Déployer le proxy NetScaler CPX sur Google Compute Engine
Ce guide de déploiement explique comment déployer NetScaler CPX avec Docker sur Google Compute Engine (GCE) de Google Cloud avec Citrix ADM s’exécutant au sein du réseau de l’entreprise. Dans ce déploiement, NetScaler CPX installé sur GCE équilibre la charge de deux serveurs principaux, et Citrix ADM fournit des solutions de licences et d’analyse.
NetScaler CPX est un proxy basé sur des conteneurs qui prend en charge toutes les fonctionnalités de couche 7, le déchargement SSL, plusieurs protocoles et l’API NITRO. Citrix ADM fournit des solutions de gestion, de licences et d’analyse. En tant que serveur de licences, Citrix ADM fournit des droits d’accès aux instances NetScaler CPX qui s’exécutent sur site ou dans le cloud.
CPX et CPX Express sont les mêmes images. Lorsque vous achetez une licence et installez l’image CPX à l’aide de Citrix ADM, l’image CPX dans le Docker App Store (version 11 ou 12) devient une instance CPX complète. Sans licence, l’image CPX devient une instance CPX Express prenant en charge 20 Mbit/s et 250 connexions SSL.
Prérequis
-
2 Go de mémoire et 1 processeur virtuel dédiés à NetScaler CPX
-
Open Source Docker disponible auprès de GCE
-
Citrix ADM s’exécutant sur site avec une connexion Internet ou VPN à GCE
Remarque
Pour plus d’informations sur le déploiement de Citrix ADM, consultez la section Déploiementde Citrix ADM.
Étapes de configuration
Vous devez suivre les étapes suivantes pour configurer ce déploiement.
-
Installez Docker sur une machine virtuelle GCE.
-
Configurez la communication d’API distante avec l’instance Docker.
-
Installez l’image NetScaler CPX.
-
Créez une instance CPX.
-
Accordez une licence NetScaler CPX via Citrix ADM.
-
Configurez les services d’équilibrage de charge sur NetScaler CPX et vérifiez la configuration.
-
Installez les serveurs Web NGINX.
-
Configurez NetScaler CPX pour l’équilibrage de charge et vérifiez la répartition de la charge entre les deux services Web.
-
Étape 1 : installer Docker sur une machine virtuelle GCE
À partir de GCE, créez une machine virtuelle Linux Ubuntu. Ensuite, installez Docker sur la machine virtuelle à l’aide des commandes illustrées dans l’exemple suivant :
$ sudo curl –ssl https://get.docker.com/ | sh
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0curl: (6) Could not resolve host: xn--ssl-1n0a
100 17409 100 17409 0 0 21510 0 --:--:-- --:--:-- --:--:-- 21492
apparmor is enabled in the kernel and apparmor utils were already installed
\+ sudo -E sh -c apt-key add -
\+ echo -----BEGIN PGP PUBLIC KEY BLOCK-----
Version: GnuPG v1
mQINBFWln24BEADrBl5p99uKh8+rpvqJ48u4eTtjeXAWbslJotmC/CakbNSqOb9o
ddfzRvGVeJVERt/Q/mlvEqgnyTQy+e6oEYN2Y2kqXceUhXagThnqCoxcEJ3+KM4R
mYdoe/BJ/J/6rHOjq7Omk24z2qB3RU1uAv57iY5VGw5p45uZB4C4pNNsBJXoCvPn
TGAs/7IrekFZDDgVraPx/hdiwopQ8NltSfZCyu/jPpWFK28TR8yfVlzYFwibj5WK
dHM7ZTqlA1tHIG+agyPf3Rae0jPMsHR6q+arXVwMccyOi+ULU0z8mHUJ3iEMIrpT
X+80KaN/ZjibfsBOCjcfiJSB/acn4nxQQgNZigna32velafhQivsNREFeJpzENiG
HOoyC6qVeOgKrRiKxzymj0FIMLru/iFF5pSWcBQB7PYlt8J0G80lAcPr6VCiN+4c
NKv03SdvA69dCOj79PuO9IIvQsJXsSq96HB+TeEmmL+xSdpGtGdCJHHM1fDeCqkZ
hT+RtBGQL2SEdWjxbF43oQopocT8cHvyX6Zaltn0svoGs+wX3Z/H6/8P5anog43U
65c0A+64Jj00rNDr8j31izhtQMRo892kGeQAaaxg4Pz6HnS7hRC+cOMHUU4HA7iM
zHrouAdYeTZeZEQOA7SxtCME9ZnGwe2grxPXh/U/80WJGkzLFNcTKdv+rwARAQAB
tDdEb2NrZXIgUmVsZWFzZSBUb29sIChyZWxlYXNlZG9ja2VyKSA8ZG9ja2VyQGRv
Y2tlci5jb20+iQIcBBABCgAGBQJWw7vdAAoJEFyzYeVS+w0QHysP/i37m4SyoOCV
cnybl18vzwBEcp4VCRbXvHvOXty1gccVIV8/aJqNKgBV97lY3vrpOyiIeB8ETQeg
srxFE7t/Gz0rsLObqfLEHdmn5iBJRkhLfCpzjeOnyB3Z0IJB6UogO/msQVYe5CXJ
l6uwr0AmoiCBLrVlDAktxVh9RWch0l0KZRX2FpHu8h+uM0/zySqIidlYfLa3y5oH
scU+nGU1i6ImwDTD3ysZC5jp9aVfvUmcESyAb4vvdcAHR+bXhA/RW8QHeeMFliWw
7Z2jYHyuHmDnWG2yUrnCqAJTrWV+OfKRIzzJFBs4e88ru5h2ZIXdRepw/+COYj34
LyzxR2cxr2u/xvxwXCkSMe7F4KZAphD+1ws61FhnUMi/PERMYfTFuvPrCkq4gyBj
t3fFpZ2NR/fKW87QOeVcn1ivXl9id3MMs9KXJsg7QasT7mCsee2VIFsxrkFQ2jNp
D+JAERRn9Fj4ArHL5TbwkkFbZZvSi6fr5h2GbCAXIGhIXKnjjorPY/YDX6X8AaHO
W1zblWy/CFr6VFl963jrjJgag0G6tNtBZLrclZgWhOQpeZZ5Lbvz2ZA5CqRrfAVc
wPNW1fObFIRtqV6vuVluFOPCMAAnOnqR02w9t17iVQjO3oVN0mbQi9vjuExXh1Yo
ScVetiO6LSmlQfVEVRTqHLMgXyR/EMo7iQIcBBABCgAGBQJXSWBlAAoJEFyzYeVS
\+w0QeH0QAI6btAfYwYPuAjfRUy9qlnPhZ+xt1rnwsUzsbmo8K3XTNh+l/R08nu0d
sczw30Q1wju28fh1N8ay223+69f0+yICaXqR18AbGgFGKX7vo0gfEVaxdItUN3eH
NydGFzmeOKbAlrxIMECnSTG/TkFVYO9Ntlv9vSN2BupmTagTRErxLZKnVsWRzp+X
\-----END PGP PUBLIC KEY BLOCK-----
OK
\+ sudo -E sh -c mkdir -p /etc/apt/sources.list.d
\+ dpkg --print-architecture
\+ sudo -E sh -c echo deb \\\[arch=amd64\\\] https://apt.dockerproject.org/repo ubuntu-yakkety main \> /etc/apt/sources.list.d/docker.list
\+ sudo -E sh -c sleep 3; apt-get update; apt-get install -y -q docker-engine
Hit:1 http://us-west1.gce.archive.ubuntu.com/ubuntu yakkety InRelease
Get:2 http://us-west1.gce.archive.ubuntu.com/ubuntu yakkety-updates InRelease \[102 kB\]
Get:3 http://us-west1.gce.archive.ubuntu.com/ubuntu yakkety-backports InRelease \[102 kB\]
Get:4 http://us-west1.gce.archive.ubuntu.com/ubuntu yakkety/restricted Sources \[5,376 B\]
Get:5 http://us-west1.gce.archive.ubuntu.com/ubuntu yakkety/multiverse Sources \[181 kB\]
Get:6 http://us-west1.gce.archive.ubuntu.com/ubuntu yakkety/universe Sources \[8,044 kB\]
Get:7 http://archive.canonical.com/ubuntu yakkety InRelease \[11.5 kB\]
Get:8 http://security.ubuntu.com/ubuntu yakkety-security InRelease \[102 kB\]
Get:9 https://apt.dockerproject.org/repo ubuntu-yakkety InRelease \[47.3 kB\]
Get:10 http://us-west1.gce.archive.ubuntu.com/ubuntu yakkety/main Sources \[903 kB\]
Get:11 http://us-west1.gce.archive.ubuntu.com/ubuntu yakkety-updates/restricted Sources \[2,688 B\]
Get:12 http://us-west1.gce.archive.ubuntu.com/ubuntu yakkety-updates/universe Sources \[57.9 kB\]
Get:13 http://us-west1.gce.archive.ubuntu.com/ubuntu yakkety-updates/multiverse Sources \[3,172 B\]
Get:14 http://us-west1.gce.archive.ubuntu.com/ubuntu yakkety-updates/main Sources \[107 kB\]
Get:15 http://us-west1.gce.archive.ubuntu.com/ubuntu yakkety-updates/main amd64 Packages \[268 kB\]
Get:16 http://us-west1.gce.archive.ubuntu.com/ubuntu yakkety-updates/main Translation-en \[122 kB\]
Get:17 http://us-west1.gce.archive.ubuntu.com/ubuntu yakkety-updates/universe amd64 Packages \[164 kB\]
Get:18 http://us-west1.gce.archive.ubuntu.com/ubuntu yakkety-updates/universe Translation-en \[92.4 kB\]
Get:19 http://us-west1.gce.archive.ubuntu.com/ubuntu yakkety-updates/multiverse amd64 Packages \[4,840 B\]
Get:20 http://us-west1.gce.archive.ubuntu.com/ubuntu yakkety-updates/multiverse Translation-en \[2,708 B\]
Get:21 http://us-west1.gce.archive.ubuntu.com/ubuntu yakkety-backports/universe Sources \[2,468 B\]
Get:22 http://us-west1.gce.archive.ubuntu.com/ubuntu yakkety-backports/main Sources \[2,480 B\]
Get:23 http://us-west1.gce.archive.ubuntu.com/ubuntu yakkety-backports/main amd64 Packages \[3,500 B\]
Get:24 http://us-west1.gce.archive.ubuntu.com/ubuntu yakkety-backports/universe amd64 Packages \[3,820 B\]
Get:25 http://us-west1.gce.archive.ubuntu.com/ubuntu yakkety-backports/universe Translation-en \[1,592 B\]
Get:26 http://archive.canonical.com/ubuntu yakkety/partner amd64 Packages \[2,480 B\]
Get:27 http://security.ubuntu.com/ubuntu yakkety-security/main Sources \[47.7 kB\]
Get:28 https://apt.dockerproject.org/repo ubuntu-yakkety/main amd64 Packages \[2,453 B\]
Get:29 http://security.ubuntu.com/ubuntu yakkety-security/universe Sources \[20.7 kB\]
Get:30 http://security.ubuntu.com/ubuntu yakkety-security/multiverse Sources \[1,140 B\]
Get:31 http://security.ubuntu.com/ubuntu yakkety-security/restricted Sources \[2,292 B\]
Get:32 http://security.ubuntu.com/ubuntu yakkety-security/main amd64 Packages \[150 kB\]
Get:33 http://security.ubuntu.com/ubuntu yakkety-security/main Translation-en \[68.0 kB\]
Get:34 http://security.ubuntu.com/ubuntu yakkety-security/universe amd64 Packages \[77.2 kB\]
Get:35 http://security.ubuntu.com/ubuntu yakkety-security/universe Translation-en \[47.3 kB\]
Get:36 http://security.ubuntu.com/ubuntu yakkety-security/multiverse amd64 Packages \[2,832 B\]
Fetched 10.8 MB in 2s (4,206 kB/s)
Reading package lists... Done
Reading package lists...
Building dependency tree...
Reading state information...
The following additional packages will be installed:
aufs-tools cgroupfs-mount libltdl7
The following NEW packages will be installed:
aufs-tools cgroupfs-mount docker-engine libltdl7
0 upgraded, 4 newly installed, 0 to remove and 37 not upgraded.
Need to get 21.2 MB of archives.
After this operation, 111 MB of additional disk space will be used.
Get:1 http://us-west1.gce.archive.ubuntu.com/ubuntu yakkety/universe amd64 aufs-tools amd64 1:3.2+20130722-1.1ubuntu1 \[92.9 kB\]
Get:2 http://us-west1.gce.archive.ubuntu.com/ubuntu yakkety/universe amd64 cgroupfs-mount all 1.3 \[5,778 B\]
Get:3 http://us-west1.gce.archive.ubuntu.com/ubuntu yakkety/main amd64 libltdl7 amd64 2.4.6-1 \[38.6 kB\]
Get:4 https://apt.dockerproject.org/repo ubuntu-yakkety/main amd64 docker-engine amd64 17.05.0~ce-0~ubuntu-yakkety \[21.1 MB\]
Fetched 21.2 MB in 1s (19.8 MB/s)
Selecting previously unselected package aufs-tools.
(Reading database ... 63593 files and directories currently installed.)
Preparing to unpack .../aufs-tools\_1%3a3.2+20130722-1.1ubuntu1\_amd64.deb ...
Unpacking aufs-tools (1:3.2+20130722-1.1ubuntu1) ...
Selecting previously unselected package cgroupfs-mount.
Preparing to unpack .../cgroupfs-mount\_1.3\_all.deb ...
Unpacking cgroupfs-mount (1.3) ...
Selecting previously unselected package libltdl7:amd64.
Preparing to unpack .../libltdl7\_2.4.6-1\_amd64.deb ...
Unpacking libltdl7:amd64 (2.4.6-1) ...
Selecting previously unselected package docker-engine.
Preparing to unpack .../docker-engine\_17.05.0~ce-0~ubuntu-yakkety\_amd64.deb ...
Unpacking docker-engine (17.05.0~ce-0~ubuntu-yakkety) ...
Setting up aufs-tools (1:3.2+20130722-1.1ubuntu1) ...
Processing triggers for ureadahead (0.100.0-19) ...
Setting up cgroupfs-mount (1.3) ...
Processing triggers for libc-bin (2.24-3ubuntu2) ...
Processing triggers for systemd (231-9ubuntu4) ...
Setting up libltdl7:amd64 (2.4.6-1) ...
Processing triggers for man-db (2.7.5-1) ...
Setting up docker-engine (17.05.0~ce-0~ubuntu-yakkety) ...
Created symlink /etc/systemd/system/multi-user.target.wants/docker.service → /lib/systemd/system/docker.service.
Created symlink /etc/systemd/system/sockets.target.wants/docker.socket → /lib/systemd/system/docker.socket.
Processing triggers for ureadahead (0.100.0-19) ...
Processing triggers for libc-bin (2.24-3ubuntu2) ...
Processing triggers for systemd (231-9ubuntu4) ...
\+ sudo -E sh -c docker version
Client:
Version: 17.05.0-ce
API version: 1.29
Go version: go1.7.5
Git commit: 89658be
Built: Thu May 4 22:15:36 2017
OS/Arch: linux/amd64
Server:
Version: 17.05.0-ce
API version: 1.29 (minimum version 1.12)
Go version: go1.7.5
Git commit: 89658be
Built: Thu May 4 22:15:36 2017
OS/Arch: linux/amd64
Experimental: false
If you would like to use Docker as a non-root user, you should now consider
adding your user to the "docker" group with something like:
sudo usermod -aG docker albert\_lee
Remember that you will have to log out and back in for this to take effect.
WARNING: Adding a user to the "docker" group will grant the ability to run
containers which can be used to obtain root privileges on the
docker host.
Refer to https://docs.docker.com/engine/security/security/\#docker-daemon-attack-surface
for more information.
$
**$ sudo docker info**
Containers: 0
Running: 0
Paused: 0
Stopped: 0
Images: 0
Server Version: 17.05.0-ce
Storage Driver: aufs
Root Dir: /var/lib/docker/aufs
Backing Filesystem: extfs
Dirs: 0
Dirperm1 Supported: true
Logging Driver: json-file
Cgroup Driver: cgroupfs
Plugins:
Volume: local
Network: bridge host macvlan null overlay
Swarm: inactive
Runtimes: runc
Default Runtime: runc
Init Binary: docker-init
containerd version: 9048e5e50717ea4497b757314bad98ea3763c145
runc version: 9c2d8d184e5da67c95d601382adf14862e4f2228
init version: 949e6fa
Security Options:
apparmor
seccomp
Profile: default
Kernel Version: 4.8.0-51-generic
Operating System: Ubuntu 16.10
OSType: linux
Architecture: x86\_64
CPUs: 1
Total Memory: 3.613GiB
Name: docker-7
ID: R5TW:VKXK:EKGR:GHWM:UNU4:LPJH:IQY5:X77G:NNRQ:HWBY:LIUD:4ELQ
Docker Root Dir: /var/lib/docker
Debug Mode (client): false
Debug Mode (server): false
Registry: https://index.docker.io/v1/
Experimental: false
Insecure Registries:
127.0.0.0/8
Live Restore Enabled: false
WARNING: No swap limit support
$
**$ sudo docker images**
REPOSITORY TAG IMAGE ID CREATED SIZE
$
**$ sudo docker ps**
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
$
<!--NeedCopy-->
Étape 2 : Configurer la communication d’API distante avec l’instance Docker
Ouvrez le port 4243 pour la communication de l’API avec l’instance Docker. Ce port est requis pour que Citrix ADM puisse communiquer avec l’instance Docker.
**cd /etc/systemd/system**
**sudo vi docker-tcp.socket**
**cat docker-tcp.socket**
\[Unit\]
**Description=Docker Socket for the API
\[Socket\]
ListenStream=4243
BindIPv6Only=both
Service=docker.service
\[Install\]
WantedBy=sockets.target**
$ **sudo systemctl enable docker-tcp.socket**
Created symlink /etc/systemd/system/sockets.target.wants/docker-tcp.socket → /etc/systemd/system/docker-tcp.socket.
**sudo systemctl enable docker.socket**
**sudo systemctl stop docker**
**sudo systemctl start docker-tcp.socket**
**sudo systemctl start docker**
$ **sudo systemctl status docker**
● docker.service - Docker Application Container Engine
Loaded: loaded (/lib/systemd/system/docker.service; enabled; vendor preset: enabled)
Active: **active (running)** since Wed 2017-05-31 12:52:17 UTC; 2s ago
Docs: https://docs.docker.com
Main PID: 4133 (dockerd)
Tasks: 16 (limit: 4915)
Memory: 30.1M
CPU: 184ms
CGroup: /system.slice/docker.service
├─4133 /usr/bin/dockerd -H fd://
└─4137 docker-containerd -l unix:///var/run/docker/libcontainerd/docker-containerd.sock --metrics-interval=0 --start-timeout 2m -
May 31 12:52:17 docker-7 dockerd\[4133\]: time="2017-05-31T12:52:17.300890402Z" level=warning msg="Your kernel does not support cgroup rt peri
May 31 12:52:17 docker-7 dockerd\[4133\]: time="2017-05-31T12:52:17.301079754Z" level=warning msg="Your kernel does not support cgroup rt runt
May 31 12:52:17 docker-7 dockerd\[4133\]: time="2017-05-31T12:52:17.301681794Z" level=info msg="Loading containers: start."
May 31 12:52:17 docker-7 dockerd\[4133\]: time="2017-05-31T12:52:17.417539064Z" level=info msg="Default bridge (docker0) is assigned with an I
May 31 12:52:17 docker-7 dockerd\[4133\]: time="2017-05-31T12:52:17.465011600Z" level=info msg="Loading containers: done."
May 31 12:52:17 docker-7 dockerd\[4133\]: time="2017-05-31T12:52:17.484747909Z" level=info msg="Daemon has completed initialization"
May 31 12:52:17 docker-7 dockerd\[4133\]: time="2017-05-31T12:52:17.485119478Z" level=info msg="Docker daemon" commit=89658be graphdriver=aufs
May 31 12:52:17 docker-7 systemd\[1\]: Started Docker Application Container Engine.
May 31 12:52:17 docker-7 dockerd\[4133\]: time="2017-05-31T12:52:17.503832254Z" level=info msg="API listen on /var/run/docker.sock"
May 31 12:52:17 docker-7 dockerd\[4133\]: time="2017-05-31T12:52:17.504061522Z" level=info msg="API listen on \[::\]:4243"
$
(external)$ **curl 104.199.209.157:4243/version**
{"Version":"17.05.0-ce","ApiVersion":"1.29","MinAPIVersion":"1.12","GitCommit":"89658be","GoVersion":"go1.7.5","Os":"linux","Arch":"amd64","KernelVersion":"4.8.0-52-generic","BuildTime":"2017-05-04T22:15:36.071254972+00:00"}
(external)$
<!--NeedCopy-->
Étape 3 : Installation de NetScaler CPX Image
Téléchargez l’image NetScaler CPX sur Docker App Store. Le CPX Express et le CPX ont la même image. Toutefois, lorsque vous achetez une licence et installez l’image CPX à l’aide de Citrix ADM, l’image devient une instance CPX complète avec des performances de 1 Gbit/s. Sans licence, l’image devient une instance CPX Express prenant en charge 20 Mbit/s et 250 connexions SSL.
$ **sudo docker pull store/citrix/citrixadccpx:13.0-36.29**
13.0-36.29: Pulling from store/citrix/citrixadccpx
4e1f679e8ab4: Pull complete
a3ed95caeb02: Pull complete
2931a926d44b: Pull complete
362cd40c5745: Pull complete
d10118725a7a: Pull complete
1e570419a7e5: Pull complete
d19e06114233: Pull complete
d3230f008ffd: Pull complete
22bdb10a70ec: Pull complete
1a5183d7324d: Pull complete
241868d4ebff: Pull complete
3f963e7ae2fc: Pull complete
fd254cf1ea7c: Pull complete
33689c749176: Pull complete
59c27bad28f5: Pull complete
588f5003e10f: Pull complete
Digest: sha256:31a65cfa38833c747721c6fbc142faec6051e5f7b567d8b212d912b69b4f1ebe
Status: Downloaded newer image for store/citrix/citrixadccpx:13.0-36.29
$
$ **sudo docker images**
REPOSITORY TAG IMAGE ID CREATED SIZE
store/citrix/citrixadccpx:13.0-36.29 6fa57c38803f 3 weeks ago 415MB
$
<!--NeedCopy-->
Étape 4 : Création d’une instance NetScaler CPX
Installez l’image NetScaler CPX sur l’hôte Docker. Ouvrez des ports pour des services spécifiques, comme indiqué dans l’exemple suivant, et spécifiez une adresse IP pour Citrix ADM :
bash-2.05b\# **CHOST=${1:-localhost}**
bash-2.05b\# **echo | openssl s\_client -connect $CHOST:443 | openssl x509 -fingerprint -noout | cut -d'=' -f2**
depth=0 C = US, ST = California, L = San Jose, O = NetScaler, OU = Internal, CN = Test Only Cert
verify error:num=18:self signed certificate
verify return:1
depth=0 C = US, ST = California, L = San Jose, O = NetScaler, OU = Internal, CN = Test Only Cert
verify return:1
DONE
24:AA:8B:91:7B:72:5E:6E:C1:FD:86:FA:09:B6:42:49:FC:1E:86:A4
bash-2.05b\#
$ **sudo docker run -dt -p 50000:88 -p 5080:80 -p 5022:22 -p 5443:443 -p 5163:161/udp -e NS\_HTTP\_PORT=5080 -e NS\_HTTPS\_PORT=5443 -e NS\_SSH\_PORT=5022 -e NS\_SNMP\_PORT=5163 -e EULA=yes -e LS\_IP=xx.xx.xx.xx -e PLATFORM=CP1000 --privileged=true --ulimit core=-1 -e NS\_MGMT\_SERVER=xx.xx.xx.xx:xxxx -e NS\_MGMT\_FINGER\_PRINT=24:AA:8B:91:7B:72:5E:6E:C1:FD:86:FA:09:B6:42:49:FC:1E:86:A4 --env NS\_ROUTABLE=false --env HOST=104.199.209.157 store/citrix/citrixadccpx:13.0-36.29**
44ca1c6c0907e17a10ffcb9ffe33cd3e9f71898d8812f816e714821870fa3538
$
$ **sudo docker ps**
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
44ca1c6c0907 store/citrix/citrixadccpx:13.0-36.29 "/bin/sh -c 'bash ..." 19 seconds ago Up 17 seconds 0.0.0.0:5022-\>22/tcp, 0.0.0.0:5080-\>80/tcp, 0.0.0.0:50000-\>88/tcp, 0.0.0.0:5163-\>161/udp, 0.0.0.0:5443-\>443/tcp gifted\_perlman
$
$ **ssh -p 5022 root@localhost**
root@localhost's password:
Welcome to nsoslx 1.0 (GNU/Linux 4.8.0-52-generic x86\_64)
\* Documentation: https://www.citrix.com/
Last login: Mon Jun 5 18:58:51 2017 from xx.xx.xx.xx
root@44ca1c6c0907:~\#
root@44ca1c6c0907:~\#
root@44ca1c6c0907:~\# **cli\_script.sh 'show ns ip'**
exec: show ns ip
Ipaddress Traffic Domain Type Mode Arp Icmp Vserver State
\--------- -------------- ---- ---- --- ---- ------- ------
1\) 172.17.0.2 0 NetScaler IP Active Enabled Enabled NA Enabled
2\) 192.0.0.1 0 SNIP Active Enabled Enabled NA Enabled
Done
root@44ca1c6c0907:~\# **cli\_script.sh 'show licenseserver'**
exec: show licenseserver
1\) ServerName: xx.xx.xx.xxPort: 27000 Status: 1 Grace: 0 Gptimeleft: 0
Done
root@44ca1c6c0907:~\# cli\_script.sh 'show capacity'
exec: show capacity
Actualbandwidth: 1000 Platform: CP1000 Unit: Mbps Maxbandwidth: 3000 Minbandwidth: 20 Instancecount: 0
Done
root@44ca1c6c0907:~\#
$ **sudo iptables -t nat -L -n**
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
DOCKER all -- 0.0.0.0/0 0.0.0.0/0 ADDRTYPE match dst-type LOCAL
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
DOCKER all -- 0.0.0.0/0 \!127.0.0.0/8 ADDRTYPE match dst-type LOCAL
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
MASQUERADE all -- 172.17.0.0/16 0.0.0.0/0
MASQUERADE tcp -- 172.17.0.2 172.17.0.2 tcp dpt:443
MASQUERADE udp -- 172.17.0.2 172.17.0.2 udp dpt:161
MASQUERADE tcp -- 172.17.0.2 172.17.0.2 tcp dpt:88
MASQUERADE tcp -- 172.17.0.2 172.17.0.2 tcp dpt:80
MASQUERADE tcp -- 172.17.0.2 172.17.0.2 tcp dpt:22
Chain DOCKER (2 references)
target prot opt source destination
RETURN all -- 0.0.0.0/0 0.0.0.0/0
DNAT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:5443 to:172.17.0.2:443
DNAT udp -- 0.0.0.0/0 0.0.0.0/0 udp dpt:5163 to:172.17.0.2:161
DNAT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:50000 to:172.17.0.2:88
DNAT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:5080 to:172.17.0.2:80
DNAT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:5022 to:172.17.0.2:22
$
<!--NeedCopy-->
Étape 5 : Accordez une licence NetScaler CPX via Citrix ADM
En supposant que Citrix ADM s’exécute sur site, vous devriez être en mesure de vérifier que NetScaler CPX communique avec Citrix ADM et envoie des informations. Les images suivantes montrent que NetScaler CPX récupère une licence auprès de Citrix ADM.
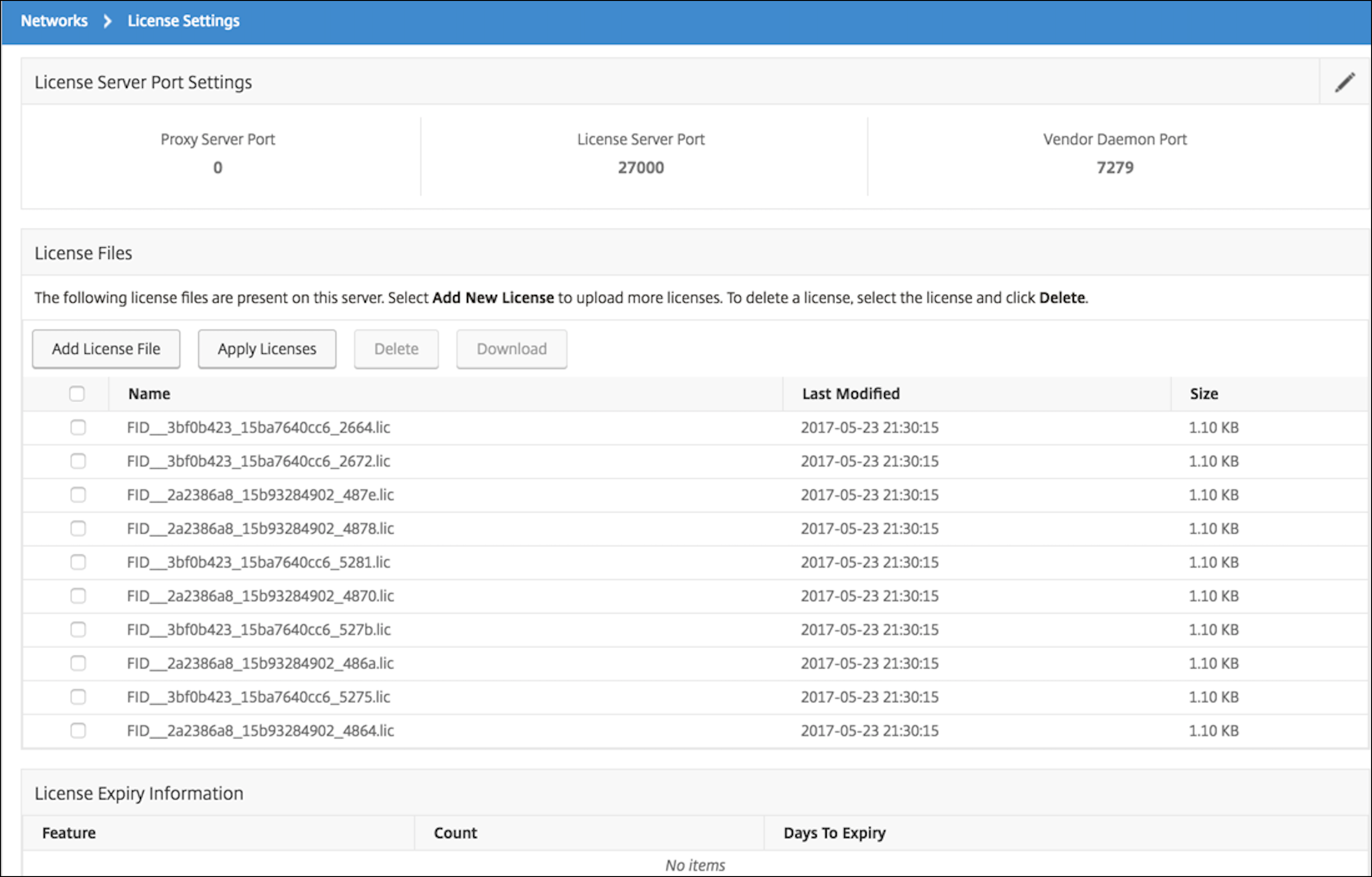
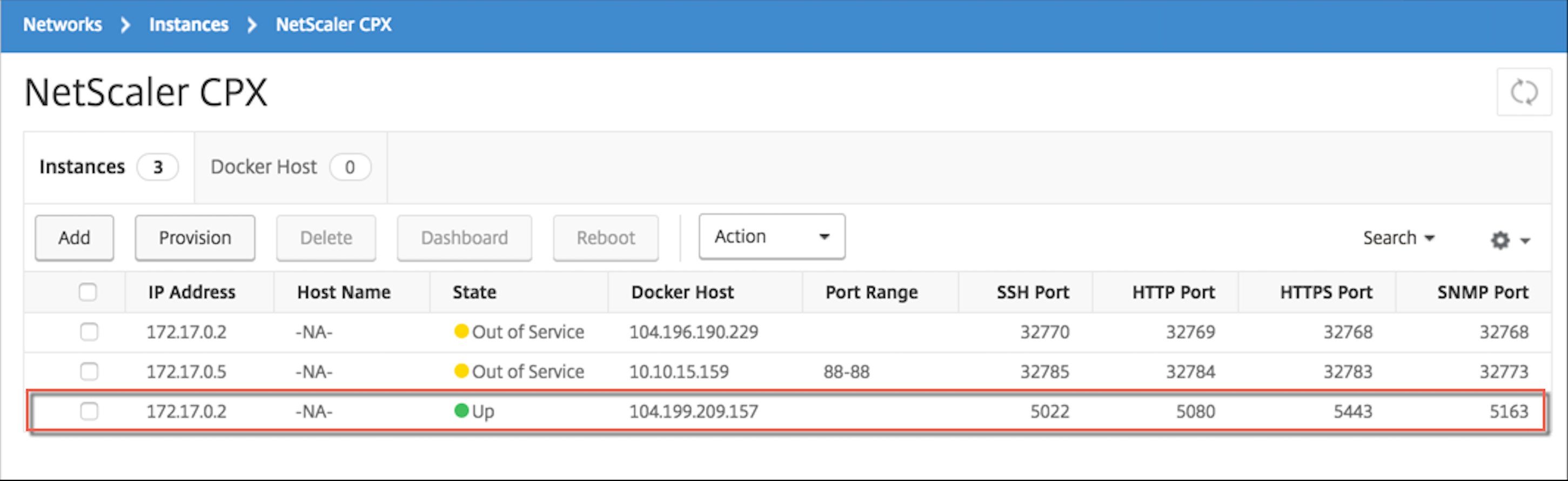
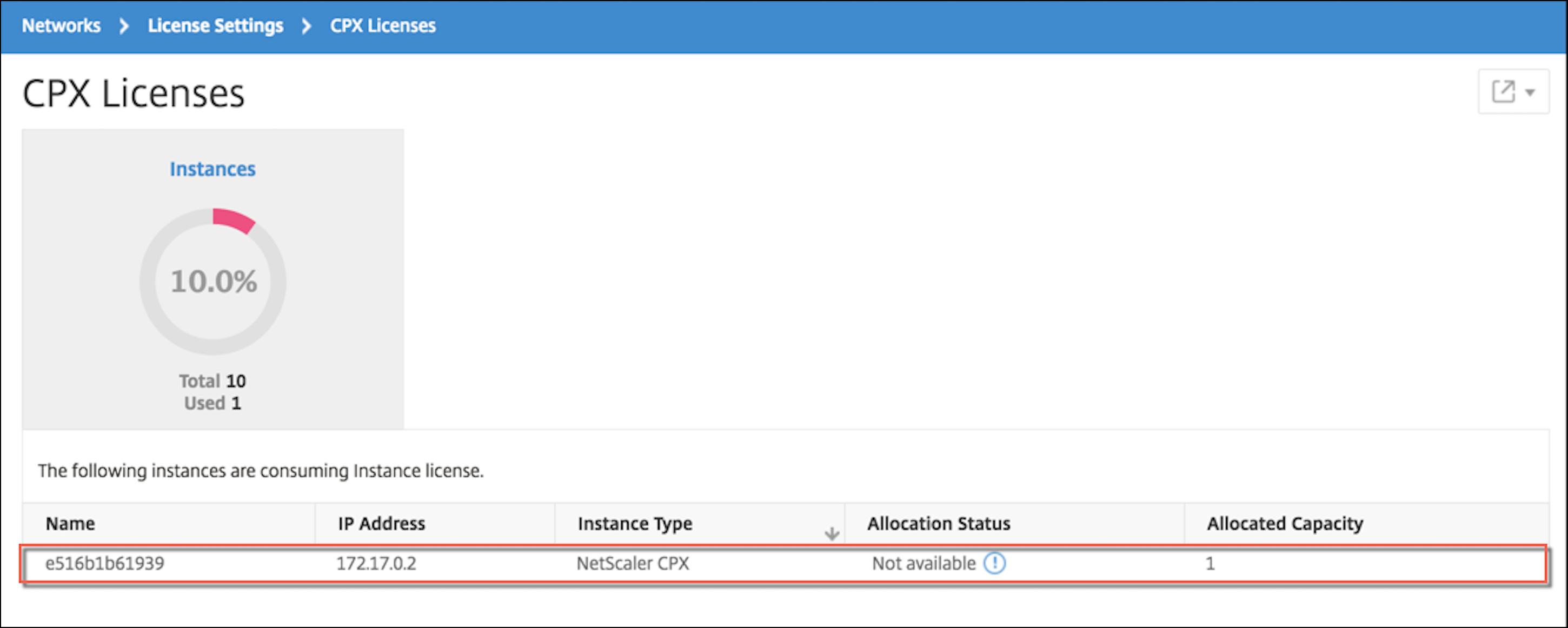
Étape 6 : configurer les services d’équilibrage de charge sur NetScaler CPX et vérifier la configuration
Tout d’abord, installez les serveurs Web NGINX sur l’hôte Docker. Configurez ensuite l’équilibrage de charge sur NetScaler CPX pour équilibrer la charge des deux serveurs Web et testez la configuration.
Installation des serveurs Web NGINX
Utilisez les commandes illustrées dans l’exemple suivant pour installer des serveurs Web NGINX.
$ sudo docker pull nginx
Using default tag: latest
latest: Pulling from library/nginx
Digest: sha256:41ad9967ea448d7c2b203c699b429abe1ed5af331cd92533900c6d77490e0268
Status: Image is up to date for nginx:latest
**$ sudo docker run -d -p 81:80 nginx**
098a77974818f451c052ecd172080a7d45e446239479d9213cd4ea6a3678616f
**$ sudo docker run -d -p 82:80 nginx**
bbdac2920bb4085f70b588292697813e5975389dd546c0512daf45079798db65
**$ sudo iptables -t nat -L -n**
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
DOCKER all -- 0.0.0.0/0 0.0.0.0/0 ADDRTYPE match dst-type LOCAL
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
DOCKER all -- 0.0.0.0/0 \!127.0.0.0/8 ADDRTYPE match dst-type LOCAL
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
MASQUERADE all -- 172.17.0.0/16 0.0.0.0/0
MASQUERADE tcp -- 172.17.0.2 172.17.0.2 tcp dpt:443
MASQUERADE udp -- 172.17.0.2 172.17.0.2 udp dpt:161
MASQUERADE tcp -- 172.17.0.2 172.17.0.2 tcp dpt:88
MASQUERADE tcp -- 172.17.0.2 172.17.0.2 tcp dpt:80
MASQUERADE tcp -- 172.17.0.2 172.17.0.2 tcp dpt:22
MASQUERADE tcp -- 172.17.0.3 172.17.0.3 tcp dpt:80
MASQUERADE tcp -- 172.17.0.4 172.17.0.4 tcp dpt:80
Chain DOCKER (2 references)
target prot opt source destination
RETURN all -- 0.0.0.0/0 0.0.0.0/0
DNAT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:5443 to:172.17.0.2:443
DNAT udp -- 0.0.0.0/0 0.0.0.0/0 udp dpt:5163 to:172.17.0.2:161
DNAT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:50000 to:172.17.0.2:88
DNAT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:5080 to:172.17.0.2:80
DNAT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:5022 to:172.17.0.2:22
DNAT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:81 to:172.17.0.3:80
DNAT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:82 to:172.17.0.4:80
$
<!--NeedCopy-->
Configurer NetScaler CPX pour l’équilibrage de charge et vérifier la répartition de la charge entre les deux services Web
$ **ssh -p 5022 root@localhost**
root@localhost's password:
Welcome to nsoslx 1.0 (GNU/Linux 4.8.0-52-generic x86\_64)
\* Documentation: https://www.citrix.com/
Last login: Mon Jun 5 18:58:54 2017 from 172.17.0.1
root@44ca1c6c0907:~\#
root@44ca1c6c0907:~\#
root@44ca1c6c0907:~\#
root@44ca1c6c0907:~\#
root@44ca1c6c0907:~\# **cli\_script.sh "add service web1 172.17.0.3 HTTP 80"**
exec: add service web1 172.17.0.3 HTTP 80
Done
root@44ca1c6c0907:~\# **cli\_script.sh "add service web2 172.17.0.4 HTTP 80"**
exec: add service web2 172.17.0.4 HTTP 80
Done
root@44ca1c6c0907:~\# **cli\_script.sh "add lb vserver cpx-vip HTTP 172.17.0.2 88"**
exec: add lb vserver cpx-vip HTTP 172.17.0.2 88
Done
root@44ca1c6c0907:~\# **cli\_script.sh "bind lb vserver cpx-vip web1"**
exec: bind lb vserver cpx-vip web1
Done
root@44ca1c6c0907:~\# **cli\_script.sh "bind lb vserver cpx-vip web2"**
exec: bind lb vserver cpx-vip web2
Done
root@44ca1c6c0907:~\#
root@44ca1c6c0907:~\# **cli\_script.sh 'show lb vserver cpx-vip'**
exec: show lb vserver cpx-vip
cpx-vip (172.17.0.2:88) - HTTP Type: ADDRESS
State: UP
Last state change was at Mon Jun 5 19:01:49 2017
Time since last state change: 0 days, 00:00:42.620
Effective State: UP
Client Idle Timeout: 180 sec
Down state flush: ENABLED
Disable Primary Vserver On Down : DISABLED
Appflow logging: ENABLED
Port Rewrite : DISABLED
No. of Bound Services : 2 (Total) 2 (Active)
Configured Method: LEASTCONNECTION
Current Method: Round Robin, Reason: A new service is bound BackupMethod: ROUNDROBIN
Mode: IP
Persistence: NONE
Vserver IP and Port insertion: OFF
Push: DISABLED Push VServer:
Push Multi Clients: NO
Push Label Rule: none
L2Conn: OFF
Skip Persistency: None
Listen Policy: NONE
IcmpResponse: PASSIVE
RHIstate: PASSIVE
New Service Startup Request Rate: 0 PER\_SECOND, Increment Interval: 0
Mac mode Retain Vlan: DISABLED
DBS\_LB: DISABLED
Process Local: DISABLED
Traffic Domain: 0
TROFS Persistence honored: ENABLED
Retain Connections on Cluster: NO
2\) web1 (172.17.0.3: 80) - HTTP State: UP Weight: 1
3\) web2 (172.17.0.4: 80) - HTTP State: UP Weight: 1
Done
root@44ca1c6c0907:~\#
(external)$ **curl 104.199.209.157:50000**
\<\!DOCTYPE html\>
\<html\>
\<head\>
\<title\>Welcome to nginx\!\</title\>
\<style\>
body {
width: 35em;
margin: 0 auto;
font-family: Tahoma, Verdana, Arial, sans-serif;
}
\</style\>
\</head\>
\<body\>
\<h1\>Welcome to nginx\!\</h1\>
\<p\>If you see this page, the nginx web server is successfully installed and
working. Further configuration is required.\</p\>
\<p\>For online documentation and support please refer to
\<a href="http://nginx.org/"\>nginx.org\</a\>.\<br/\>
Commercial support is available at
\<a href="http://nginx.com/"\>nginx.com\</a\>.\</p\>
\<p\>\<em\>Thank you for using nginx.\</em\>\</p\>
\</body\>
\</html\>
(external)$
(external)$ for i in {1..100} ; **do curl http://104.199.209.157:50000 -o /dev/null ; done**
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 612 100 612 0 0 1767 0 --:--:-- --:--:-- --:--:-- 1768
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 612 100 612 0 0 1893 0 --:--:-- --:--:-- --:--:-- 1894
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 612 100 612 0 0 1884 0 --:--:-- --:--:-- --:--:-- 1883
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 612 100 612 0 0 1917 0 --:--:-- --:--:-- --:--:-- 1924
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 612 100 612 0 0 1877 0 --:--:-- --:--:-- --:--:-- 1883
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 612 100 612 0 0 1852 0 --:--:-- --:--:-- --:--:-- 1848
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 612 100 612 0 0 1860 0 --:--:-- --:--:-- --:--:-- 1865
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 612 100 612 0 0 1887 0 --:--:-- --:--:-- --:--:-- 1888
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 612 100 612 0 0 1802 0 --:--:-- --:--:-- --:--:-- 1800
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 612 100 612 0 0 1902 0 --:--:-- --:--:-- --:--:-- 1906
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 612 100 612 0 0 1843 0 --:--:-- --:--:-- --:--:-- 1848
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 612 100 612 0 0 1862 0 --:--:-- --:--:-- --:--:-- 1860
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 612 100 612 0 0 1806 0 --:--:-- --:--:-- --:--:-- 1810
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 612 100 612 0 0 1702 0 --:--:-- --:--:-- --:--:-- 1704
(external)$
root@44ca1c6c0907:~\# **cli\_script.sh 'stat lb vserver cpx-vip'**
exec: stat lb vserver cpx-vip
Virtual Server Summary
vsvrIP port Protocol State Health actSvcs
cpx-vip 172.17.0.2 88 HTTP UP 100 2
inactSvcs
cpx-vip 0
Virtual Server Statistics
Rate (/s) Total
Vserver hits 0 101
Requests 0 101
Responses 0 101
Request bytes 0 8585
Response bytes 0 85850
Total Packets rcvd 0 708
Total Packets sent 0 408
Current client connections -- 0
Current Client Est connections -- 0
Current server connections -- 0
Current Persistence Sessions -- 0
Requests in surge queue -- 0
Requests in vserver's surgeQ -- 0
Requests in service's surgeQs -- 0
Spill Over Threshold -- 0
Spill Over Hits -- 0
Labeled Connection -- 0
Push Labeled Connection -- 0
Deferred Request 0 0
Invalid Request/Response -- 0
Invalid Request/Response Dropped -- 0
Vserver Down Backup Hits -- 0
Current Multipath TCP sessions -- 0
Current Multipath TCP subflows -- 0
Apdex for client response times. -- 1.00
Average client TTLB -- 0
web1 172.17.0.3 80 HTTP UP 51 0/s
web2 172.17.0.4 80 HTTP UP 50 0/s
Done
root@44ca1c6c0907:~\#
<!--NeedCopy-->