Configure authentication and authorization settings
Authentication with the NetScaler SDX Management Service can be local or external. With external authentication, the Management Service grants user access based on the response from an external server. The Management Service supports the following external authentication protocols:
- Remote Authentication Dial In User Service (RADIUS)
- Terminal Access Controller Access-Control System (TACACS)
- Lightweight Directory Access Protocol (LDAP)
The Management Service also supports authentication requests from SSH. The SSH authentication supports only keyboard-interactive authentication requests. The authorization of SSH users is limited to admin privileges only. Users with read-only privileges cannot log on through SSH.
To configure authentication, specify the authentication type, and configure an authentication server.
Authorization through the Management Service is local. The Management Service supports two levels of authorization. Users with admin privileges are allowed to perform any action on the management service. Users with read-only privileges are allowed to perform only read operations. The authorization of SSH users is limited to admin privileges only. Users with read-only privileges cannot log on through SSH.
Authorization for RADIUS and LDAP is supported by group extraction. You can set the group extraction attributes during the configuration of RADIUS or LDAP servers on the Management Service. The extracted group name is matched with the group names on the Management Service to determine the privileges given to the user. A user can belong to multiple groups. In that case, if any group to which the user belongs has admin privileges, the user has admin privileges. A Default Authentication group attribute can be set during configuration. This group is considered along with the extracted groups for authorization.
In TACACS authorization, the TACACS server administrator must permit a special command, admin for a user with admin privileges and deny this command for users with read-only privileges. When a user logs on to an SDX appliance, the Management Service checks if the user has permission to run this command. If the user has permission, the user is assigned the admin privileges else the user is assigned read-only privileges.
Add a user group
Groups are logical sets of users that need to access common information or perform similar kinds of tasks. You can organize users into groups defined by a set of common operations. By providing specific permissions to groups rather than individual users, you can save time when creating users.
If you are using external authentication servers for authentication, groups in SDX can be configured to match groups configured on authentication servers. When a user belonging to a group whose name matches a group on an authentication server, logs on and is authenticated, the user inherits the settings for the group.
To add a user group
-
Navigate to Configuration > System > User Administration > Groups, and then click Add.
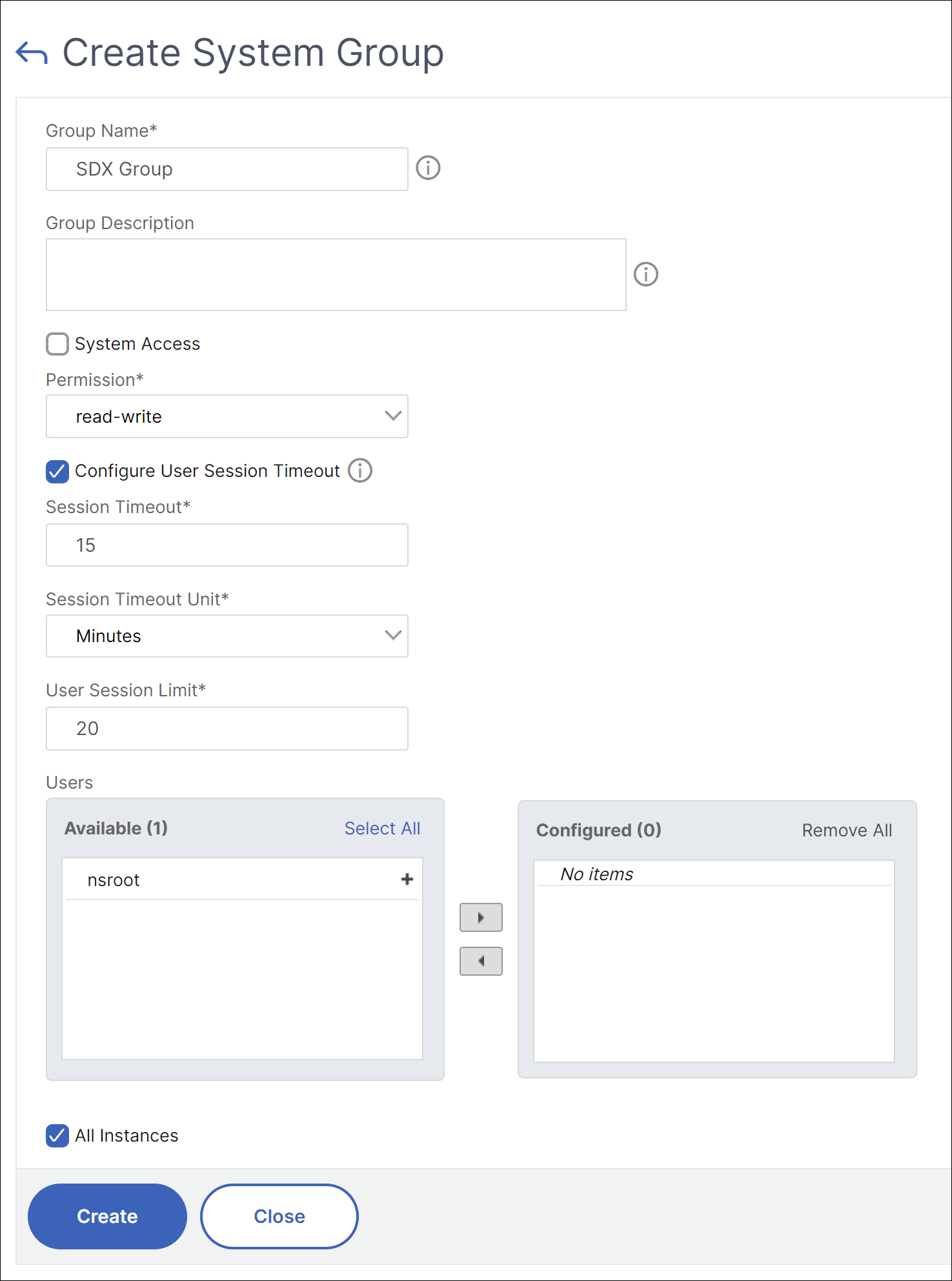
- In the Create System Group page, update the following parameters:
- Group Name: Enter the name of the group. The allowed characters include alphanumerics, underscore(_), hash (#), period(.), space, colon (:), at (@), equals (=), and hyphen (-) characters. Maximum length: 64.
- Group Description: Enter a brief description for the group.
- System Access: Select the option to give access to the entire SDX appliance and the instances running on it. Alternatively, for instance-level access, select the instances under All Instances.
-
Permission: Select the group privileges from the list. The admin has read-write privilege. The possible values are:
- read-write: The group can perform all administration tasks related to the Management Service. By default, the group permission is set to read-write.
- read: The group can only monitor the system.
-
Configure User Session Timeout: Select the option to configure the time period for a user to remain active.
When enabled, you can specify the following parameters:
- Session Timeout: Enter the time period for how long a user session can remain active. Default value: 15.
- Session Timeout Unit: Select the timeout unit from the list, in minutes or hours. Default value: minutes.
- User Session Limit: Enter the maximum number of sessions allowed per user.
Note:
Members of admin and read-only groups are assigned 40 user sessions by default. Members of other groups are assigned 20 user sessions by default.
- Users: Lists the users belonging to the group. You can add the users to a group by selecting from the Available list and moving to the Configured list.
- Click Create and Close.
Configure user accounts
A user logs on to the SDX appliance to perform appliance management tasks. To allow a user to access the appliance, you must create a user account on the SDX appliance for that user. Users are authenticated locally, on the appliance.
Important: The password applies to the SDX appliance, Management Service, and Citrix Hypervisor. Do not change the password directly on the Citrix Hypervisor.
To configure a user account
-
On the Configuration tab, under System, expand Administration, and then click Users. The Users pane displays a list of existing user accounts, with their permissions.
-
In the Users pane, do one of the following:
- To create a user account, click Add.
- To modify a user account, select the user, and then click Modify.
-
In the Create System User or Modify System User dialog box, set the following parameters:
- Name*: The user name of the account. The following characters are allowed in the name: letters a through z and A through Z, numbers 0 through 9, period (.), space, and underscore (_). Maximum length: 128. You cannot change the name.
- Password*: The password for logging on to the appliance. Maximum length: 128
- Confirm Password*: The password.
-
Permission*: The user’s privileges on the appliance. Possible values:
- admin: The user can perform all administration tasks related to the Management Service.
- read-only: The user can only monitor the system and change the password of the account. Default: admin.
-
Enable External Authentication: Enables external authentication for this user. Management Service attempts external authentication before database user authentication. If this parameter is disabled, the user is not authenticated with the external authentication server.
Note: If the remote authentication server is not reachable, the user might lose access to the appliance. In such cases, authentication falls back to the default admin user (
nsroot). -
Configure Session Timeout: Enables you to configure the time period for how long a user can remain active. Specify the following details:
- Session Timeout: The time period for how long a user session can remain active.
- Session Timeout Unit: The timeout unit, in minutes or hours.
- Groups: Assign the groups to the user.
*A required parameter
-
Click Create or OK, and then click Close. The user that you created is listed in the Users pane.
To remove a user account
- On the Configuration tab, in the navigation pane, expand System, expand Administration, and then click Users.
- In the Users pane, select the user account, and then click Delete.
- In the Confirm message box, click OK.
Set the authentication type
From the Management Service interface, you can specify local or external authentication. External authentication is disabled for local users by default. It can be enabled by checking the Enable External Authentication option when adding the local user or modifying the settings for the user.
Important: External authentication is supported only after you set up a RADIUS, LDAP, or TACACS authentication server.
To set the authentication type
- On the Configuration tab, under System, click Authentication.
- In the details pane, click Authentication Configuration.
- Set the following parameters:
- Server Type: Type of authentication server configured for user authentication. Possible values: LDAP, RADIUS, TACACS, and Local.
-
Server Name: Name of the authentication server configured in the Management Service. The menu lists all the servers configured for the selected authentication type.
- Enable fallback local authentication: Alternatively, you can choose to authenticate a user with the local authentication when external authentication fails. This option is enabled by default.
- Click OK.
Enable or disable basic authentication
You can authenticate to the Management Service NITRO interface using basic authentication. By default, basic authentication is enabled in the SDX appliance. Perform the following to disable basic authentication using the Management Service interface.
To disable basic authentication
- On the Configuration tab, click System.
- In the System Settings group, click Change System Settings.
- In the Configure System Settings dialog box, clear the Allow Basic Authentication check box.
- Click OK.