Content Security Policy response header support for NetScaler Gateway and authentication virtual server-generated responses
Starting from NetScaler release build 13.0–76.29, the Content-Security-Policy (CSP) response header is supported for NetScaler Gateway and authentication virtual server-generated responses.
The Content-Security-Policy (CSP) response header is a combination of policies, which the browser uses to avoid Cross Site Scripting (CSS) attacks. The HTTP CSP response header allows website administrators to control the resources the user agent is allowed to load for a given page. With a few exceptions, policies mostly involve specifying server origins and script endpoints. This helps guard against cross-site scripting attacks. The CSP header is designed to modify the way browsers render pages, and thus to protect from various cross-site injections, including CSS. It is important to set the header value correctly, in a way that does not prevent proper operation of the website. For example, if the header is set to prevent execution of inline JavaScript, the website must not use inline JavaScript in its pages.
The following are the advantages of the CSP response header.
- The primary function of a CSP response header is to prevent CSS attacks.
- In addition to restricting the domains from which content can be loaded, the server can specify which protocols are allowed to be used; for example (and ideally, from a security standpoint), a server can specify that all contents must be loaded using HTTPS.
- CSP helps in securing NetScaler from cross-site scripting attacks by securing files like “tmindex.html” and “homepage.html. The file “tmindex.html” is related to authentication and the file “homepage.html” is related to the published apps/links.
Configuring Content-Security-Policy header for NetScaler Gateway and authentication virtual server-generated responses
To enable the CSP header, you need to configure your web server to return the CSP HTTP header.
Points to note:
- By default, the CSP header is enabled in the following NetScaler builds:
- 14.1-47.46 and later
- 13.1-59.19 and later
- While enabling or disabling the default CSP policy, you are recommended to run the following command.
Flush cache contentgroup loginstaticobjects- For modifying the CSP for /logon/LogonPoint/index.html, modify the “Header set Content-Security-Policy” value as required under the section corresponding to the logon directory, which can be found under the directory
/var/netscaler/logon.- For instructions on how to configure a rewrite action and policy using the GUI, see Rewrite.
To configure CSP for authentication virtual server and NetScaler Gateway generated responses using CLI, type the following command at the command prompt:
set aaa parameter -defaultCSPHeader <ENABLE/DISABLE>
To configure CSP for NetScaler Gateway and authentication virtual server-generated responses using the GUI.
-
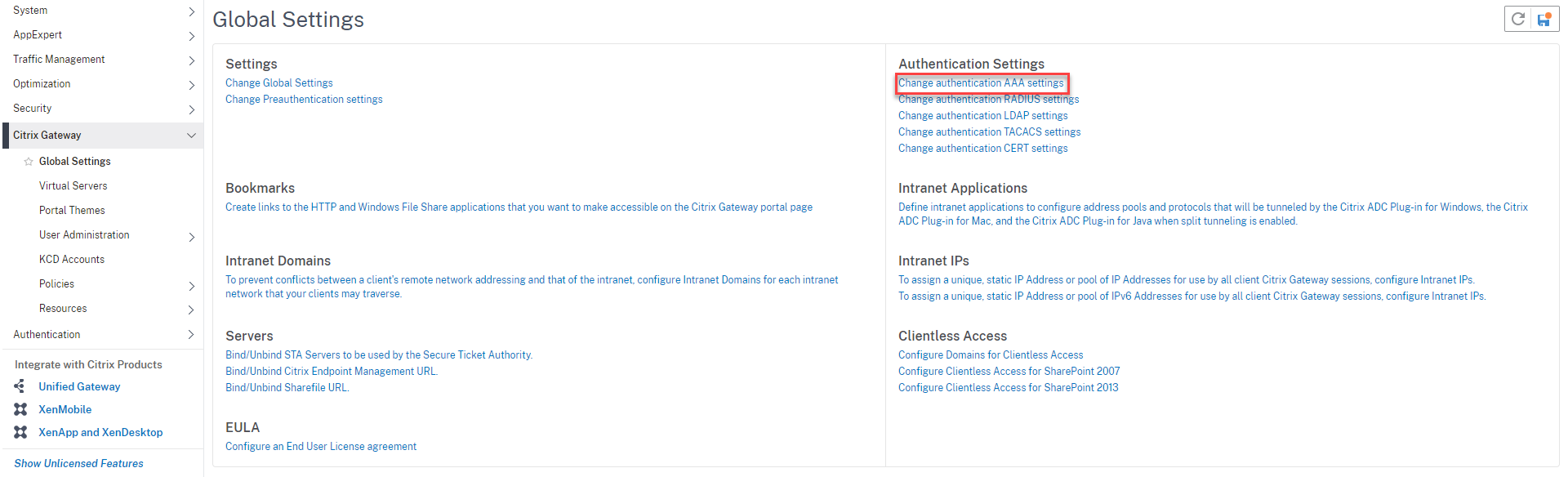
Navigate to NetScaler Gateway > Global Settings, click Change authentication AAA settings under Authentication Settings.
-
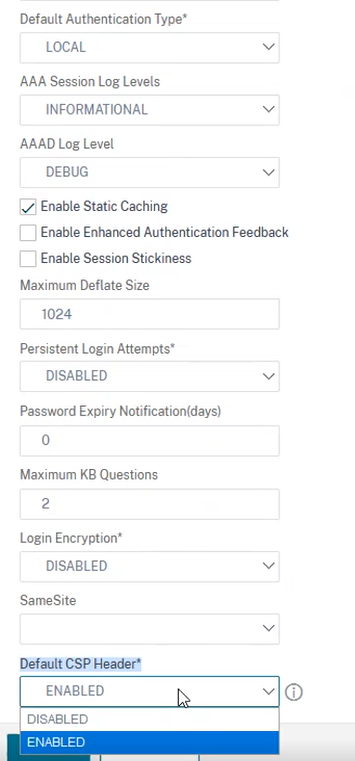
On the Configure AAA Parameters page, select the Enabled in Default CSP Header field.
Custom Content-Security-Policy header
You can configure a custom CSP header using a rewrite policy on the VPN virtual server and authentication virtual servers for authentication, authorization, and auditing endpoint-generated responses.
The following is an example for CSP header customization to include images and scripts only from the following two specified sources respectively, https://company.fqdn.com, https://example.com.
add rewrite action modify_csp insert_http_header Content-Security-Policy "\"default-src 'self'; script-src 'self' https://company.fqdn.com 'unsafe-inline' 'unsafe-eval'; connect-src 'self'; img-src http://localhost:* https://example.com 'self' data: http: https:; style-src 'self' 'unsafe-inline'; font-src 'self'; frame-src 'self'; child-src 'self' com.citrix.agmacepa://* citrixng://* com.citrix.nsgclient://*; form-action 'self'; object-src 'self'; report-uri /nscsp_violation/report_uri\""
add rewrite policy csp_pol true modify_csp
<!--NeedCopy-->
To bind the policy to the authentication virtual server,
bind authentication vserver auth_vs -policy csp_pol -priority 1 -type AAA_RESPONSE
bind authentication vserver auth_vs -policy csp_pol -priority 2 -type RESPONSE
<!--NeedCopy-->
Note:
When the policy is bound to the authentication virtual server:
If the packet engine generates the response, it is handled using
-type AAA_RESPONSE.If Apache generates the response, it is handled using
-type RESPONSE.
To bind the policy to the VPN virtual server,
bind vpn vserver vpn_vs -policy csp_pol -priority 1 -type AAA_RESPONSE
bind vpn vserver vpn_vs -policy csp_pol -priority 2 -type RESPONSE
<!--NeedCopy-->
Note:
The custom CSP header cannot be configured on the content switching and load balancing virtual servers for certain AAA-generated responses.
Rewrite policies to support DUO authentication
Rewrite policies for VPN virtual server
Rewrite the policies as follows to ensure that DUO authentication works correctly when the CSP header is enabled in a VPN virtual server:
add rewrite action delete_csp_header delete_http_header Content-Security-Policy
add rewrite policy delete_csp_header_policy "HTTP.REQ.URL.CONTAINS(\"/logon/LogonPoint/tmindex.html\")" delete_csp_header
bind authentication vserver authvs_radius -policy delete_csp_header_policy -priority 1 -gotoPriorityExpression NEXT -type RESPONSE
add rewrite action modify_csp_header_with_duo insert_http_header Content-Security-Policy "\"default-src \'self\'; script-src https://www.google.com/recaptcha/api.js https://www.gstatic.com/recaptcha/releases/ https://.duosecurity.com \'self\' \'unsafe-inline\'; connect-src \'self\'; img-src http://localhost: \'self\' data:; style-src \'self\' \'unsafe-inline\'; font-src \'self\' data:; frame-src https://www.google.com/recaptcha/ com.citrix.agmacepa://* citrixng://* com.citrix.nsgclient://* vmware-view://* nsgcepa://* application://* receiver:// https://.duosecurity.com \'self\'; child-src \'self\' com.citrix.agmacepa:// citrixng:// com.citrix.nsgclient://* vmware-view://* nsgcepa://nsgcepa application://*; form-action \'self\'; object-src \'none\'; report-uri /nscsp_violation/report_uri\""
add rewrite policy add_modified_csp_header_with_duo "HTTP.REQ.URL.CONTAINS(\"/logon/LogonPoint/tmindex.html\")" modify_csp_header_with_duo
bind authentication vserver authvs_radius -policy add_modified_csp_header_with_duo -priority 2 -gotoPriorityExpression NEXT -type RESPONSE
<!--NeedCopy-->
Rewrite policies for Traffic Management (TM) virtual server
Rewrite the policies as follows to ensure that DUO authentication works correctly when the CSP header is enabled in a TM virtual server:
add rewrite action delete_csp_header delete_http_header Content-Security-Policy
add rewrite policy delete_csp_header_policy "HTTP.REQ.URL.CONTAINS(\"/logon/LogonPoint/tmindex.html\")" delete_csp_header
bind authentication vserver tmvs_radius -policy delete_csp_header_policy -priority 1 -gotoPriorityExpression NEXT -type RESPONSE
add rewrite action modify_csp_header_with_duo insert_http_header Content-Security-Policy "\"default-src \'self\'; script-src https://www.google.com/recaptcha/api.js https://www.gstatic.com/recaptcha/releases/ https://.duosecurity.com \'self\' \'unsafe-inline\'; connect-src \'self\'; img-src http://localhost: \'self\' data:; style-src \'self\' \'unsafe-inline\'; font-src \'self\' data:; frame-src https://www.google.com/recaptcha/ com.citrix.agmacepa://* citrixng://* com.citrix.nsgclient://* vmware-view://* nsgcepa://* application://* receiver:// https://.duosecurity.com \'self\'; child-src \'self\' com.citrix.agmacepa:// citrixng:// com.citrix.nsgclient://* vmware-view://* nsgcepa://nsgcepa application://*; form-action \'self\'; object-src \'none\'; report-uri /nscsp_violation/report_uri\""
add rewrite policy add_modified_csp_header_with_duo "HTTP.REQ.URL.CONTAINS(\"/logon/LogonPoint/tmindex.html\")" modify_csp_header_with_duo
bind authentication vserver tmvs_radius -policy add_modified_csp_header_with_duo -priority 2 -gotoPriorityExpression NEXT -type RESPONSE
<!--NeedCopy-->