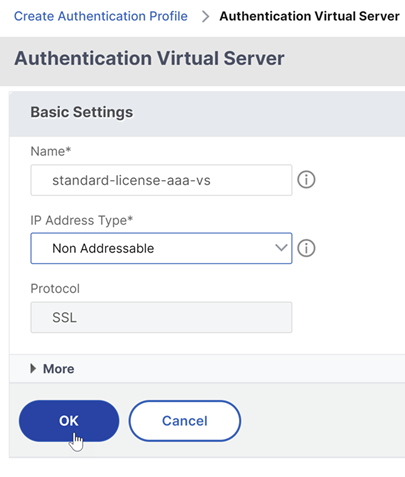
Note:
- In the NetScaler Standard license, the steps for creating a policy are the same as the Premium License for supported policy types.
- NetScaler Standard license does not support an addition of new login schemas in the nFactor configuration.
References
For an end-to-end nFactor configuration example, see Configuring nFactor authentication.
In this article
- Authentication, authorization, and auditing feature licensing requirements
- Use cases
- Authentication response handling
- Client support
- WebView credential type support for authentication mechanisms
- Command line configuration
- Interop challenges
- Endpoint analysis (EPA)
- Misconfiguration considerations
- Defining Clients
- Restricting nFactor for Gateway
- LoginSchema
- LoginSchema and nFactor knowledge required
- Configuring dual factor authentication without using LoginSchema
- User name and password expressions
- High-level steps in nFactor configuration
- GUI Configuration
- Create a virtual server
- Create an authentication virtual server
- Create an authentication CERT profile
- Create an authentication policy
- Add an LDAP authentication server
- Add an LDAP authentication policy
- Add a RADIUS authentication server
- Add a RADIUS authentication policy
- Create an Authentication Login Schema
- Create a policy label
- re-Captcha configuration for nFactor authentication
- Create a Gateway virtual server for nFactor authentication in NetScaler Standard license
- References