Gi-LAN Integration
Typically, a NetScaler appliance is inserted as a separate L3 inline node in the Gi-LAN, similarly to an L3 router.
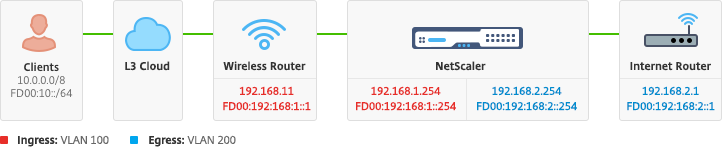
Figure: A simple depiction of a Gi-LAN
Connectivity
A physical NetScaler connectivity to upstream switches is recommended to provide for sufficient redundancy. For example, assuming that a NetScaler appliance is inserted in a Gi-LAN that is handling a total (uplink+downlink) of 24Gbps, connectivity with 4x10GbE or more interfaces is recommended. This effectively provides for N+1 redundancy in case of a link failure.
The relevant ports on the upstream switch should be configured for LACP port aggregation. The relevant configuration on NetScaler is outlined below:
Connectivity Configuration:
set interface 10/1 –tagall ON –lacpMode ACTIVE –lacpKey 1
set interface 10/2 –tagall ON –lacpMode ACTIVE –lacpKey 1
set interface 10/3 –tagall ON –lacpMode ACTIVE –lacpKey 1
set interface 10/4 –tagall ON –lacpMode ACTIVE –lacpKey 1
<!--NeedCopy-->
You can verify the appropriate functionality of LACP using the “show interface” command:
show interface:
sh interface LA/1
1) Interface LA/1 (802.3ad Link Aggregate) #39
flags=0x4100c020 <ENABLED, UP, AGGREGATE, UP, HAMON, 802.1q>
MTU=1500, native vlan=1, MAC=02:e0:ed:33:88:b0, uptime 340h11m56s
Requested: media NONE, speed AUTO, duplex NONE, fctl NONE,
throughput 0
Actual: throughput 4000
LLDP Mode: NONE,
RX: Pkts(918446) Bytes(110087414) Errs(0) Drops(795989) Stalls(0)
TX: Pkts(124113) Bytes(15255532) Errs(0) Drops(0) Stalls(0)
NIC: InDisc(0) OutDisc(0) Fctls(0) Stalls(0) Hangs(0) Muted(0)
Bandwidth thresholds are not set.
Disable the remaining unused interfaces and turn off the monitor.
set interface 10/5 –haMonitor OFF
<!--NeedCopy-->
Command:
set interface 10/24 –haMonitor OFF
disable interface 10/5
disable interface 10/24
<!--NeedCopy-->
Configuration of physical interfaces is not shared across the two NetScaler units. Hence, the above commands must be run across both NetScaler nodes in case of an HA pair deployment.
HA Configuration
All other configuration parameters are shared between the NetScaler nodes of an HA pair. Hence, HA sync should be enabled prior to any other configuration commands being run. Basic HA configuration involves the following steps:
1. Using the exact same NetScaler hardware, software, and license: HA pairs are not supported between different models (i.e. a T1100 and an MPX21550) or same models with different firmware levels. Refer to the appropriate instructions on upgrading an existing HA pair - Upgrading to Release 11.1.
2. Establishing the HA pair.
Example:
netscaler-1> add HA node 1 <netscaler-2-NSIP>
netscaler-2> add HA node 1 <netscaler-1-NSIP>
<!--NeedCopy-->
3. Verify the HA pair establishment running the following command in either node; both nodes should be visible, one of them as Primary (active), the other as a Secondary (standby).
Example:
show HA node
<!--NeedCopy-->
4. Enable failsafe mode and maxFlips. This ensures that in case of a route monitor failure on both nodes at least one node remains active without active/standby status constantly switching.
Example:
set HA node –failsafe ON
set HA node -maxFlips 3 -maxFlipTime 1200
<!--NeedCopy-->
5. Finally, enable HA sync to occur over the dedicated intra-NetScaler ports rather than the OAM network.
Example:
add vlan 4080 -aliasName syncVlan
set HA node -syncvlan 4080
<!--NeedCopy-->
Note
The VLAN 4080 in the commands in the above example shouldn’t be taken literally. Any unused VLAN-ID might be reserved.
VLAN Configuration
After the physical interfaces have been appropriately configured, you might configure the appropriate Gi-LAN VLANs. For instance, consider a rather simple Gi-LAN environment with an ingress/egress VLAN pair with 100/101 VLAN-identifier respectively.
The following commands configure the relevant VLANs on top of the LACP channel created in the prior step.
add vlan 100
add vlan 101
bind vlan 100 –ifnum LA/1 –tagged
bind vlan 101 –ifnum LA/1 –tagged
<!--NeedCopy-->
IPv4 Configuration
Typically, a NetScaler appliance requires one SNIP per VLAN. The example below assumes that the networks outlined in the Gi-LAN integration diagram, given in the begining of this page, have a /24 subnet mask:
add ns ip 192.168.1.254 255.255.255.0 –vserver DISABLED –mgmtAccess DISABLED
add ns ip 192.168.2.254 255.255.255.0 –vserver DISABLED –mgmtAccess DISABLED
<!--NeedCopy-->
After the SNIPs have been configured they should be associated with the appropriate VLAN:
bind vlan 100 –IPAddress 192.168.1.254 255.255.255.0
bind vlan 101 –IPAddress 192.168.2.254 255.255.255.0
<!--NeedCopy-->
IPv4 Static Routing
The example outlined in the Management Network section calls for only a couple of static routing rules:
- A 10.0.0.0/8 static route to the clients through the ingress router
- A default route to the internet through the egress router
Example:
add route 0.0.0.0 0.0.0.0 192.168.2.1
add route 10.0.0.0 255.0.0.0 192.168.1.1
<!--NeedCopy-->
IPv4 Policy-Based (VLAN - VLAN) routing
A NetScaler appliance allows for policy-based routing instead of static routing, with routing decisions usually keyed against the incoming interface and/or VLAN rather than destination IP. Policy-based routing is either a convenient alternative, in case the client source IP address range is subject to periodic changes, or a mandatory consideration, in case a packet’s destination IP address is not sufficient by itself to reach a routing decision (i.e. in case of overlapping client IP addresses across multiple VLANs).
Example:
add ns pbr fromWirelessToInternet ALLOW –nextHop 192.168.2.1 –vlan 100 –priority 10
Done
add ns pbr fromInternetToWireless ALLOW –nextHop 192.168.1.1 –vlan 200 –priority 20
Done
apply ns pbrs
<!--NeedCopy-->
IPv6 Configuration
The following commands assign IPv6 SNIP per vlan. The example below assumes that the networks outlined in the Figure: A simple depiction of a Gi-LAN in this page have a /64 subnet mask:
Command:
add ns ip6 fd00:192:168:1::254/64 -vServer DISABLED –mgmtAccess DISABLED
add ns ip6 fd00:192:168:2::254/64 -vServer DISABLED –mgmtAccess DISABLED
bind vlan 100 -IPAddress fd00:192:168:1::254/64
bind vlan 200 -IPAddress fd00:192:168:2::254/64
<!--NeedCopy-->
IPv6 Routing
After IPv6 addressing is complete, IPv6 static routing might be configured:
- A fd00:10::/64 static route to the clients via the ingress router
- A default route to the internet via the egress router
Example:
add route6 fd00:10::/64 fd00:192:168:1::1
add route6 ::/0 fd00:192:168:2::1
<!--NeedCopy-->
Or using policy-based routing:
Example:
add ns pbr6 fromWirelessToInternetv6 ALLOW -vlan 100 -priority 10 -nextHop fd00:192:168:2::1
add ns pbr6 fromInternetToWirelessv6 ALLOW -vlan 200 -priority 20 -nextHop fd00:192:168:1::1
apply ns pbr6
<!--NeedCopy-->
LACP Redundancy and Failover
In case of an HA configuration, it’s recommended to leverage the throughput option to configure a low threshold for the LACP channel. For instance, consider a 25Gbps Gi-LAN and a 4x10GbE channel between each NetScaler appliance in the HA pair and the upstream switch to provide N+1 link redundancy:
Example:
set interface LA/1 –haMonitor ON –throughput 29000
<!--NeedCopy-->
In case of a double-link failure between the primary appliance and the upstream switch the maximum Gi-LAN throughput that can be supported would fall to 20Gbps. A 29Gbps low threshold per the example above would result in a redundancy switchover event to the secondary appliance (which has not suffered similar link failures) so that Gi-LAN traffic is not affected.
Route Monitors
In addition to LACP redundancy, route monitor checks might be configured and associated with the HA pair configuration. Route monitor checks can be useful to detect failures between the NetScaler appliance and the next-hop routers, especially if said routers are not directly connected but through an upstream switch.
A typical HA route monitor configuration per the sample Gi-LAN in section 2.5.1 is outlined below:
add route 192.168.1.0 255.255.255.0 192.168.1.1 -msr ENABLED -monitor arp
add route 192.168.2.0 255.255.255.0 192.168.2.1 -msr ENABLED -monitor arp
bind HA node -routeMonitor 192.168.1.0 255.255.255.0
bind HA node -routeMonitor 192.168.2.0 255.255.255.0
<!--NeedCopy-->