Advanced policy support for enterprise bookmarks
Enterprise bookmarks (VPN URLs) can be configured as advanced policies.
Notes:
NetScaler Gateway supports HTTP, HTTPs, and RDP protocols for the enterprise bookmarks.
NetScaler Gateway supports only absolute URLs for the enterprise bookmarks.
Configure VPN URL as an advanced policy
On the GUI
-
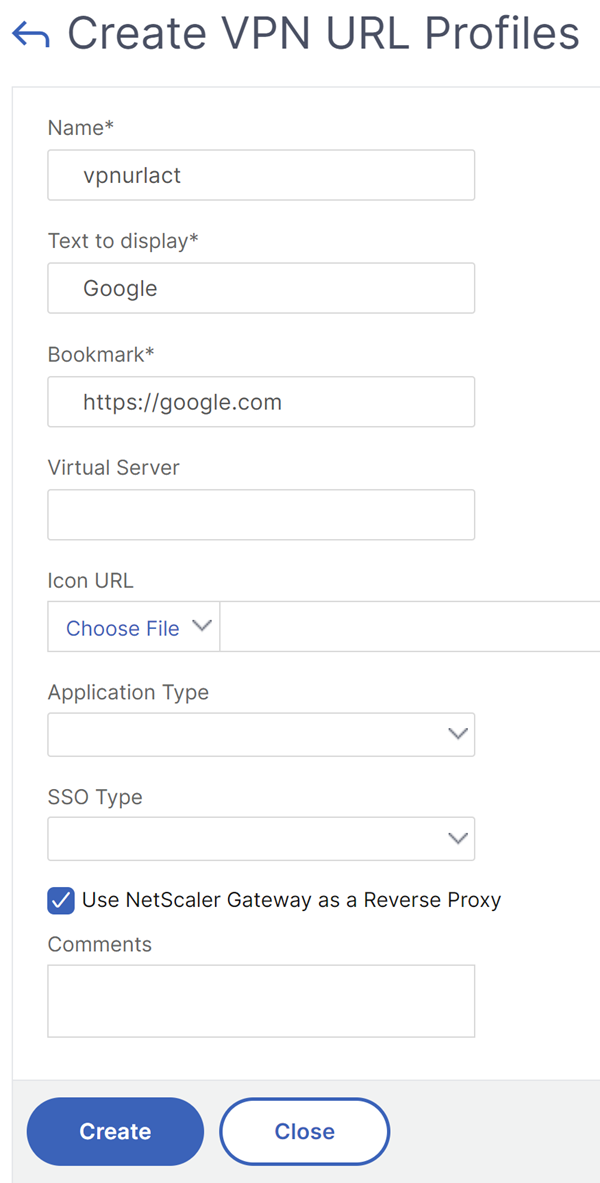
Create a VPN URL Profile.
-
Navigate to Configuration > NetScaler Gateway > Policies > VPN URL.
-
On the VPN URL Policies and Profiles page, select the VPN URL Profiles tab and click Add.
-
Update the required fields and click Create.
- Name: A name for the VPN URL profile.
- Text to display: A brief description of the link. The description appears on the access interface.
- Bookmark: Web address of the application.
- Virtual Server: Name of the associated load balancing or content switching virtual server that is configured. This field is optional.
- Icon URL: The icons uploaded in this field are supported for all themes except the default theme. Maximum recommended size is 70x70 pixels. We recommend that you use transparent images. This field is optional.
- Application Type: select the type of application (VPN, clientless VPN, or SaaS) that the URL represents. This field is optional.
- SSO Type: SSO type that you want to configure for the bookmark. When SSO is configured, users can access the applications without having to enter their credentials in the subsequent logons. The following SSO types are supported:
- Unified Gateway: This SSO configuration allows secure remote access to multiple resources of an application through a single URL.
- Self-authentication: In this SSO configuration, NetScaler Gateway users are prompted to provide the login credentials to access the application.
- SAML-based authentication: In this SSO configuration, NetScaler Gateway uses an IdP to validate the user details, generates a SAML assertion, and sends it to the SP. If the validation passes, the SSO is successful.
Note:
If you enable clientless access, you can make sure that requests to websites go through NetScaler Gateway. For example, you added a bookmark for Google. Select the Use NetScaler Gateway as a reverse proxy check box. When you select this check box, website requests go from the user device to NetScaler Gateway and then to the website. When you clear the check box, requests go from the user device to the website. This check box is only available if you enable clientless access.
-
-
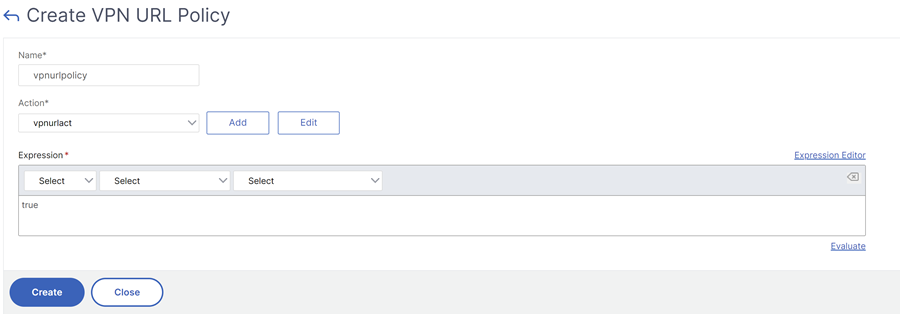
Create a VPN URL Policy.
-
Navigate to Configuration > NetScaler Gateway > Policies > VPN URL.
-
On the VPN URL Policies and Profiles page, select the VPN URL Policy tab and click Add.
-
Update the required fields and click Create.
- Name: A name for the VPN URL policy.
- Action: Select the configured VPN URL profile. If there is no profile on the drop-down list, click Add and repeat step 1.
- Expression: Refer to Policies and expressions for information about the advanced policy expressions.
-
-
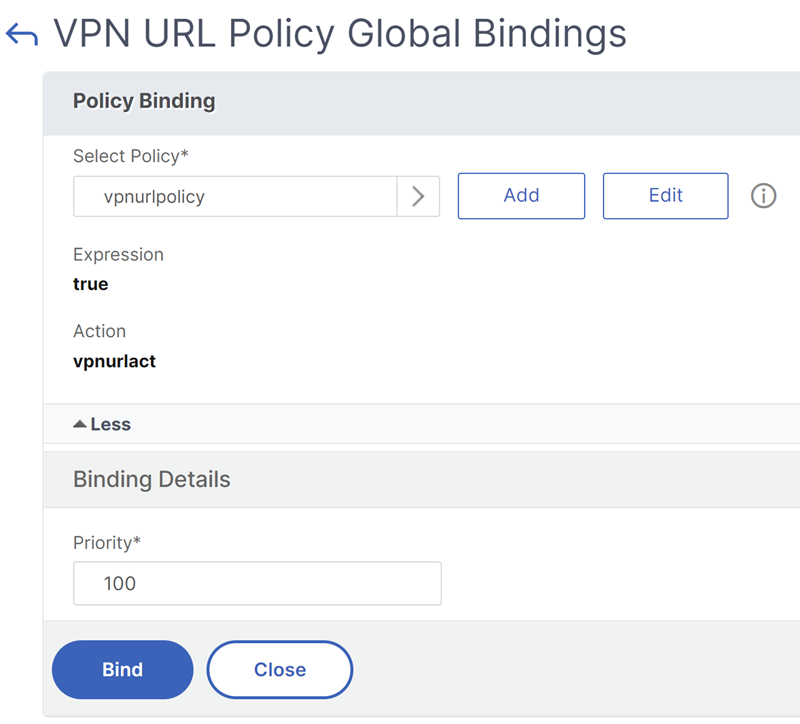
Bind the VPN URL policy to a bind point.
-
Navigate to Configuration > NetScaler Gateway > Policies > VPN URL.
-
On the VPN URL Policies and Profiles page, select the VPN URL Policy tab.
-
Select Global Bindings from the Select Action drop-down list.
-
Select the VPN URL policy. If there is no policy listed, click Add and repeat step 2.
-
In the Binding Details section, assign a priority to the VPN URL policy.
-
On the CLI
Create a VPN URL action:
At the command prompt, type the following:
add vpn urlAction <name> -linkName <string> -actualURL <string> \[-vServerName <string>] \[-clientlessAccess \( ON | OFF )] \[-comment <string>] \[-iconURL <URL>] \[-ssotype <ssotype>] \[-applicationtype <applicationtype>] \[-samlSSOProfile <string>]
NetScaler Gateway supports the following operations for VPN URL action:
-
add
add vpn urlAction <name> -linkName <string> -actualURL <string> \[-vServerName <string>] \[-clientlessAccess \( ON | OFF )] \[-comment <string>] \[-iconURL <URL>] \[-ssotype <ssotype>] \[-applicationtype <applicationtype>] \[-samlSSOProfile <string>] -
set
set vpn urlAction <name> \[-vServerName <string>] \[-clientlessAccess \( ON | OFF )] \[-comment <string>] \[-iconURL <URL>] \[-ssotype <ssotype>] \[-applicationtype <applicationtype>] \[-samlSSOProfile <string>] -
unset
unset vpn urlAction <name> [-vServerName] [-clientlessAccess] [-comment] [-iconURL] [-ssotype] [-applicationtype] [-samlSSOProfile]Note:
If you set clientless access to ON, you can make sure that requests to websites go from the user device to NetScaler Gateway and then to the website.
-
show
show vpn urlAction [<name>] -
remove
remove vpn urlAction <name> -
rename
rename vpn urlAction <name>@ <newName>@
Create a VPN URL policy:
NetScaler Gateway supports the following operations for VPN URL policy:
-
add
add vpn urlPolicy <name> -rule <expression> -action <string> [-comment <string>] [-logAction <string>] -
set
set vpn urlPolicy <name> [-rule <expression>] [-action <string>] [-comment <string>] [-logAction <string>] -
unset
unset vpn urlPolicy <name> [-comment] [-logAction] -
show
show vpn urlPolicy [<name>] -
remove
remove vpn urlPolicy <name> -
rename
rename vpn urlpolicy <name>@ <newName>@ -
stat
stat vpn urlpolicy \[<name>] \[-detail] \[-fullValues] \[-ntimes <positive\_integer>] \[-logFile <input\_filename>] \[-clearstats \( basic | full )]
Bind the policy to a bind point:
NetScaler Gateway supports the following operations for VPN URL policy binding:
-
bind
bind vpn vserver <vserver name> -policy <string> -priority <positive_integer> [-gotoPriorityExpression <expression>] bind vpn global -policyName <string> -priority <positive_integer> [-gotoPriorityExpression <expression>] bind aaa user <userName> -policy <string> [-priority <positive_integer>] [-type <type>] [-gotoPriorityExpression <expression>] bind aaa group <groupName> -policy <string> [-priority <positive_integer>] [-type <type>] [-gotoPriorityExpression <expression>] -
unbind
unbind vpn vserver <name> -policy <string> unbind vpn global -policyName <string> unbind aaa user <name> -policy <string> unbind aaa group <name> -policy <string>Note:
Bind Points are
aaauser,aaagroup,vpnvserver, andvpnglobal.