Advanced Endpoint Analysis scans
Advanced Endpoint Analysis (EPA) is used for scanning user devices for the endpoint security requirement configured on NetScaler Gateway. If a user device tries to access the NetScaler Gateway, the device is scanned for security information, such as operating system, antivirus, web browser versions and so forth before an administrator can grant access to NetScaler Gateway.
The Advanced EPA scan is a policy-based scan that you can configure on NetScaler Gateway for authentication sessions. The policy performs a registry check on a user device and based on evaluation, the policy allows or denies access to the NetScaler network. For more information about the Citrix EPA client system requirements, see Endpoint Analysis requirements.
Important:
OPSWAT scans requiring admin privileges are not supported on Citrix EPA clients for Windows and macOS. To verify supported OPSWAT scans, refer to the “Supported application list.xlsx” available on the Citrix Downloads page for the specific version of the OPSWAT libraries in use.
If a scan qualifier in the “Supported application list.xlsx” is marked as “FALSE”, it indicates that the corresponding OPSWAT scan qualifier is not supported. In such cases, it is recommended to adjust your scans to use supported configurations.
You can configure the advanced EPA scan by using the GUI or the CLI.
On the GUI
-
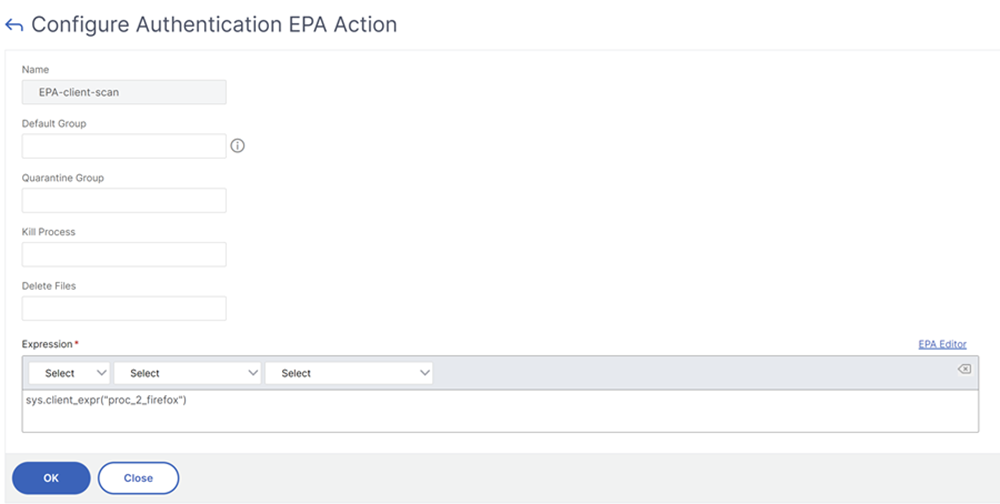
Create EPA action.
Navigate to Security > AAA - Application Traffic > Policies > Authentication > Advanced Policies > Actions > EPA and click Add. On the Create Authentication EPA Action page, update the following information and click Create.
- Name: Name of the EPA action.
- Default Group: The default group that is chosen when the EPA check succeeds.
- Quarantine Group: The quarantine group that is chosen when the EPA check fails.
- Kill Process: A string specifying the name of a process to be terminated by the EPA plug-in. Multiple processes must be comma-separated.
- Delete Files: A string specifying the paths and names of the files to be deleted by the EPA plug-in. Multiple files must be comma-separated.
- Expression: Refer to Advanced Endpoint Analysis policy expression reference for the EPA expression format.
- EPA Editor: Select the operators for the product version scan.
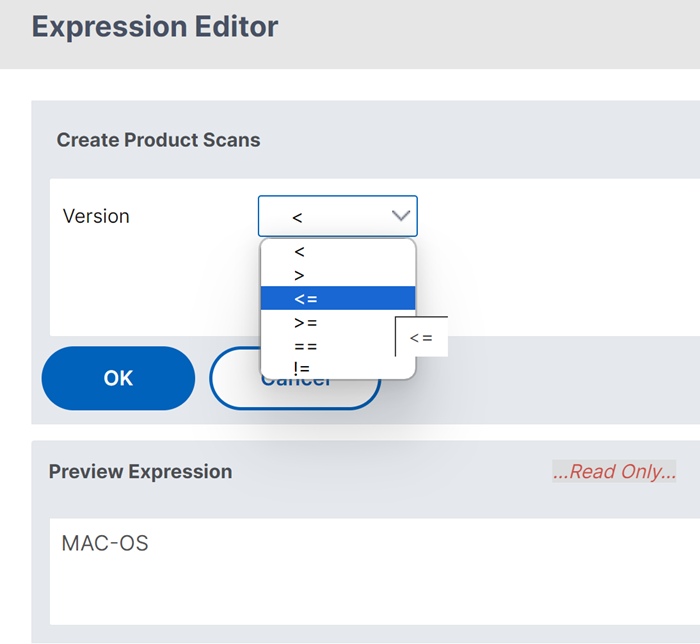
Note:
Citrix EPA client for macOS 24.2.1.5 / Citrix Secure Access client for macOS 24.02.1 and later versions support the EPA operators
>,<,>=,<=,==and!=on the EPA editor. Also, the Mac OS option is now available as a separate option on the EPA editor (Mac > Mac OS). Previously, the macOS product version scan had to be performed at Common > Operating System > MacOS using only the==and!=operators. Ensure that you are using NetScaler Gateway 14.1-12.x or later to use this functionality.You can perform a product version scan of your macOS devices at Mac > Mac OS using these operators. For example, to allow the OS versions from 12.4 to 13.0, except 12.8, configure the expression
sys.client_expr("sys_0_MAC-OS_version_>=_12.4")&&sys.client_expr("sys_0_MAC-OS_version_<=_13.0")&&sys.client_expr("sys_0_MAC-OS_version_!=_12.8")on the EPA editor. -
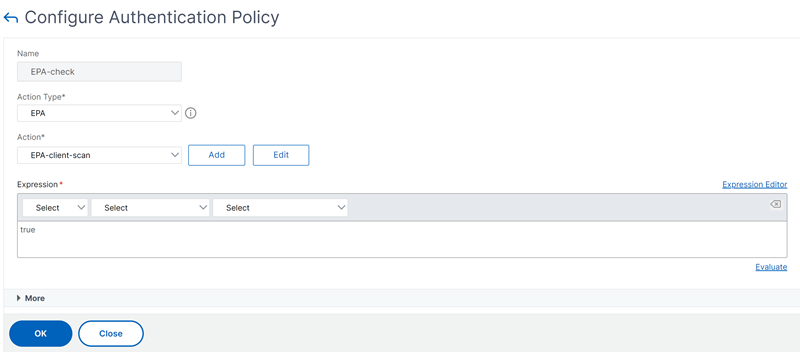
Create a corresponding EPA policy.
Navigate to Security > AAA - Application Traffic > Policies > Authentication > Advanced Policies > Policies and click Add. On the Create Authentication Policy page, update the following information and click Create.
- Name: Name of the advanced EPA policy.
- Action Type: Type of the authentication action.
- Action: Name of the authentication action to be performed if the policy matches.
- Expression: Refer to Advanced Endpoint Analysis policy expression reference for the EPA expression format.
- Log Action: Name of message log action to use when a request matches this policy. The maximum allowed length is 127 characters.
-
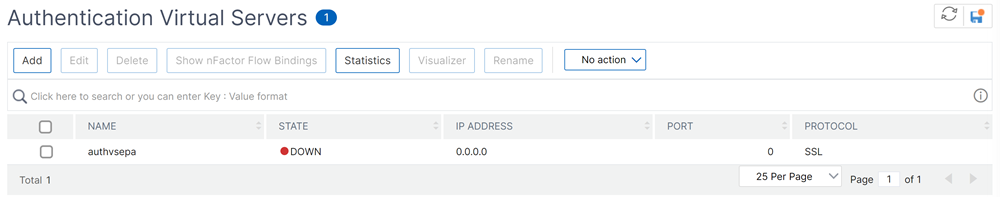
Configure an authentication virtual server and an authentication profile.
- Navigate to Security > AAA - Application Traffic > Authentication Virtual servers and click Add.
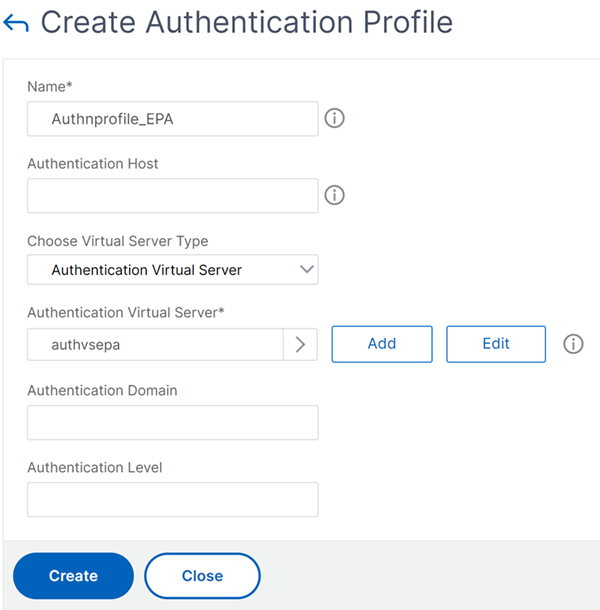
- Navigate to Security > AAA - Application Traffic > Authentication Profile and click Create.
-
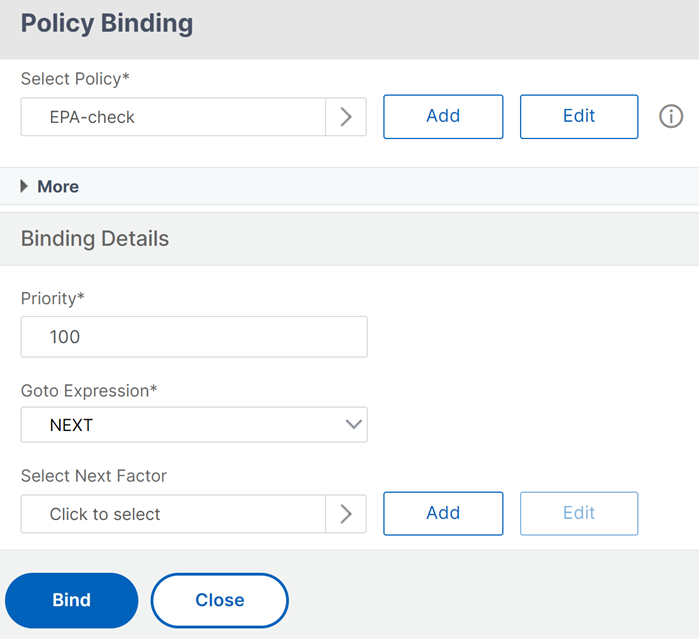
Bind the advanced EPA policy to the authentication virtual server.
- Navigate to Security > AAA – Application Traffic > Authentication Virtual Servers and select the authentication virtual server.
- Select the policy in the Advanced Authentication Policies section.
- Click Bind in the Policy Binding section.
-
Bind the EPA policy to nFactor flow.
For details about how to add an advanced EPA policy as a factor to the nFactor flow, see EPA scan as a factor in nFactor authentication.
On the CLI
-
Create an action to perform the EPA scan.
add authentication epaAction EPA-client-scan -csecexpr "sys.client_expr (\"proc_2_firefox\")" <!--NeedCopy-->The preceding expression scans if the process ‘Firefox’ is running. The EPA plug-in checks for the process existence every 2 minutes, signified by the digit ‘2’ in the scan expression.
-
Associate the EPA action to an advanced EPA policy.
add authentication Policy EPA-check -rule true -action EPA-client-scan <!--NeedCopy--> -
Configure an authentication virtual server and an authentication profile.
add authentication vserver authnvsepa ssl -ip address 192.0.2.0 -port 443 <!--NeedCopy-->add Authnprofile_EPA -authnVsName authnvsepa <!--NeedCopy--> -
Bind the advanced EPA policy to the authentication virtual server.
bind authentication vs authnvsepa -policy EPA-check -pr 1 <!--NeedCopy-->
Upgrade EPA libraries
To use the NetScaler GUI to upgrade EPA libraries:
-
Navigate to Configuration > NetScaler Gateway > Update Client Components.
-
Under Update Client Components, click Upgrade EPA Libraries link.
-
Choose the required file and click Upgrade.
Important:
In a NetScaler Gateway high availability, the EPA Libraries must be upgraded on both the primary and secondary nodes.
In a NetScaler Gateway clustering setup, the EPA Libraries must be upgraded on all the cluster nodes.
If you experience issues after upgrading the EPA library, you cannot downgrade to a lower version. Contact Citrix Support for assistance.
For the list of Windows and MAC Supported applications by OPSWAT for NetScaler scans, see https://support.citrix.com/article/CTX234466.
Troubleshooting advanced Endpoint Analysis scans
To help with troubleshooting Advanced Endpoint Analysis scans, the client plug-ins write logging information to a file on client endpoint systems. These log files can be found in the following directories, depending on the user’s operating system.
Windows Vista, Windows 7, Windows 8, Windows 8.1, and Windows 10:
C:\Users\<username>\AppData\Local\Citrix\AGEE\nsepa.txt
Windows XP:
C:\Documents and Settings\All Users\Application Data\Citrix\AGEE\nsepa.txt
Mac OS X systems:
~/Library/Application Support/Citrix/EPAPlugin/epaplugin.log
(Where the ~ symbol indicates the relevant macOS user’s home directory path.) (Where the ~ symbol indicates the relevant macOS user’s home directory path.)
Ubuntu:
-
~/.citrix/nsepa.txt
-
~/.citrix/nsgcepa.txt
Windows Last Update Scan
Note:
To update the EPA library, download it from https://www.citrix.com/downloads/citrix-secure-access/epa-libraries/epa-libraries-for-netscaler-gateway.html.
The Windows Last Update scan enhancement is applicable from EPA library version 24.9.1.1 and later. Starting from version 24.9.1.1, the scan includes updates installed through BigFix, Intune, and other third-party tools, in addition to those installed through the Windows Auto Upgrade service. The Windows Last Update scan is not applicable for manually installed updates where the update patch is downloaded and installed by the user.
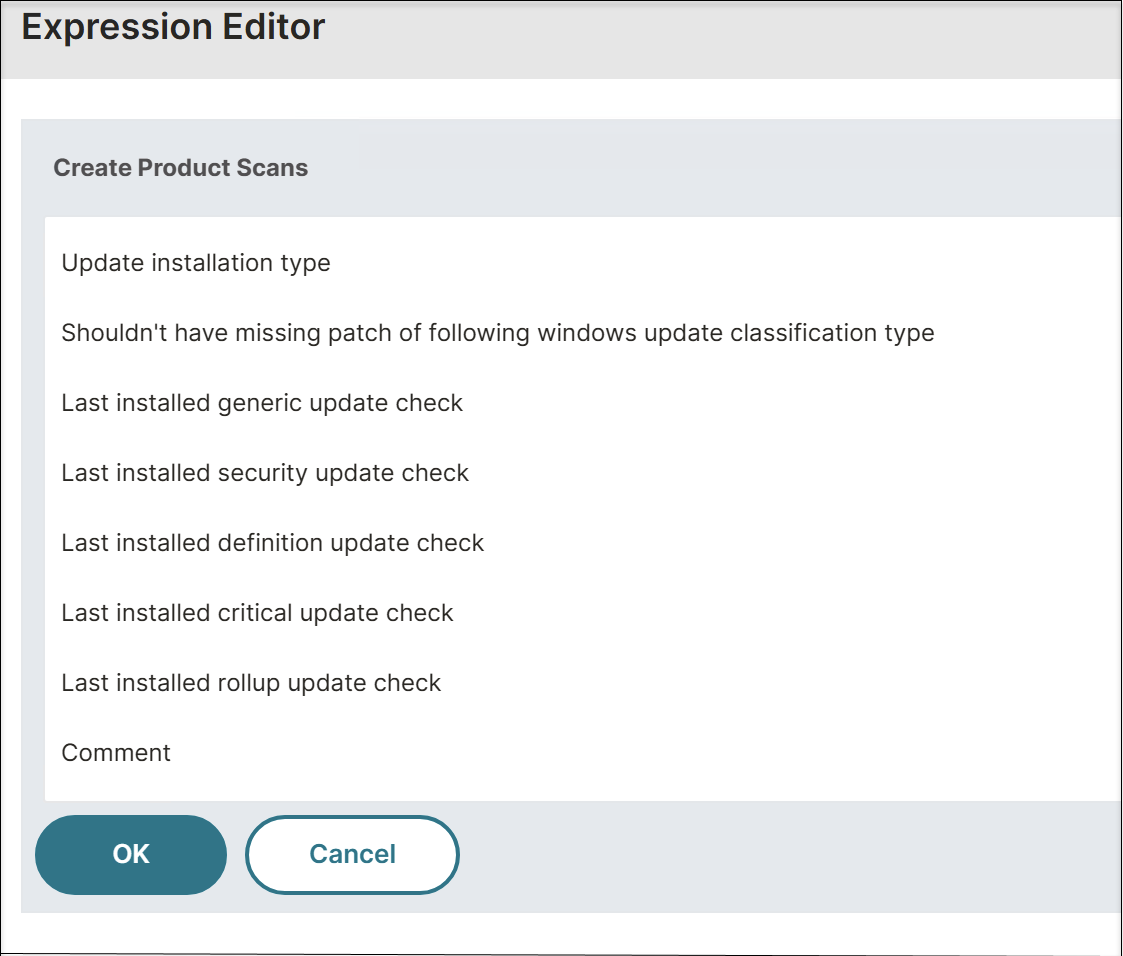
Starting from the EPA library version 24.11.1.1, the Windows Last Update scan lists the Windows updates in the following categories:
-
Generic updates: This category includes updates installed using Windows update, Microsoft update, or automatic updates feature.
-
Security updates: This category includes the patches for security-related vulnerabilities. The security updates are published on the second Tuesday of each month.
-
Critical updates: This category includes the patches for critical and non-security-related bugs. The critical updates are published as and when required.
-
Definition updates: This category includes updates that contain additions to a product’s definition database. When definition updates are published only the differences between the latest update and the update that is currently installed are downloaded and applied to the device.
-
Update rollups: This category includes tested, cumulative set of hotfixes, security updates, critical updates, and updates that are packaged together for easy deployment. The update rollups are published on the second Tuesday of each month.
Note:
While configuring the Windows Last Update scan, ensure that updates are scheduled within the configured period for each category. If updates are not installed within this timeframe, the scan fails.