Logging and Monitoring LSN
You can log LSN information to diagnose, troubleshoot problems, and to meet legal requirements. You can monitor the performance of the LSN feature by using LSN statistical counters and displaying current LSN sessions.
Logging LSN
Logging LSN information is one of the important functions required by the ISPs to meet legal requirements and for identifying the source of traffic at any given time.
A NetScaler appliance logs LSN mapping entries and the LSN sessions created or deleted for each LSN group. You can control logging of LSN information for an LSN group by using the logging and session logging parameters of the LSN group. These are group level parameters and are disabled by default. The NetScaler appliance logs LSN sessions for an LSN group only when both logging and session logging parameters are enabled.
The following table displays the logging behavior for an LSN group for various settings of logging and session logging parameters.
| Logging | Session Logging | Logging Behavior |
|---|---|---|
| Enabled | Enabled | Logs LSN mapping entries as well as LSN sessions. |
| Enabled | Disabled | Logs LSN mapping entries but not LSN sessions. |
| Disabled | Enabled | Logs neither mapping entries nor LSN sessions. |
A log message for an LSN mapping entry consists of the following information:
- NetScaler owned IP address (NSIP address or SNIP address) from which the log message is sourced.
- Time stamp
- Entry type (MAPPING)
- Whether the LSN mapping entry was created or deleted
- Subscriber’s IP address, port, and traffic domain ID
- NAT IP address and port
- Protocol name
- Destination IP address, port, and traffic domain ID might be present, depending on the following conditions:
- Destination IP address and port are not logged for Endpoint-Independent mapping.
- Only the destination IP address is logged for Address-Dependent mapping. The port is not logged.
- Destination IP address and port are logged for Address-Port-Dependent mapping.
A log message for an LSN session consists of the following information:
- NetScaler owned IP address (NSIP address or SNIP address) from which the log message is sourced.
- Time stamp
- Entry type (SESSION)
- Whether the LSN session is created or removed
- Subscriber’s IP address, port, and traffic domain ID
- NAT IP address and port
- Protocol name
- Destination IP address, port, and traffic domain ID
The appliance uses its existing syslog and audit log framework to log LSN information. You must enable global level LSN logging by enabling the LSN parameter in the related NSLOG action and SYLOG action entities. When the Logging parameter is enabled, the NetScaler appliance generates log messages related to LSN mappings and LSN sessions of this LSN group. The appliance then sends these log messages to servers associated with the NSLOG action and SYSLOG action entities.
For logging LSN information, Citrix® recommends:
- Logging the LSN information on external log servers instead of on the NetScaler appliance. Logging on external servers facilitates optimal performance when the appliance creates large amounts of LSN log entries (in order of millions).
-
Using SYSLOG over TCP, or NSLOG. By default SYSLOG uses UDP, and NSLOG uses only TCP to transfer log information to the log servers. TCP is more reliable than UDP for transferring complete data.
Note:
- The SYSLOG generated on NetScaler appliance are dynamically sent to the external log servers.
- When using SYSLOG over TCP, if the TCP connection is down or the SYSLOG server is busy, then the NetScaler appliances stores the logs in buffer and send the data once the connection is active.
For more information about configuring logging, see Audit Logging.
Configuring LSN logging consists of the following tasks:
-
Configuring the NetScaler appliance for logging. This task involves creating and setting various entities and parameters of the NetScaler appliance:
-
Create a SYSLOG or NSLOG audit logging configuration. Creating an audit logging configuration involves the following tasks:
- Create a NSLOG or SYSLOG audit action and enable the LSN parameter. Audit actions specify the IP addresses of log servers.
- Create a SYSLOG or NSLOG audit policy and bind the audit action to the audit policy. Audit actions specify the IP addresses of log servers. Optionally, you can set the transport method for log messages that are sent to the external log servers. By default UDP is selected, you can set the transport method as TCP for a reliable transport mechanism.Bind the audit policy to system global.
- Create a SYSLOG or NSLOG audit policy and bind the audit action to the audit policy.
- Bind the audit policy to system global. Note: For an existing audit logging configuration, just enable the LSN parameter for logging LSN information in the server specified by the audit action.
- Enable logging and session logging parameters. Enable logging and session logging parameters either as you add LSN groups or after you have created the groups. The NetScaler appliance generates log messages related to these LSN groups and sends them to the server of those audit actions that have the LSN parameter enabled.
-
Create a SYSLOG or NSLOG audit logging configuration. Creating an audit logging configuration involves the following tasks:
- Configuring log servers. This task involves installing SYSLOG or NSLOG packages on the desired servers. This task also involves specifying the NSIP address of the NetScaler appliance in the configuration file of SYSLOG or NSLOG. Specifying the NSIP address enables the server to identify the log information sent by the NetScaler appliance for storing them in a log file.
For more information about configuring logging, see Audit Logging.
SYSLOG Configuration Using the CLI
To create a SYSLOG server action for LSN logging by using the command line interface
At the command prompt, type:
add audit syslogAction <name> <serverIP> [-serverPort <port>] -logLevel <logLevel>... [-transport (TCP)] [-lsn ( ENABLED | DISABLED )]
<!--NeedCopy-->
To create a SYSLOG server policy for LSN logging by using the CLI
At the command prompt, type:
add audit syslogPolicy <name> <rule> <action>
<!--NeedCopy-->
To bind a SYSLOG server policy to system global for LSN logging by using the CLI
At the command prompt, type:
bind system global [<policyName> [-priority <positive_integer>]]
<!--NeedCopy-->
SYSLOG Configuration Using the Configuration Utility
To configure a SYSLOG server action for LSN logging by using the configuration utility
- Navigate to Systems > Auditing > Syslog and, on the Servers tab, add a new auditing server or edit an existing server.
- To enable LSN logging, select the Large Scale NAT Logging option.
- (Optional) To enable SYSLOG over TCP, select the TCP Logging option.
To configure a SYSLOG server policy for LSN logging by using the configuration utility
Navigate to Systems > Auditing > Syslog and, on the Policies tab, add a new policy or edit an existing policy.
To bind a SYSLOG server policy to system global for LSN logging by using the configuration utility
- Navigate to Systems > Auditing > Syslog.
- On the Policies tab, in the Action list, click Global Bindings to bind the audit global policies.
NSLOG Configuration Using the CLI
To create a NSLOG server action for LSN logging by using the CLI
At the command prompt, type:
add audit nslogAction <name> <serverIP> [-serverPort <port>] -logLevel <logLevel> ... [-lsn ( ENABLED | DISABLED )]
<!--NeedCopy-->
To create a NSLOG server policy for LSN logging by using the CLI
At the command prompt, type:
add audit nslogPolicy <name> <rule> <action>
<!--NeedCopy-->
To bind a NSLOG server policy to system global for LSN logging by using the CLI
At the command prompt, type:
bind system global [<policyName>]
<!--NeedCopy-->
NSLOG Configuration Using the Configuration Utility
To configure a NSLOG server action for LSN logging by using the configuration utility
- Navigate to Systems > Auditing > Nslog and, on the Servers tab, add a new auditing server or, edit an existing server.
- To enable LSN logging, select the Large Scale NAT Logging option.
To configure a NSLOG server policy for LSN logging by using the configuration utility
Navigate to Systems > Auditing > Nslog and, on the Policies tab, add a new policy or edit an existing policy.
To bind a NSLOG server policy to system global for LSN logging by using the configuration utility
- Navigate to Systems > Auditing > Nslog.
- On the Policies tab, in the Action list, click Global Bindings to bind the audit global policies.
Example
The following configuration specifies two SYSLOG and two NSLOG servers for storing log entries including LSN logs. LSN Logging is configured for LSN groups LSN-GROUP-2 and LSN-GROUP-3.
The NetScaler appliance generates log messages related to LSN mappings and LSN sessions of these LSN groups, and sends them to the specified log servers.
add audit syslogAction SYS-ACTION-1 198.51.101.10 -logLevel ALL -lsn ENABLED
Done
add audit syslogPolicy SYSLOG-POLICY-1 ns_true SYS-ACTION-1
Done
bind system global SYSLOG-POLICY-1
Done
add audit syslogAction SYS-ACTION-2 198.51.101.20 -logLevel ALL -lsn ENABLED
Done
add audit syslogPolicy SYSLOG-POLICY-2 ns_true SYS-ACTION-2
Done
bind system global SYSLOG-POLICY-2
Done
add audit nslogAction NSLOG-ACTION-1 198.51.101.30 -logLevel ALL -lsn ENABLED
Done
add audit nslogPolicy NSLOG-POLICY-1 ns_true NSLOG-ACTION-1
Done
bind system global NSLOG-POLICY-1
Done
add audit nslogAction NSLOG-ACTION-2 198.51.101.40 -logLevel ALL -lsn ENABLED
Done
add audit nslogPolicy NSLOG-POLICY-2 ns_true NSLOG-ACTION-2
Done
bind system global NSLOG-POLICY-2
Done
add lsn group LSN-GROUP-3 -clientname LSN-CLIENT-2 –logging ENABLED –sessionLogging ENABLED
Done
set lsn group LSN-GROUP-2 –logging ENABLED –sessionLogging ENABLED
Done
<!--NeedCopy-->
The following configuration specifies SYSLOG configuration for sending log messages to the external SYSLOG server 192.0.2.10 using TCP.
add audit syslogAction SYS-ACTION-1 192.0.2.10 -logLevel ALL -transport TCP
Done
add audit syslogPolicy SYSLOG-POLICY-1 ns_true SYS-ACTION-1
Done
bind system global SYSLOG-POLICY-1
Done
<!--NeedCopy-->
The following table displays sample LSN log entries of each type stored on the configured log servers. These LSN log entries are generated by a NetScaler appliance whose NSIP address is 10.102.37.115.
| LSN Log Entry Type | Sample Log Entry |
|---|---|
| LSN session creation | Local4.Informational 10.102.37.115 08/05/2014:09:59:48 GMT 0-PPE-0 : LSN LSN_SESSION 2581750 : SESSION CREATED Client IP:Port:TD 192.0.2.10: 15136:0, NatIP:NatPort 203.0.113.6: 6234, Destination IP:Port:TD 198.51.100.9: 80:0, Protocol: TCP |
| LSN session deletion | Local4.Informational 10.102.37.115 08/05/2014:10:05:12 GMT 0-PPE-0 : LSN LSN_SESSION 3871790 : SESSION DELETED Client IP:Port:TD 192.0.2.11: 15130:0, NatIP:NatPort 203.0.113.6: 7887, Destination IP:Port:TD 198.51.101.2:80:0, Protocol: TCP |
| LSN mapping creation | Local4.Informational 10.102.37.115 08/05/2014:09:59:47 GMT 0-PPE-0 : LSN LSN_MAPPING 2581580 : EIM CREATED Client IP:Port 192.0.2.15: 14567, NatIP:NatPort 203.0.113.5: 8214, Protocol: TCP |
| LSN mapping deletion | Local4.Informational 10.102.37.115 08/05/2014:10:05:12 GMT 0-PPE-0 : LSN LSN_MAPPING 3871700 : EIM DELETED Client IP:Port 192.0.3.15: 14565, NatIP:NatPort 203.0.113.11: 8217, Protocol: TCP |
Minimal Logging
Deterministic LSN configurations and Dynamic LSN configurations with port block significantly reduces the LSN log volume. For these two types of configuration, the NetScaler appliance allocates a NAT IP address and a block of ports to a subscriber. The NetScaler appliance generates a log message for a port block at the time of allocation to a subscriber. The NetScaler appliance also generates a log message when a NAT IP address and port block is freed. For a connection, a subscriber can be identified just by its mapped NAT IP address and port block. Because of this reason, the NetScaler appliance does not log any LSN session created or deleted. The appliance also neither logs any mapping entry created for a session nor when the mapping entry gets removed.
The minimal logging feature for deterministic LSN configurations and dynamic LSN configurations with port block is enabled by default and there is no provision to disable it. In other words, the NetScaler appliance automatically do minimal logging for deterministic LSN configurations and dynamic LSN configurations with port block. There is no option available for disabling this feature. The appliance sends the log messages to all the configured log servers.
A log message for each port block consists of the following information:
- NSIP address of the NetScaler appliance
- Time stamp
- Entry type as DETERMINISTIC or PORTBLOCK
- Whether a port block is allocated or is freed
- Subscriber’s IP address and the assigned NAT IP address and port block
- Protocol name
Minimal Logging for Deterministic LSN Configuration
Consider an example of a simple deterministic LSN configuration for four subscribers having the IP address 192.0.17.1, 192.0.17.2, 192.0.17.3, and 192.0.17.4.
In this LSN configuration, the port block size is set to 32768 and LSN NAT IP address pool has IP addresses in the range 203.0.113.19-203.0.113.23.
add lsn client LSN-CLIENT-7
Done
bind lsn client LSN-CLIENT-7 -network 192.0.17.0 -netmask 255.255.255.253
Done
add lsn pool LSN-POOL-7 -nattype DETERMINISTIC
Done
bind lsn pool LSN-POOL-7 203.0.113.19-203.0.113.23
Done
add lsn group LSN-GROUP-7 -clientname LSN-CLIENT-7 -nattype DETERMINISTIC -portblocksize 32768
Done
bind lsn group LSN-GROUP-7 -poolname LSN-POOL-7
Done
<!--NeedCopy-->
The NetScaler appliance sequentially preallocates, from the LSN NAT IP pool and on the basis of the set port block size, an LSN NAT IP address and a block of ports to each subscriber. It assigns the first block of ports (1024-33791) on the beginning NAT IP address (203.0.113.19) to the beginning subscriber IP address (192.0.17.1). The next range of ports is assigned to the next subscriber, and so on, until the NAT address does not have enough ports for the next subscriber. At that point, the first port block on the next NAT IP address is assigned to the subscriber, and so on. The appliance logs the NAT IP address and the block of ports allocated for each subscriber.
The NetScaler appliance does not log any LSN session created or deleted for these subscribers. The appliance generates the following log messages for the LSN configuration.
1) 03/23/2015:00:30:56 GMT Informational 0-PPE-0 : default LSN LSN_DETERMINISTIC 79201453 0 : Dtrstc ALLOC Client 12.0.0.241, NatInfo 50.0.0.2:59904 to 60415
2) 03/23/2015:00:30:56 GMT Informational 0-PPE-0 : default LSN LSN_DETERMINISTIC 79201454 0 : Dtrstc ALLOC Client 12.0.0.242, NatInfo 50.0.0.2:60416 to 60927
3) 03/23/2015:00:30:56 GMT Informational 0-PPE-0 : default LSN LSN_DETERMINISTIC 79201455 0 : Dtrstc ALLOC Client 12.0.0.243, NatInfo 50.0.0.2:60928 to 61439
4) 03/23/2015:00:30:56 GMT Informational 0-PPE-0 : default LSN LSN_DETERMINISTIC 79201455 0 : Dtrstc ALLOC Client 12.0.0.243, NatInfo 50.0.0.2:60928 to 61439
<!--NeedCopy-->
When you remove the LSN configuration, the allocated NAT IP address and block of ports is freed from each subscriber. The appliance logs NAT IP address and block of ports freed from each subscriber. The appliance generates the following log messages for each subscriber when you remove the LSN configuration.
1) 03/23/2015:00:33:57 GMT Informational 0-PPE-0 : default LSN LSN_DETERMINISTIC 79201706 0 : Dtrstc FREE Client 12.0.0.238, NatInfo 50.0.0.2:58368 to 58879
2) 03/23/2015:00:33:57 GMT Informational 0-PPE-0 : default LSN LSN_DETERMINISTIC 79201707 0 : Dtrstc FREE Client 12.0.0.239, NatInfo 50.0.0.2:58880 to 59391
3) 03/23/2015:00:33:57 GMT Informational 0-PPE-0 : default LSN LSN_DETERMINISTIC 79201708 0 : Dtrstc FREE Client 12.0.0.240, NatInfo 50.0.0.2:59392 to 59903
<!--NeedCopy-->
Minimal Logging for Dynamic LSN Configuration with Port Block
Consider an example of a simple dynamic LSN configuration with port block for any subscriber in the network 192.0.2.0/24. In this LSN configuration, the port block size is set to 1024 and LSN NAT IP address pool has IP addresses in the range 203.0.113.3-203.0.113.4.
set lsn parameter -memLimit 4000
Done
add lsn client LSN-CLIENT-1
Done
bind lsn client LSN-CLIENT-1 -network 192.0.2.0 -netmask 255.255.255.0
Done
add lsn pool LSN-POOL-1
Done
bind lsn pool LSN-POOL-1 203.0.113.3-203.0.113.4
Done
add lsn group LSN-GROUP-1 -clientname LSN-CLIENT-1 -portblocksize 1024
Done
bind lsn group LSN-GROUP-1 -poolname pool1 LSN-POOL-1
Done
<!--NeedCopy-->
The NetScaler appliance allocates a random NAT IP address and a block of ports, from the LSN NAT IP pool and on the basis of the set port block size, for a subscriber when it initiates a session for the first time. The NetScaler logs the NAT IP address and block of ports allocated to this subscriber. The appliance does not log any LSN session created or deleted for this subscriber. If all the ports are allocated (for different subscriber’s sessions) from the subscriber’s allocated port block, the appliance allocates a new random NAT IP address and port block for the subscriber for additional sessions. The NetScaler logs every NAT IP address and port block allocated to a subscriber.
The appliance generates the following log message when the subscriber, having the IP address 192.0.2.1, initiates a session. The log message shows that the appliance has allocated NAT IP address 203.0.113.3 and port block 1024-2047 to the subscriber.
03/23/2015:00:07:12 GMT Informational 0-PPE-3 : default LSN LSN_PORTBLOCK 106725793 0 : Portblock ALLOC Client 12.0.2.72, NatInfo 203.0.113.3:1024 to 2047, Proto:TCP
<!--NeedCopy-->
Once there are no more sessions left that is using the allocated NAT IP address and one of the ports in the allocated port block, the allocated NAT IP address and block of ports is freed from the subscriber. The NetScaler logs that the NAT IP address and the block of ports is freed from the subscriber. The appliance generates the following log messages for the subscriber, having the IP address 192.0.2.1 , when no more sessions are left that is using the allocated NAT IP address ( 203.0.113.3 ) and a port from the allocated port block ( 1024-2047 ). The log message shows that the NAT IP address and port block are freed from the subscriber.
03/23/2015:00:11:09 GMT Informational 0-PPE-3 : default LSN LSN_PORTBLOCK 106814342 0 : Portblock FREE Client 12.0.3.122, NatInfo 203.0.113.3: 1024 to 2047, Proto:TC
<!--NeedCopy-->
Load Balancing SYSLOG Servers
The NetScaler appliance send its SYSLOG events and messages to all the configured external log servers. This results in storing redundant messages and makes monitoring difficult for system administrators. To address this issue, the NetScaler appliance offers load balancing algorithms that can load balance the SYSLOG messages among the external log servers for better maintenance and performance. The supported load balancing algorithms include RoundRobin, LeastBandwidth, CustomLoad, LeastConnection, LeastPackets, and AuditlogHash.
Load balancing of SYSLOG servers using the CLI
Add a service and specify the service type as SYSLOGTCP or SYSLOGUDP.
add service <name>(<IP> | <serverName>) <serviceType (SYSLOGTCP | SYSLOGUDP)> <port>
<!--NeedCopy-->
Add a load balancing virtual server, specify the service type as SYSLOGTCP or SYSLOGTCP, and load balancing method as AUDITLOGHASH.
add lb vserver <name> <serviceType (SYSLOGTCP | SYSLOGUDP)> [-lbMethod <AUDITLOGHASH>]
<!--NeedCopy-->
Bing the service to the load balancing virtual server.
Bind lb vserver <name> <serviceName>
<!--NeedCopy-->
Add a SYSLOG action and specify the load balancing server name that has SYSLOGTCP or SYSLOGUDP as service type.
add syslogaction <name> <serverIP> [-lbVserverName <string>] [-logLevel <logLevel>]
<!--NeedCopy-->
Add a SYSLOG policy by specifying the rule and action.
add syslogpolicy <name> <rule> <action>
<!--NeedCopy-->
Bind the SYSLOG policy to the system global for the policy to take effect.
bind system global <policyName>
<!--NeedCopy-->
Load balancing of SYSLOG servers using the configuration utility
-
Add a service and specify the service type as SYSLOGTCP or SYSLOGUDP.
Navigate to Traffic Management > Services, click Add and select SYLOGTCP or SYSLOGUDP as protocol.
-
Add a load balancing virtual server, specify the service type as SYSLOGTCP or SYSLOGTCP, and load balancing method as AUDITLOGHASH.
Navigate to Traffic Management > Virtual Servers, click Add and select SYLOGTCP or SYSLOGUDP as protocol.
-
Bing the service to the load balancing virtual server to the service.
Bing the service to the load balancing virtual server.
Navigate to Traffic Management > Virtual Servers, select a virtual server and then selectAUDITLOGHASH in the Load Balancing Method.
-
Add a SYSLOG action and specify the load balancing server name that has SYSLOGTCP or SYSLOGUDP as service type.
Navigate to System > Auditing, click Servers and add a server by selecting LB Vserver option inServers.
-
Add a SYSLOG policy by specifying the rule and action.
Navigate to System > Syslog, click Policies and add a SYSLOG policy.
-
Bind the SYSLOG policy to the system global for the policy to take effect.
Navigate to System > Syslog, select a SYSLOG policy and click Action, and then click Global Bindings and bind the policy to system global.
Example:
The following configuration specifies load balance of SYSLOG messages among the external log servers using the AUDITLOGHASH as load balancing method. The NetScaler appliance generates SYSLOG events and messages that are load balanced amongst the services, service1, service2, and service 3.
add service service1 192.0.2.10 SYSLOGUDP 514
Done
add service service2 192.0.2.11 SYSLOGUDP 514
Done
add service service3 192.0.2.11 SYSLOGUDP 514
Done
add lb vserver lbvserver1 SYSLOGUDP -lbMethod AUDITLOGHASH
Done
bind lb vserver lbvserver1 service1
Done
bind lb vserver lbvserver1 service2
Done
bind lb vserver lbvserver1 service3
Done
add syslogaction sysaction1 -lbVserverName lbvserver1 -logLevel All
Done
add syslogpolicy syspol1 ns_true sysaction1
Done
bind system global syspol1
Done
<!--NeedCopy-->
Logging HTTP Header Information
The NetScaler appliance can now log request header information of an HTTP connection that is using the LSN fucntionality of the NetScaler. The following header information of an HTTP request packet can be logged:
- URL that the HTTP request is destined to.
- HTTP Method specified in the HTTP request.
- HTTP version used in the HTTP request.
- IP address of the subscriber that sent the HTTP request.
The HTTP header logs can be used by ISPs to see the trends related to the HTTP protocol among a set a subscribers. For example, an ISP can use this feature to find out the most popular websites among a set of subscribers.
An HTTP header log profile is a collection of HTTP header attributes (for example, URL and HTTP method) that can be enabled or disabled for logging. The HTTP header log profile is then bound to an LSN group. The NetScaler appliance then logs HTTP header attributes, which are enabled in the bound HTTP header log profile for logging, of any HTTP requests related to the LSN group. The appliance then sends the log messages to the configured log servers.
An HTTP header log profile can be bound to multiple LSN groups but an LSN group can have only one HTTP header log profile.
To create an HTTP header log profile by using the the CLI
At the command prompt, type:
add lsn httphdrlogprofile <httphdrlogprofilename> [-logURL ( ENABLED | DISABLED )] [-logMethod ( ENABLED | DISABLED )] [-logVersion ( ENABLED | DISABLED )] [-logHost ( ENABLED | DISABLED )]
show lsn httphdrlogprofile
<!--NeedCopy-->
To bind an HTTP header log profile to an LSN group by using the the CLI
At the command prompt, type:
bind lsn group <groupname> -httphdrlogprofilename <string>
show lsn group <groupname>
<!--NeedCopy-->
Example
In the following example of an LSN configuration, HTTP header log profile HTTP-Header-LOG-1 is bound to LSN group LSN-GROUP-1. The log profile has all the HTTP attributes (URL, HTTP method, HTTP version, and HOST IP address) enabled for logging so that all these attributes are logged for any HTTP requests from subscribers (in the network 192.0.2.0/24) related to the LSN group.
add lsn httphdrlogprofile HTTP-HEADER-LOG-1
Done
set lsn parameter -memLimit 4000
Done
add lsn client LSN-CLIENT-1
Done
bind lsn client LSN-CLIENT-1 -network 192.0.2.0 -netmask 255.255.255.0
Done
add lsn pool LSN-POOL-1
Done
bind lsn pool LSN-POOL-1 203.0.113.3-203.0.113.4
Done
add lsn group LSN-GROUP-1 -clientname LSN-CLIENT-1 -portblocksize 1024
Done
bind lsn group LSN-GROUP-1 -poolname pool1 LSN-POOL-1
Done
bind lsn group LSN-GROUP-1 -httphdrlogprofilename HTTP-HEADER-LOG-1
Done
<!--NeedCopy-->
The NetScaler generates the following HTTP header log message when one of the subscriber belonging to the LSN configuration example sends an HTTP request.
The log message tells us that a client having the IP address 192.0.2.33 sends an HTTP request to URL example.com using HTTP method GET and HTTP version 1.1.
03/19/2015:16:24:04 GMT Informational 0-PPE-1 : default LSN Message 59 0 : "LSN Client IP:TD 10.102.37.118:0 URL: example.com Host: 192.0.2.33 Version: HTTP1.1 Method: GET"
<!--NeedCopy-->
Logging MSISDN Information
A Mobile Station Integrated Subscriber Directory Number (MSISDN) is a telephone number uniquely identifying a subscriber across multiple mobile networks. The MSISDN is associated with a country code and a national destination code identifying the subscriber’s operator.
You can configure a NetScaler appliance to include MSISDNs in LSN log entries for subscribers in mobile networks. The presence of MSISDNs in the LSN logs helps the administrator in faster and accurate back tracing of a mobile subscriber who has violated a policy or law, or whose information is required by lawful interception agencies.
The following sample LSN log entries include MSISDN information for a connection from a mobile subscriber in an LSN configuration. The log entries show that a mobile subscriber whose MSISDN is E164:5556543210 was connected to destination IP:port 23.0.0.1:80 through the NAT IP:port 203.0.113.3:45195.
| Log Entry Type | Sample Log Entry |
|---|---|
| LSN session creation | Oct 14 15:37:30 10.102.37.77 10/14/2015:10:08:14 GMT 0-PPE-6 : default LSN LSN_SESSION 25012 0 : SESSION CREATED E164:5556543210 Client IP:Port:TD 192.0.2.50:4649:0, NatIP:NatPort 203.0.113.3:45195, Destination IP:Port:TD 23.0.0.1:0:0, Protocol: TCP |
| LSN mapping creation | Oct 14 15:37:30 10.102.37.77 10/14/2015:10:08:14 GMT 0-PPE-6 : default LSN LSN_ADDR_MAPPING 25013 0 : ADM CREATED E164:5556543210 Client IP:Port:TD 192.0.2.50:4649:0, NatIP:NatPort 203.0.113.3:45195, Destination IP:Port:TD 23.0.0.1:0:0, Protocol: TCP |
| LSN session deletion | Oct 14 15:40:30 10.102.37.77 10/14/2015:10:11:14 GMT 0-PPE-6 : default LSN LSN_SESSION 25012 0 : SESSION CREATED E164:5556543210 Client IP:Port:TD 192.0.2.50:4649:0, NatIP:NatPort 203.0.113.3:45195, Destination IP:Port:TD 23.0.0.1:0:0, Protocol: TCP |
| LSN mapping | Oct 14 15:40:30 10.102.37.77 10/14/2015:10:11:14 GMT 0-PPE-6 : default LSN LSN_ADDR_MAPPING 25013 0 : ADM CREATED E164:5556543210 Client IP:Port:TD 192.0.2.50:4649:0, NatIP:NatPort 203.0.113.3:45195, Destination IP:Port:TD 23.0.0.1:0:0, Protocol: TCP |
Perform the following tasks for including MSISDN information in LSN logs
- Create an LSN log profile. An LSN log profile includes the log subscriber ID parameter, which specifies whether to or not to include the MSISDN information in the LSN logs of an LSN configuration. Enable the log subscriber ID parameter when creating the LSN log profile.
- Bind the LSN log profile to an LSN group of an LSN configuration. Bind the created LSN log profile to an LSN group of an LSN configuration by setting the log profile name parameter to the created LSN log profile name. For instructions on configuring Large Scale NAT, see Configuration Steps for LSN.
To create an LSN log profile by using the CLI
At the command prompt, type:
add lsn logprofile <logprofilename -logSubscriberID ( ENABLED | DISABLED )
show lsn logprofile
<!--NeedCopy-->
To bind an LSN log profile to an LSN group of an LSN configuration by using the CLI
At the command prompt, type:
bind lsn group <groupname> -logProfileName <lsnlogprofilename>
show lsn group
<!--NeedCopy-->
Sample Configuration:
In this example of LSN configuration, the LSN log profile has the log subscriber ID parameter enabled. The profile is bound to LSN group LSN-GROUP-9. MSISDN information is included in the LSN session and LSN mapping logs for connections from mobile subscribers (in the network 192.0.2.0/24).
add lsn logprofile LOG-PROFILE-MSISDN-9 -logSubscriberID ENABLED
Done
add lsn client LSN-CLIENT-9
Done
bind lsn client LSN-CLIENT-9 -network 192.0.2.0 -netmask 255.255.255.0
Done
add lsn pool LSN-POOL-9
Done
bind lsn pool LSN-POOL-9 203.0.113.3-203.0.113.4
Done
add lsn group LSN-GROUP-9 -clientname LSN-CLIENT-9
Done
bind lsn group LSN-GROUP-9 -poolname LSN-POOL-9
Done
bind lsn group LSN-GROUP-9 -logprofilename LOG-PROFILE-MSISDN-9
Done
<!--NeedCopy-->
Displaying Current LSN Sessions
You can display the current LSN sessions for detecting any unwanted or inefficient LSN sessions on the NetScaler appliance. You can display all or some LSN sessions on the basis of selection parameters.
Note: When more than a million LSN sessions exist on the NetScaler appliance, Citrix recommends displaying selected LSN sessions instead of all by using the selection parameters.
Configuration Using the CLI
To display all LSN sessions by using the CLI
At the command prompt, type:
show lsn session
<!--NeedCopy-->
To display selective LSN sessions by using the CLI
At the command prompt, type:
show lsn session [-clientname <string>] [-network <ip_addr> [-netmask <netmask>] [-td <positive_integer>]] [-natIP <ip_addr> [-natPort <port>]]
<!--NeedCopy-->
Example
To display all LSN sessions existing on a NetScaler
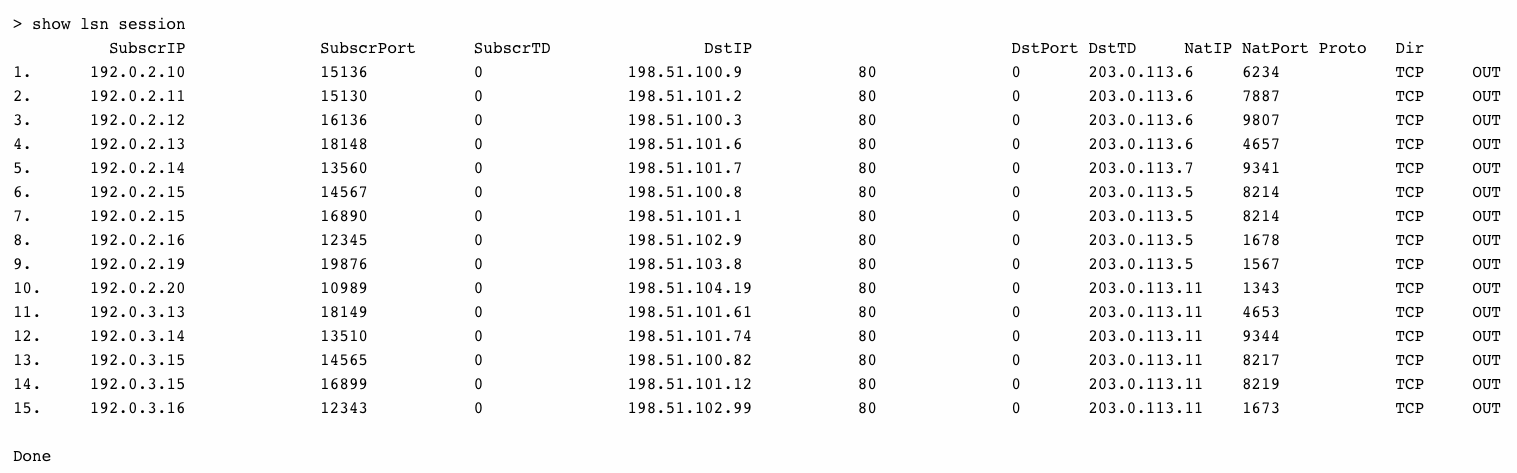
To display all LSN sessions related to an LSN client entity LSN-CLIENT-2
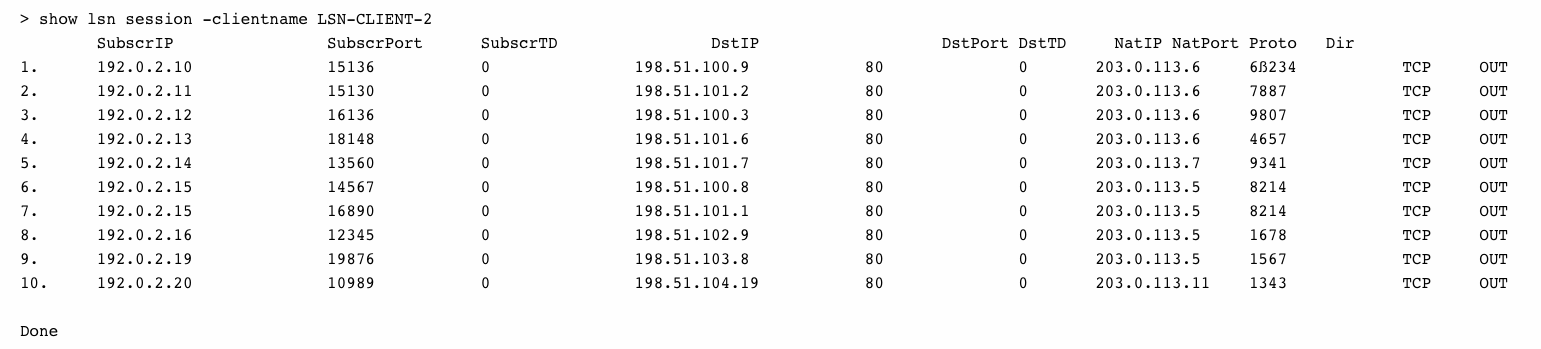
To display all LSN sessions that uses 203.0.113.5 as the NAT IP address
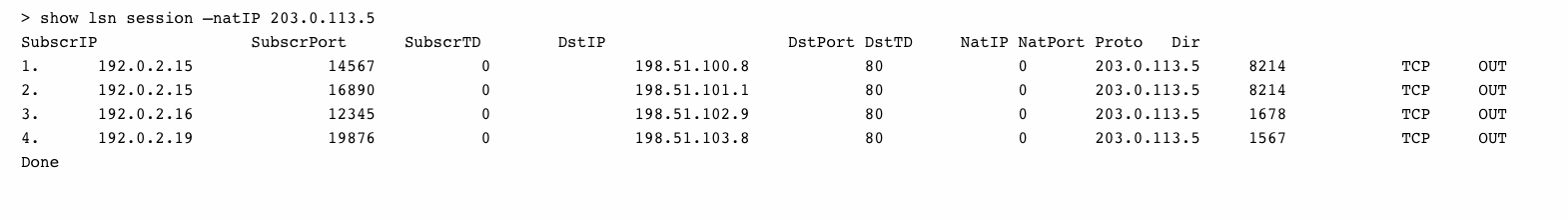
Configuration Using the Configuration Utility
To display all or selected LSN sessions by using the configuration utility
- Navigate to System > Large Scale NAT > Sessions, and click the NAT44 tab.
- For displaying LSN sessions on the basis of selection parameters, click Search.
Parameter Descriptions (of commands listed in the CLI procedure)
-
show lsn session
-
clientname
Name of the LSN Client entity. Maximum Length: 127
-
network
IP address or network address of subscriber(s).
-
netmask
Subnet mask for the IP address specified by the network parameter.
Default value: 255.255.255.255
-
td
Traffic domain ID of the LSN client entity.
Default value: 0
Minimum value: 0
Maximum value: 4094
-
natIP
Mapped NAT IP address used in LSN sessions.
-
Displaying LSN Statistics
You can display statistics related to the LSN feature for evaluating the performance of the LSN feature or to troubleshoot problems. You can display a summary of statistics of the LSN feature or of a particular LSN group. The statistical counters reflect events since the NetScaler appliance was last restarted. All these counters are reset to 0 when the NetScaler appliance is restarted.
To display all LSN statistics by using the CLI
At the command prompt, type:
stat lsn
<!--NeedCopy-->
To display statistics for a specified LSN group by using the CLI
At the command prompt, type:
stat lsn group [<groupname>]
<!--NeedCopy-->
Example
> stat lsn
Large Scale NAT statistics
Rate(/s) Total
LSN TCP Received Packets 0 40
LSN TCP Received Bytes 0 3026
LSN TCP Transmitted Packets 0 40
LSN TCP Transmitted Bytes 0 3026
LSN TCP Dropped Packets 0 0
LSN TCP Current Sessions 0 0
LSN UDP Received Packets 0 0
LSN UDP Received Bytes 0 0
LSN UDP Transmitted Packets 0 0
LSN UDP Transmitted Bytes 0 0
LSN UDP Dropped Packets 0 0
LSN UDP Current Sessions 0 0
LSN ICMP Received Packets 0 982
LSN ICMP Received Bytes 0 96236
LSN ICMP Transmitted Packets 0 0
LSN ICMP Transmitted Bytes 0 0
LSN ICMP Dropped Packets 0 982
LSN ICMP Current Sessions 0 0
LSN Subscribers 0 1
Done
> stat lsn group LSN-GROUP-1
LSN Group Statistics
Rate (/s) Total
TCP Translated Pkts 0 40
TCP Translated Bytes 0 3026
TCP Dropped Pkts 0 0
TCP Current Sessions 0 0
UDP Translated Pkts 0 0
UDP Translated Bytes 0 0
UDP Dropped Pkts 0 0
UDP Current Sessions 0 0
ICMP Translated Pkts 0 0
ICMP Translated Bytes 0 0
ICMP Dropped Pkts 0 0
ICMP Current Sessions 0 0
Current Subscribers 0 1
Done
<!--NeedCopy-->
Parameter Descriptions (of commands listed in the CLI procedure)
-
stat lsn group
-
groupname
Name of the LSN Group. Maximum Length: 127
-
detail
Specifies detailed output (including more statistics). The output can be quite voluminous. Without this argument, the output will show only a summary.
-
fullValues
Specifies that numbers and strings should be displayed in their full form. Without this option, long strings are shortened and large numbers are abbreviated.
-
ntimes
The number of times, in intervals of seven seconds, the statistics should be displayed.
Default value: 1
-
logFile
The name of the log file to be used as input.
-
clearstats
Clear the statsistics / counters
Possible values: basic, full
-
Compact Logging
Logging LSN information is one of the important functions needed by ISPs to meet legal requirements and be able to identify the source of traffic at any given time. This eventually results in a huge volume of log data, requiring the ISPs to make large investments to maintain the logging infrastructure.
Compact logging is a technique for reducing the log size by using a notational change involving short codes for event and protocol names. For example, C for client, SC for session created, and T for TCP. Compact logging results in an average of 40 percent reduction in log size.
The following examples of NAT44 mapping creation log entries show the advantage of compact logging.
| Default logging format | 02/02/2016:01:13:01 GMT Informational 0-PPE-2 : default LSN LSN_ADDRPORT_MAPPING 85 0 : A&PDM CREATED ClientIP:Port:TD1.1.1.1:6500:0,NatIP:NatPort8.8.8.8:47902, DestinationIP:Port:TD2.2.2.2:80:0, Protocol: TCP |
| Compact logging format | 02/02/2016:01:14:57 GMT Info 0-PE2:default LSN 87 0:A&PDMC|C-1.1.1.1:6500:0|N-8.8.8.9:51066|D-2.2.2.2:80:0|T |
Configuration Steps
Perform the following tasks for logging LSN information in compact format:
- Create an LSN log profile. An LSN log profile includes the Log Compact parameter, which specifies whether to or not to log information in compact format for an LSN configuration.
- Bind the LSN log profile to an LSN group of an LSN configuration. Bind the created LSN log profile to an LSN group of an LSN configuration by setting the Log Profile Name parameter to the created LSN log profile name. All sessions and mappings for this LSN group are logged in compact format.
To create an LSN log profile by using the CLI
At the command prompt, type:
add lsn logprofile <logprofilename> -logCompact (ENABLED|DISABLED)
show lsn logprofile
<!--NeedCopy-->
To bind an LSN log profile to an LSN group of an LSN configuration by using the CLI
At the command prompt, type:
bind lsn group <groupname> -logProfileName <lsnlogprofilename>
show lsn group
<!--NeedCopy-->
Sample configuration:
add lsn logprofile LOG-PROFILE-COMPACT-9 -logCompact ENABLED
Done
add lsn client LSN-CLIENT-9
Done
bind lsn client LSN-CLIENT-9 -network 192.0.2.0 -netmask 255.255.255.0
Done
add lsn pool LSN-POOL-9
Done
bind lsn pool LSN-POOL-9 203.0.113.3-203.0.113.4
Done
add lsn group LSN-GROUP-9 -clientname LSN-CLIENT-9
Done
bind lsn group LSN-GROUP-9 -poolname LSN-POOL-9
Done
bind lsn group LSN-GROUP-9 –logProfileName LOG-PROFILE-COMPACT-9
Done
<!--NeedCopy-->
IPFIX Logging
The NetScaler appliance supports sending information about LSN events in Internet Protocol Flow Information Export (IPFIX) format to the configured set of IPFIX collector(s). The appliance uses the existing AppFlow feature to send LSN events in IPFIX format to the IPFIX collectors.
IPFIX based logging is available for the following large scale NAT44 related events:
- Creation or deletion of an LSN session.
- Creation or deletion of an LSN mapping entry.
- Allocation or de-allocation of port blocks in the context of deterministic NAT.
- Allocation or de-allocation of port blocks in the context of dynamic NAT.
- Whenever subscriber session quota is exceeded.
Points to Consider before you Configure IPFIX logging
Before you start configuring IPSec ALG, consider the following points:
- You must configure the AppFlow feature and IPFIX collector(s) on the NetScaler appliance. For instructions, see Configuring the AppFlow feature topic.
Configuration Steps
Perform the following tasks for logging LSN information in IPFIX format:
- Enable LSN logging in the AppFlow® configuration. Enable the LSN logging parameter as part of AppFlow configuration.
- Create an LSN log profile. An LSN log profile includes the IPFIX parameter that enables or disables the log information in IPFIX format.
- Bind the LSN log profile to an LSN group of an LSN configuration. Bind the LSN log profile to one or multiple LSN group(s). Events related to the bound LSN group will be logged in IPFIX format.
To enable LSN logging in the AppFlow configuration by using the CLI
At the command prompt, type:
set appflow param -lsnLogging ( ENABLED | DISABLED )
show appflow param
<!--NeedCopy-->
To create an LSN log profile by using the CLI
At the command prompt, type:
set lsn logprofile <logProfileName> -logipfix ( ENABLED | DISABLED )
show lsn logprofile
<!--NeedCopy-->
To bind the LSN log profile to an LSN group of an LSN configuration by using the CLI
At the command prompt, type:
bind lsn group <groupname> -logProfileName <lsnlogprofilename>
show lsn group
<!--NeedCopy-->
To create an LSN log profile by using the GUI
Navigate to System > Large Scale NAT > Profiles, click Log tab, and then add a log profile.
To bind the LSN log profile to an LSN group of an LSN configuration by using the GUI
- Navigate to System > Large Scale NAT > LSN Group, open the LSN group.
- In Advanced Settings, click + Log Profile to bind the created Log profile to the LSN group.