Recommended native OTP configurations for device registration
This section describes the native OTP configurations that you can perform for device registration in the following scenarios:
- New users who are registering their devices
- Registered users who have lost their devices
Pre-requisite
Configure the authentication virtual server using the NetScaler CLI.
add authentication vserver authvs_otp SSL 1.2.3.5 443
bind authentication vserver authvs_otp -portaltheme RFWebUI
bind ssl vserver authvs_otp -certkeyname otpauthcert
<!--NeedCopy-->
Native OTP configurations for enhanced OTP security
-
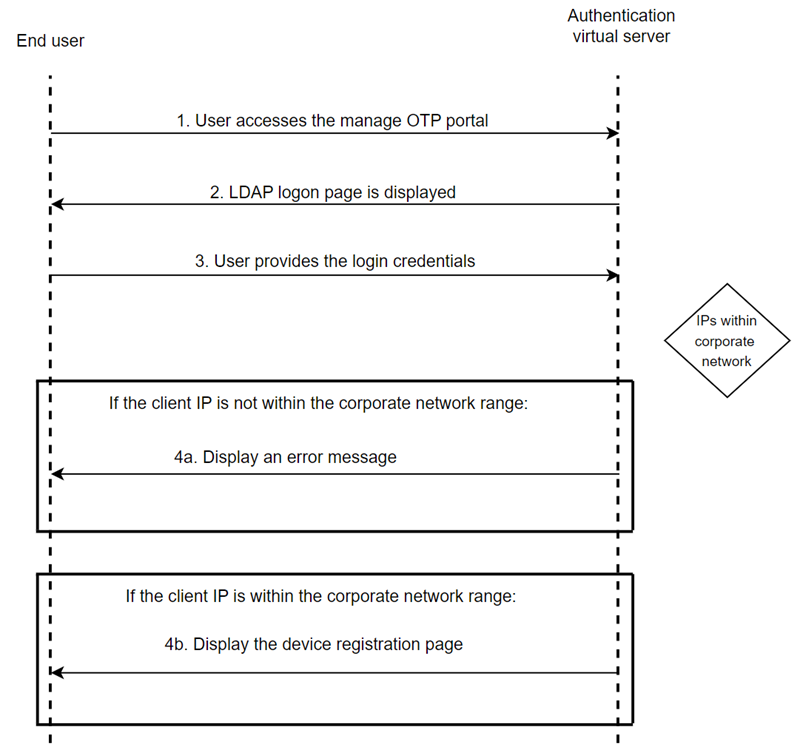
Approach 1: Client IP address restriction
In this approach, the validity of the user access is evaluated using the client source IP address. The user must be present in the office network or the branch office to register or remove their device. User requests for device registration from outside the office subnets are not approved.
-
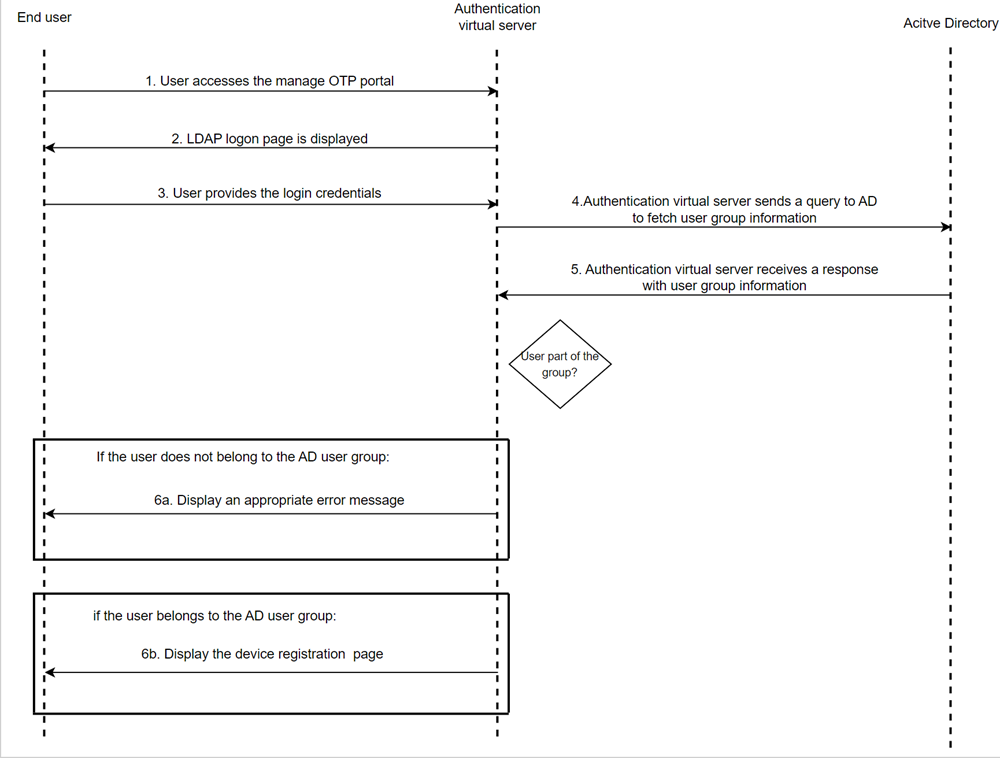
Approach 2: User group membership based restriction
In this approach, the validity of the user’s access is evaluated based on their membership of the AD group. A user is added to a special group whenever a new registration is required or when the user has lost their mobile device.
-
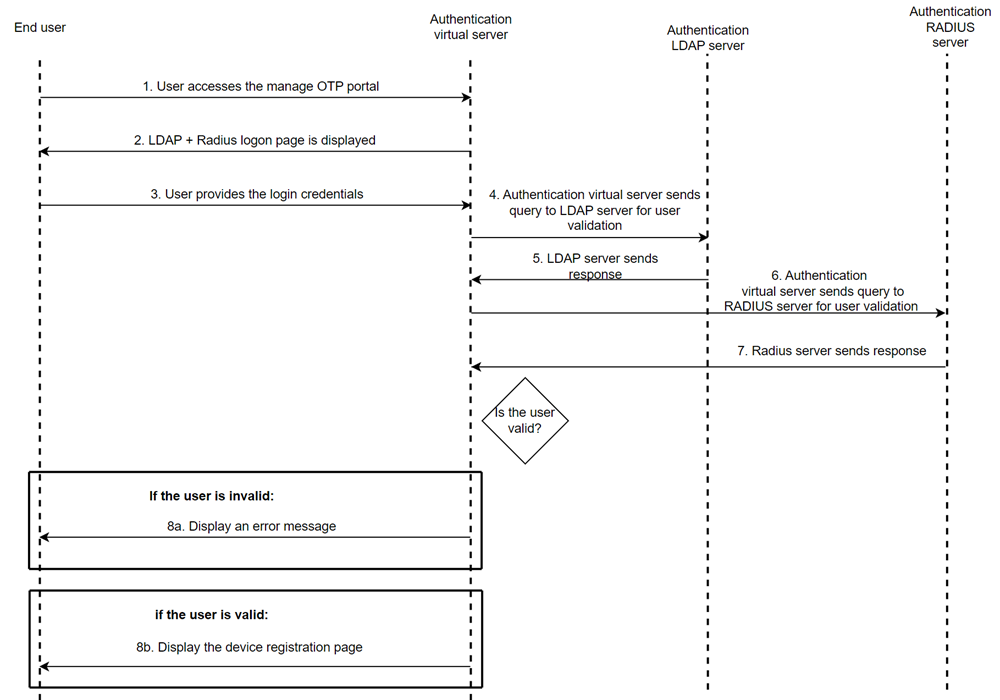
Approach 3: Introduce an additional factor along with LDAP authentication
In this approach, an additional validation factor is configured along for authentication. In this example, LDAP and RADIUS authentication methods are used for configuration.
Approach 1: Client IP address restriction
-
Configure the first factor. The first factor determines whether the client device is accessing the device registration page or attempting the native OTP multi-factor logon.
- Create an authentication policy for the device registration request.
add authentication Policy check_request_for_manageotp -rule "HTTP.REQ.COOKIE.VALUE(\"NSC_TASS\").EQ(\"manageotp\")" -action NO_AUTHN -
This factor determines whether the access is legitimate or not. NetScaler verifies if the client IP address is within the range of the configured corporate network IP addresses.
-
Create a login schema for the device registration flow.
add authentication loginSchema lschema_single_manage_otp -authenticationSchema "/nsconfig/loginschema/LoginSchema/SingleAuthManageOTP.xml" -
Create a device registration flow policy label for the second factor.
add authentication policylabel otp_manage_flow -loginSchema lschema_single_manage_otp -
Create an LDAP action for user validation.
add authentication ldapAction ldap_otp_action_for_manageotp -serverIP <LDAPServerIP> -ldapBase <LdapBase> -ldapBindDn <LdapAdminUser> -ldapBindDnPassword <LdapAdminPassword> -ldapLoginName samAccountName -groupAttrName memberOF -subAttributeName CN -
Create an authentication policy for user validation. The rule is based on the end user’s office network.
add authentication Policy ldap_otp_policy_for_manageotp -rule "CLIENT.IP.SRC.APPLY_MASK(255.255.255.0).EQ(10.140.200.0)" -action ldap_otp_action_for_manageotp
-
-
Configure the third factor. Based on the policy evaluation from the previous factor, the user is either allowed to access the device registration page or denied access with an appropriate error message.
-
Create an authentication policy for an invalid user access.
add authentication Policy noauthnotallowed -rule true -action NO_AUTHN -
Create a login schema for an invalid user access. You can customise the login schema based on your requirement for displaying the relevant message.
add authentication loginSchema notallowed -authenticationSchema "/nsconfig/loginschema/LoginSchema/InvalidFlow.xml" -
Create a policy label for the invalid user access and add a login schema.
add authentication policylabel notallowed -loginSchema notallowed -
Bind the policy to the
otp_manage_flowpolicy label to complete the invalid user access flow.bind authentication policylabel otp_manage_flow -policyName noauthnotallowed -priority 1000 -gotoPriorityExpression NEXT -nextFactor notallowed
-
-
Configure the fourth factor. In this factor, the user can add or remove their OTP device in the device registration page.
-
Create an LDAP action for valid user access, The user can register the devices in this factor.
add authentication ldapAction ldap_otp_register_action -serverIP <LDAPServerIP> -ldapBase <LdapBase> -ldapBindDn <LdapAdminUser> -ldapBindDnPassword <LdapAdminPassword> -ldapLoginName samAccountName -authentication DISABLED -OTPSecret userParameters -
Create an LDAP policy for valid user access.
add authentication Policy ldap_otp_register_policy -rule true -action ldap_otp_register_action -
Add an authentication policy label for valid user access.
add authentication loginSchema lschema_noschema -authenticationSchema noschema add authentication policylabel otp_manage_register_factor -loginSchema lschema_noschema <!--NeedCopy--> -
Bind the LDAP policy to the label for valid user access.
bind authentication policylabel otp_manage_register_factor -policyNamel ldap_otp_register_policy -priority 10 -
Bind the policy to the previous factor.
bind authentication policylabel otp_manage_flow -policyName ldap_otp_policy_for_manageotp -priority 1 -gotoPriorityExpression NEXT -nextFactor otp_manage_register_factor
-
-
Bind the device registration flow to the authentication virtual server to complete the flow.
bind authentication vserver authvs_otp -policy check_request_for_manageotp -priority 10 -nextFactor otp_manage_flow -gotoPriorityExpression NEXT
Examples:
-
A user accesses the device registration page from outside the office network and therefore denied access.
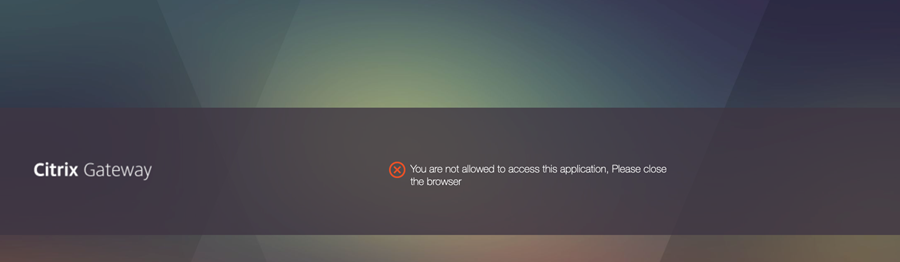
-
A user accesses the device registration page from the office network and therefore allowed access.

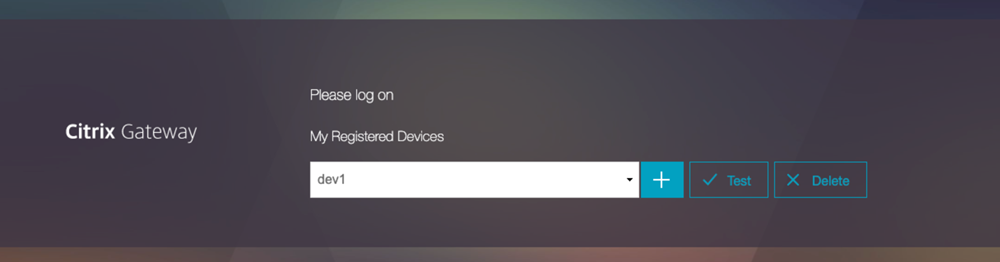
Use the following login schema to display an appropriate error message:
-
InvalidFlow.xml
<AuthenticateResponse xmlns="http://citrix.com/authentication/response/1"> <Status>success</Status> <Result>more-info</Result> <StateContext/> <AuthenticationRequirements> <PostBack>/nf/auth/doAuthentication.do</PostBack> <CancelPostBack>/nf/auth/doLogoff.do</CancelPostBack> <CancelButtonText>Cancel</CancelButtonText> <Requirements> <Req<AuthenticateResponse xmlns="http://citrix.com/authentication/response/1"> <Status>success</Status> <Result>more-info</Result> <StateContext/> <AuthenticationRequirements> <PostBack>/nf/auth/doAuthentication.do</PostBack> <CancelPostBack>/nf/auth/doLogoff.do</CancelPostBack> <CancelButtonText>Cancel</CancelButtonText> <Requirements> <Requirements> <Requirement> <Credential> <Type>none</Type> </Credential> <Label> <Text>You are not allowed to access this application, Please close the browser</Text> <Type>error</Type> </Label> <Input/> </Requirement> <Requirement> <Credential> <ID>error_okBtn</ID> <Type>error_okBtn</Type> </Credential> <Label> <Type>none</Type> </Label> </Requirement> </Requirements> </Requirements> </AuthenticationRequirements> </AuthenticateResponse> <!--NeedCopy-->
Approach 2: User group membership based restriction
-
Configure the first factor. This factor determines whether the client device is accessing the device registration page or attempting a native OTP multi-factor login.
-
Configure an authentication policy for the device registration request.
add authentication Policy check_request_for_manageotp -rule "HTTP.REQ.COOKIE.VALUE(\"NSC_TASS\").EQ(\"manageotp\")" -action NO_AUTHN
-
-
Configure the second factor. This factor determines if the access is legitimate. NetScaler fetches the group information from the LDAP server and verifies if the user belongs to a specific group configured for device registration. In the following example, the “allowmanageotp” group is used.
-
Create a login schema for the device registration flow.
add authentication loginSchema lschema_single_manage_otp -authenticationSchema "/nsconfig/loginschema/LoginSchema/SingleAuthManageOTP.xml" -
Create a device registration flow policy label for the second factor.
add authentication policylabel otp_manage_flow -loginSchema lschema_single_manage_otp -
Create an LDAP action for user validation.
add authentication ldapAction ldap_otp_action_for_manageotp -serverIP <LDAPServerIP> -ldapBase <LdapBase> -ldapBindDn <LdapAdminUser> -ldapBindDnPassword <LdapAdminPassword> -ldapLoginName samAccountName -groupAttrName memberOF -subAttributeName CN -
Create an authentication policy for user validation. The rule is based on the end user’s office network.
add authentication Policy ldap_otp_policy_for_manageotp -rule "AAA.USER.GROUPS.CONTAINS(\"allowedmanageotp\")" -action ldap_otp_action_for_manageotp
-
-
Configure the third factor. Based on the policy evaluation from the previous factor, NetScaler verifies the group membership based on the LDAP server’s response. If a valid group membership is found, then the user is allowed to access the device registration page or is denied access with an appropriate error message.
-
Create an authentication policy for invalid user access.
add authentication Policy noauthnotallowed -rule true -action NO_AUTHN -
Create a login schema for invalid user access. You can customise the login schema based on your requirement for displaying the relevant message.
add authentication loginSchema notallowed -authenticationSchema "/nsconfig/loginschema/LoginSchema/InvalidFlow.xml" -
Create a policy label for invalid user access and add the login schema.
add authentication policylabel notallowed -loginSchema notallowed -
Bind the policy to the
otp_manage_flowpolicy label to complete the invalid user access flow.bind authentication policylabel otp_manage_flow -policyName noauthnotallowed -priority 1000 -gotoPriorityExpression NEXT -nextFactor notallowed
-
-
Configure the fourth factor. This factor determines where the user can add or remove their OTP device on the device registration page. Based on the policy evaluation of the previous factor, the actual user device registration happens in this factor.
-
Create an LDAP action for valid user access. The user registers their device in this factor.
add authentication ldapAction ldap_otp_register_action -serverIP <LDAPServerIP> -ldapBase <LdapBase> -ldapBindDn <LdapAdminUser> -ldapBindDnPassword <LdapAdminPassword> -ldapLoginName samAccountName -authentication DISABLED -OTPSecret userParameters -
Create an LDAP policy for valid user access.
add authentication Policy ldap_otp_register_policy -rule true -action ldap_otp_register_action -
Add an authentication policy label for valid user access.
add authentication loginSchema lschema_noschema -authenticationSchema noschema add authentication policylabel otp_manage_register_factor -loginSchema lschema_noschema <!--NeedCopy--> -
Bind the LDAP policy to the policy label for valid user access.
bind authentication policylabel otp_manage_register_factor -policyNamel ldap_otp_register_policy -priority 10 -
Bind the policy to the previous factor.
bind authentication policylabel otp_manage_flow -policyName ldap_otp_policy_for_manageotp -priority 1 -gotoPriorityExpression NEXT -nextFactor otp_manage_register_factor -
Bind the device registration flow to the authentication virtual server to complete the overall flow.
bind authentication vserver authvs_otp -policy check_request_for_manageotp -priority 10 -nextFactor otp_manage_flow -gotoPriorityExpression NEXT
-
Example:
A user who is outside of the allowed device registration group attempts to access the device registration page through the office network. The user is denied access to the portal.
For details about the login schema to be used for this configuration, refer to Approach 1: Client IP address restriction.

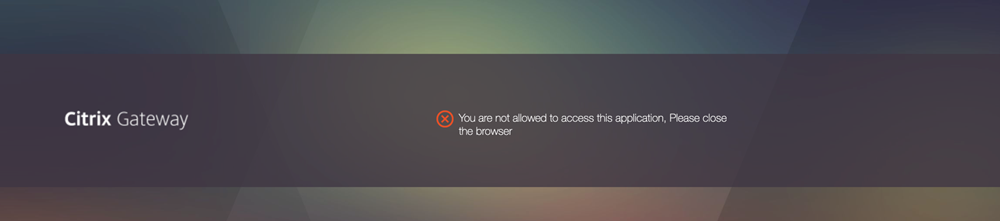
Approach 3: Introduce an additional factor along with LDAP authentication
-
Configure the first factor. This factor determines whether the user is accessing the device registration page or attempting a native OTP multifactor logon.
-
Authentication policy for the device registration request.
add authentication Policy check_request_for_manageotp -rule "HTTP.REQ.COOKIE.VALUE(\"NSC_TASS\").EQ(\"manageotp\")" -action NO_AUTH
-
-
Configure the second factor. In this factor, NetScaler verifies if the client IP address belongs to the office network.
In this example, the
DualAuthManageOTP.xmllogin schema is used. This login schema requests the user for the LDAP and RADIUS credentials.- Create a login schema for the device registration flow.
`add authentication loginSchema dualauth_manageOTP -authenticationSchema "/nsconfig/loginschema/LoginSchema/DualAuthManageOTP.xml"`-
Add a policy label for the device registration flow.
add authentication policylabel otp_manage_flow -loginSchema dualauth_manageOTP -
Add an LDAP authentication action for user validation.
add authentication ldapAction ldap_otp_action_for_manageotp -serverIP <LDAPServerIP> -ldapBase <LdapBase> -ldapBindDn <LdapAdminUser> -ldapBindDnPassword <LdapAdminPassword> -ldapLoginName samAccountName -
Add an LDAP authentication policy for user validation.
add authentication Policy ldap_pol_for_manageOTP -rule true -action ldap_action_for_manageOTP
-
Configure the third factor, an additional factor after LDAP, to further secure access to the device registration page. In this factor, the RADIUS policy is added to verify the user identity with the RADIUS server. If the user’s client IP address matches the office subnet range, then the user is allowed to access the device registration page. If not, the user is denied access with an appropriate error message. Based on the policy evaluation of the previous factor, the actual user device registration happens in this factor.
-
Add the
noschemalogin schema.add authentication loginSchema lschema_noschema -authenticationSchema noschema -
Add a policy label for RADIUS authentication.
add authentication policylabel radius_label_for_mangeOTP -loginSchema lschema_noschema -
Add an authentication policy for RADIUS authentication.
add authentication Policy rad_pol_for_manageOTP -rule true -action rad_act_for_manageOTP -
Add an authentication action for RADIUS authentication.
add authentication radiusAction rad_act_for_manageOTP -serverIP <RADIUS Server IP> -radKey <RADIUSKEY> -
Bind the RADIUS factor to the previous policy label.
bind authentication policylabel otp_manage_flow -policyName ldap_pol_for_manageOTP -priority 10 -gotoPriorityExpression NEXT -nextFactor radius_label_for_mangeOTP
-
-
Configure the fourth factor. This factor is where the user can add or remove their OTP device on the device registration page.
-
Add a policy label for device registration.
add authentication policylabel ldap_label_for_mangeOTP_registration -loginSchema lschema_noschema -
Add an authentication LDAP action for OTP device registration.
add authentication ldapAction ldap_action_for_manageOTP_registration -serverIP <LDAPServerIP> -ldapBase <LdapBase> -ldapBindDn <LdapAdminUser> -ldapBindDnPassword <LdapAdminPassword> -ldapLoginName samAccountName -authentication DISABLED -OTPSecret userParameters -
Add an authentication policy for OTP device registration.
add authentication Policy ldap_pol_for_manageOTP_registration -rule true -action ldap_action_for_manageOTP_registration -
Bind the authentication policy to the policy label.
bind authentication policylabel ldap_label_for_manageOTP_registration -policyName ldap_pol_for_manageOTP_registration -priority 10 -
Bind the policy label to the previous factor.
bind authentication policylabel radius_label_for_mangeOTP -policyName rad_pol_for_manageOTP -priority 1 -gotoPriorityExpression NEXT -nextFactor ldap_label_for_mangeOTP_registration
-
-
Complete the nFactor flow by binding the first factor to the authentication virtual server.
bind authentication vserver authvs_otp -policy check_OTP_manageRequest -priority 10 -nextFactor otp_manage_flow
Examples:
-
A user accesses the device registration page and is prompted to provide the LDAP credentials and the RADIUS password.
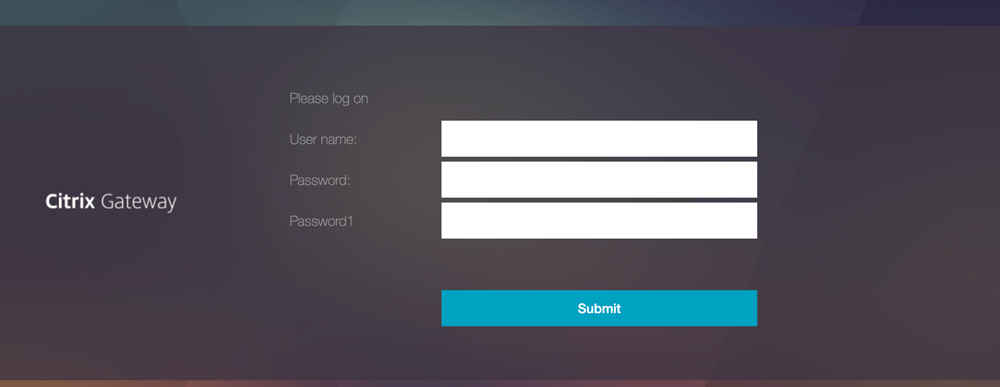
-
A user provides the required fields and therefore is allowed to access the device registration page.
Use the following login schema in this configuration where an additional authentication method is introduced after AD based authentication:
-
DualAuthManageOTP.xml
<?xml version="1.0" encoding="UTF-8" standalone="yes"?> <AuthenticateResponse xmlns="http://citrix.com/authentication/response/1"> <Status>success</Status> <Result>more-info</Result> <StateContext/> <AuthenticationRequirements> <PostBack>/nf/auth/doAuthentication.do</PostBack> <CancelPostBack>/nf/auth/doLogoff.do</CancelPostBack> <CancelButtonText>Cancel</CancelButtonText> <Requirements> <Requirement> <Credential> <Type>none</Type> </Credential> <Label> <Text>dualauth_please_log_on</Text> <Type>nsg-login-label</Type> </Label> <Input/> </Requirement> <Requirement> <Credential> <ID>login</ID> <SaveID>login</SaveID> <Type>username</Type> </Credential> <Label> <Text>dualauth_user_name</Text> <Type>nsg-login-label</Type> </Label> <Input> <Text> <ReadOnly>false</ReadOnly> <InitialValue/> <Constraint>.+</Constraint> </Text> </Input> </Requirement> <Requirement> <Credential> <ID>passwd</ID> <SaveID>passwd</SaveID> <Type>password</Type> </Credential> <Label> <Text>dualauth_password</Text> <Type>nsg-login-label</Type> </Label> <Input> <Text> <Secret>true</Secret> <Constraint>.+</Constraint> </Text> </Input> </Requirement> <Requirement> <Credential> <ID>passwd1</ID> <SaveID>passwd1</SaveID> <Type>password</Type> </Credential> <Label> <Text>Password1</Text> <Type>nsg-login-label</Type> </Label> <Input> <Text> <Secret>true</Secret> <Constraint>.+</Constraint> </Text> </Input> </Requirement> <Requirement> <Credential> <ID>otpmanage</ID> <Type>otpmanage</Type> </Credential> <Input> <Text> <Secret>false</Secret> <Hidden>true</Hidden> <InitialValue>1</InitialValue> <Constraint>.+</Constraint> </Text> </Input> </Requirement> <Requirement> <Credential> <ID>pushregister</ID> <Type>nsg_registerpush</Type> </Credential> <Input> <Text> <Secret>false</Secret> <Hidden>true</Hidden> <InitialValue>1</InitialValue> <Constraint>.+</Constraint> </Text> </Input> </Requirement> <Requirement> <Credential> <ID>otpregister</ID> <Type>nsg_registerotp</Type> </Credential> <Input> <Text> <Secret>false</Secret> <Hidden>true</Hidden> <InitialValue>1</InitialValue> <Constraint>.+</Constraint> </Text> </Input> </Requirement> <Requirement> <Credential> <ID>savecredentials</ID> <SaveID/> <Type>savecredentials</Type> </Credential> <Label> <Text>dualauth_remember_my_credentials</Text> <Type>nsg-login-label</Type> </Label> <Input> <AssistiveText>dualauth_</AssistiveText> <CheckBox> <InitialValue>false</InitialValue> </CheckBox> </Input> </Requirement> <Requirement> <Credential> <ID>Logon</ID> <Type>none</Type> </Credential> <Label> <Type>none</Type> </Label> <Input> <Button>dualauth_submit</Button> </Input> </Requirement> </Requirements> </AuthenticationRequirements> </AuthenticateResponse> <!--NeedCopy-->
NetScaler login
To configure the NetScaler login flow:
-
Configure the first factor. This factor determines whether this is a login request or a device registration request.
-
Add an authentication policy for OTP login flow.
add authentication Policy otp_login_pol -rule true -action NO_AUTHN
-
-
Configure the second factor. In this factor, a login schema that prompts the user for the credentials (user name, password, and OTP passcode) is added. To validate the user identity, an LDAP action is added in this factor.
-
Add a login schema to display the user login page.
add authentication loginSchema dualauth_login -authenticationSchema "LoginSchema/DualAuth.xml" -
Add a policy label for user login and attach the login schema.
add authentication policylabel otp_login_flow -loginSchema dualauth_login -
Add an LDAP action for user login.
add authentication ldapAction ldap_act_for_validation -serverIP <LDAPServerIP> -ldapBase <LdapBase> -ldapBindDn <LdapAdminUser> -ldapBindDnPassword <LdapAdminPassword> -ldapLoginName samAccountName -groupAttrName memberOF -subAttributeName CN add authentication Policy ldap_pol_for_validation -rule true -action ldap_act_for_validation <!--NeedCopy-->
-
-
Configure the third factor. Validation of OTP is done in this factor. An LDAP action that is used for OTP passcode validation is added here.
-
Add a policy label for the user OTP validation.
add authentication policylabel otp_validation_login_factor -loginSchema LSCHEMA_INT -
Add an LDAP action for user OTP validation.
add authentication ldapAction ldap_otp_validate_action -serverIP <LDAPServerIP> -ldapBase <LdapBase> -ldapBindDn <LdapAdminUser> -ldapBindDnPassword <LdapAdminPassword> -ldapLoginName samAccountName -authentication DISABLED -OTPSecret userParameters -
Add an authentication policy for user OTP validation.
add authentication policy ldap_otp_validate_pol -action ldap_otp_validate_action -rule true -
Bind the policy to the policy label.
bind authentication policylabel otp_validation_login_factor -policyName ldap_otp_validate_pol -priority 100 -
Bind the current policy label as the next factor for the OTP login flow.
bind authentication policylabel otp_login_flow -policyName aaa_local_pwd_pol -priority 100 -nextFactor otp_validation_login_factor
-
-
Complete the login flow by binding the first factor to the authentication virtual server.
bind authentication vserver authvs_otp -policy otp_login_pol -nextfactor otp_login_flow -priority 100
For more information about NetScaler login, see Native OTP workflow.