Configure SSL action to forward client traffic
When parsing the client hello message, a NetScaler appliance can forward the client traffic using an SSL forward action associated with an SSL policy. The policy is bound to the virtual server at client hello request bind point. Some use cases where forwarding can be used are discussed in the following sections. For information about configuring an SSL forward action if a cipher is not supported on a NetScaler appliance, see Configure SSL action to forward client traffic if a cipher is not supported on the ADC.
The following illustration explains the traffic flow. The forward virtual server is of type SSL_TCP in this illustration.
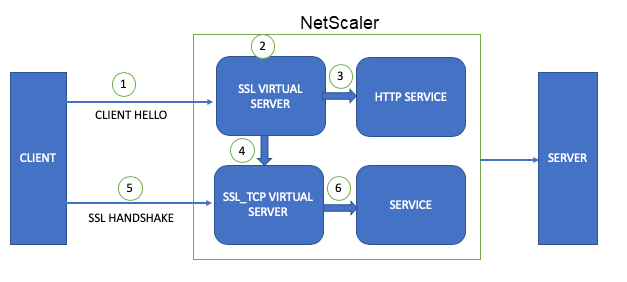
- A client initiates the SSL handshake and sends the client hello message to the ADC appliance.
- The appliance evaluates the configured policy by using the parameters in the client hello message.
- If the policy evaluates to false, the decrypted traffic is forwarded to the HTTP service and then to the back-end server.
- If the policy evaluates to true, the traffic is forwarded to the forward virtual server defined in the action.
- The forward virtual server completes the handshake with the client.
- All the traffic meeting the policy rule is forwarded to the back-end service through the service bound to the forward virtual server.
Configure an SSL action to forward client traffic if the appliance does not have a domain specific (SNI) certificate
Note: This feature is available in release 12.1 build 49.x and later.
In the client hello message, you might receive a request for a domain for which the certificate is not available on the appliance. In this case, you can configure an SSL action to forward the client traffic to a different virtual server. In the following example, we have configured an SSL virtual server as the forward virtual server. This setting ensures that all the connections that fail because of a missing SNI certificate on the original virtual server are successful on the forward virtual server.
Perform the following steps:
- Add a load balancing virtual server of type SSL (For example, vMain). Client traffic is received on this virtual server.
- Add server and CA certificates and bind them to the SSL virtual server.
- Add an SSL service with port 443.
- Bind this service to the SSL virtual server.
- Add another load balancing virtual server of type SSL/SSL_TCP/TCP/SSL_BRIDGE to forward the traffic to. (For example,
fwd-vserver). - Add a service and bind it to this virtual server.
- Add an SSL forward action specifying the SSL virtual server
fwd-vserverin the ‘forward’ parameter. - Add an SSL policy (for example,
pol-ssl-sni) specifying the preceding action if a specific domain name (SNI) is received in the client hello message. - Bind this policy to the SSL virtual server at CLIENTHELLO_REQ.
- Save the configuration.
Configuration using the CLI
Configuration for the SSL virtual server to which to forward the traffic:
add lb vserver fwd-vserver SSL 198.51.100.20 443
add ssl certkey sv -cert complete/server/server_rsa_2048.pem -key complete/server/server_rsa_2048.ky
add ssl certkey cacert -cert SHA256-RSA-PEM_512.pem -key SHA256-RSA-PEM_512.ky
bind ssl vserver fwd-vserver -certkeyName sv
bind ssl vserver fwd-vserver -certkeyName cacert -CA
add service ssl-service2 198.51.100.18 SSL 443
bind lb vserver fwd-vserver ssl-service2
<!--NeedCopy-->
Configuration for the SSL virtual server that originally receives the client traffic:
add service ssl-service 198.51.100.5 SSL 443
add lb vserver vMain SSL 198.51.100.25 443
bind ssl vserver vMain -certkeyName sv
bind lb vserver vMain ssl-service
set ssl vserver vMain -sni ENABLED
add ssl certKey snicert2 -cert /nsconfig/ssl/complete/SNI/server/serverabc.pem -key /nsconfig/ssl/complete/SNI/server/serverabc.ky
add ssl certKey snicert -cert /nsconfig/ssl/complete/SNI/server/serverabcnetscaler.pem -key /nsconfig/ssl/complete/SNI/server/serverabcnetscaler.ky
bind ssl vserver vMain -certkeyName snicert -sniCert
bind ssl vserver vMain -certkeyName snicert2 -sniCert
<!--NeedCopy-->
Policy configuration for the SSL virtual server vMain:
add ssl action act_ssl_fwd -forward fwd-vserver
add ssl policy pol-ssl-sni -rule client.ssl.client_hello.sni.contains("xyz") -action act_ssl_fwd
bind ssl vserver vMain -policyName pol-ssl-sni -type CLIENTHELLO_REQ -priority 1
<!--NeedCopy-->
sh ssl vserver vMain
Advanced SSL configuration for VServer vMain:
DH: DISABLED
DH Private-Key Exponent Size Limit: DISABLED Ephemeral RSA: ENABLED Refresh Count: 0
Session Reuse: ENABLED Timeout: 120 seconds
Cipher Redirect: DISABLED
SSLfwd-vserver Redirect: DISABLED
ClearText Port: 0
Client Auth: DISABLED
SSL Redirect: DISABLED
Non FIPS Ciphers: DISABLED
SNI: ENABLED
OCSP Stapling: DISABLED
HSTS: DISABLED
HSTS IncludeSubDomains: NO
HSTS Max-Age: 0
SSLfwd-vserver: DISABLED SSLv3: ENABLED TLSv1.0: ENABLED TLSv1.1: ENABLED TLSv1.2: ENABLED TLSv1.3: DISABLED
Push Encryption Trigger: Always
Send Close-Notify: YES
Strict Sig-Digest Check: DISABLED
Zero RTT Early Data: DISABLED
DHE Key Exchange With PSK: NO
Tickets Per Authentication Context: 1
ECC Curve: P_256, P_384, P_224, P_521
1) CertKey Name: sv Server Certificate
2) CertKey Name: snicert2 Server Certificate for SNI
3) CertKey Name: snicert Server Certificate for SNI
Data policy
1) Policy Name: pol-ssl-sni Priority: 1
1) Cipher Name: DEFAULT
Description: Default cipher list with encryption strength >= 128bit
Done
<!--NeedCopy-->
sh ssl policy pol-ssl-sni
Name: pol-ssl-sni
Rule: client.ssl.client_hello.sni.contains("xyz")
Action: act_ssl_fwd
UndefAction: Use Global
Hits: 0
Undef Hits: 0
Policy is bound to following entities
1) Bound to: CLIENTHELLO_REQ VSERVER v1
Priority: 1
Done
<!--NeedCopy-->
sh ssl action act_ssl_fwd
1) Name: act_ssl_fwd
Type: Data Insertion
Forward to: fwd-vserver
Hits: 0
Undef Hits: 0
Action Reference Count: 1
Done
<!--NeedCopy-->
sh ssl vserver fwd-vserver
Advanced SSL configuration for VServer fwd-vserver:
DH: DISABLED
DH Private-Key Exponent Size Limit: DISABLED Ephemeral RSA: ENABLED Refresh Count: 0
Session Reuse: ENABLED Timeout: 120 seconds
Cipher Redirect: DISABLED
SSLfwd-vserver Redirect: DISABLED
ClearText Port: 0
Client Auth: DISABLED
SSL Redirect: DISABLED
Non FIPS Ciphers: DISABLED
SNI: DISABLED
OCSP Stapling: DISABLED
HSTS: DISABLED
HSTS IncludeSubDomains: NO
HSTS Max-Age: 0
SSLfwd-vserver: DISABLED SSLv3: ENABLED TLSv1.0: ENABLED TLSv1.1: ENABLED TLSv1.2: ENABLED TLSv1.3: DISABLED
Push Encryption Trigger: Always
Send Close-Notify: YES
Strict Sig-Digest Check: DISABLED
Zero RTT Early Data: DISABLED
DHE Key Exchange With PSK: NO
Tickets Per Authentication Context: 1
ECC Curve: P_256, P_384, P_224, P_521
1) CertKey Name: sv Server Certificate
1) Cipher Name: DEFAULT
Description: Default cipher list with encryption strength >= 128bit
Done
<!--NeedCopy-->
Configure an SSL action to forward client traffic based on the application protocol in the ALPN extension of the client hello message
Note: This feature is supported in release 13.0 build 61.x and later.
A NetScaler appliance can identify the protocols coming in the ALPN extension of the client hello message while parsing the message for policy evaluation. The rule to identify the protocol in the ALPN extension of the client hello message is client.ssl.client_hello.alpn.has_nextprotocol<protocol_name>. Associate a “forward” type SSL action with the policy to forward the packets to the forward virtual server. The forward virtual server can be of type SSL, SSL_TCP, SSL_BRIDGE, or TCP.
To negotiate the application protocol in the ALPN extension for the connections handled by the SSL_TCP virtual server, a parameter alpnProtocol is added to the front-end SSL profiles. Supported values for the parameter are HTTP1.1, HTTP2, or NONE (default value). Only the protocol specified in the SSL profile is negotiated, if the same protocol is received in the ALPN extension of the client hello message. The maximum supported length of the ALPN extension for policy evaluation is 4096 bytes.
Sample configuration to forward all requests containing HTTP2 protocol in the ALPN extension to an SSL_TCP virtual server
The SSL_TCP virtual server to forward the traffic to is fwd-vserver-1.
Configuration for the SSL virtual server to which to forward the traffic:
add lb vserver fwd-vserver-1 SSL_TCP 198.51.100.20 443
add ssl certkey sv -cert complete/server/server_rsa_2048.pem -key complete/server/server_rsa_2048.ky
add ssl certkey rootCA -cert SHA256-RSA-PEM_512.pem -key SHA256-RSA-PEM_512.ky
bind ssl vserver fwd-vserver-1 -certkeyName sv
bind ssl vserver fwd-vserver-1 -certkeyName rootCA -CA
add service ssl-tcp-service 198.51.100.14 SSL_TCP 443
bind lb vserver fwd-vserver-1 ssl-tcp-service
<!--NeedCopy-->
Configuration for the SSL virtual server that originally receives the client traffic:
add service ssl-service 198.51.100.5 SSL 443
add lb vserver vMain-alpn SSL 198.51.100.25 443
bind ssl vserver vMain-alpn -certkeyName sv
bind lb vserver vMain-alpn ssl-service
<!--NeedCopy-->
Policy configuration for the SSL virtual server vMain-alpn:
add ssl action forward-action-alpn -forward fwd-vserver-1
add ssl policy pol-ssl-alpn -rule "client.ssl.client_hello.alpn.has_nextprotocol(\"h2\")" -action forward-action-alpn
bind ssl vserver VMain-alpn -policyName pol-ssl-alpn -priority 2 -type CLIENTHELLO_REQ
<!--NeedCopy-->
sh ssl vserver vMain-alpn
Advanced SSL configuration for VServer vMain-alpn:
DH: DISABLED
DH Private-Key Exponent Size Limit: DISABLED Ephemeral RSA: ENABLED Refresh Count: 0
Session Reuse: ENABLED Timeout: 120 seconds
Cipher Redirect: DISABLED
ClearText Port: 0
Client Auth: DISABLED
SSL Redirect: DISABLED
Non FIPS Ciphers: DISABLED
SNI: DISABLED
OCSP Stapling: DISABLED
HSTS: DISABLED
HSTS IncludeSubDomains: NO
HSTS Max-Age: 0
HSTS Preload: NO
SSLv3: ENABLED TLSv1.0: ENABLED TLSv1.1: ENABLED TLSv1.2: ENABLED TLSv1.3: DISABLED
Push Encryption Trigger: Always
Send Close-Notify: YES
Strict Sig-Digest Check: DISABLED
Zero RTT Early Data: DISABLED
DHE Key Exchange With PSK: NO
Tickets Per Authentication Context: 1
ECC Curve: P_256, P_384, P_224, P_521
1) CertKey Name: sv Server Certificate
Data policy
1) Policy Name: pol-ssl-alpn Priority: 2
1) Cipher Name: DEFAULT
Description: Default cipher list with encryption strength >= 128bit
Done
<!--NeedCopy-->
sh ssl policy pol-ssl-alpn
Name: pol-ssl-alpn
Rule: client.ssl.client_hello.alpn.has_nextprotocol("h2")
Action: forward-action-alpn
UndefAction: Use Global
Hits: 0
Undef Hits: 0
Policy is bound to following entities
1) Bound to: CLIENTHELLO_REQ VSERVER VMain-alpn
Priority: 2
Done
<!--NeedCopy-->
sh ssl action forward-action-alpn
1) Name: forward-action-alpn
Type: Data Insertion
Forward to: fwd-vserver-1
Hits: 0
Undef Hits: 0
Action Reference Count: 1
Done
<!--NeedCopy-->
sh ssl vserver fwd-vserver-1
Advanced SSL configuration for VServer fwd-vserver-1:
DH: DISABLED
DH Private-Key Exponent Size Limit: DISABLED Ephemeral RSA: ENABLED Refresh Count: 0
Session Reuse: ENABLED Timeout: 120 seconds
Cipher Redirect: DISABLED
ClearText Port: 0
Client Auth: DISABLED
SSL Redirect: DISABLED
Non FIPS Ciphers: DISABLED
SNI: DISABLED
OCSP Stapling: DISABLED
HSTS: DISABLED
HSTS IncludeSubDomains: NO
HSTS Max-Age: 0
HSTS Preload: NO
SSLv3: ENABLED TLSv1.0: ENABLED TLSv1.1: ENABLED TLSv1.2: ENABLED TLSv1.3: DISABLED
Push Encryption Trigger: Always
Send Close-Notify: YES
Strict Sig-Digest Check: DISABLED
Zero RTT Early Data: DISABLED
DHE Key Exchange With PSK: NO
Tickets Per Authentication Context: 1
ECC Curve: P_256, P_384, P_224, P_521
1) CertKey Name: sv Server Certificate
2) CertKey Name: rootCA CA Certificate OCSPCheck: Optional CA_Name Sent
1) Cipher Name: DEFAULT
Description: Default cipher list with encryption strength >= 128bit
Done
<!--NeedCopy-->