Configure NetScaler Gateway preauthentication EPA scan for the domain check
You can configure NetScaler Gateway preauthentication EPA scan to check if the user device is domain-joined or not. For the scan to pass, the client machine must be domain-joined to the domain whose suffix is configured in the EPA policy.
After enabling the scan, test it with a client machine that has a domain membership matching the configured suffix. Then, test again with a non-domain-joined or mismatched-domain client to verify that the policy correctly blocks access.
You can configure preauthentication EPA scan using an advanced or a classic authentication policy. We recommend you to use an advanced authentication policy because classic policies are deprecated in future releases.
Preauthentication EPA scan configuration by using the advanced authentication policy
High level steps involved in this configuration
-
Preauthentication EPA scan for domain check validates if the domain suffix of the client machine matches the domain configured in the preauthentication policy.
-
If the EPA scan passes, the authentication process proceeds to the next configured authentication factor (for example, LDAP).
-
If the EPA scan fails, the connection is denied before the next authentication factor is attempted.
Pre-requisites
It is assumed that the following configurations are in place:
-
An authentication virtual server to host the advanced authentication policy.
-
An authentication profile must be linked to the VPN virtual server so that the “EPA -> next authentication factor” flow applies to VPN logins.
Configuration by using the GUI
-
Navigate to Security > AAA - Application Traffic > Policies > Authentication > Advanced Policies > Actions > EPA.
-
On the Authentication EPA Action page, click Add.
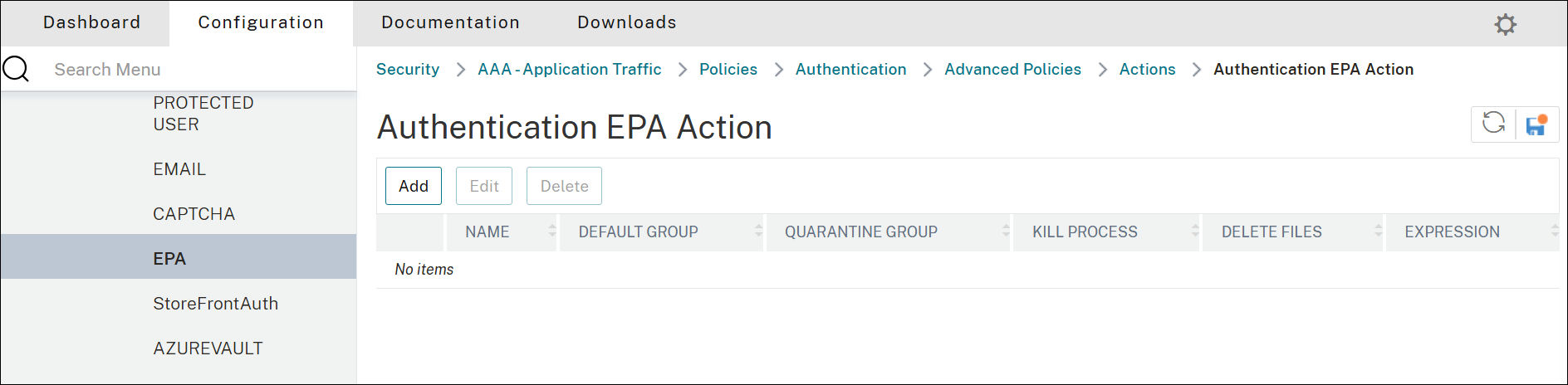
-
In Name, enter a name for the EPA action.
-
Click EPA Editor.
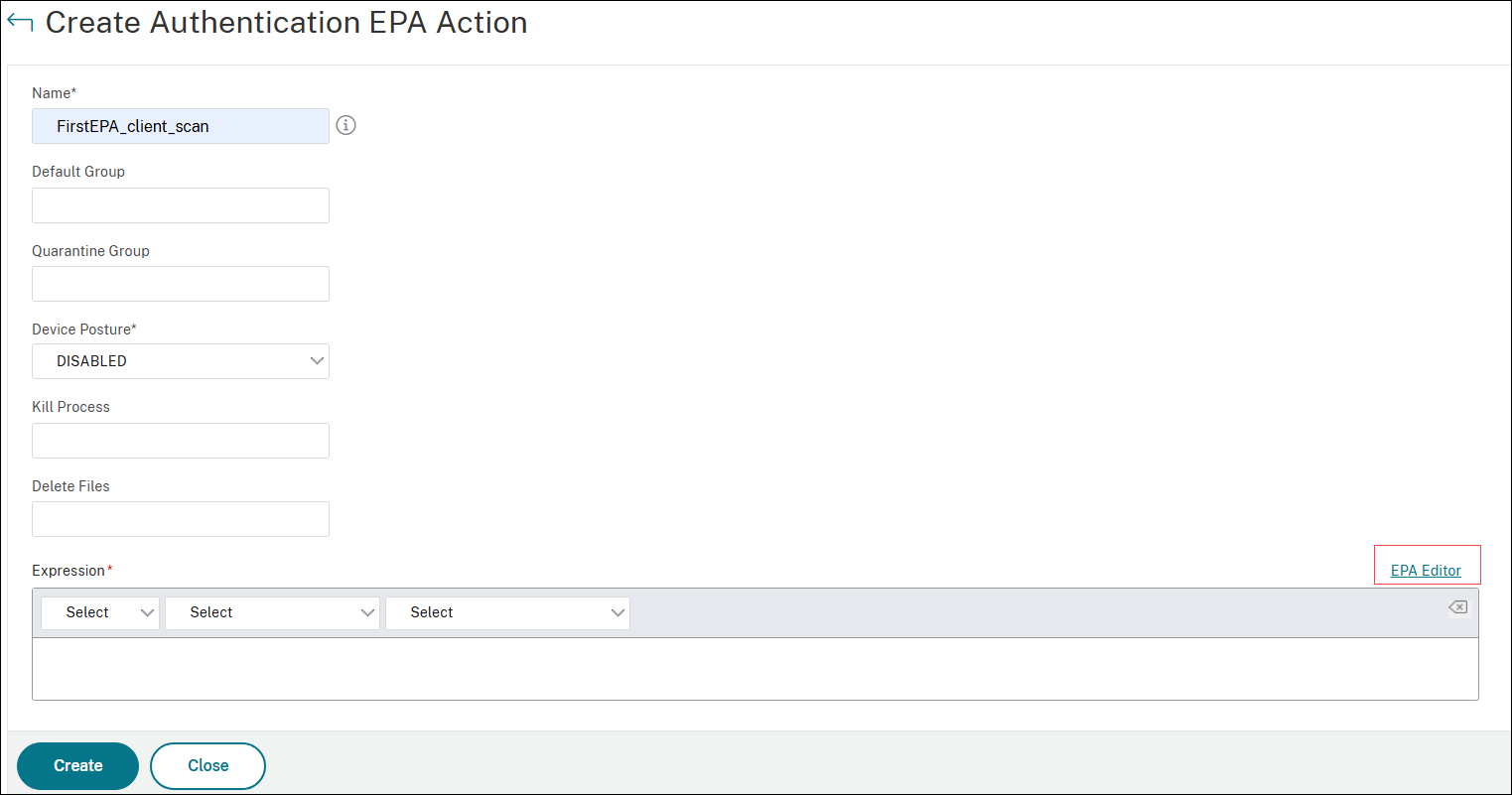
-
On the Expression Editor page, select Windows and then Domain check in the drop-down menus.
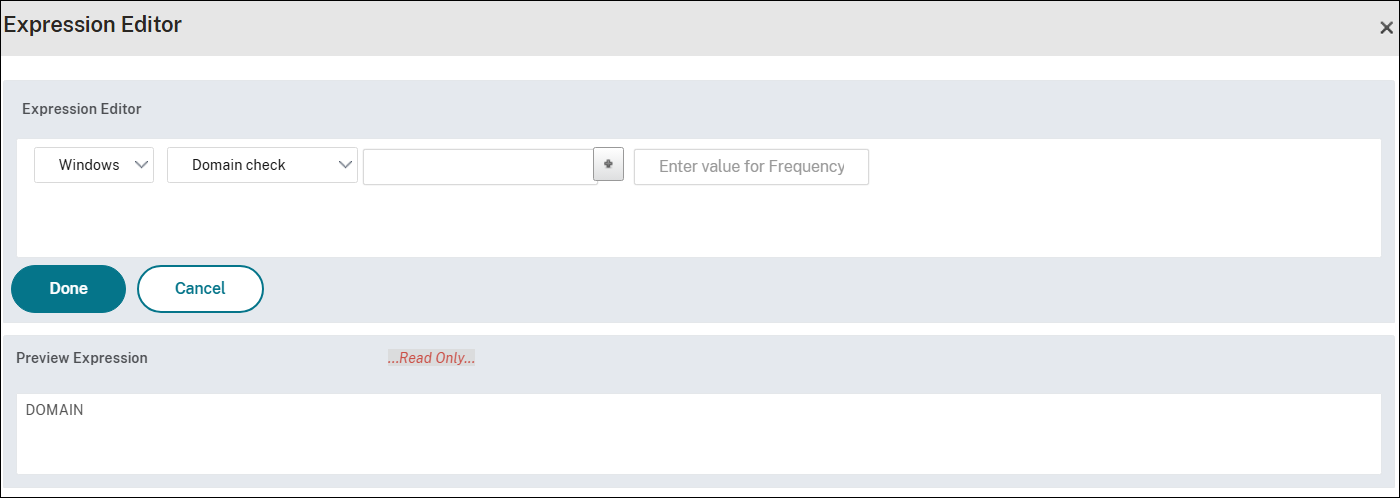
-
Click the + sign and in Domain suffix, select anyof.
-
In the textbox next to Domain suffix, enter the domain name to be scanned and click OK.
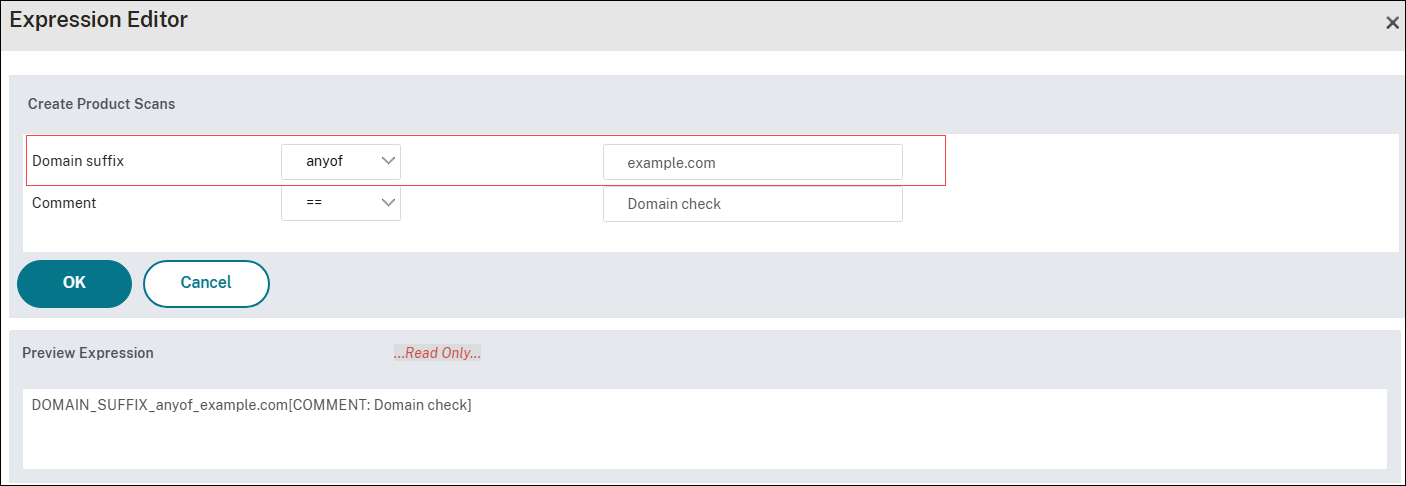
-
On the Expression Editor page, validate the Preview Expression and click Done.
-
Click Create.
Configuration by using the CLI
-
Configure an EPA Action to check if the client’s domain suffix matches the configured domain.
add authentication epaAction adv_epa_act -csecexpr "sys.client_expr(\"sys_0_DOMAIN_SUFFIX_anyof_example.com[COMMENT: Domain check]\")" <!--NeedCopy--> -
Configure an EPA policy.
add authentication Policy adv_epa_pol -rule true -action adv_epa_act <!--NeedCopy--> -
Bind the EPA policy to the authentication virtual server with the next authentication factor. For example, the following command uses LDAP as the next authentication factor.
bind authentication vserver authn_vserver -policy adv_epa_pol -priority 100 -nextFactor adv_ldap_pol_label -gotoPriorityExpression NEXT <!--NeedCopy--> -
Bind the policy to the policy label. For example, the following command binds an LDAP policy to an LDAP policy label.
bind authentication policylabel adv_ldap_pol_label -policyName adv_ldap_pol -priority 100 -gotoPriorityExpression END <!--NeedCopy-->
Preauthentication EPA scan configuration by using the classic authentication policy
Configuration by using the GUI
- Navigate to NetScaler Gateway > Policies > Preauthentication.
-
Click the Preauthentication Profiles, tab and then click Add.
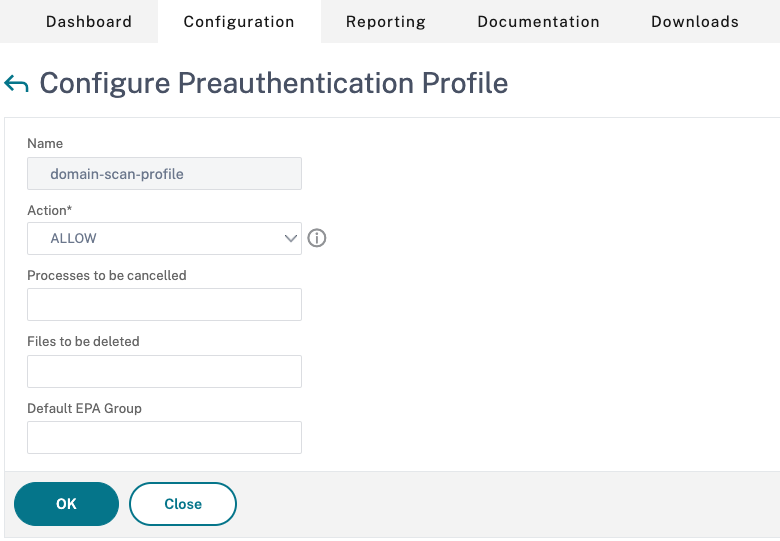
- Enter a name for the new profile, and click Create.
- Switch to the Preauthentication Policies tab and click Add.
- Enter a name for the policy.
- In Request Action, choose the previously created domain scan profile.
- In Expression, click OPSWAT EPA Editor.
-
In Expression Editor, select Windows to scan Windows based systems, and then choose Domain Check.
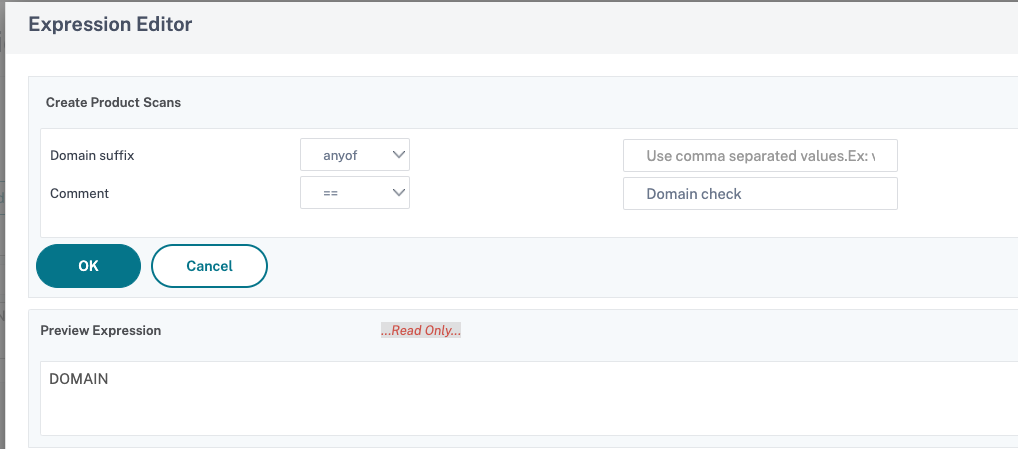
- Click + and enter the domain suffix and comment, if any. In this example, ‘example.com’ is used as the domain suffix.
-
Click OK and then click Done.
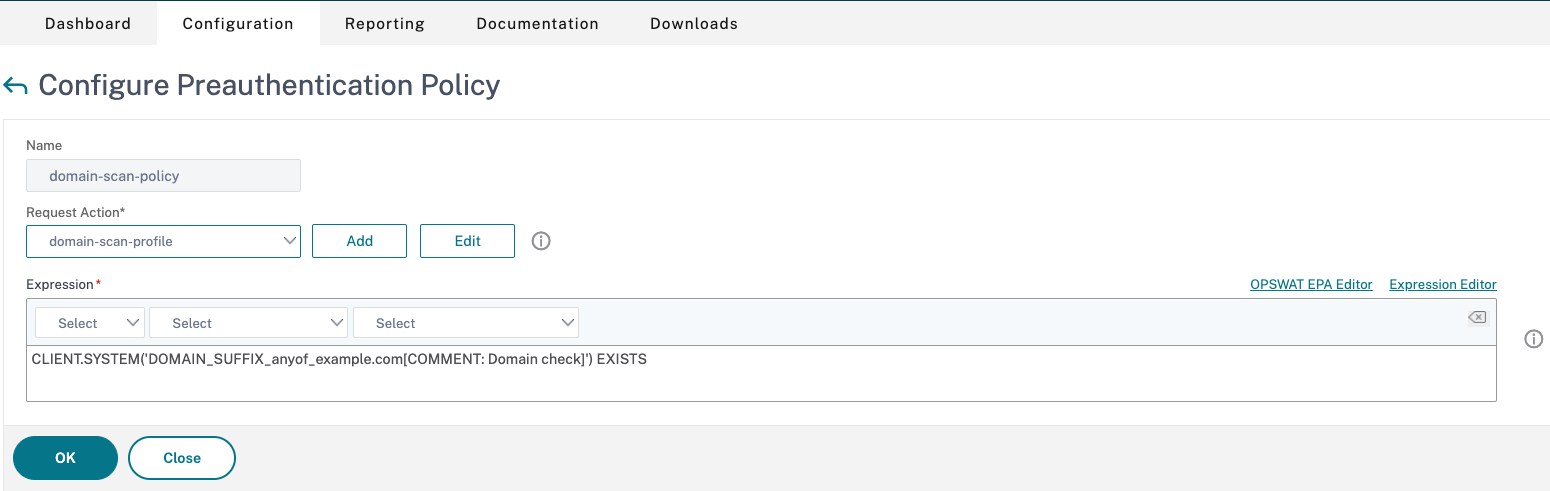
- On the Create Preauthentication Policy page, click Create.
- Bind the policy to the virtual server to enable the policy.
- Navigate to NetScaler Gateway > Virtual Servers.
- Select the virtual server, and then click Edit.
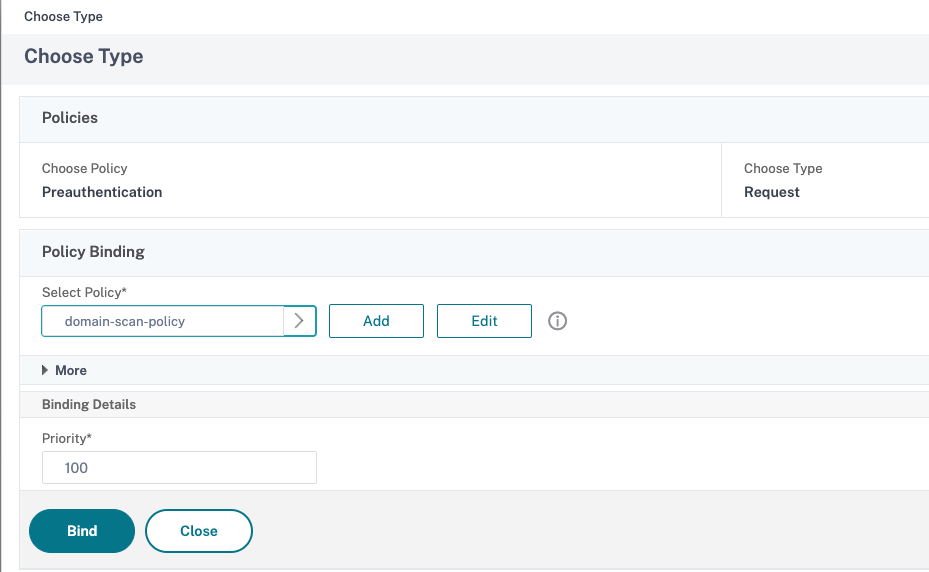
- In the Policies section, click the + sign.
- In Choose Policy, select Preauthentication, and then click Continue.
- In Select Policy, select the policy created for domain scan, and then click Bind.
- Click Done. The Policies pane displays the other policies and the new preauthentication policy bound to the virtual server.
Configuration by using the CLI
To enable preauthentication policy for domain check, at the command prompt, type:
add aaa preauthenticationaction domainCheckEPAAction ALLOW
add aaa preauthenticationpolicy domainCheckEPAPolicy "CLIENT.SYSTEM(\'DOMAIN_SUFFIX_anyof_example.com[COMMENT: Allow example.com]\') EXISTS" domainCheckEPAAction
<!--NeedCopy-->