Citrix Secure Access auto log on for Windows Azure AD joined machines
Auto log on to NetScaler Gateway virtual server
Citrix Secure Access client can perform SSO to NetScaler Gateway virtual server using PRT and auto-connect the user to the NetScaler Gateway URL mentioned in the AlwaysOnURL registry. For more information, see NetScaler Gateway Windows VPN client registry keys.
Admin must configure the following to enable SSO to NetScaler Gateway virtual server using PRT:
-
Microsoft Entra ID must be configured as the SAML IdP.
-
NetScaler Gateway must be configured as the SAML SP.
-
Citrix Secure Access client must be configured in Always On or Always On service mode.
To configure Citrix Secure Access client to perform SSO using PRT, you must complete the following steps:
-
Join the windows machine to Azure Entra ID. Admin must visit the following url and join the windows machine:
-
Configure NetScaler Gateway as SAML SP and Microsoft Entra ID as SAML IdP. For more information, see Configure Microsoft Entra ID as SAML IdP and NetScaler as SAML SP.
-
Configure Citrix Secure Access client in Always On and Always On service mode. For more information, see Always On VPN before Windows Logon (formally Always On service) and Always On.
Users must use their credentials and login for the first time. During subsequent system reboots, Citrix Secure Access client auto-connects the user to NetScaler Gateway virtual server using PRT.
Auto log on to the Secure Private Access service
Citrix Secure Access client can perform SSO to Secure Private Access service using PRT. This works when the client is configured in Always On or Always On service mode.
To configure Citrix Secure Access client to perform SSO using PRT, you must complete the following steps:
-
Join the windows machine to Azure Entra ID. Admin must visit the following url and join the windows machine:
-
Log in to the Citrix Cloud account.
-
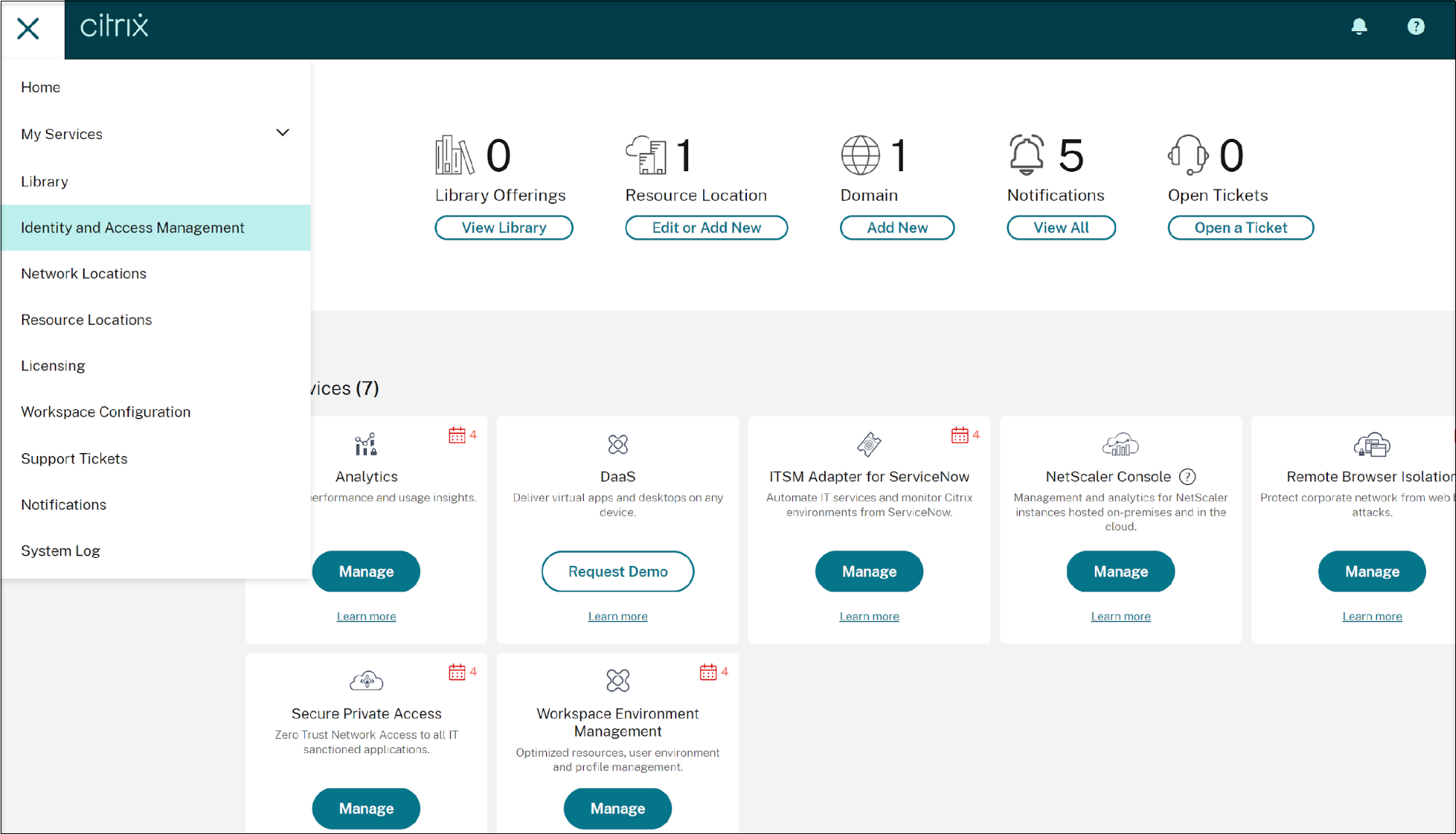
Click the hamburger icon and navigate to Identity and Access Management.
-
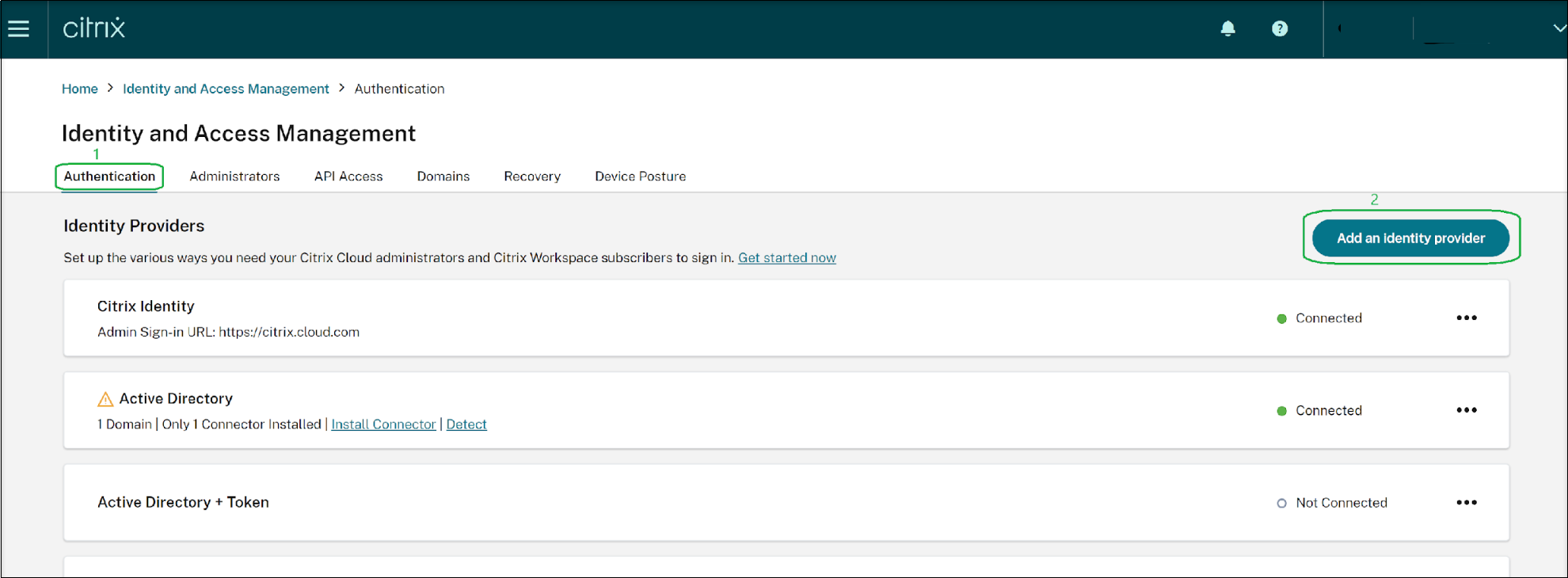
On the Identity and Access Management screen, click the Authentication tab and then click the Add an Identity provider button.
-
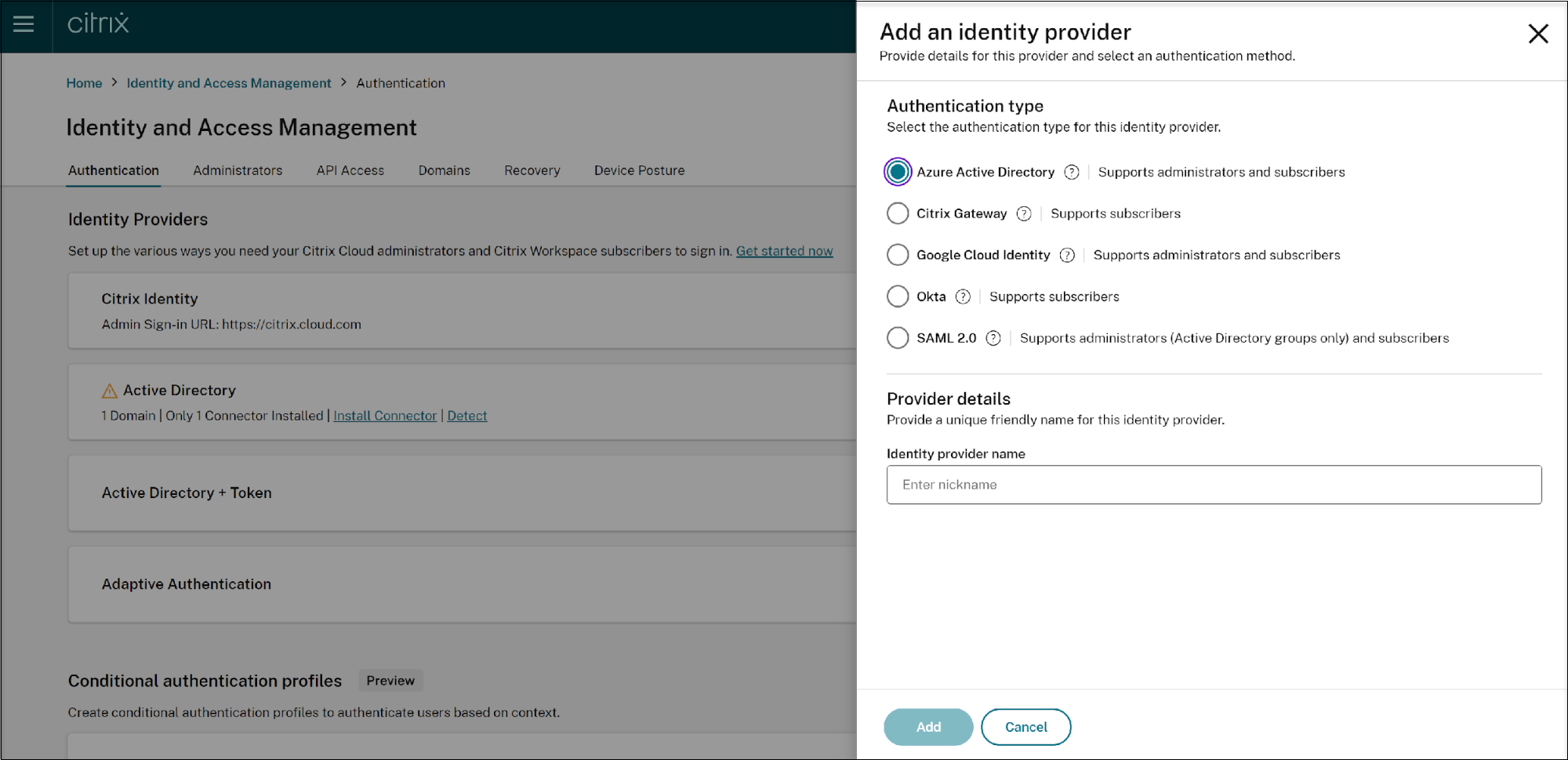
Select the authentication type as Azure Active Directory, provide a name to the identity provider in the Identity Provider name text box, and click the Add button.
-
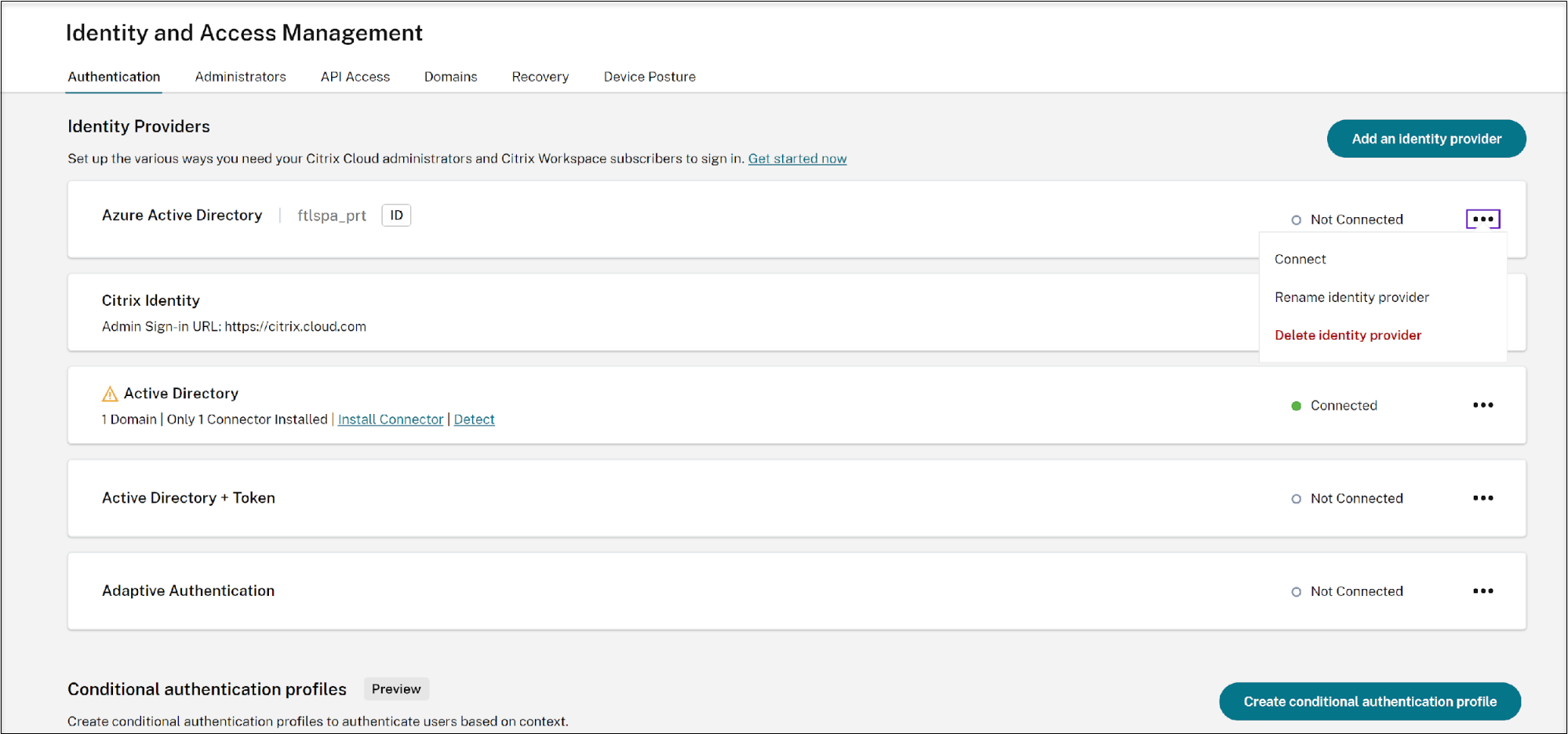
Azure Active Directory is listed on the identity providers list as shown below. Click Connect.
-
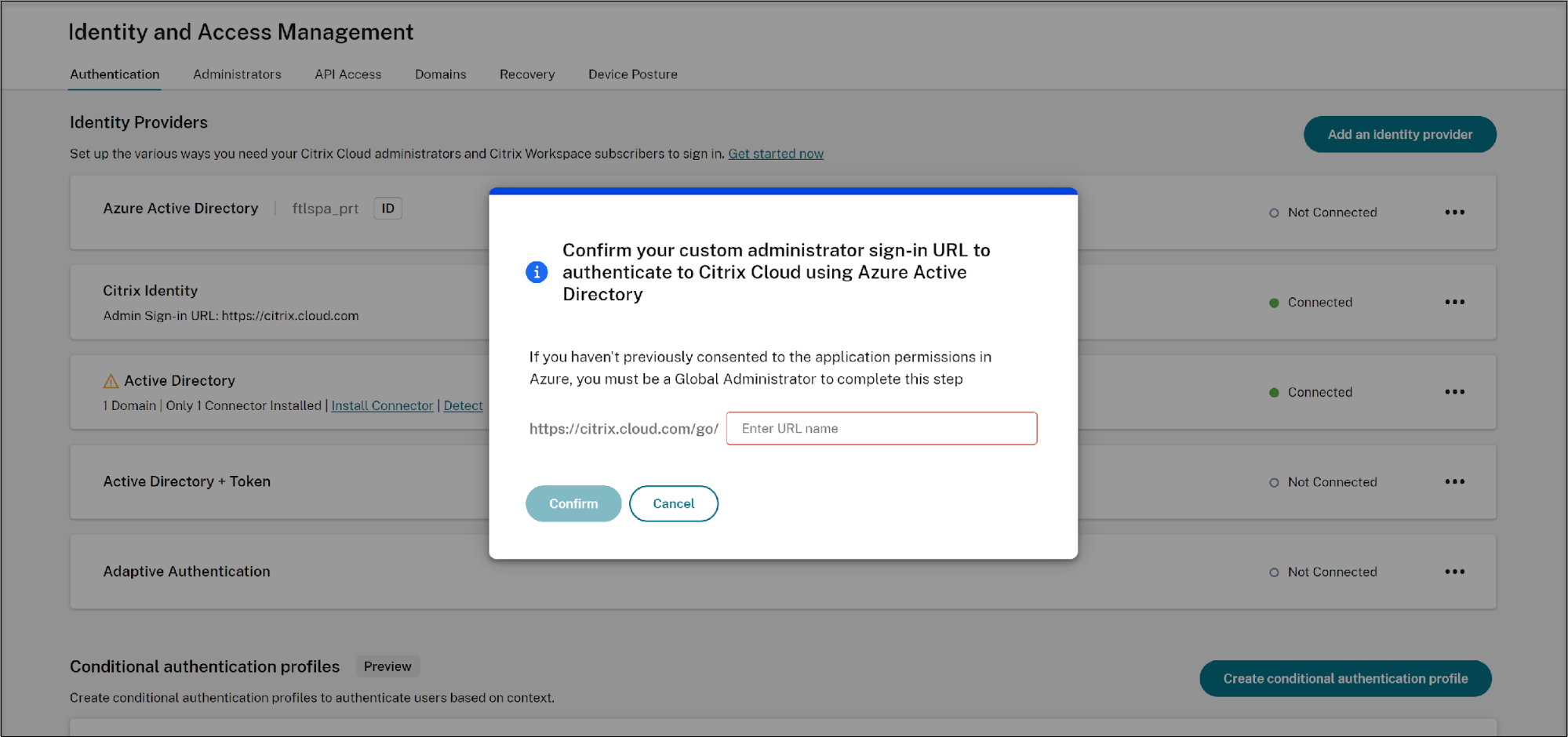
On the connect screen, enter the URL name and click the Confirm button.
-
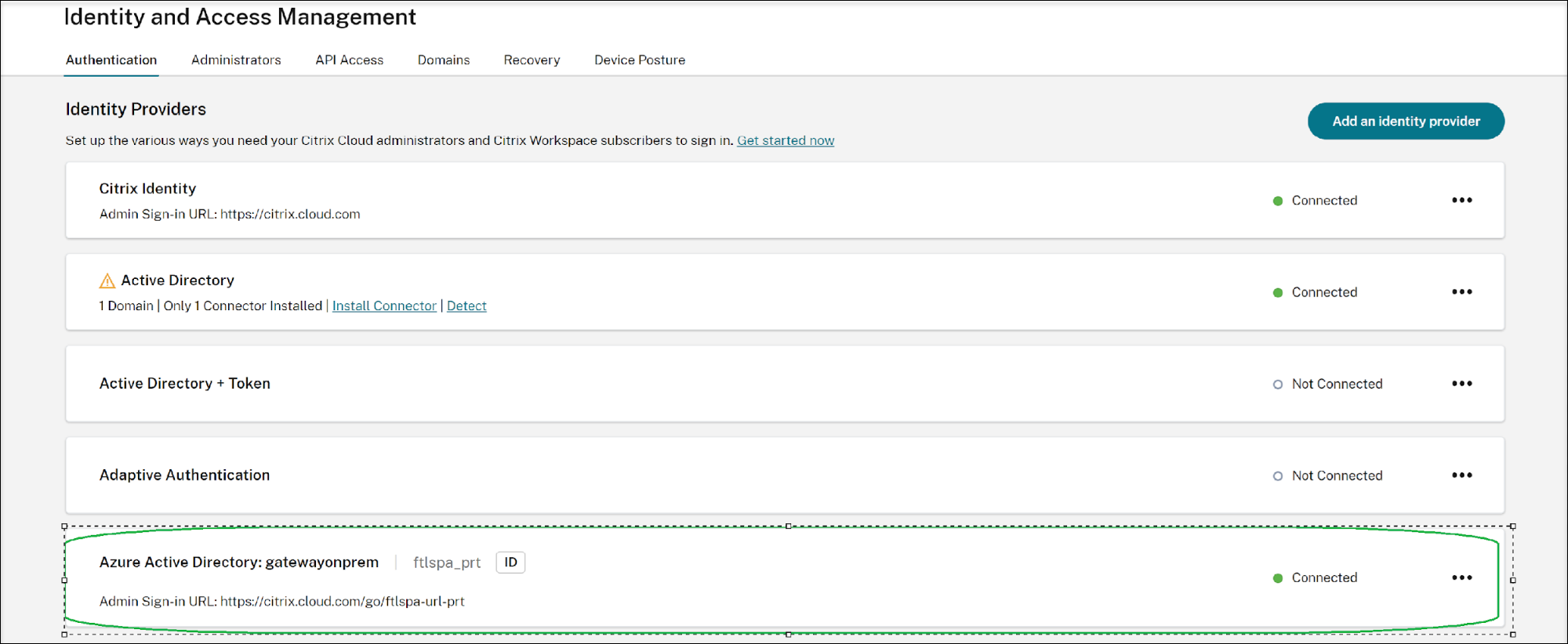
Admin is redirected to the Microsoft sign-in page. Sign in using an Azure Entra ID user account. Once login succeeds, Azure Active Directory shows as connected.
-
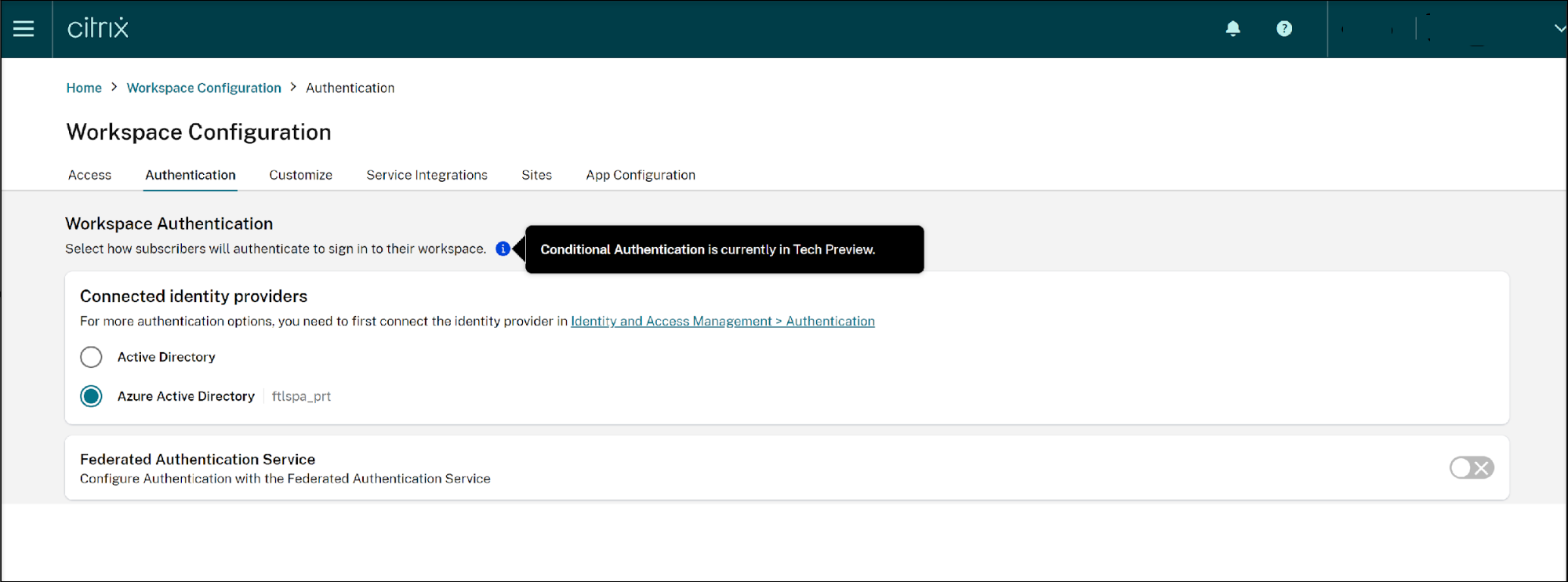
Go back to Workspace Configuration, click the Authentication tab, and select Azure Active Directory.
-
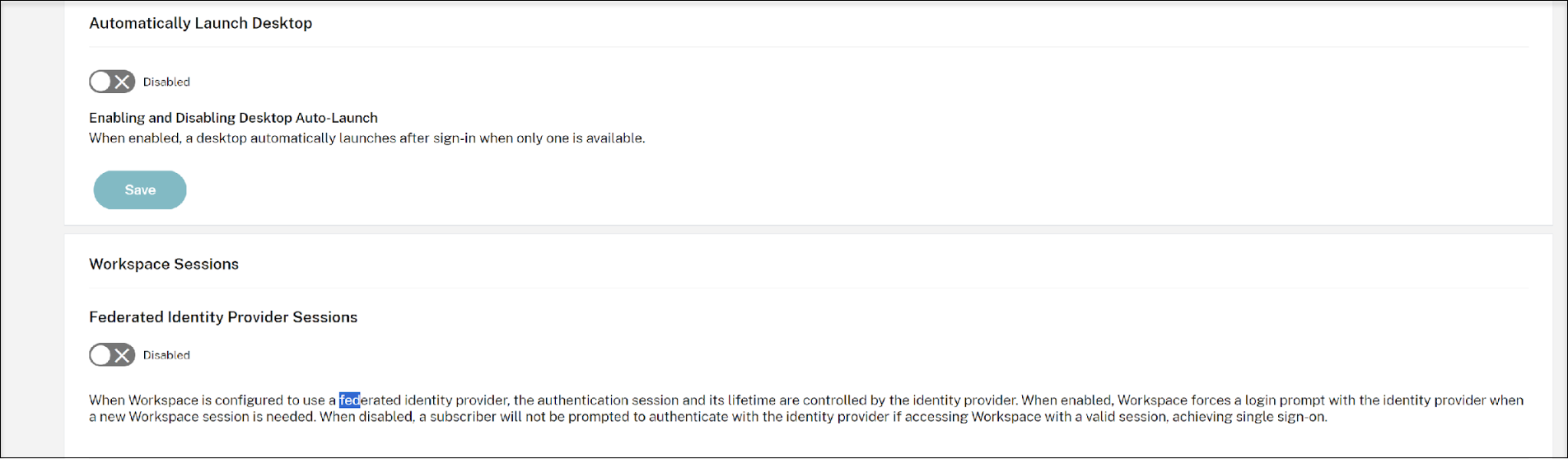
Navigate to Workspace Configuration -> customize -> preferences and deselect the checkbox below Federated Identity Provider Sessions to disable Federated Authentication Service.
Users must use their credentials and login for the first time. During subsequent system reboots, the Citrix Secure Access client auto-connects the user to Secure Private Access using PRT.