Set up Citrix Secure Access in an Intune Android Enterprise environment
Important:
Citrix SSO for Android is now called Citrix Secure Access. We are updating our documentation and the UI screenshots to reflect this name change.
The topic captures details about deploying and configuring Citrix Secure Access through Microsoft Intune. This document assumes that Intune is already configured for Android Enterprise support and device enrollment is already done.
Prerequisites
- Intune is configured for Android Enterprise Support
- Device enrollment is complete
To set up Citrix Secure Access in an Intune Android Enterprise environment
- Add Citrix Secure Access as a managed app
- Configure managed app policy for Citrix Secure Access
Add Citrix Secure Access as a managed app
-
Log in to your Azure portal.
-
Click Intune on the left navigation blade.
-
Click Client Apps in the Microsoft Intune blade and then click Apps in the Client apps blade.
-
Click +Add link in the top right menu options. The Add app configuration blade appears.
-
Select Managed Google Play for the app type.
This adds Manage Google Play search and approve blade if you have configured Android Enterprise.
-
Search for Citrix Secure Access and select it from the list of apps.

Note: If Citrix Secure Access does not appear in the list, it means that the app is not available in your country.
-
Click APPROVE to approve Citrix Secure Access for deployment through Managed Google Play store.
The permissions that are required by the Citrix Secure Access are listed.
-
Click APPROVE to approve the app for deployment.
-
Click Sync to sync this selection with Intune.
Citrix Secure Access is added to the Client apps list. You might have to search for the Citrix Secure Access if there are many apps added.
-
Click Citrix Secure Access app to open the app details blade.
-
Click Assignments in the details blade. Citrix Secure Access - Assignments blade appears.
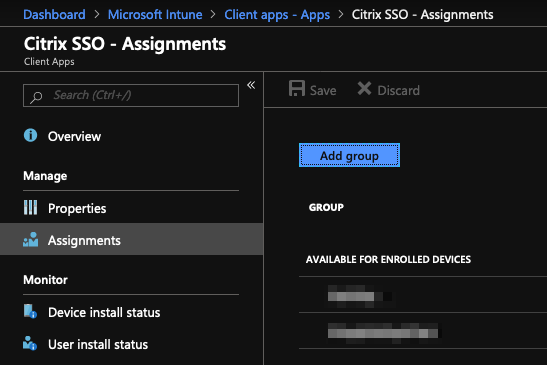
-
Click Add group to assign the user groups to which you want to give permission to install Citrix Secure Access, and click Save.
-
Close the Citrix Secure Access details blade.
Citrix Secure Access is added and enabled for deployment to your users.
Configure managed app policy for Citrix Secure Access
After Citrix Secure Access is added, you must create a managed configuration policy for Citrix Secure Access so that the VPN profile can be deployed to Citrix Secure Access on the device.
-
Open the Intune blade in your Azure portal.
-
Open Client Apps blade from the Intune blade.
-
Select App configuration policies item from the Client apps blade and click Add to open the Add configuration policy blade.
-
Enter a name for the policy and add a description for it.
-
In Device enrollment type, select Managed devices.
-
In Platform, select Android.
This adds another configuration option for the associated app.
-
Click Associated app and select Citrix Secure Access app.
You might have to search for it if you have many apps.
-
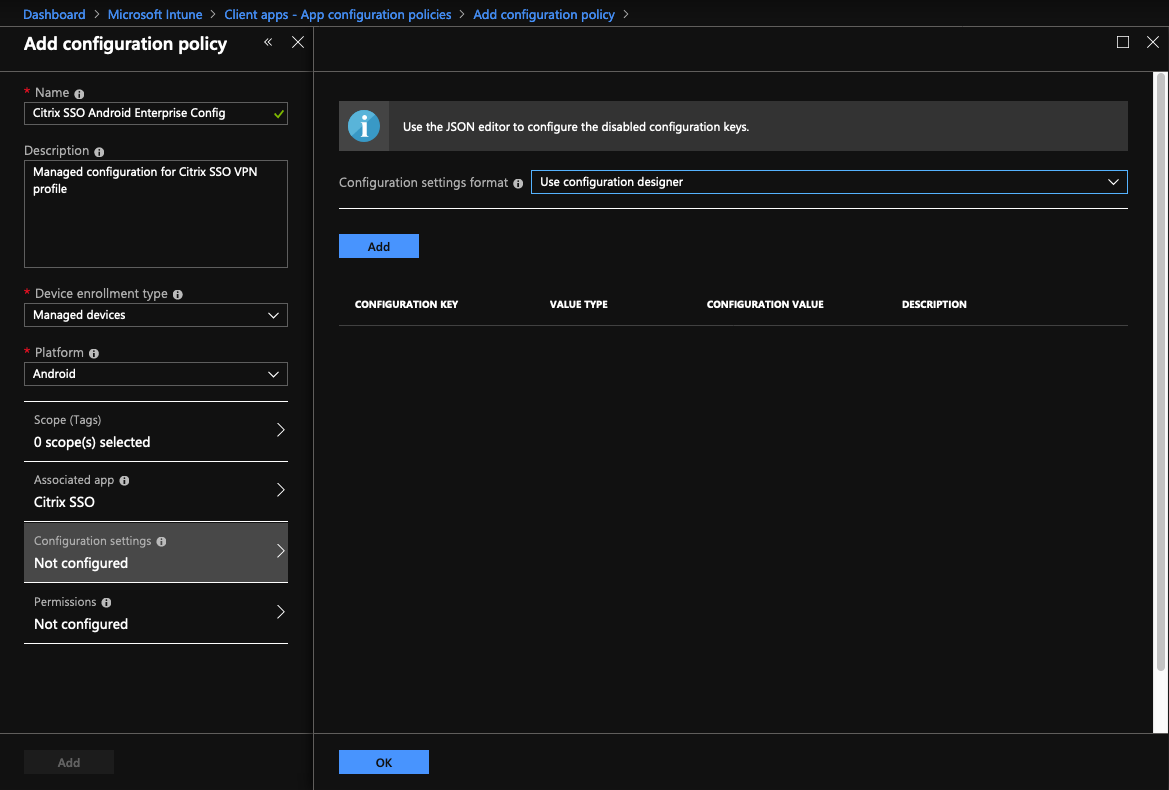
Click OK. A configuration settings option is added in the Add configuration policy blade.
-
Click Configuration settings.
A blade to configure Citrix Secure Access appears.
-
In Configuration Settings, select either Use configuration designeror Enter JSON data to configure the Citrix Secure Access.
Note:
For simple VPN configurations it is recommended to use the configuration designer.
VPN configuration using configuration designer
-
In Configuration Settings, select Use configuration designer and Click Add.
You are presented with a key value entry screen for configuring various properties that are supported by Citrix Secure Access. At a minimum you must configure the Server Address and VPN Profile Name properties. You can hover over the DESCRIPTION section to get more information about each property.
-
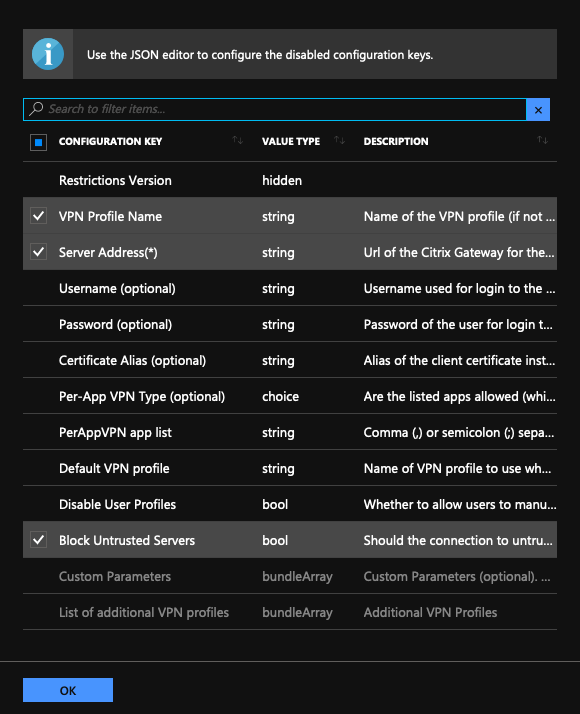
For example, select VPN Profile Name and Server Address(*) properties and click OK.
This adds the properties to the configuration designer. You can configure the following properties.
-
VPN Profile Name. Type a name for the VPN profile. If you are creating more than one VPN profile, use a unique name for each. If you do not provide a name, the address you enter in the Server Address field is used as the VPN profile name.
-
Server Address(*). Type your NetScaler Gateway base FQDN. If your NetScaler Gateway port is not 443, also type your port. Use URL format. For example,
https://vpn.mycompany.com:8443. -
Username (optional). Enter the user name that the end users use to authenticate to the NetScaler Gateway. You can use the Intune config value token for this field if the gateway is configured to use it (see config value tokens.) If you do not provide a user name, users are prompted to provide a user name when they connect to NetScaler Gateway.
-
Password (optional). Enter the password that end users use to authenticate to the NetScaler Gateway. If you do not provide a password, users are prompted to provide a password when they connect to NetScaler Gateway.
-
Certificate Alias (optional). Provide a certificate alias in the Android KeyStore to be used for client certificate authentication. This certificate is pre-selected for users if you are using certificate-based authentication.
-
Gateway Certificate Pins (optional). JSON object describing certificate pins used for NetScaler Gateway. Example value:
{"hash-alg" : "sha256", "pinset" : ["AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA=", "BBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBB="]}. For details, see NetScaler Gateway certificate pinning with Android Citrix Secure Access. -
Per-App VPN Type (optional). If you are using a per-app VPN to restrict which apps use this VPN, you can configure this setting.
- If you select Allow, network traffic for app package names listed in the PerAppVPN app list is routed through the VPN. The network traffic of all other apps is routed outside the VPN.
- If you select Disallow, network traffic for app package names listed in the PerAppVPN app list are routed outside the VPN. The network traffic of all other apps is routed through the VPN. Default is Allow.
- PerAppVPN app list. A list of apps whose traffic is allowed or disallowed on the VPN, depending on the value of Per-App VPN Type. List the app package names separated by commas or semicolons. App package names are case sensitive and must appear on this list exactly as they appear in the Google Play store. This list is optional. Keep this list empty for provisioning device-wide VPN.
- Default VPN profile. The VPN profile name used when Always On VPN is configured for Citrix Secure Access. If this field is empty, the main profile is used for the connection. If only one profile is configured, it is marked as the default VPN profile.
-
Always On VPN (optional): When set to True, it indicates that the VPN profile is an Always On VPN profile. This property can be set only for the main VPN profile. It cannot be set for the additional VPN profiles. By default, this property is set to False.
Note:
The
Always On VPN (optional)property is available from Citrix Secure Access for Android 24.04.1 onwards.
Note:
-
For making Citrix Secure Access as an Always On VPN app in Intune, use VPN provider as custom and
com.citrix.CitrixVPNas the app package name. -
Only certificate-based client authentication is supported for Always On VPN by Citrix Secure Access.
-
Admins must select Client Authentication and set Client Certificate to Mandatory in the SSL Profile or SSL Properties on the NetScaler Gateway for Citrix Secure Access to work as intended.
-
Disable User Profiles
- If you set this value to true, users cannot add new VPN profiles on their devices.
- If you set this value to false, users can add their own VPNs on their devices.
The default value is false.
-
Block Untrusted Servers
- Set this value to false when using a self-signed certificate for NetScaler Gateway or when the root certificate for the CA issuing the NetScaler Gateway certificate is not in the system CA list.
- Set this value to true to enable the Android operating system validate the NetScaler Gateway certificate. If the validation fails, the connection is not allowed.
The default value is true.
-
-
For the Server Address(*) property, enter your VPN gateway base URL (for example,
https://vpn.mycompany.com). -
For VPN Profile Name, enter a name that is visible to the end user in the Citrix Secure Access client’s main screen (for example, My Corporate VPN).
-
You can add and configure other properties as appropriate to your NetScaler Gateway deployment. Click OK when you are done with configuration.
-
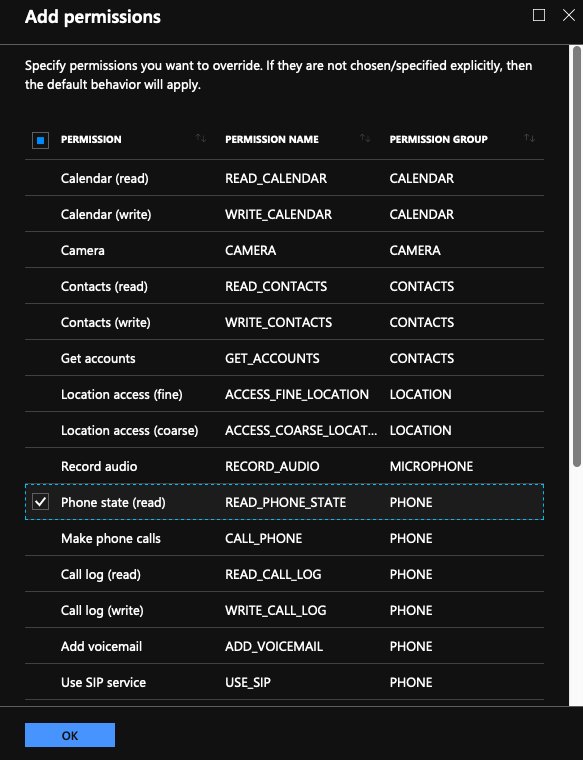
Click the Permissions section. You can grant the following permissions required by Citrix Secure Access:
-
If you are using the Intune NAC check, Citrix Secure Access requires that you grant Phone state (read) permission. Click Add button to open permissions blade. Currently, Intune displays a significant list of permissions that are available to all the apps.
-
If you are using Intune NAC check, select Phone state (read) permission and click OK. This adds it to the list of permissions for the app. Select either Prompt or Auto grant so that the Intune NAC check can work and click OK.
-
You are advised to autogrant notifications permissions to Citrix Secure Access.
Note:
For Android 13+ users using Citrix Secure Access 23.12.1 and above, MDM admins are advised to grant the notification permission to Citrix Secure Access (package ID:
com.citrix.CitrixVPN) in their solution. -
-
Click Add at the bottom of the App configuration policy blade to save the managed configuration for Citrix Secure Access.
-
Click Assignments in the App configuration policy blade to open the Assignments blade.
-
Select the user groups for which you want this Citrix Secure Access configuration to be delivered and applied.
VPN configuration by entering JSON data
-
In Configuration Settings, select Enter JSON data for configuring the Citrix Secure Access.
-
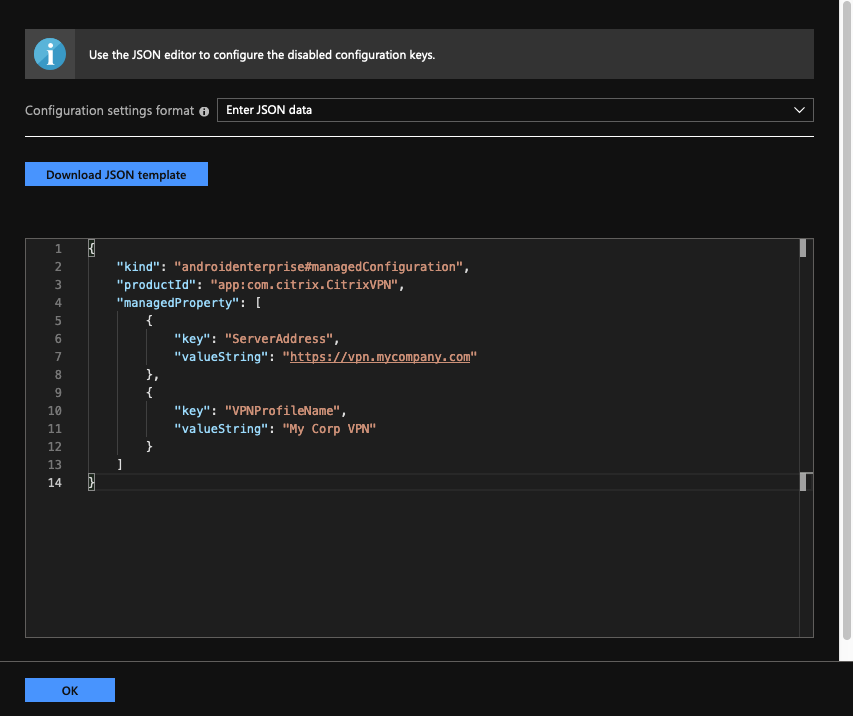
Use the Download JSON template button to download a template that allows for providing more detailed/complex configuration for Citrix Secure Access. This template is a set of JSON key-value pairs to configure all the possible properties that Citrix Secure Access understands.
For a list of all the available properties that can be configured, see Available properties for configuring VPN profile in Citrix Secure Access app.
-
Once you have created a JSON configuration file, copy and paste its contents in the editing area. For example, the following is the JSON template for basic configuration created previously using the configuration designer option.
This completes the procedure for configuring and deploying VPN profiles for Citrix Secure Access in the Microsoft Intune Android Enterprise environment.
Important:
Certificate used for client certificate-based authentication is deployed using an Intune SCEP profile. The alias for this certificate must be configured in the Certificate Alias property of the managed configuration for Citrix Secure Access.
Available properties for configuring VPN profile in Citrix Secure Access
| Configuration Key | JSON Field Name | Value Type | Description |
|---|---|---|---|
| VPN Profile Name | VPNProfileName | Text | Name of the VPN profile (if not set defaults to server address). |
| Server Address(*) | ServerAddress | URL | Base URL of the NetScaler Gateway for the connection (https://host[:port]). This is a required field. |
Username (optional) |
Username | Text | User name used for authenticating with the NetScaler Gateway (optional). |
| Password (optional) | Password | Text | Password of the user for authenticating with the NetScaler Gateway (optional). |
| Certificate Alias (optional) | ClientCertAlias | Text | Alias of the client certificate installed in the Android credential store for use in certificate-based client authentication (optional). Certificate alias is a required field when using certificate-based authentication on NetScaler Gateway. |
| Gateway Certificate Pins (optional) | ServerCertificatePins | JSON Text | Embedded JSON object describing certificate pins used for NetScaler Gateway. Example value: {"hash-alg" : "sha256", "pinset" : ["AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA=", "BBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBB="]}. Make sure to escape this embedded JSON data when using the JSON configurator. |
| Per-App VPN Type (optional) | PerAppVPN_Allow_Disallow_Setting | Enum (Allow, Disallow) | Are the listed apps allowed (allow list) or disallowed (block list) to use the VPN tunnel. If set to Allow, only listed apps (in the PerAppVPN app list property) are allowed to tunnel through the VPN. If set to Disallow, all apps except the listed ones are allowed to tunnel through the VPN. If no apps are listed the all apps are allowed to tunnel through the VPN. |
| PerAppVPN app list | PerAppName_Appnames | Text | Comma (,) or semicolon (;) separated list of app package names for per-app VPN. The package names must be the same as they appear in the Google Play store app listing page URL. Package names are case sensitive. |
| Default VPN profile | DefaultProfileName | Text | Name of the VPN profile to use when the system starts the VPN service. This setting is used for identifying the VPN profile to use when Always On VPN is configured on the device. |
| Always On VPN (optional)
|
IsAlwaysOnVpn
|
Boolean
|
Determines whether the VPN profile is an Always ON VPN profile or not. When set to True, it indicates that the VPN profile is an Always On VPN profile. This property can be set only on the main VPN profile. It cannot be set for the additional VPN profiles. Default value is False. |
| This property is available from starting from Citrix Secure Access for Android 24.04.1 release onwards. | |||
| Disable User Profiles | DisableUserProfiles | Boolean | Property to allow or not allow the end users to manually create VPN profiles. Set this value to true to disable users from creating VPN profiles. Default value is false. |
| Block Untrusted Servers | BlockUntrustedServers | Boolean | Property to determine if the connection to untrusted gateways (for example, using self-signed certificates or when issuing CA is not trusted by the Android operating system) be blocked? Default value is true (block connections to untrusted gateways). |
| Custom Parameters (optional) | CustomParameters | List | List of custom parameters (optional) that are supported by Citrix Secure Access. For details, see Custom Parameters. Check the NetScaler Gateway product documentation for available options. |
| List of other VPN profiles | bundle_profiles | List | List of other VPN profiles. Most of the previously mentioned values for each profile are supported. For details, see Properties supported for each VPN in VPN Profile List. |
Custom Parameters
Each custom parameter must be defined using the following key-value names.
| Key | Value Type | Value |
|---|---|---|
| ParameterName | Text | Name of the custom parameter. |
| ParameterValue | Text | Value of the custom parameter. |
Custom Parameters for Intune configuration
| Parameter name | Description | Value |
|---|---|---|
| UserAgent | Citrix Secure Access appends this parameter value to the user-agent HTTP header, when communicating with NetScaler Gateway, to perform an additional check on NetScaler Gateway. | Specify the text that you need to append to the user-agent HTTP header. The text must conform to the HTTP user-agent specifications. |
| EnableDebugLogging | Enable debug logging on Citrix Secure Access to help troubleshoot VPN connectivity issues in case of Always On VPN. You can enable it in any one of the managed VPN configurations. The debug logging takes effect when the managed configurations are processed. | True: Enables debug logging. Default value: False. |
For more information about the custom parameters, see Create an Android Enterprise managed configuration for Citrix Secure Access.
Properties supported for each VPN in VPN Profile List
Following properties are supported for each of the VPN profile when configuring multiple VPN profiles using the JSON template.
| Configuration Key | JSON Field Name | Value Type |
|---|---|---|
| VPN Profile Name | bundle_VPNProfileName | Text |
| Server Address(*) | bundle_ServerAddress | URL |
| User name | bundle_Username | Text |
| Password | bundle_Password | Text |
| Client Cert Alias | bundle_ClientCertAlias | Text |
| Gateway Certificate Pins | bundle_ServerCertificatePins | Text |
| Per-App VPN Type | bundle_PerAppVPN_Allow_Disallow_Setting | Enum (Allow, Disallow) |
| PerAppVPN app list | bundle_PerAppVPN_Appnames | Text |
| Custom Parameters | bundle_CustomParameters | List |
Set Citrix Secure Access as Always On VPN provider in Intune
In the absence of an on-demand VPN support in an Android VPN subsystem, the Always On VPN can be used as an alternative to provide seamless VPN connectivity option along with client certificate authentication with Citrix Secure Access. The VPN is started by the operating system when it starts up or when the work profile is turned on.
For making Citrix Secure Access an Always On VPN app in Intune, you must use the following settings.
-
Choose the correct type of managed configuration to use (personally owned with work profile OR fully managed, dedicated, and corporate owned work profile).
-
Create a device configuration profile and select Device restrictions and then go to Connectivity section. Select enable for Always On VPN setting.
-
Choose Citrix Secure Access as VPN client. If Citrix Secure Access is not available as an option, you can choose Custom as VPN Client and enter com.citrix.CitrixVPN in the Package ID field (the Package ID field is case sensitive)
-
Leave other options as is. It is recommended not to enable Lockdown mode. When enabled, the device might lose complete network connectivity if VPN is not available.
-
In addition to these settings, you can also set Per-App VPN type and PerAppVPN app list in the App configuration policies page to enable per-app VPN for Android as described in the preceding sections.
Note:
Always On VPN is supported only with client certificate authentication in Citrix Secure Access.
References
Refer to the following topics for more details about setting up connectivity options in Intune.
Automatic restart of Always On VPN
Starting from Citrix SSO for Android 23.8.1, Citrix Secure Access automatically restarts the Always On VPN when an app that is a part of the allow or block list is installed in a work profile or a device profile.Traffic from the newly installed app is automatically tunneled over a VPN connection without restarting the work profile or rebooting the device.
To enable automatic restart of Always On VPN, end users must grant the Query all packages consent to Citrix Secure Access. Once the consent is granted, Citrix Secure Access:
- Receives the package install notification from the operating system.
- Restarts the Always On VPN.
When an end user connects to a per-app VPN profile for the first time, the user is prompted to provide consent (required by Google policies) to collect information of the installed package. If the end user grants the consent, the VPN connection is initiated. If the user denies the consent, the VPN connection is aborted. The consent screen does not reappear once the consent has been granted. For details about the end user instructions, see How to use Citrix Secure Access from your Android device.
Limitations
The following are the limitations for per-app VPN in Android Enterprise environment on Android 11+ devices due to package visibility restrictions introduced in Android 11:
- If an app that is part of the allowed/denied list is deployed to a device after the VPN session has started, the end user must restart the VPN session for the app to be able to route its traffic through the VPN session.
- If per-app VPN is used via an Always On VPN session, then after installing a new app on the device, the end user must restart the work profile or reboot the device for the app’s traffic to be routed via the VPN session.
Note:
These limitations are not applicable if you are using Citrix SSO for Android 23.8.1 or later versions. See Automatic restart of Always On VPN for more details.