NetScaler as an Active Directory Federation Services proxy
Active Directory Federation Services (ADFS) is a Microsoft service that enables single sign-on (SSO) experience for Active Directory-authenticated clients to resources outside the enterprise data center. An ADFS server farm allows internal users to access external cloud-hosted services. But the moment external users are brought into the mix, the external users must be given a way to connect remotely and access cloud-based services through federated identity. Most enterprises do not prefer keeping the ADFS server exposed in the DMZ. Therefore, ADFS proxy plays a critical role in remote user connectivity and application access.
For more than a decade, NetScaler appliance is playing similar roles of remote user connectivity, and application access. NetScaler appliance becomes the preferred solution to be used as ADFS proxy for supporting a new ADFS implementation to enable the following services:
- Secure connectivity.
- Authentication and handling of federated identity.
For more information about NetScaler as a SAML IdP, see NetScaler as a SAML IdP.
Advantages of ADFS proxy
- Reduces the footprint in DMZ to cater the need for most of the enterprises.
- Provides an SSO experience for end users.
- Supports rich methods for pre-authentication and enables multifactor authentication.
- Supports both active and passive clients.
Prerequisites for using NetScaler as ADFS proxy
Before you configure the NetScaler appliance as an ADFS proxy, make sure that the following prerequisites are met:
- A NetScaler appliance with 12.1 build or later.
- Domain ADFS server.
- Domain SSL certificate.
- Virtual IP for Content Switching virtual server.
- Enable Load Balancing, SSL Offload, Content Switching, Rewrite, and authentication, authorization, and auditing traffic management features on NetScaler appliance.
Configure NetScaler appliance as ADFS proxy
To achieve this use case, configure NetScaler as an ADFS proxy in a DMZ zone. The ADFS server is configured along with the AD domain controller in the back-end.
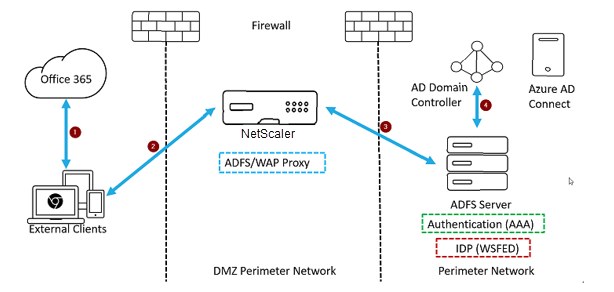
-
A client request to access Microsoft Office365 gets redirected to NetScaler deployed as ADFS proxy.
-
User’s credentials are passed to the ADFS server.
-
ADFS server authenticates the credentials with on-premises AD of the domain.
-
ADFS server upon successful validation of credentials with AD, generates a token which is passed to Microsoft Office365 for session establishment.
The following are the high-level steps involved in configuring NetScaler appliance before you configure as ADFS proxy.
At the NetScaler command prompt, type the following commands:
-
Create an SSL profile for the back-end and enable SNI in the SSL profile. Disable SSLv3/TLS1.
add ssl profile <new SSL profile> -sslprofileType backEnd -sniEnable ENABLED -ssl3 DISABLED -tls1 DISABLED -commonName <FQDN of ADFS> -
Disable SSLv3/TLS1 for the service.
set ssl service <adfs service name> -sslProfile <SSL profile created in the above step> -
Enable SNI extension for back-end server handshakes.
set vpn parameter –backendServerSni ENABLEDset ssl parameter -denySSLReneg NONSECURE
Configure NetScaler appliance as ADFS proxy using the CLI
The following sections are categorized based on the requirement to complete the configuration steps.
To configure ADFS service
-
Configure ADFS service on NetScaler for ADFS server.
add service <Domain_ADFS_Service> <ADFS Server IP> SSL 443 -gslb NONE -maxClient 0 -maxReq 0 -cip DISABLED -usip NO -useproxyport YES -sp OFF -cltTimeout 180 -svrTimeout 360 -CKA NO -TCPB NO -CMP NOExample
add service CTXTEST_ADFS_Service 1.1.1.1 SSL 443 -gslb NONE -maxClient 0 -maxReq 0 -cip DISABLED -usip NO -useproxyport YES -sp OFF -cltTimeout 180 -svrTimeout 360 -CKA NO -TCPB NO -CMP NO
-
Configure FQDN for content switching virtual server and enable SNI.
set ssl service <Domain_ADFS_Service> -SNIEnable ENABLED -commonName <sts.domain.com>Example
set ssl service CTXTEST_ADFS_Service -SNIEnable ENABLED -commonName sts.ctxtest.com
To configure ADFS load balancing virtual server
Important
Domain SSL certificate (SSL_CERT) is required for secure traffic.
-
Configure ADFS load balancing virtual server.
add lb vserver <Domain_ADFS_LBVS> SSL <IP_address> -persistenceType NONE -cltTimeout 180Example
add lb vserver CTXTEST_ADFS_LBVS SSL 192.168.1.0 -persistenceType NONE -cltTimeout 180 -
Bind ADFS load balancing virtual server to ADFS service.
bind lb vserver <Domain_ADFS_LBVS> <Domain_ADFS_Service>Example
bind lb vserver CTXTEST_ADFS_LBVS CTXTEST_ADFS_Service -
Bind an SSL virtual server certificate-key pair.
bind ssl vserver <Domain_ADFS_LBVS> -certkeyName <SSL_CERT>Example
bind ssl vserver CTXTEST_ADFS_LBVS -certkeyName ctxtest_newcert_2019
To configure content switching virtual server for domain
Note
One free virtual IP (for example, 2.2.2.2), which is NATed to public IP is required for a content switching virtual server. It must be reachable for both external and internal traffic.
-
Create a content switching virtual server with free VIP.
add cs vserver <Domain_CSVS> SSL <FREE VIP> 443 -cltTimeout 180 -persistenceType NONEExample
add cs vserver CTXTEST_CSVS SSL 2.2.2.2 443 -cltTimeout 180 -persistenceType NONE -
Bind content switching virtual server to load balancing virtual server.
bind cs vserver <Domain_CSVS> -lbvserver <Domain_ADFS_LBVS>Example
bind cs vserver CTXTEST_CSVS -lbvserver CTXTEST_ADFS_LBVSset ssl vserver CTXTEST_CSVS -sessReuse DISABLED
-
Bind an SSL virtual server certificate-key pair.
bind ssl vserver <Domain_CSVS> -certkeyName <SSL_CERT>Example
bind ssl vserver CTXTEST_CSVS -certkeyName ctxtest_newcert_2019
Supported protocols
The Microsoft provided protocols plays a vital role in integrating with the NetScaler appliance. NetScaler as ADFS proxy supports the following protocols:
- WS-Federation. For details, see Web Services Federation protocol.
- ADFSPIP. For details, see Active Directory Federation Service Proxy Integration Protocol compliance.
Note
NetScaler appliance does not support device certificate authentication when deployed as an ADFS proxy.