-
Basic components of authentication, authorization, and auditing configuration
-
-
Protected user authentication
-
Web Application Firewall protection for VPN virtual servers and authentication virtual servers
-
On-premises NetScaler Gateway as an identity provider to Citrix Cloud
-
Authentication, authorization, and auditing with commonly used protocols
-
Troubleshoot authentication and authorization related issues
This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Protected user authentication
The “Protected Users” security group in Active Directory enforces strict security policies for the members of this group. These policies are designed to protect privileged accounts (for example, domain admins) by enforcing stricter authentication methods.
Starting with NetScaler release 14.1 build 47.x, you can configure user authentication for LDAP users belonging to the “Protected Users” group in the Active Directory. For sample configuration of protected user authentication, see Configure protected user as an authentication factor in NetScaler nFactor authentication.
Important:
Disable the Do not require Kerberos preauthentication setting from account properties for Protected Users in Active Directory. NetScaler uses Kerberos authentication to authenticate Protected Users.
To configure protected user authentication by using the CLI
At the command prompt, type:
add authentication protectedUserAction protectedUser -realmStr <AAA.LOCAL> -maxConcurrentUsers <8>
<!--NeedCopy-->
In the preceding command:
-
realmStr: Specifies the domain to which the user belongs. This parameter is mandatory. -
maxConcurrentUsers: Limits the number of concurrent authentication requests to prevent DDoS attacks. This parameter is optional. Default value: 8.
Example:
If the protected user belongs to realm aaa.local1, then that realm must be mentioned as part of realmStr parameter as follows:
add authentication protectedUserAction <name> -realmStr aaa.local1
To configure protected user authentication by using the GUI
-
Configure the LDAP group extraction to extract the users in the “Protected Users” group. For more information, see Create an LDAP Authentication Action using the GUI.
-
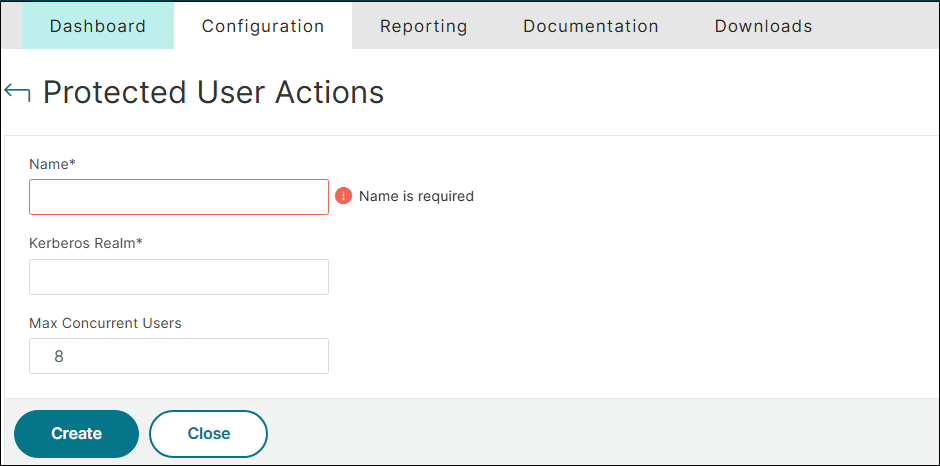
Navigate to Security > AAA - Application Traffic > Policies > Authentication > Advanced Policies > Actions > PROTECTED USER and click Add.
-
In the Protected User Actions page, enter values for the following parameters:
-
Name: Name for the protected user authentication. This parameter is mandatory.
-
Kerberos Realm: Domain to which the user belongs. This parameter is mandatory.
-
Max Concurrent Users: Limits the number of concurrent authentication requests to prevent DDoS attacks. This parameter is optional. Default value: 8.
-
-
Click Create.
Share
Share
This Preview product documentation is Cloud Software Group Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Cloud Software Group Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Cloud Software Group product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.