Endpoint Analysis v2
Endpoint Analysis (EPA) is vital for Zero Trust Network Access (ZTNA), assessing endpoint device context and posture before granting access. From release 14.1 build 25.56, EPA v2 offers a more robust and reliable policy evaluation, with enhanced capabilities for stronger assurance and improved security, making it the recommended option.
Supported platforms and versions
The following table lists the EPA client platforms and versions that support EPA v2:
| EPA client platform | Version |
|---|---|
| Windows | 24.6.1.18 and later |
| macOS | 24.04.1 and later |
| Linux | 23.10.3 and later |
Supported and non-supported scans
EPA v2 supports most of the scans for browser-based and Citrix Workspace app-initiated sessions, which are supported by EPA v1. For more information, see Endpoint Analysis.
The following scans are not supported by EPA v2:
-
Windows EPA scans for missing patches
-
Windows last update scan
-
MAC Address scans under Windows and Mac drop-down menus in the Expression editor
-
Registry scans with version comparison using operators (<, >, ==, !=, <=, >=). This limitation is only specific to version comparisons while the standard integer comparisons work as expected.
Prerequisites
-
Configure nFactor authentication (advanced authentication) in NetScaler Gateway.
-
Enable the
HttpOnlyCookieparameter either by using the CLI or the GUI.-
To enable
HttpOnlyCookieparameter by using the CLI, type the following command in the command prompt:set aaa parameter -httpOnlyCookie ENABLED <!--NeedCopy--> -
To enable
HttpOnlyCookieparameter by using the GUI, navigate to NetScaler Gateway > Global Settings > Change authentication AAA settings. On the Configure AAA Parameter page, set HttpOnly Cookie to ENABLED.
-
Enable EPA v2 on NetScaler Gateway
To enable EPA v2 by using the CLI
At the command prompt, type:
set aaa parameter -enhancedEPA ENABLED
<!--NeedCopy-->
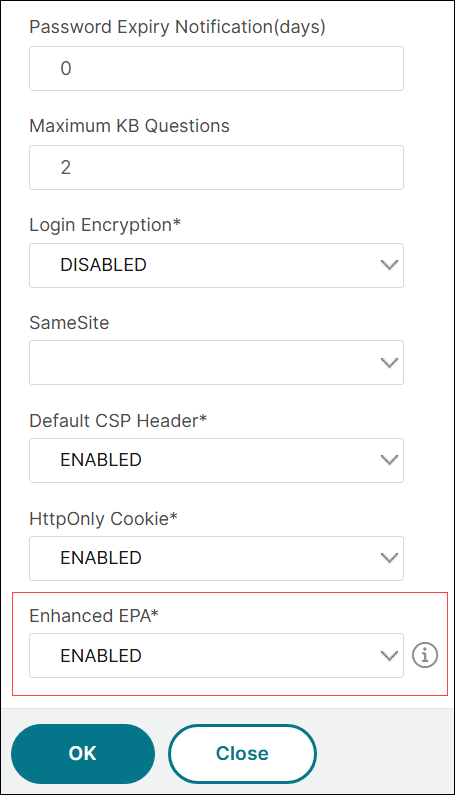
To enable EPA v2 by using the GUI
-
Navigate to NetScaler Gateway > Global Settings > Change authentication AAA settings.
-
On the Configure AAA Parameter page, set Enhanced EPA to ENABLED.
-
Click OK.
-
Reboot the primary node (which was previously a secondary node) to make sure that both the nodes of the HA setup have the same configuration.
Note:
A reboot is not required for a new NetScaler configuration.
Upgrade NetScaler
Upgrade your NetScaler to the appropriate version by downloading from the Citrix Downloads page. For detailed instructions on how to upgrade an HA pair, see Upgrade a high availability pair.
Upgrade client components on NetScaler Gateway
Run the following command in the NetScaler shell to check the client versions associated with your NetScaler:
cat /var/netscaler/gui/vpn/pluginlist.xml
<!--NeedCopy-->
If the associated client versions do not comply with Supported platforms and versions, update the clients as mentioned in the following sections.
Upgrade the Citrix Secure Access™ client and EPA client for Windows
Upgrade the Citrix Secure Access client and EPA client for Windows according to the steps mentioned in Upgrade the Citrix Secure Access client and EPA client for Windows on NetScaler Gateway.
Upgrade the Citrix Secure Access client and EPA client for macOS
Upgrade the Citrix Secure Access client for macOS to the latest version from the App store.
Perform the following steps on NetScaler Gateway to upgrade the EPA client for macOS:
-
Download the latest EPA client for macOS from https://www.citrix.com/downloads/citrix-secure-access/plug-ins/EPA-clients-for-macOS.html
-
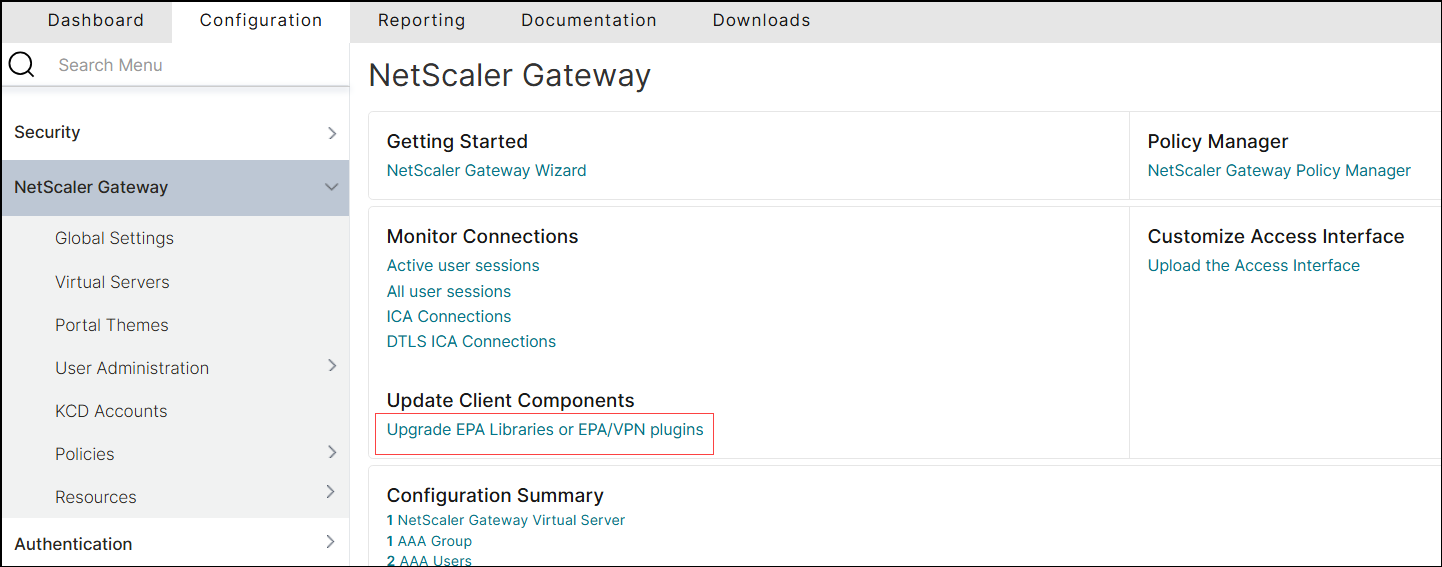
Navigate to NetScaler Gateway > Update Client Components.
-
Under Update Client Components, click the Upgrade EPA Libraries or EPA/VPN plugins link.
-
Click Choose File and select the downloaded EPA client file.
-
Click Upgrade.
-
Update the
pluginlist.xmlto reflect the new version details as follows:-
Copy the downloaded
Citrix_Endpoint_Analysis.dmgto the/var/netscaler/gui/epa/scripts/mac/directoryon NetScaler Gateway. -
Modify the
versionandcompatibleFromattributes ofplugintag with nameNetScaler Gateway EPA plug-in for Macin/var/netscaler/gui/vpn/pluginlist.xmlto the appropriate values.version=“<version>” compatibleFrom=”<version>” <!--NeedCopy-->The new
plugintag appears as follows:<plugin name="NetScaler Gateway EPA plug-in for Mac" type="MAC-EPA" version="23.7.6" path="/epa/scripts/mac/Citrix_Endpoint_Analysis.dmg" compatibleFrom="23.7.6" compatibleTill="" /> <!--NeedCopy--> -
For the changes to take effect, run the following commands on both the primary and secondary nodes:
rm -rf /netscaler/ns_gui ln -s /var/netscaler/gui /netscaler/ns_gui <!--NeedCopy-->
-
Upgrade EPA client for Windows and macOS on end-user machines
On upgrading EPA in NetScaler Gateway to EPA v2, the EPA client fails to launch if the EPA client version installed on the end-user machine is not supported by EPA v2. After a timeout of 20 seconds, users are prompted to download the new EPA client.
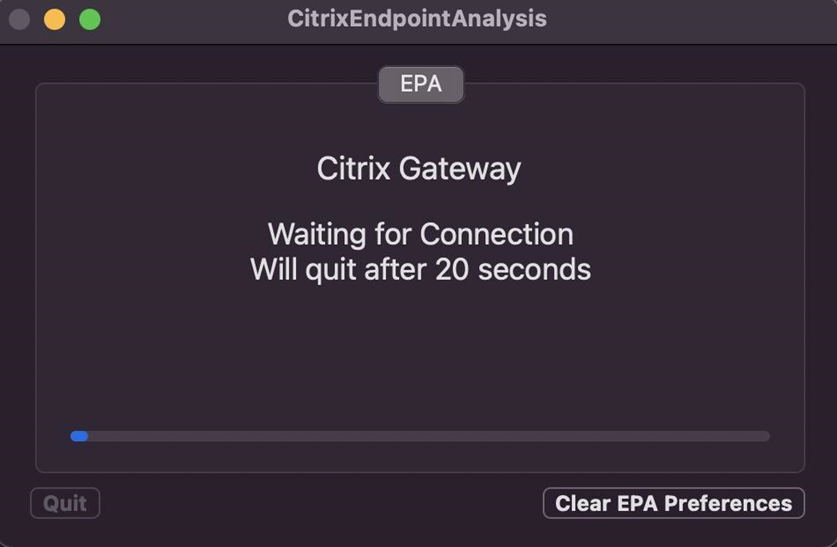
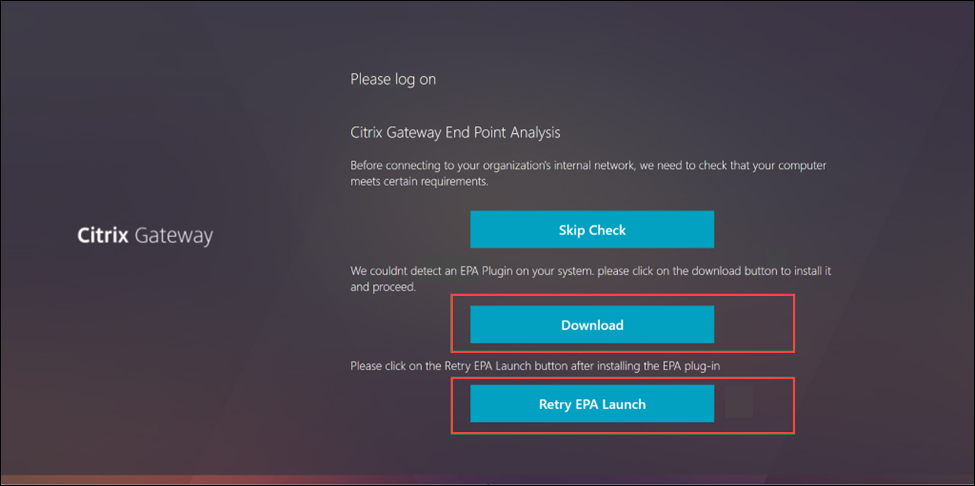
Update the EPA client on end-user machines using the following steps:
-
Click the Download button to download the new EPA client that was previously uploaded to NetScaler Gateway.
-
Once the new EPA client is installed, click the Retry EPA Launch button on the same page to restart the EPA client.
Troubleshooting issues with EPA v2
Mac address scans
EPA v2 does not support MAC Address scans under Windows and Mac drop-down menus in the Expression editor. The following is a sample scan configuration:
Windows: sys.client_expr("sys_0_MAC_1A2B3C4D5E6F,1D2B3E4D5F6E[COMMENT: MAC Address]")
macOS: sys.client_expr("sys_0_MAC-MAC_1A2B3C4D5E6F,1D2B3E4D5F6E[COMMENT: MAC Address]")
Workaround:
Configure EPA scan to allow specific MAC addresses. For more information, see EPA scan for MAC addresses.
Registry scans using operators (<, >, ==, !=, <=, >=)
EPA v2 does not support registry scans with version comparison using operators (<, >, ==, !=, <=, >=).
Workaround:
Use contains or not contains instead of operators. However, this workaround still does not work for cases like >, <, <=, >=.
Example:
The following is a sample scan configuration with the comparison operator:
sys.client_expr(\"sys_0_REG_PATH_==_HKEY\\\\_LOCAL\\\\_MACHINE\\\\\\\\SOFTWARE\\\\\\\\Citrix\\\\\\\\AppProtection\\\\\\\\Version_REDIR-64_==_TRUE_EXISTS_==_TRUE_VALUE_<=_20.1\")
<!--NeedCopy-->
Replace the preceding scan configuration with the following configuration:
sys.client_expr(\"sys_0_REG_PATH_==_HKEY\\\\_LOCAL\\\\_MACHINE\\\\\\\\SOFTWARE\\\\\\\\Citrix\\\\\\\\AppProtection\\\\\\\\Version_REDIR-64_==_TRUE_EXISTS_==_RUE_VALUE_contains_20.1\")
<!--NeedCopy-->
EPA client download failure
The EPA client download from NetScaler Gateway might fail while upgrading the EPA client on the end-user machine.
Workaround:
Use the following NOCACHE parameter to avoid this issue:
add cache policy bypass_epa_plugin_cache -rule "HTTP.REQ.URL.ENDSWITH(\".dmg\") || HTTP.REQ.URL.ENDSWITH(\".exe\") || HTTP.REQ.URL.ENDSWITH(\".deb\")" -action NOCACHE
bind vpn vserver <vpn-vserver-name> -policy bypass_epa_plugin_cache -priority 5 -gotoPriorityExpression END -type REQUEST
bind authentication vserver <authvs-name> -policy bypass_epa_plugin_cache -priority 5 -gotoPriorityExpression END -type REQUEST
<!--NeedCopy-->