Deployment architecture
The Istio service mesh can be logically divided into control plane and data plane components. The data plane is composed of a set of proxies which manage the network traffic between instances of the service mesh. The control plane generates and deploys the configuration that controls the data plane’s behavior.
For detailed information on Istio architecture and different components, see Istio documentation.
NetScaler Integration with Istio control plane components
The Istio control plane is a set of gRPC based services and it pushes configuration changes to clients listening at the data plane. Pilot, Mixer, Galley, and Citadel are important control plane components. Out of these components, the data plane proxy primarily needs to interact with Pilot and Citadel.
Pilot is a gRPC based xDS server and provides configuration data to proxies. NetScaler provides an xDS client called xDS-adapter to communicate with the Istio control plane for installing NetScalers in Istio service mesh. It acts as a gRPC client to the control plane API server and listens to updates. Based on the updates from the control plane, NetScaler xDS adapter generates the equivalent NetScaler configuration. Then, it configures the NetScaler ingress or proxy device accordingly.
Citadel is a control plane service which provides key and certificate management. It is responsible for providing TLS certificates to data plane proxies. NetScaler xDS adapter monitors secrets managed by Citadel, and updates the NetScaler proxy with relevant details.
NetScaler service mesh solution provides a container, NetScaler Metrics Exporter, which collects the statistical data from NetScaler Ingress Gateway device and exports it to Prometheus.
Citrix also provides its own in-house solution NetScaler Observability Exporter for the telemetry purpose. NetScaler CPX running as a sidecar proxy interacts with the NetScaler Observability Exporter. NetScaler CPX sends metrics and transactions to NetScaler Observability Exporter. NetScaler Observability Exporter supports endpoints such as Zipkin and Prometheus, and sends the data collected from sidecar proxies to these endpoints in an appropriate format.
NetScaler can be integrated with Istio in three ways:
- NetScaler CPX, MPX, or VPX as an Ingress Gateway to the service mesh
-
NetScaler CPX as a sidecar proxy with application containers in the service mesh
- NetScaler CPX as an Egress Gateway for the service mesh
All the modes can be combined to have a unified data plane solution.
Deploy NetScaler as an Ingress Gateway
An Istio Ingress Gateway acts as an entry point for the incoming traffic to the service mesh. It secures and controls access to the service mesh from outside. You can deploy a NetScaler CPX, MPX, or VPX as an ingress Gateway to the Istio service mesh.
NetScaler CPX as an Ingress Gateway
The NetScaler CPX Ingress Gateway is deployed as a set of horizontal scaling Kubernetes pods. Each pod runs a NetScaler CPX that controls and routes the incoming requests. Each pod also runs an NetScaler xDS adapter container as a sidecar to the NetScaler. The NetScaler xDS adapter container establishes a connection with Istio control plane components, reads the ingress policies applied, and configures the NetScaler CPX accordingly.
The following diagram shows a sample deployment of NetScaler CPX as an Ingress Gateway.
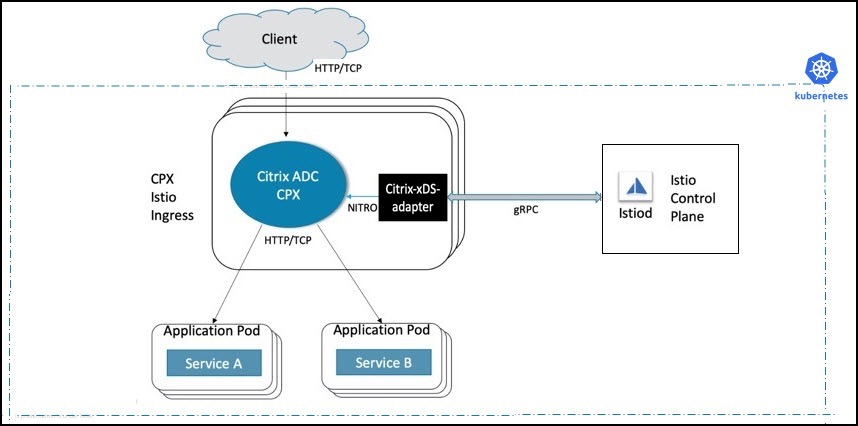
For detailed instructions on how to deploy NetScaler CPX as an Ingress Gateway, see Deploying NetScaler with Istio.
NetScaler MPX or VPX as an Ingress Gateway
NetScaler VPX or MPX can be deployed as an Ingress Gateway to the Istio service mesh. In this deployment, a Kubernetes pod is deployed with an NetScaler xDS adapter container. The NetScaler xDS adapter container connects to the Istio control plane and reads the ingress configuration and then configures the NetScaler VPX or MPX accordingly.
Note: For this deployment, establish the connectivity between the concerned NetScaler and the cluster nodes.
The following diagram shows a sample deployment of NetScaler VPX/MPX as an Ingress Gateway.
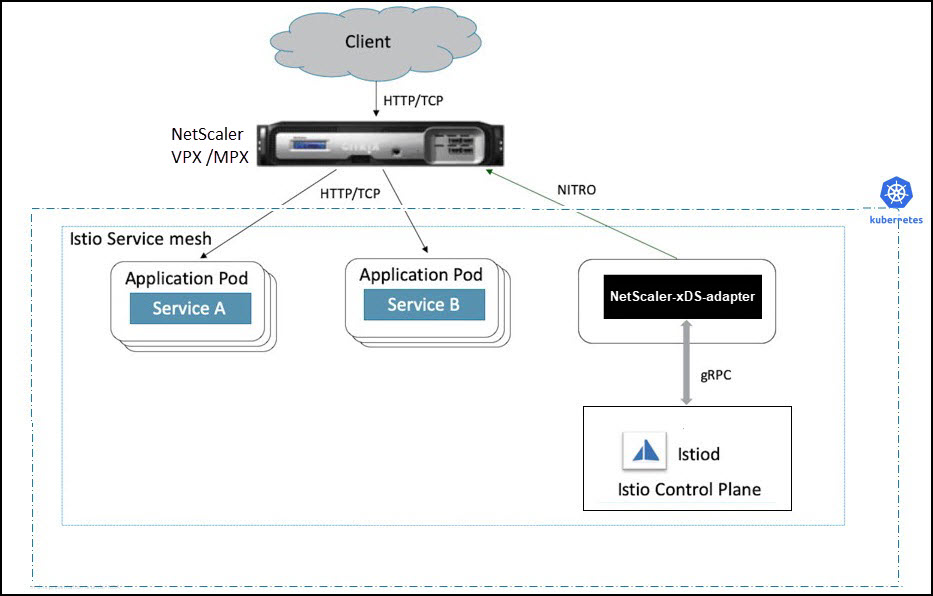
For detailed instructions on how to deploy NetScaler VPX or MPX as an Ingress Gateway, see Deploying NetScaler with Istio.
Deploy NetScaler CPXs as sidecars
NetScaler CPX can be deployed as a sidecar proxy in application pods. It intercepts all the incoming and outgoing traffic from the application pod and applies the configured routing policies or rules.
In this deployment, each application pod contains a NetScaler CPX and an NetScaler xDS adapter container along with the application container.
The NetScaler xDS adapter container listens to updates from the Istio control plane and configures the NetScaler CPX instance accordingly.
The following diagram shows a sample deployment of NetScaler CPXs as sidecars.
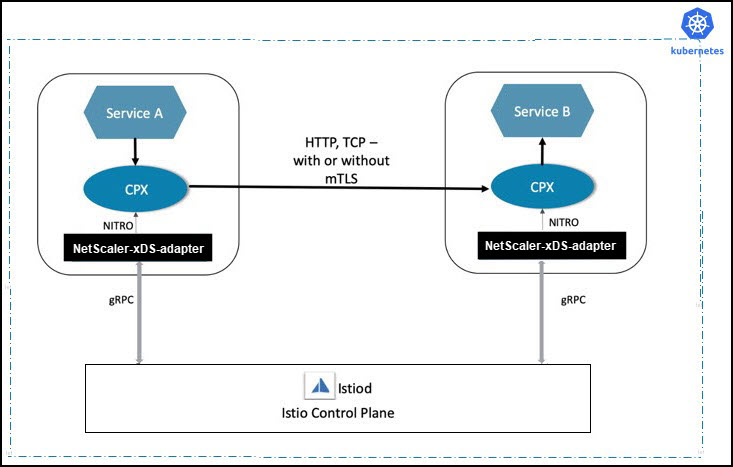
For detailed instructions on how to deploy NetScaler CPX as a sidecar, see Deploying NetScaler with Istio.
Deploy NetScaler CPX as an Egress Gateway
An Egress Gateway defines the traffic exit point from a service mesh. NetScaler CPX as an Egress Gateway performs load balancing, monitoring at the edge of the service mesh, and provides routing rules to exit the service mesh.
The following diagram shows a sample deployment of NetScaler CPX as an Egress Gateway.
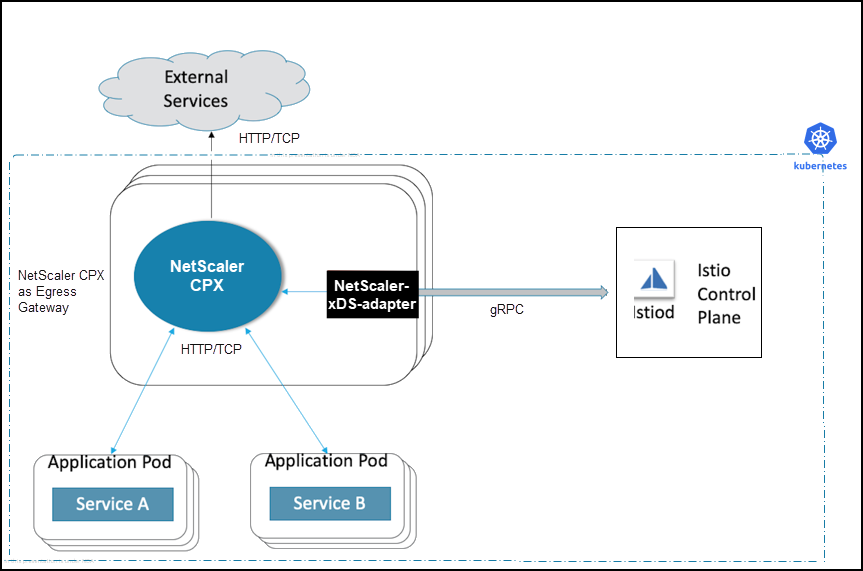
For detailed instructions on how to deploy NetScaler CPX as an Egress Gateway, see Deploying NetScaler with Istio.
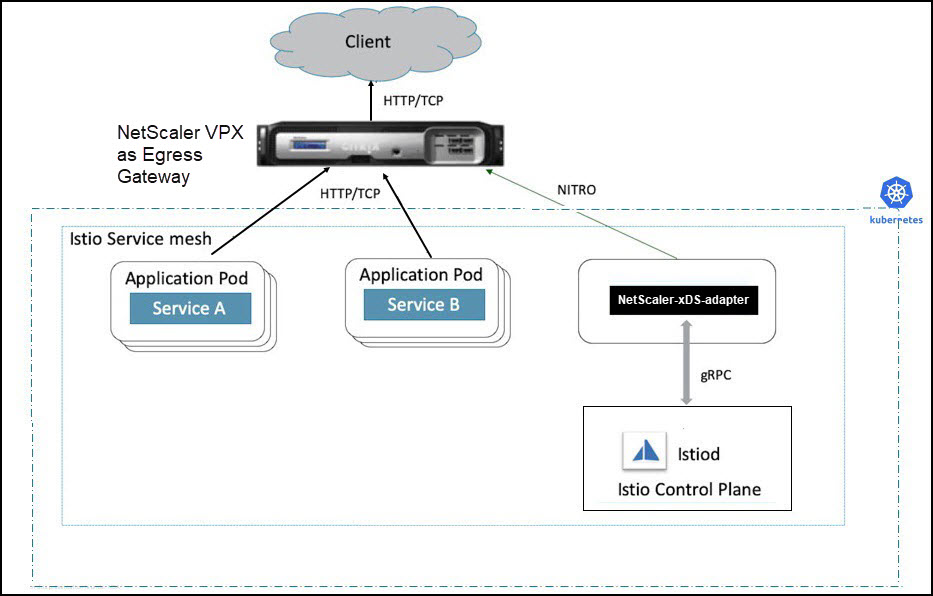
Deploy NetScaler VPX as an Egress Gateway
An Egress Gateway defines the traffic exit point from a service mesh. NetScaler VPX can be deployed as an Egress Gateway to the Istio service mesh. In this deployment, a Kubernetes pod is deployed with an NetScaler xDS adapter container. The NetScaler xDS adapter container connects to the Istio control plane and reads the egress configuration and then configures the NetScaler VPX accordingly.
Note: For this deployment, establish the connectivity between the concerned NetScaler and the cluster nodes.
The following diagram shows a sample deployment of NetScaler VPX as an Egress Gateway.
For detailed instructions on how to deploy NetScaler VPX as an Egress Gateway, see Deploying NetScaler with Istio.