Set up Citrix Secure Access for macOS users
Important:
Citrix SSO for iOS is now called Citrix Secure Access. We are updating our documentation and the UI screenshots to reflect this name change.
The Citrix Secure Access client for macOS provides a best-in-class application access and data protection solution offered by NetScaler Gateway. You can now securely access business critical applications, virtual desktops, and corporate data from anywhere at any time. Citrix Secure Access is the next generation VPN client for NetScaler Gateway to create and manage VPN connections from macOS devices. Citrix Secure Access is built using Apple’s Network Extension (NE) framework. NE framework from Apple is a modern library which contains APIs that can be used to customize and extend the core networking features of macOS. Network Extension with support for SSL VPN is available on devices running macOS 10.11+.
Citrix Secure Access provides complete Mobile Device Management (MDM) support on macOS. With an MDM server, an admin can now remotely configure and manage device level VPN profiles and per-app VPN profiles. Citrix Secure Access for macOS can be installed from a Mac App store.
For the list of some commonly used features supported by the Citrix Secure Access client for macOS, see NetScaler Gateway VPN clients and supported features.
Compatibility with MDM products
Citrix Secure Access for macOS is compatible with most MDM providers such as Citrix XenMobile, Microsoft Intune and so on. It supports a feature called Network Access Control (NAC) using which, MDM administrators can enforce end user device compliance before connecting to NetScaler Gateway. NAC on Citrix Secure Access requires an MDM server such as XenMobile and NetScaler Gateway. For more information on NAC, see Configure Network Access Control device check for NetScaler Gateway virtual server for single factor login.
Note:
To use the Citrix Secure Access with NetScaler Gateway VPN without MDM, you must add a VPN configuration. You can add the VPN configuration on macOS from the Citrix Secure Access configuration page.
Configure an MDM managed VPN profile for Citrix Secure Access
The following section captures step-by-step instructions to configure both device-wide and per-app VPN profiles for Citrix Secure Access using Citrix Endpoint Management (formerly XenMobile) as an example. Other MDM solutions can use this document as reference when working with Citrix Secure Access.
Note:
This section explains the configuration steps for a basic Device-wide and Per-App VPN profile. Also you can configure On-Demand, Proxies by following the Citrix Endpoint Management (formerly XenMobile) documentation or Apple’s MDM VPN payload configuration.
Device level VPN profiles
Device level VPN profiles are used to set up a system wide VPN. Traffic from all apps and services is tunneled to NetScaler Gateway based on the VPN policies (such as Full-tunnel, Split-tunnel, Reverse Split tunnel) defined in NetScaler.
To configure a device level VPN on Citrix Endpoint Management
Perform the following steps to configure a device level VPN.
-
On the Citrix Endpoint Management MDM console, navigate to Configure > Device Policies > Add New Policy.
-
Select macOS on the left Policy Platform pane. Select VPN Policy on the right pane.
-
On the Policy Info page, enter a valid policy name and description and click Next.
-
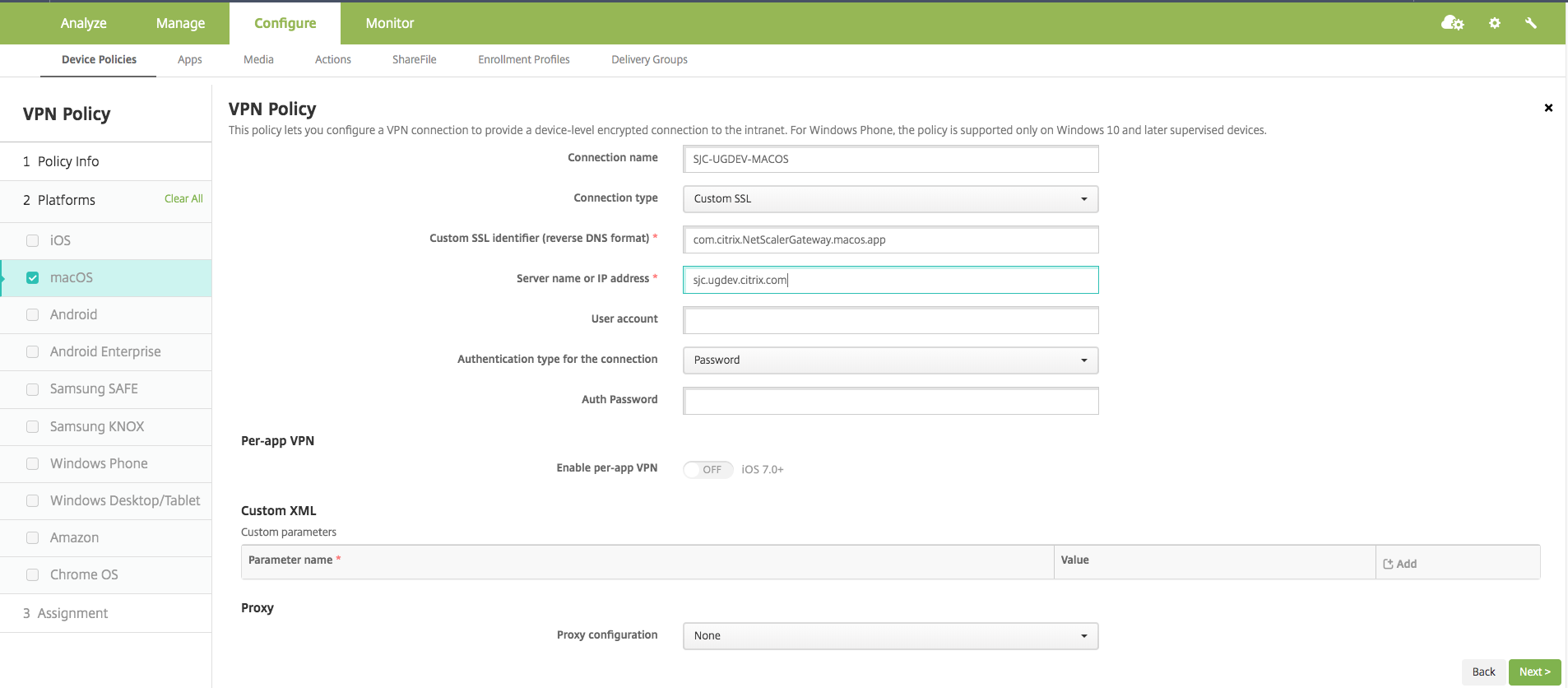
On the Policy detail page for macOS, type a valid connection name and choose Custom SSL in Connection Type.
In the MDM VPN payload, the connection name corresponds to the UserDefinedName key and VPN Type Key must be set to VPN.
-
In Custom SSL identifier (reverse DNS format), enter com.citrix.NetScalerGateway.macos.app. This is the bundle identifier for the Citrix Secure Access on macOS.
In the MDM VPN payload, the Custom SSL identifier corresponds to the VPNSubType key.
-
In Provider bundle identifier enter com.citrix.NetScalerGateway.macos.app.vpnplugin. This is the bundle identifier of the network extension contained in the Citrix Secure Access client binary.
In the MDM VPN payload, the provider bundle identifier corresponds to the ProviderBundleIdentifier key.
-
In Server name or IP address enter the IP address or FQDN of the NetScaler associated with this Citrix Endpoint Management instance.
The remaining fields in the configuration page are optional. Configurations for these fields can be found in the Citrix Endpoint Management documentation.
-
Click Next.
-
Click Save.
Per-App VPN profiles
Per-App VPN profiles are used to set up a VPN for a specific application. Traffic from only the specific app is tunneled to NetScaler Gateway. The Per-App VPN payload supports all keys for Device-wide VPN plus a few other keys.
To configure a per-App level VPN on Citrix Endpoint Management
Perform the following steps to configure a Per-App VPN on Citrix Endpoint Management:
-
Complete the device level VPN configuration on Citrix Endpoint Management.
-
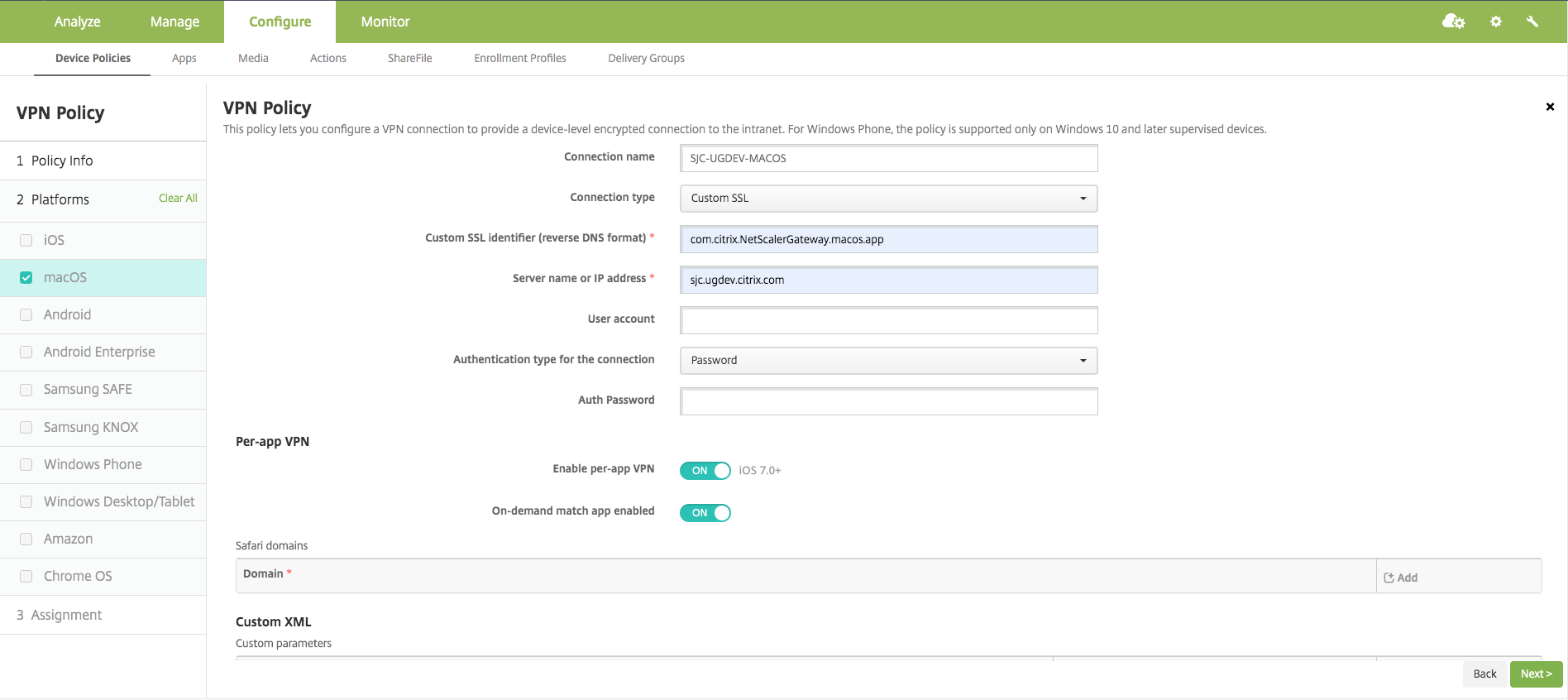
Turn the Enable Per-App VPN switch ON in the Per-App VPN section.
-
Turn the On-Demand Match App Enabled switch ON if Citrix Secure Access must be started automatically when the Match App is launched. This is recommended for most Per-App cases.
In the MDM VPN payload, this field corresponds to the key OnDemandMatchAppEnabled.
-
Safari Domain configuration is optional. When a Safari domain is configured, Citrix Secure Access starts automatically when users launch Safari and navigate to a URL that matches the one in the Domain field. This is not recommended if you want to restrict the VPN for a specific app.
In the MDM VPN payload, this field corresponds to the key SafariDomains.
The remaining fields in the configuration page are optional. Configurations for these fields can be found in the Citrix Endpoint Management (formerly XenMobile) documentation.
-
Click Next.
-
Click Save.
To associate the VPN profile to a specific App on the device, you must create an App Inventory policy and a credentials provider policy.
Configuring split tunnel in Per-App VPN
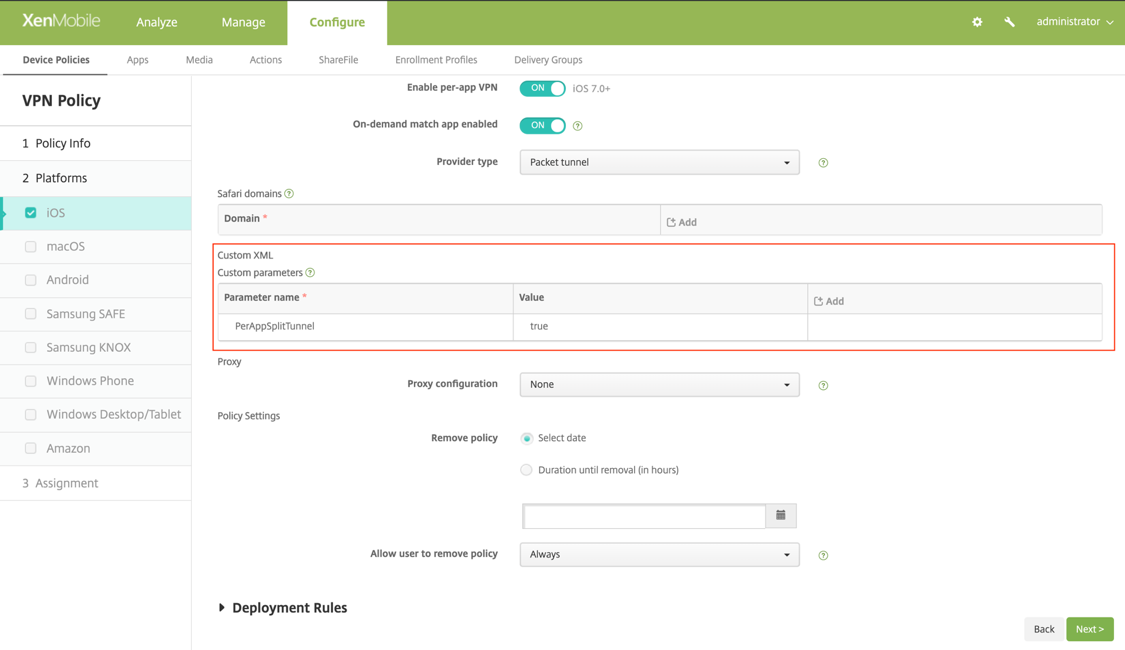
MDM customers can configure split tunnel in Per-App VPN for Citrix Secure Access. The following key/value pair must be added to the vendor configuration section of the VPN profile created on the MDM server.
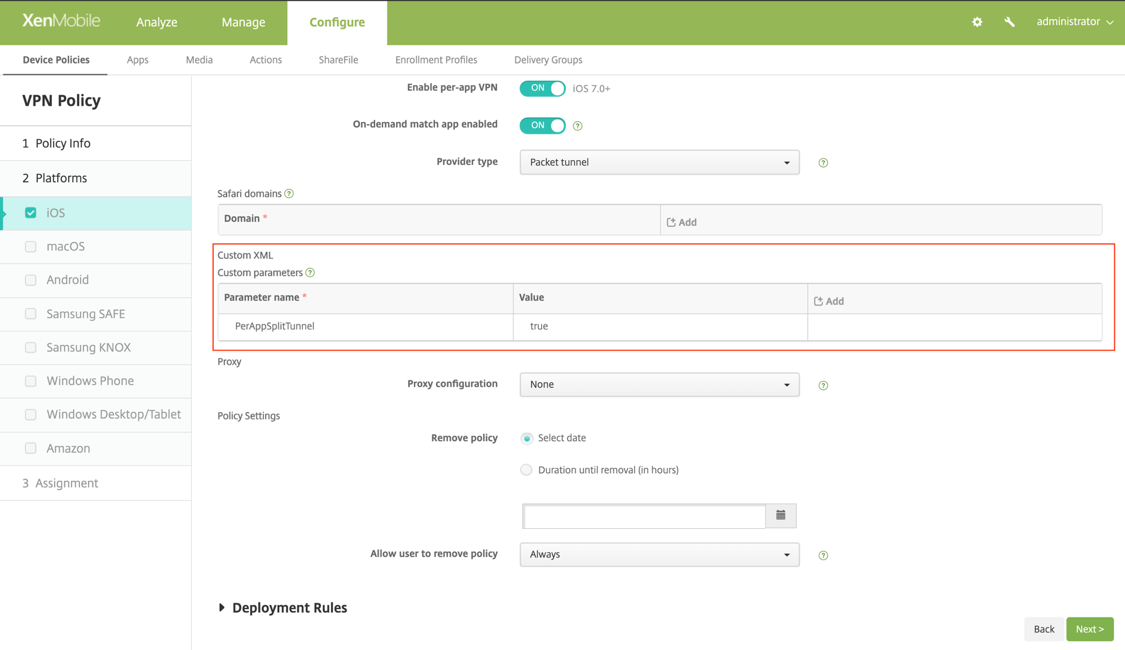
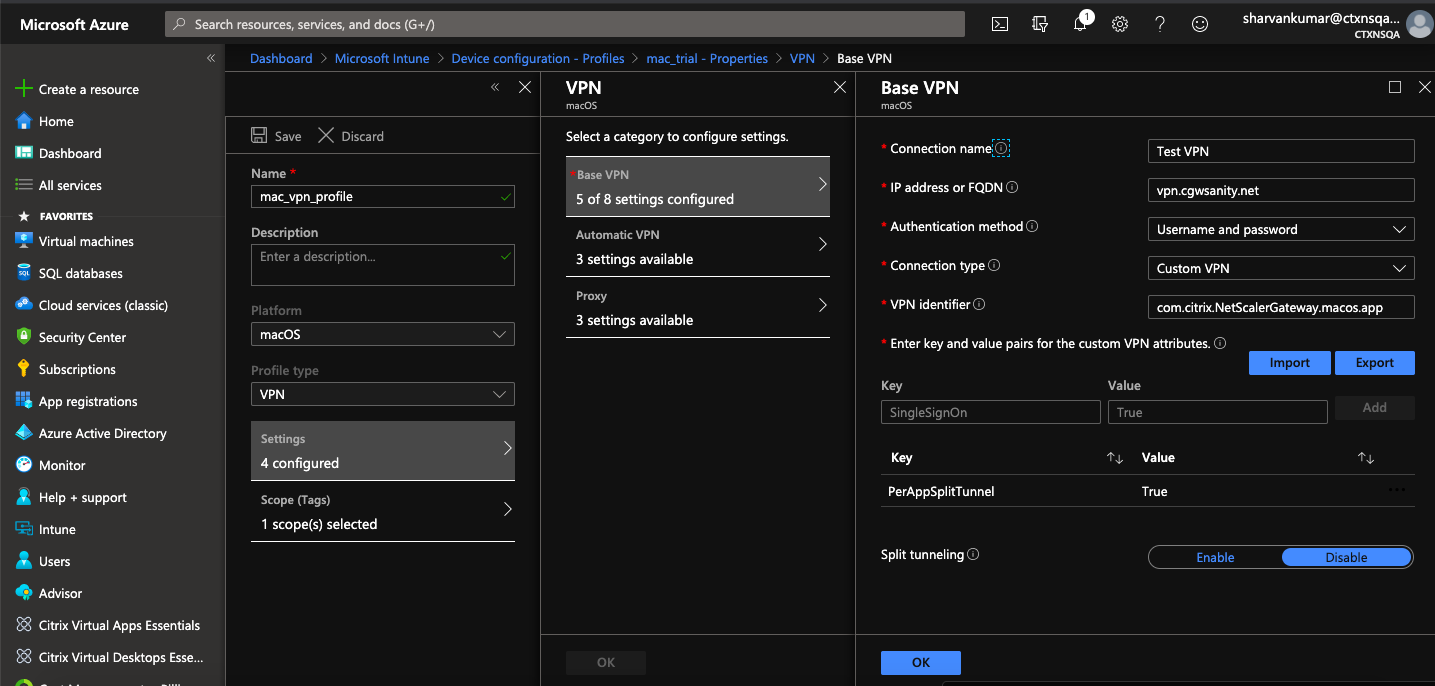
- Key = "PerAppSplitTunnel"
- Value = "true or 1 or yes"
The key is case sensitive and must be an exact match while the value is not case sensitive.
Note:
The user interface to configure vendor configuration is not standard across the MDM vendors. Contact the MDM vendor to find the vendor configuration section on your MDM user console.
The following is a sample screenshot of the configuration (vendor specific settings) in Citrix Endpoint Management.
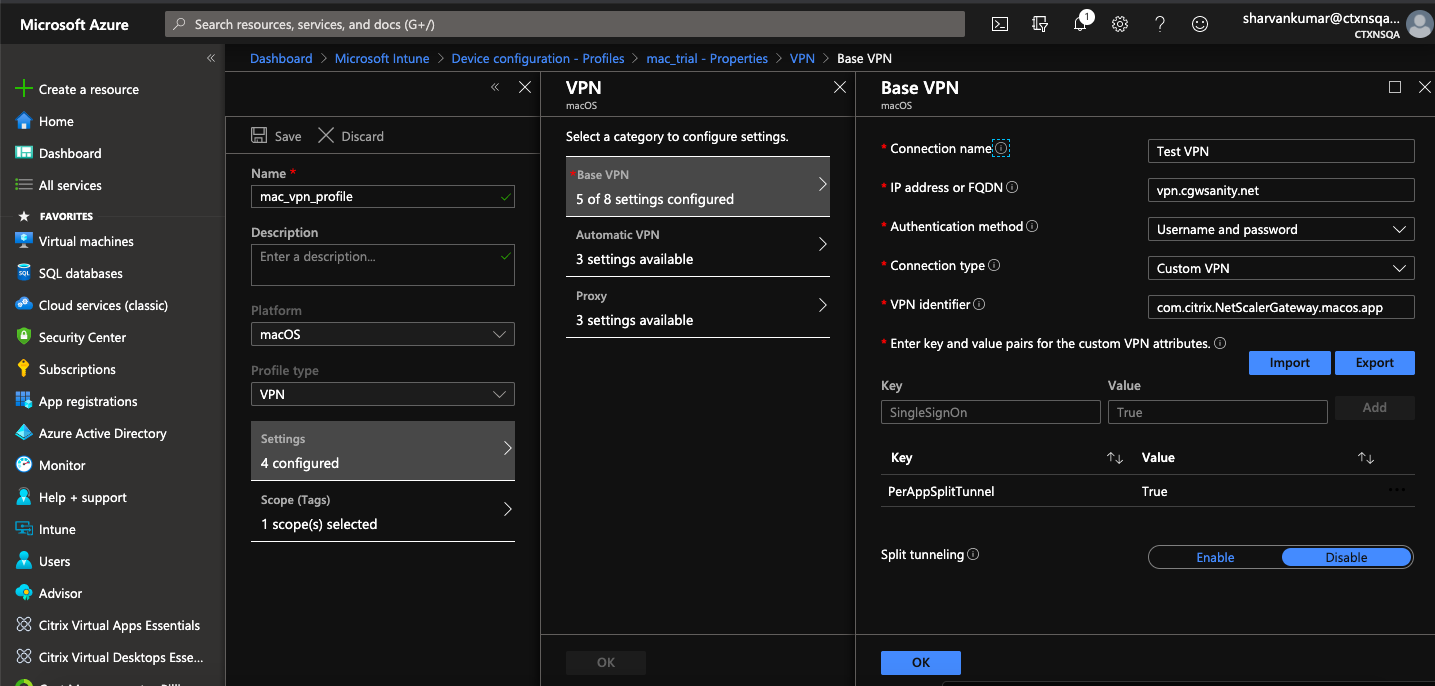
The following is a sample screenshot of the configuration (vendor specific settings) in Microsoft Intune.
Disabling user created VPN profiles
MDM customers can prevent users from manually creating VPN profiles from within the Citrix Secure Access. To do this, the following key/value pair must be added to the vendor configuration section of the VPN profile created on the MDM server.
- Key = "disableUserProfiles"
- Value = "true or 1 or yes"
The key is case sensitive and must be an exact match while the value is not case sensitive.
Note:
The user interface to configure vendor configuration is not standard across MDM vendors. Contact the MDM vendor to find the vendor configuration section on your MDM user console.
The following is a sample screenshot of the configuration (vendor specific settings) in Citrix Endpoint Management.
The following is a sample screenshot of the configuration (vendor specific settings) in Microsoft Intune.
DNS handling
The recommended DNS settings for Citrix Secure Access are as follows:
- Split DNS > REMOTE if the split tunnel is set to OFF.
- Split DNS > BOTH if the split tunnel is set to ON. In this case, the admins have to add DNS suffixes for the intranet domains. DNS queries for FQDNs belonging to DNS suffixes are tunneled to the NetScaler appliance and the remaining queries go to the local router.
Note:
It is recommended that the DNS truncate fix flag is always ON. For more details, see https://support.citrix.com/article/CTX200243.
When split tunnel is set to ON and split DNS is set to REMOTE, there might be issues resolving DNS queries after the VPN is connected. This is related to the Network Extension framework not intercepting all the DNS queries.
Supported EPA scans
For the complete list of scans supported, see Latest EPA Libraries.
- In the section Supported Scan Matrix by OPSWAT v4, click Supported Application List under the column MAC OS Specific.
- In the Excel file, click the Classic EPA scans tab to view the details.
Known issues
The following are the known issues currently.
- EPA login fails if the user is placed in the quarantine group.
- Forced timeout warning message is not displayed.
- Citrix Secure Access allows login if the split tunnel is ON and no intranet apps are configured.
Limitations
The following are the limitations currently.
- The following EPA scans might fail because of restricted access to Secure Access due to sandboxing.
- Hard Disk encryption ‘type’ and ‘path’
- Web Browser ‘default’ and ‘running’
- Patch management ‘missing patches’
- Kill process operation during EPA
- Split tunneling based on ports/protocols is not supported.
- Ensure that you do not have two certificates with the same name and expiry date in the keychain as this causes the client to display only one of the certificates instead of both.
Troubleshooting
If the end users are presented with the Download EPA plug-in button in the authentication window of Citrix Secure Access, it means that the content security policy on the NetScaler appliance is blocking invocation of the URL com.citrix.agmacepa://. The admins have to modify the content security policy such that com.citrix.agmacepa:// is allowed.