Configure EULA as an authentication factor in NetScaler nFactor system
The following figure displays an end-user logon flow with EULA. In this flow, existing first factor is moved to after the EULA. EULA becomes a first/vserver profile with previous first factor becoming a second factor.
Note:
This feature is available with the NetScaler Enterprise and Premium edition licenses.
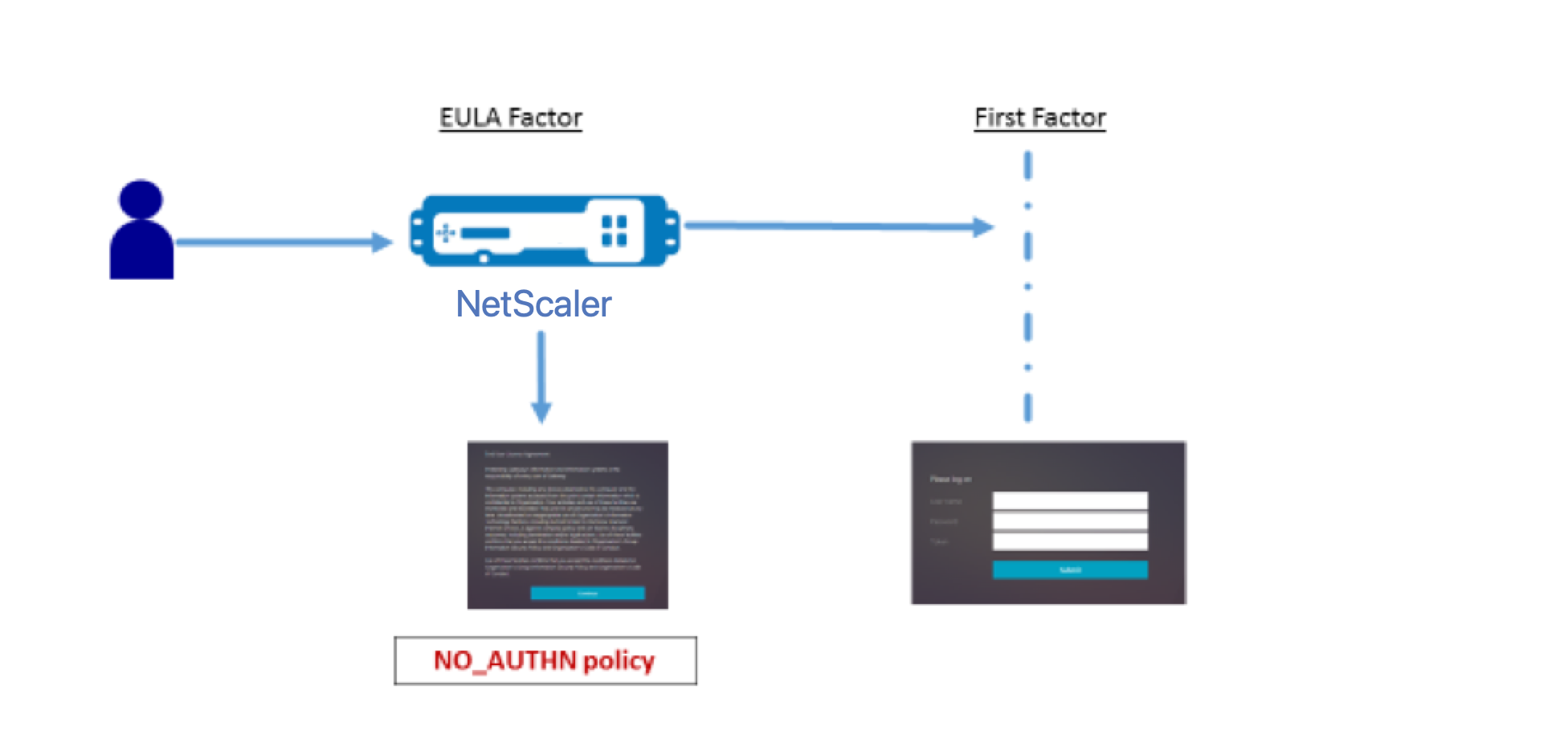
nFactor flow presentation
The setup can also be created through nFactor Visualizer present in ADC version 13.0 and above.
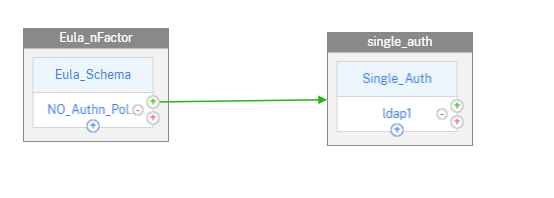
Configuration by using the CLI
- Copy eula.xml to /nsconfig/loginschema on your NetScaler. The login schema used in this example is present in NetScaler version 13.0 and need not be created separately. For more information on the login schema, see the last section of this page.
-
Add a login schema for EULA.
add authentication loginSchema eulaschema -authenticationSchema eula.xml add authentication loginSchemaPolicy eula_schema -rule true -action eulaschema bind authentication vserver auth -policy eula_schema -priority 5 <!--NeedCopy--> -
Add authentication factor as a secondary factor.
add authentication loginSchema single_auth -authenticationSchema "LoginSchema/SingleAuth.xml" add authentication policylabel single_factor -loginSchema single_auth bind authentication policylabel single_factor -policyName ldap-adv -priority 5 <!--NeedCopy--> -
Add no-auth policy at the virtual server cascade.
add authentication Policy noauth_pol -rule "http.req.url.contains(\"/nf/auth/doAuthentication.do\")" -action NO_AUTHN bind authentication vserver auth -policy noauth_pol -priority 1 -nextFactor single_factor -gotoPriorityExpression NEXT <!--NeedCopy-->
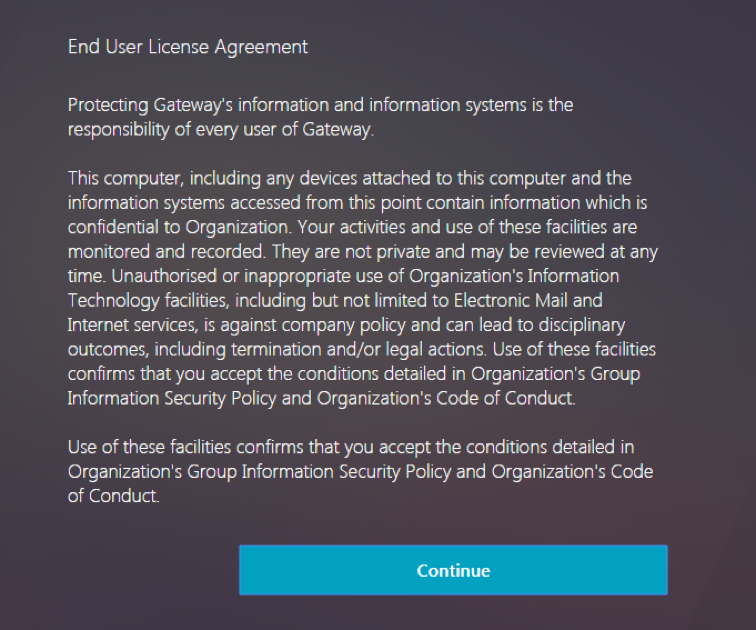
The following screen capture is of the EULA that is configured at virtual server as a factor.
Configuration by using the nFactor Visualizer
-
Navigate to Security > AAA-Application Traffic > nFactor Visualizer > nFactor Flow and click Add.
-
Click the + sign to add the nFactor flow.
-
Add a factor. The name that you enter is the name of the nFactor flow.
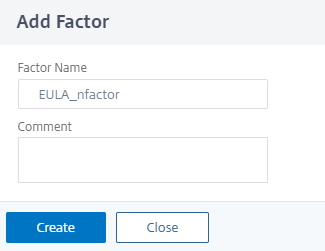
-
Click Add Schema to add a schema for the first factor and then click Add.
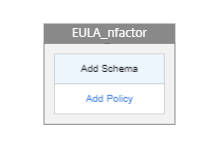
-
Create a EULA_Schema by selecting the eula.xml login schema.
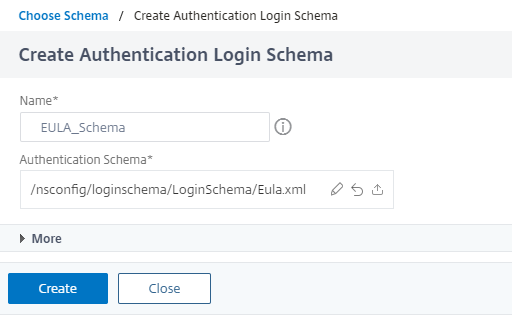
-
Choose the schema for first factor, that is the EULA.
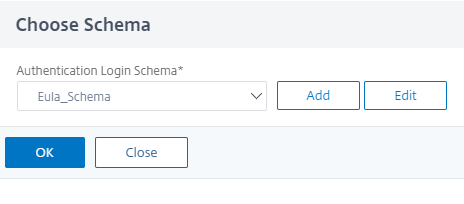
-
Click Add Policy to create an authentication Policy for NO_AUTHN and then click Add.
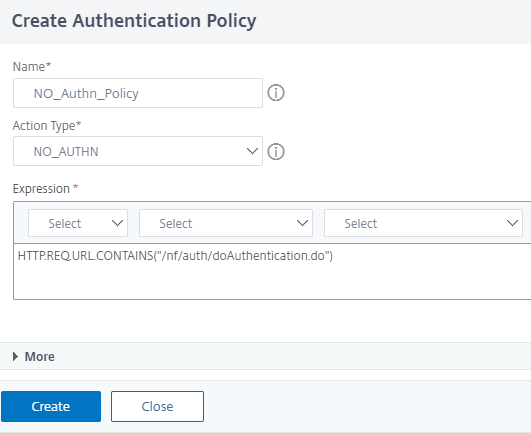
-
Click the green + sign add the next factor, that is single_auth.
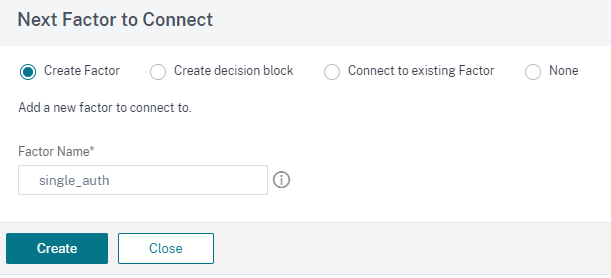
-
Click Add Schema again to add a schema for the second factor and then click Add.
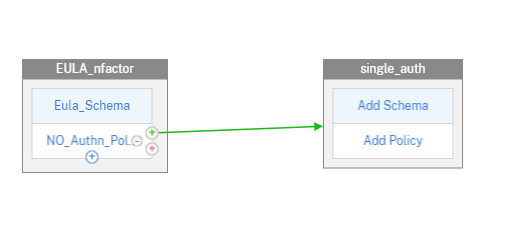
-
Create a single_auth schema by selecting the Single_Auth.xml login schema and then click Create.
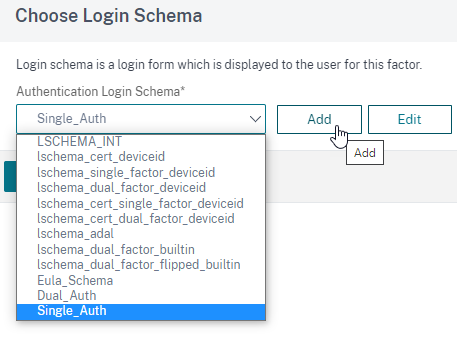
-
Click Add Policy to select a policy for LDAP authentication and then click Add.
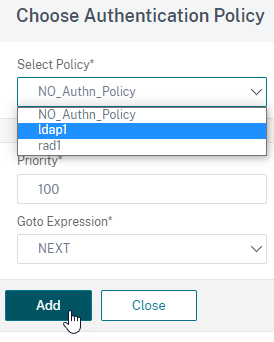
For details about creating LDAP authentication see, Configuring LDAP Authentication.
-
Click Done The configuration is saved.
-
Click Bind to Authentication Server, select the nFactor flow just created to bind the flow to an authentication, authorization, and auditing virtual server and then click Create.
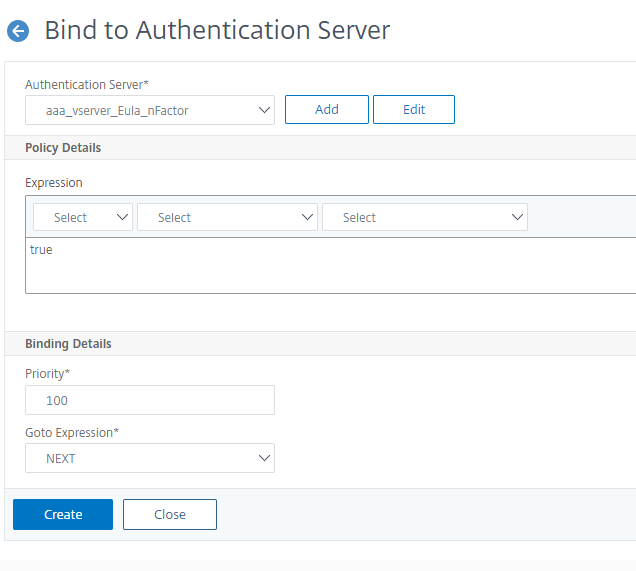
Note: Bind and Unbind the nFactor flow through the option given in nFactor flow under Show Bindings only.
To unbind the nFactor flow
-
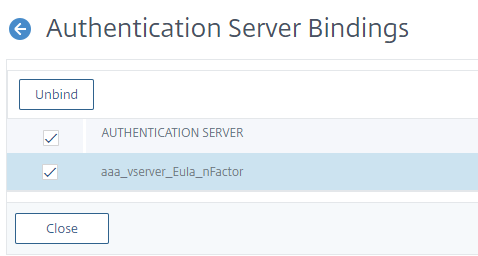
Select the nFactor flow and click Show Bindings.
-
Select the authentication virtual server to which the nFactor flow is bound and click Unbind.
Login schema used in this example
When copying text from web browser, certain quotes are rendered differently. It is recommended that you copy the schema in a text editor to normalize quotes.
Note: This login Schema is present in NetScaler version 13.0 and need not be created separately.
<?xml version="1.0" encoding="UTF-8"?>
<AuthenticateResponse xmlns="http://citrix.com/authentication/response/1">
<Status>success</Status>
<Result>more-info</Result>
<StateContext></StateContext>
<AuthenticationRequirements>
<PostBack>/nf/auth/doAuthentication.do</PostBack>
<CancelPostBack>/nf/auth/doLogoff.do</CancelPostBack>
<CancelButtonText>Cancel</CancelButtonText>
<Requirements>
<Requirement><Credential><Type>none</Type></Credential><Label><Text>End User License Agreement</Text><Type>heading</Type></Label><Input /></Requirement>
<Requirement><Credential><Type>none</Type></Credential><Label><Text>Protecting Gateway's information and information systems is the responsibility of every user of Gateway.</Text><Type>plain</Type></Label><Input /></Requirement>
<Requirement><Credential><Type>none</Type></Credential><Label><Text>This computer, including any devices attached to this computer and the information systems accessed from this point contain information which is confidential to Organization. Your activities and use of these facilities are monitored and recorded. They are not private and may be reviewed at any time. Unauthorised or inappropriate use of Organization's Information Technology facilities, including but not limited to Electronic Mail and Internet services, is against company policy and can lead to disciplinary outcomes, including termination and/or legal actions. Use of these facilities confirms that you accept the conditions detailed in Organization's Group Information Security Policy and Organization's Code of Conduct.</Text><Type>plain</Type></Label><Input /></Requirement>
<Requirement><Credential><Type>none</Type></Credential><Label><Text>Use of these facilities confirms that you accept the conditions detailed in Organization's Group Information Security Policy and Organization's Code of Conduct.</Text><Type>plain</Type></Label><Input /></Requirement>
<Requirement><Credential><ID>loginBtn</ID><Type>none</Type></Credential><Label><Type>none</Type></Label><Input><Button>Continue</Button></Input></Requirement>
</Requirements>
</AuthenticationRequirements>
</AuthenticateResponse>
<!--NeedCopy-->