Getting started
This article describes how to get started with Citrix Secure Internet Access™ (CSIA) for the first time.
Before you begin the initial setup, review the licensing and pre-requisites information.
Pre-requisites
Ensure you have the following:
-
Citrix Cloud account. To use Citrix Secure Internet Access, you must have a Citrix Cloud account. Go to https://citrix.cloud.com and verify that you can sign in with your existing Citrix Cloud account.
If you do not have a Citrix Cloud account, first create a Citrix Cloud account. You can also join an existing account created by someone else in your organization. For detailed processes and instructions on how to proceed, see Sign up for Citrix Cloud.
-
Citrix Virtual Apps and Desktops™ deployment accessible through Citrix Workspace.
-
Workspace app on your host systems such as laptops and mobile devices.
-
SD-WAN deployments. If you are working from a branch office, you must have the following deployments:
- Citrix SD-WAN 11.1 and later
- Subscription to Citrix SD-WAN Orchestrator™ service. Ensure that you have done the initial setup and configured sites on your SD-WAN Orchestrator.
Initial setup
This section walks you through the required tasks for the Citrix Secure Internet Access initial setup.
Step 1: Request access to Citrix Secure Internet Access
You can get access to Citrix Secure Internet Access by requesting for a Citrix Secure Internet Access trial. You can use the trial for a maximum 60 days period. For more information on service trials, see Citrix Cloud Service Trials.
To request a trial,
Sign in to your Citrix Cloud™ account.
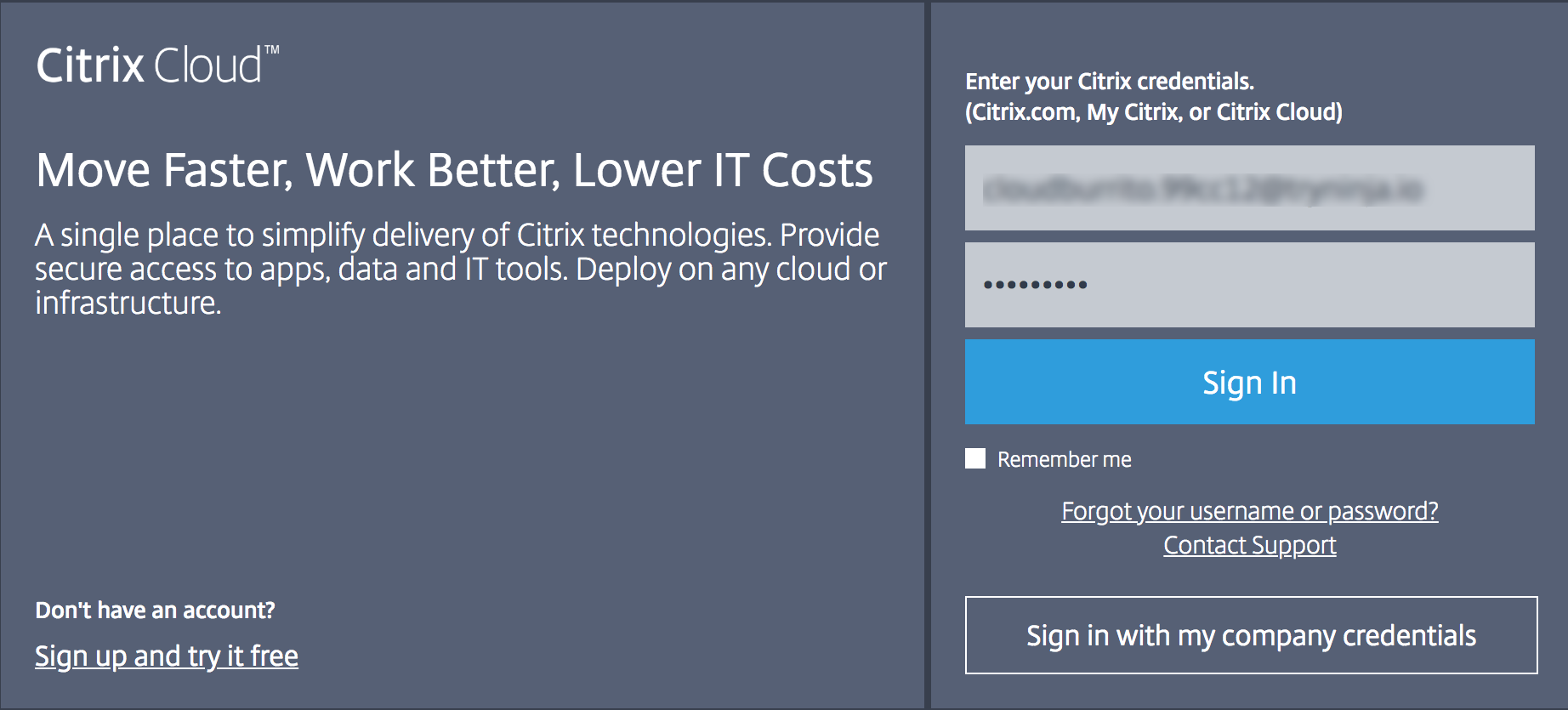
On the Citrix Cloud home page, in Available Services, on the Secure Internet Access tile, click Request Demo.
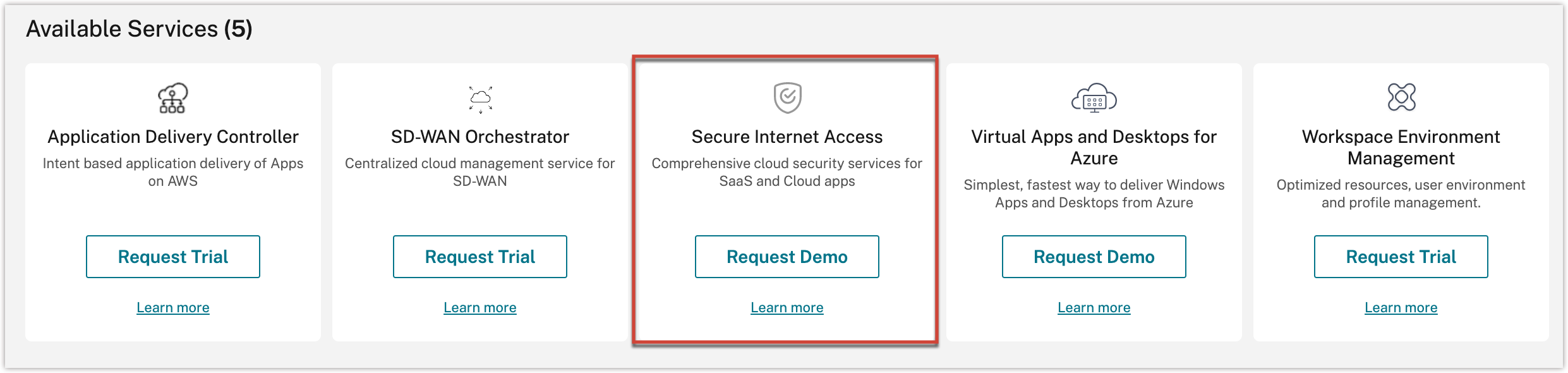
Note
Alternatively, you can also visit https://www.citrix.com/products/citrix-secure-internet-access/form/inquiry/ and contact a Citrix expert who can help you.
Enter the required details and select Submit.
When your trial is approved, Citrix initiates the trial process and creates your Customer Entitlement Package based on the license package selected. You also receive an email confirmation.
Step 2: View status of your account
After your trial is approved and initiated, you will receive an email confirmation and you can also view your account status on Citrix Cloud.
To set up your account, Citrix provisions gateway nodes for you implicitly. These nodes are containerized nodes that scan data and traffic in the cloud. The nodes also perform security functions such as web filtering, malware prevention, and data loss prevention.
After the nodes are set up, you receive an email notification that your account is available. Provisioning of nodes can take a few days.
To view the status of your account
- Sign in to your Citrix Cloud account.
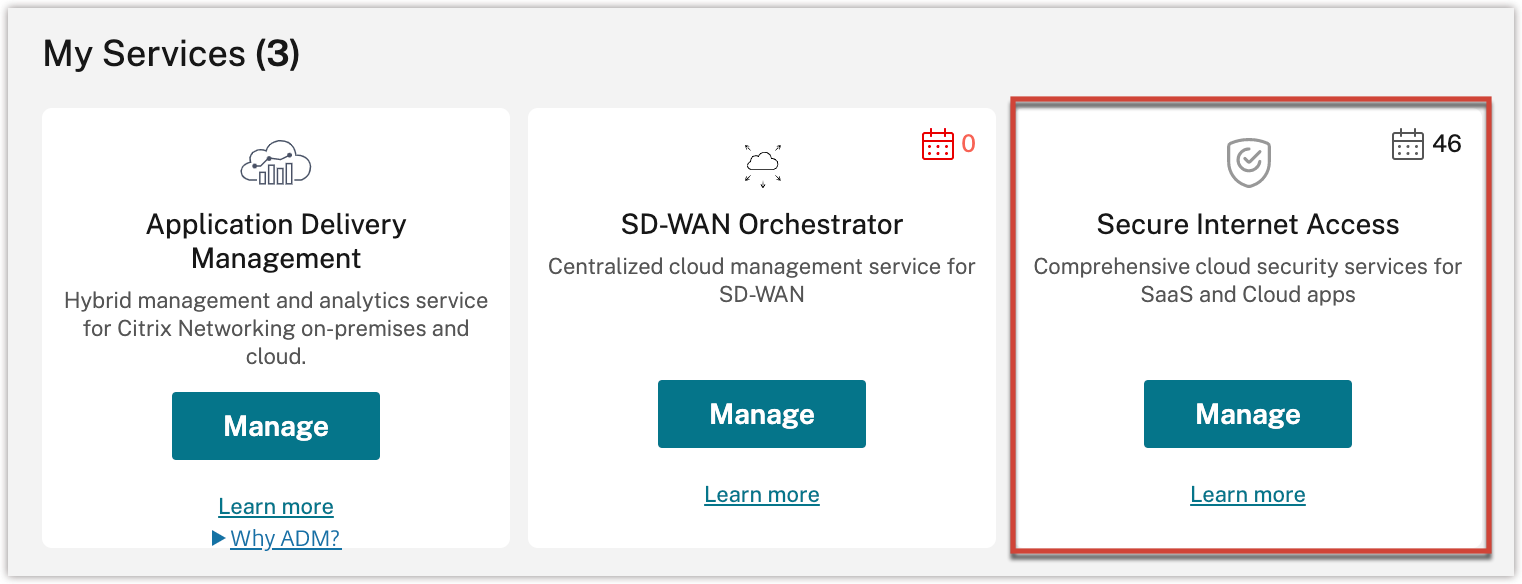
- On the Citrix Cloud home page, in My Services, on the Secure Internet Access tile, click Manage.
If your account provisioning is in progress, you see the following message:
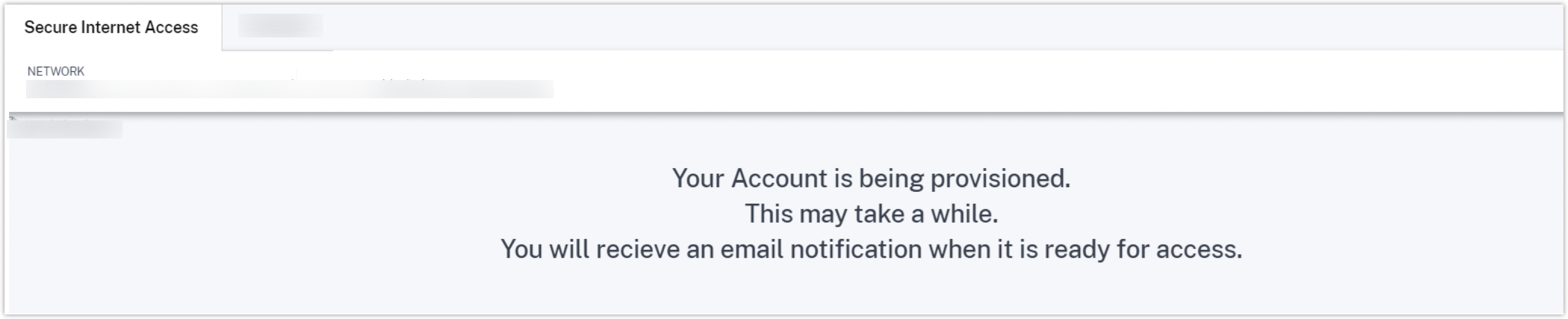
Step 3: Manage Citrix Secure Internet Access
After you receive the email confirmation about your account setup, sign in to Citrix Cloud and start configuring and managing your deployment.
On the Citrix Cloud home page, in My Services, on the Secure Internet Access tile, click Manage.
Note
If you have a Citrix SD-WAN™ Orchestrator subscription, you can also click Manage on the SD-WAN Orchestrator tile to view the Citrix Secure Internet Access dashboard.

On the Dashboard menu, you can view the status and a graphical representation of your nodes.
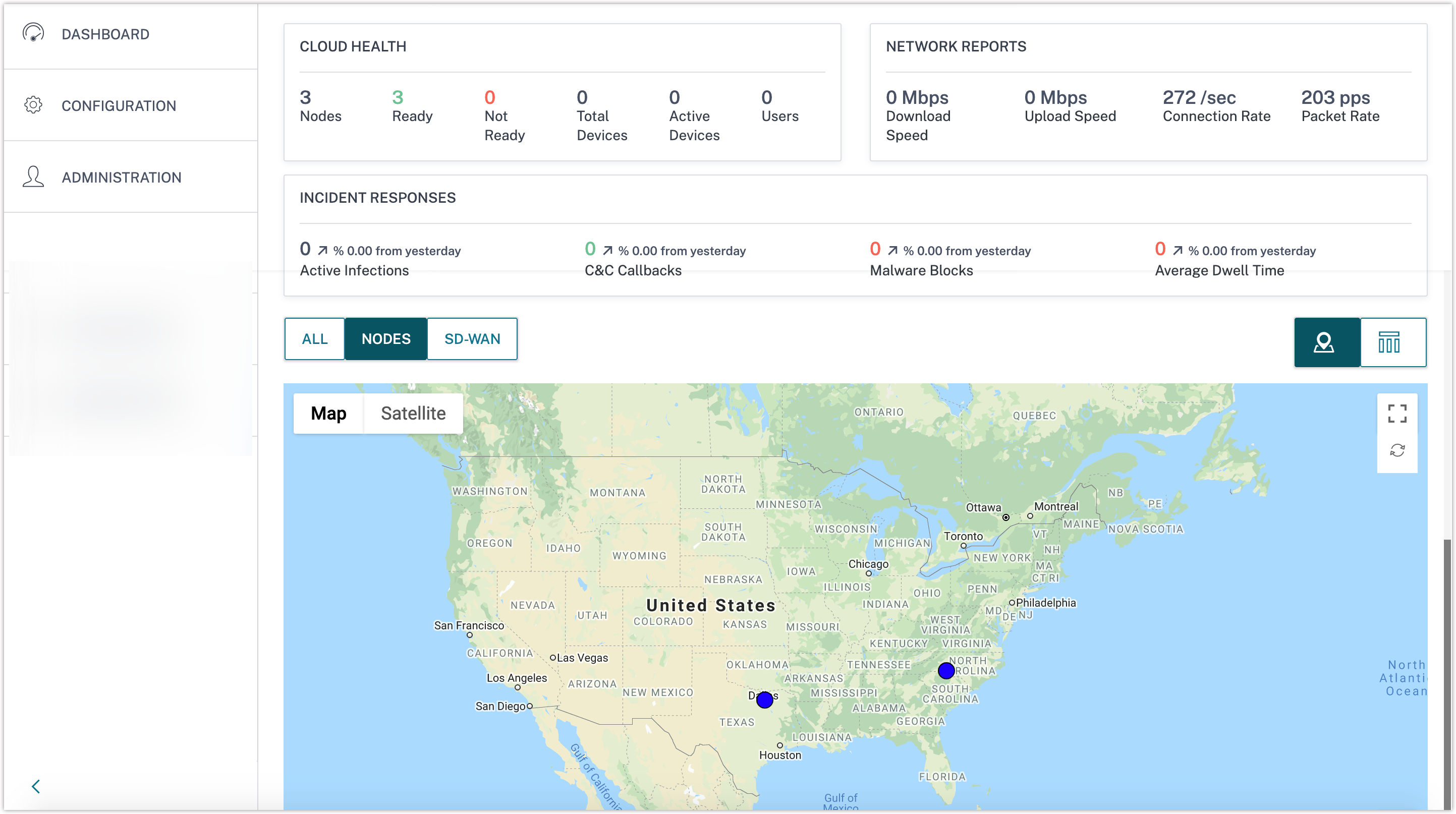
The initial setup is now complete.
Onboarding
The Citrix Secure Internet Access Onboarding lets you configure your user account after your account is provisioned. You must perform some basic onboarding settings to access the other CSIA configuration.
The Open Citrix SIA Configuration option is available in the Network Configuration Home page. You cannot view the configuration policy portal without completing the onboarding process.
Once your account is provisioned, you land on the Citrix Secure Internet Access Onboarding page by default. Click Get Started to proceed with the onboarding process or click Skip Onboarding to skip this step and perform the onboarding later. When you click Skip Onboarding, you will land on the Citrix Secure Internet Access dashboard page.
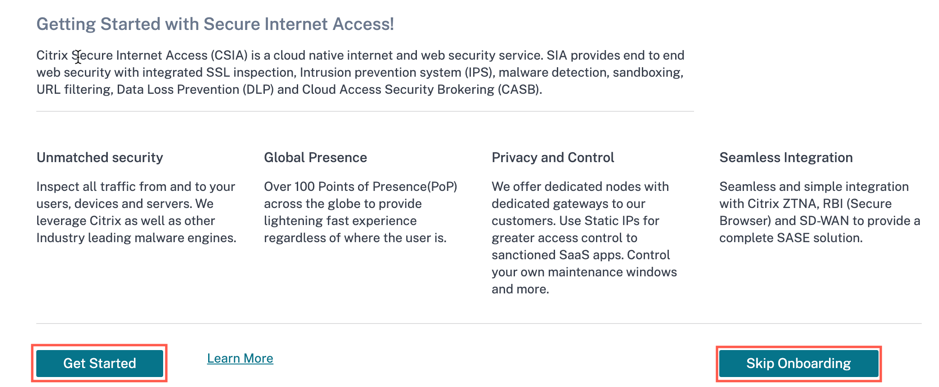
-
Configure Proxy Settings
Select the user authentication method from the drop-down list. The default value is set to Local User Credentials + Cloud Connections.
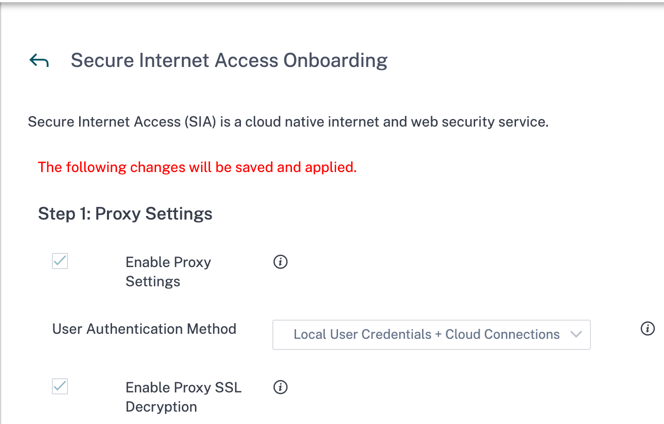
The following are the four authentication methods:
-
Local User Credentials + Cloud Connections: Login with local secure internet access account. This method also supports agent mode which enables secure internet access agents/endpoints to automatically register with the gateway by injecting proxy authentication into requests.
-
Local User Credentials: Login with local secure internet access account.
-
Cloud Connectors Only: Uses agent mode which enables secure internet access agents/endpoints to automatically register with the gateway by injecting proxy authentication into requests.
-
Browser Based SMAL: Authentication in the browser and ideal for branch office users who would be sourced from the same public IP.
Enable Proxy Settings and Enable Proxy SSL Decryption settings are enabled by default and non-editable check boxes.
In the proxy auto configuration settings, under the PAC Settings: Bypass Domains section, select the following check box as required:
-
Bypass WebSockets: Bypass domains for WebSockets traffic and WebSockets traffic over the Secure Sockets Layer (SSL)/ Transport Layer Security (TLS). The Bypass WebSockets check box is enabled by default.
-
Bypass Cloud security for Citrix Cloud infrastructure domains: Bypass the Citrix sites requests. It is enabled by default. The Citrix Cloud Domain List is a non-editable list of Citrix Cloud infrastructure domains that must be bypassed from any inspection.
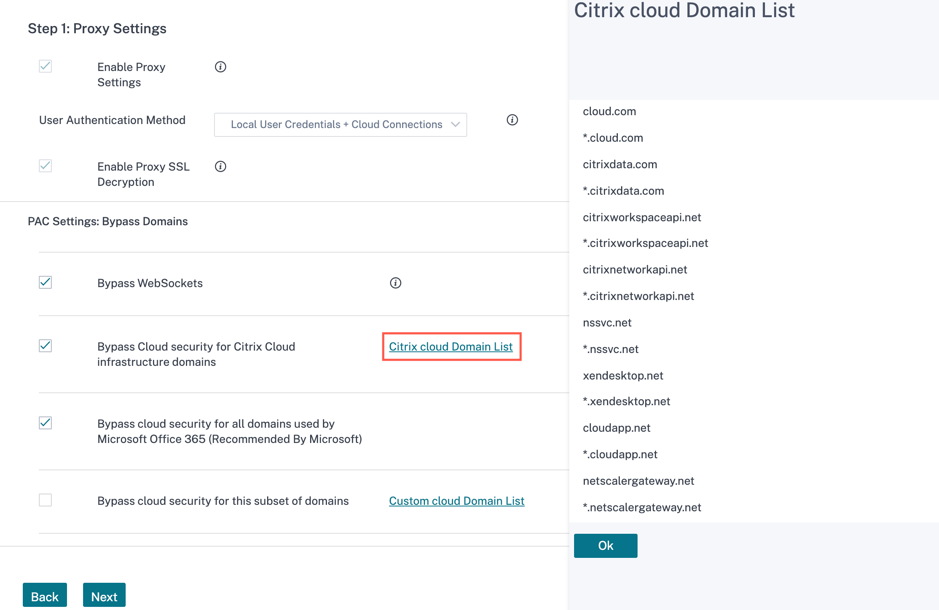
-
Bypass Cloud security for all domains used by Microsoft Office 365 (Recommended by Microsoft): Bypass the domains that is used for the Microsoft Office 365. The Bypass Cloud security for all domains used by Microsoft Office 365 (Recommended by Microsoft) check box is enabled by default.
-
Bypass Cloud security for this subset of domains: Bypass any custom domains. You can create your own domains using the Custom Cloud Domain List option.
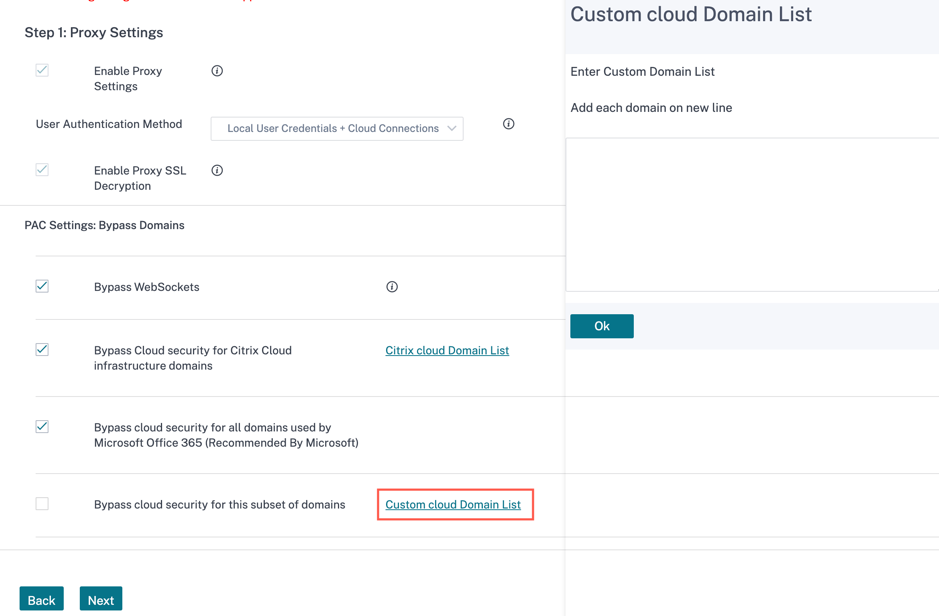
Click Next.
-
-
Configure Cloud Connector Settings
The Cloud Connector is a downloadable agent that is available for various OS such as Windows, Linux, macOS, and so on. These settings will configure the behavior of the installed Cloud Connector on your devices.
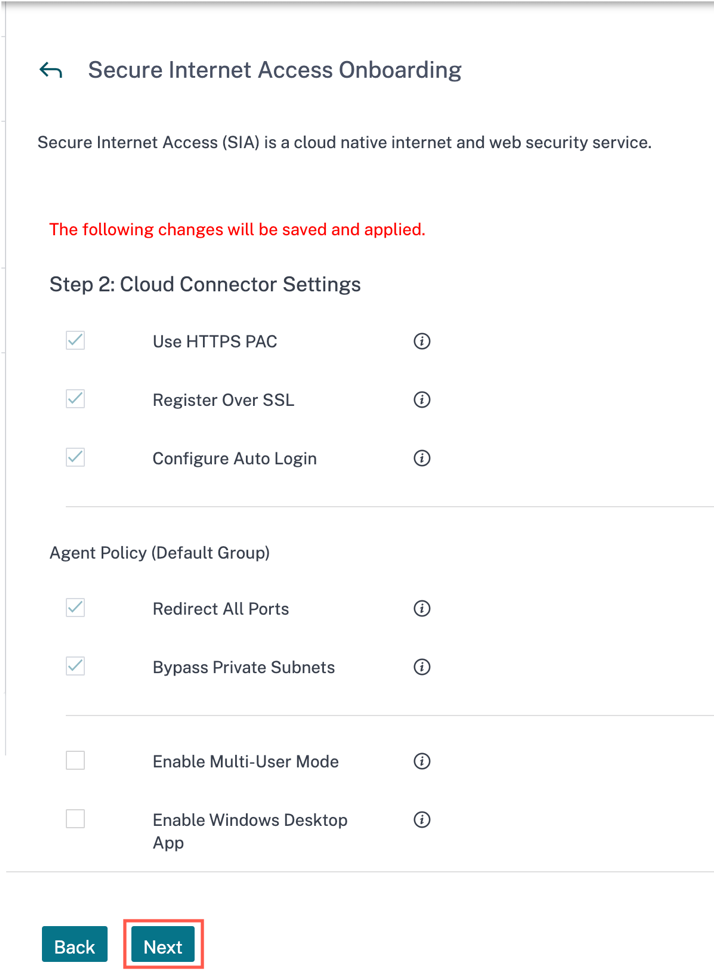
Use HTTPS PAC, Register Over SSL, Configure Auto Login, Redirect All Ports, and Bypass Private Subnets settings are enabled by default and cannot be edited.
-
Enable Multi-User mode: Check/Uncheck the Enable Multi user mode as needed. You can select Enable Multi-User mode to support multiple user sessions when running a virtual desktop or terminal server.
-
Enable Windows Desktop App: Check/Uncheck the Enable Windows Desktop App as needed. The Enable Windows Desktop Application installs an interactive desktop application on Windows devices.
Click Next.
-
-
Configure Security Settings
In Security Settings page configure Web Security, Cloud Access Security Broker, Malware Defense and Intrusion Prevention settings (available in Advanced and Premium SKUs), and Data Loss Prevention (available in Premium SKUs).
-
Web Security
- Show Groups: View the first 20 groups list.
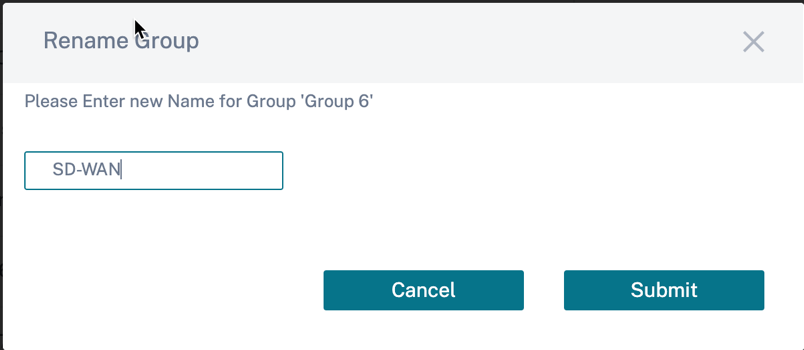
You can edit the names of the group, for example department/domain/product and so on. Click the edit option next to the group name > enter the group name > click Submit.
Upon selection of a group, the pre-defined group policy is applied on the user. The Default group is a non-editable group.
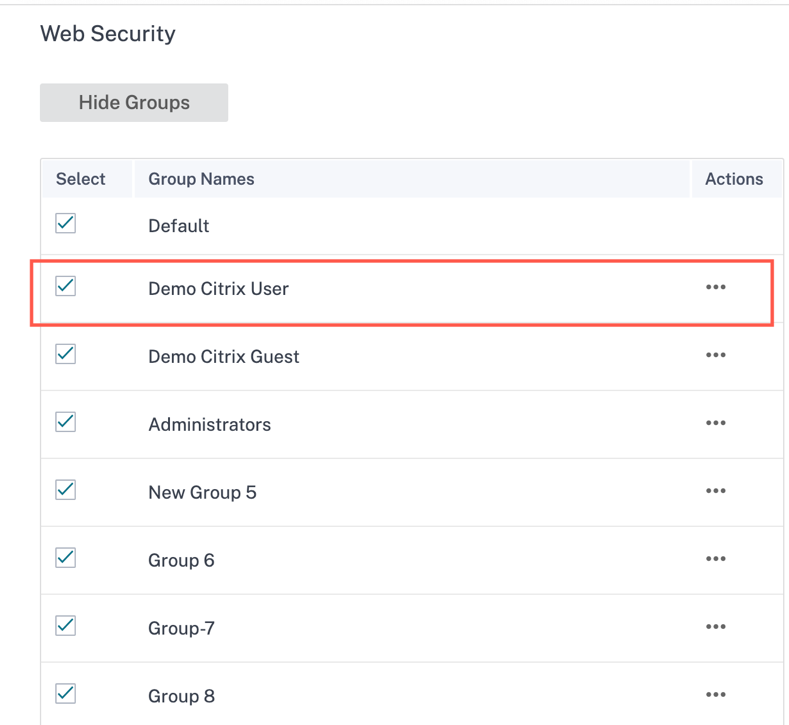
All these 20 groups are checked by default. You can check/uncheck the groups as required. The changes you make to the security settings are applied to the selected group.
-
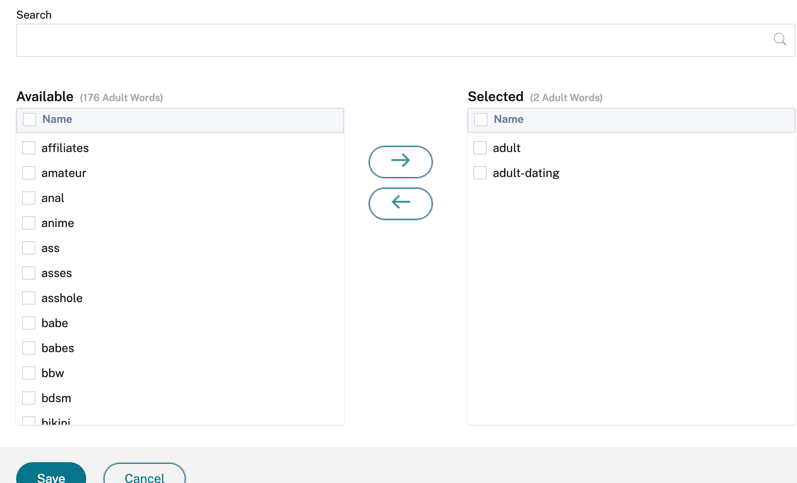
Block Default Keywords: Select the Adult and High Risk check boxes to block the defined keywords. The Edit option helps you to configure the set of keywords that you want to block.
Click Edit > Select Adult Words/Select High Risk Words > select the available keywords and move them to selected section and click Save.
The search bar helps to quickly find the keyword you are looking for.
-
Web Filtering Level: Select the Web Filtering Level to Allow All, Lenient, Moderate, or Strict profile. These filtering levels are defined based on some pre-set categories as described in the below table:
Category Lenient Moderate Strict Adult Blocked Blocked Blocked Computing and Internet Some blocked Some blocked Blocked Gambling Blocked Blocked Blocked Illegal and harmful content Blocked Blocked Blocked Malware and Spam Blocked Blocked Blocked Business and Industry, Finance Allowed Blocked Blocked Email, Messaging, Chat, Telephony Allowed Blocked Blocked News, Entertainment, and Society Allowed Some blocked Blocked Social Networking Allowed Blocked Blocked 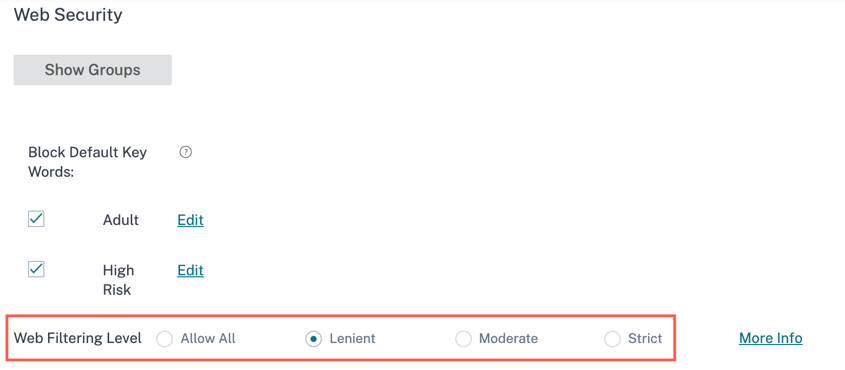
Click More Info link to view the web filtering level information.
-
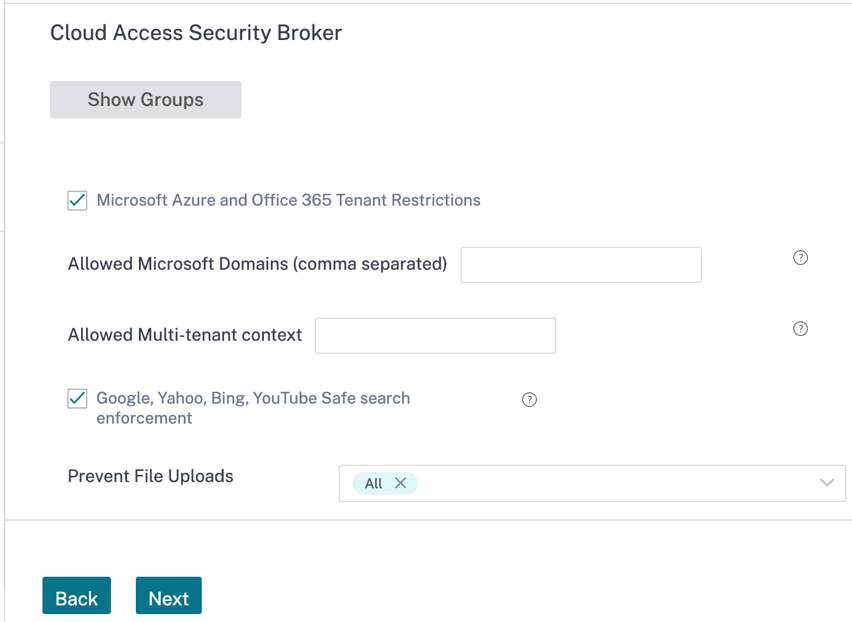
Cloud Access Security Broker: Provides the ability to block file uploads to various services, enforce safe search through various search engines such as Google/Yahoo/Bing and so on.
If the Microsoft Azure and Office 365 Tenant Restriction check box is selected, specify the allowed domain names and multitenant context to apply the security settings.
Select the location (All/Dropbox/Box/OneDrive/Google Drive/Generic File Uploads/None) from the Prevent File Uploads drop-down list to prevent uploading the files. By default All is selected.
In Citrix Secure Internet Access, there are three different SKUs available – Standard, Advanced, and Premium.
In Citrix Secure Internet Access GUI:
-
The Malware Defense and Intrusion Prevention settings option is only available for the customers who have Advanced and Premium SKUs.
-
The Data Loss Prevention (DLP) option is only available for the customers who have Premium SKUs.
For Standard plan, the Malware Defense and Intrusion Prevention settings and Data Loss Prevention (DLP) options are not available in Citrix Secure Internet Access UI.
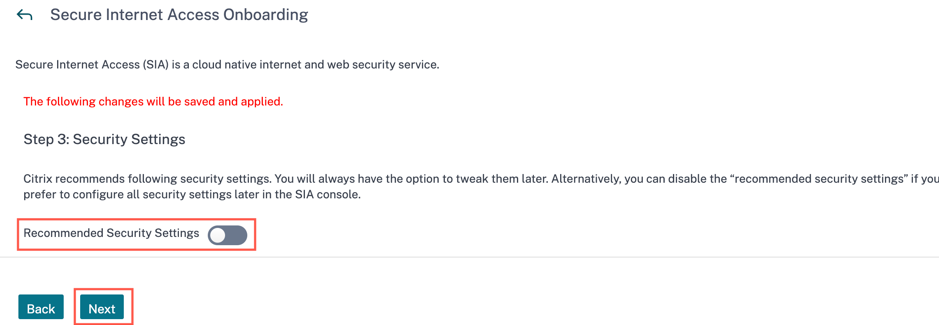
By default all the options are pre-checked for both Malware Defense and Intrusion Prevention settings and Data Loss Prevention (DLP). You can reset the settings or select the options as needed. Click Next.
Alternatively, if you want to skip the Security Settings configuration, you can disable the Recommended Security Settings button. You can configure the settings later in CSIA console.
In this scenario, click Next and review the settings that you made and click Finish to save the changes.
-
-
You can view the summary page with all your settings that you set to complete the onboarding process.
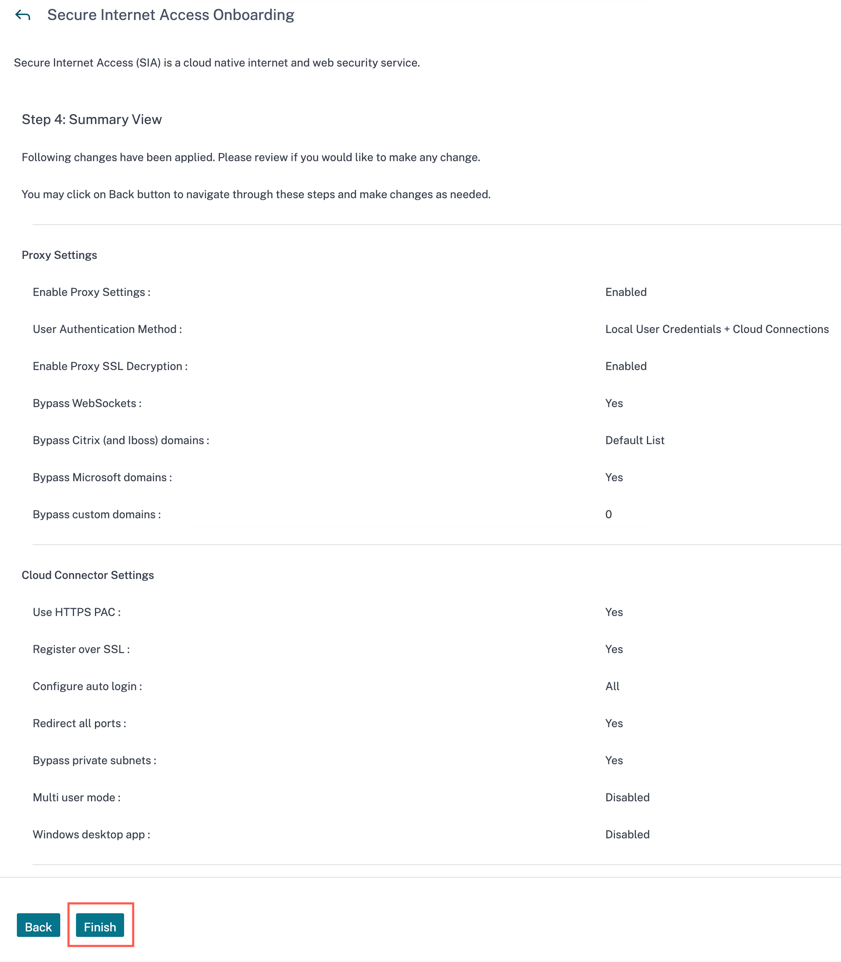
Click Finish, a popup is shown to confirm that you have successfully completed the onboarding settings. Click OK.
Also, an email is sent to all Citrix Cloud administrators who have been added under this customer account for Citrix Internet Secure Access service.
Once the onboarding is completed, navigate to Configuration > Network Configuration Home > Open Citrix SIA Configuration > select Connect Device to Cloud. In this page, you can follow the instruction to download/install Cloud Connector matching to the end-device OS.
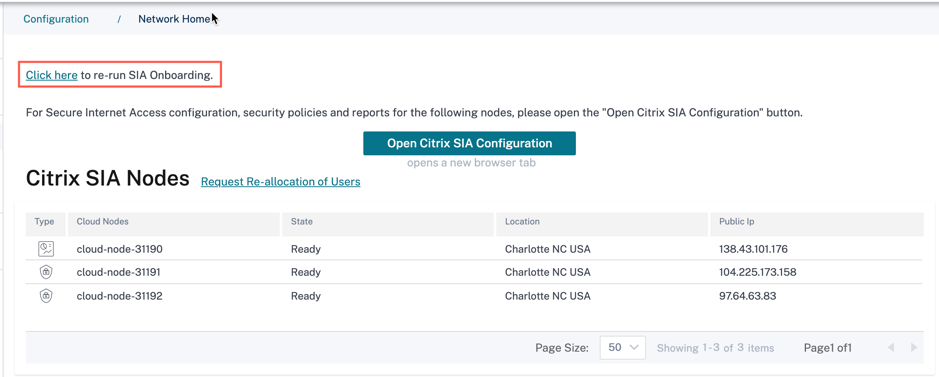
You can rerun the onboarding process from Configuration > Network Configuration Home page. If you missed out any settings, you can always go back and rerun the onboarding process to restore default/recommended settings.
What’s next?
- View the status of the nodes in your network. See Dashboard.
- View details about your subscribed license entitlements. See View licensing details.
- Configure CSIA Cloud Connector agents on Virtual Delivery Agents (VDA) and local host systems. See Configure Citrix Secure Internet Access Cloud Connector agents.
- Configure tunnels for your branch office if you also have a Citrix SD-WAN deployment. See Configure tunnels for branch office.
- Use the Citrix Secure Internet Access configuration policy portal to configure cloud connectors and security features and to monitor reports and logs. See Configuration.