Deploy NetScaler® Web App Firewall on Azure
NetScaler Web App Firewall is an enterprise grade solution offering state of the art protections for modern applications. NetScaler Web App Firewall mitigates threats against public-facing assets, including websites, web applications, and APIs. NetScaler Web App Firewall includes IP reputation-based filtering, Bot mitigation, OWASP Top 10 application threats protections, Layer 7 DDoS protection and more. Also included are options to enforce authentication, strong SSL/TLS ciphers, TLS 1.3, rate limiting and rewrite policies. Using both basic and advanced WAF protections, NetScaler Web App Firewall provides comprehensive protection for your applications with unparalleled ease of use. Getting up and running is a matter of minutes. Further, using an automated learning model, called dynamic profiling, NetScaler Web App Firewall saves users precious time. By automatically learning how a protected application works, NetScaler Web App Firewall adapts to the application even as developers deploy and alter the applications. NetScaler Web App Firewall helps with compliance for all major regulatory standards and bodies, including PCI-DSS, HIPAA, and more. With our CloudFormation templates, it has never been easier to get up and running quickly. With auto scaling, users can rest assured that their applications remain protected even as their traffic scales up.
NetScaler Web App Firewall can be installed as either a Layer 3 network device or a Layer 2 network bridge between customer servers and customer users, usually behind the customer company’s router or firewall. For more information, see Introduction to NetScaler Web App Firewall.
NetScaler Web App Firewall deployment strategy
-
Deploy the web application firewall is to evaluate which applications or specific data need maximum security protection, which ones are less vulnerable, and the ones for which security inspection can safely be bypassed. This helps users in coming up with an optimal configuration, and in designing appropriate policies and bind points to segregate the traffic. For example, users might want to configure a policy to bypass security inspection of requests for static web content, such as images, MP3 files, and movies, and configure another policy to apply advanced security checks to requests for dynamic content. Users can use multiple policies and profiles to protect different contents of the same application.
-
To baseline the deployment, create a virtual server and run test traffic through it to get an idea of the rate and amount of traffic flowing through the user system.
-
Deploy the Web Application Firewall. Use NetScaler ADM and the Web Application Firewall StyleBook to configure the Web Application Firewall. See the StyleBook section below in this guide for details.
-
Implement the NetScaler Web App Firewall and OWASP Top Ten.
The three of the Web Application Firewall protections are especially effective against common types of Web attacks, and are therefore more commonly used than any of the others. Thus, they should be implemented in the initial deployment. They are:
-
HTML Cross-Site Scripting: Examines requests and responses for scripts that attempt to access or modify content on a different website than the one on which the script is located. When this check finds such a script, it either renders the script harmless before forwarding the request or response to its destination, or it blocks the connection.
-
HTML SQL Injection: Examines requests that contain form field data for attempts to inject SQL commands into a SQL database. When this check detects injected SQL code, it either blocks the request or renders the injected SQL code harmless before forwarding the request to the Web server.
Note:
Ensure that your Web App Firewall is correctly configured for the following conditions to apply in your configuration:
>- If users enable the HTML Cross-Site Scripting check or the HTML SQL Injection check (or both). > >- User protected websites accept file uploads or contain Web forms that can contain large POST body data.
For more information about configuring the Web Application Firewall to handle this case, see Configuring the Application Firewall: Configuring the Web App Firewall.
- Buffer Overflow: Examines requests to detect attempts to cause a buffer overflow on the Web server.
Configuring the Web Application Firewall
Ensure that the NetScaler Web App Firewall is already enabled and functioning correctly. We recommend that you configure NetScaler Web App Firewall using the Web Application Firewall StyleBook. Most users find it the easiest method to configure the Web Application Firewall, and it is designed to prevent mistakes. Both the GUI and the command-line interface are intended for experienced users, primarily to modify an existing configuration or use advanced options.
SQL injection
The NetScaler Web App Firewall HTML SQL Injection check provides special defenses against the injection of unauthorized SQL code that might break user application security. NetScaler Web App Firewall examines the request payload for injected SQL code in three locations: 1) POST body, 2) headers, and 3) cookies. For more information, see HTML SQL injection check.
Cross-Site scripting
The HTML Cross-Site Scripting (cross-site scripting) check examines both the headers and the POST bodies of user requests for possible cross-site scripting attacks. If it finds a cross-site script, it either modifies (transforms) the request to render the attack harmless, or blocks the request. For more information, see HTML cross-site scripting check.
Buffer overflow check
The Buffer Overflow check detects attempts to cause a buffer overflow on the web server. If the Web Application Firewall detects that the URL, cookies, or header are longer than the configured length, it blocks the request because it can cause a buffer overflow. For more information, see Buffer overflow check.
Virtual patching/signatures
The signatures provide specific, configurable rules to simplify the task of protecting user websites against known attacks. A signature represents a pattern that is a component of a known attack on an operating system, web server, website, XML-based web service, or other resource. A rich set of preconfigured built-in or native rules offers an easy-to-use security solution, applying the power of pattern matching to detect attacks and protect against application vulnerabilities. For more information, see Signatures.
NetScaler Web App Firewall supports both Auto & Manual update of signatures. We also suggest enabling Auto-update for signatures to stay up to date.

These signature files are hosted on the AWS Environment and it is important to allow outbound access to NetScaler IP address’s from network firewalls to fetch the latest signature files. There is no effect of updating signatures to the NetScaler while processing real-time traffic.
Application security analytics
The Application Security Dashboard provides a holistic view of the security status of user applications. For example, it shows key security metrics such as security violations, signature violations, and threat indexes. The application security dashboard also displays attack-related information such as syn attacks, small window attacks, and DNS flood attacks for the discovered NetScaler.
Note:
To view the metrics of the application security dashboard, AppFlow for Security insight should be enabled on the NetScaler instances that users want to monitor.
To view the security metrics of a NetScaler instance on the application security dashboard:
-
Log in to NetScaler ADM using the administrator credentials.
-
Navigate to Applications > App Security Dashboard, and select the instance IP address from the Devices list.
Users can further drill down on the discrepancies reported on the Application Security Investigator by clicking the bubbles plotted on the graph.
Centralized learning on ADM
NetScaler Web App Firewall protects user web applications from malicious attacks such as SQL injection and cross-site scripting (XSS). To prevent data breaches and provide the right security protection, users must monitor their traffic for threats and real-time actionable data on attacks. Sometimes, the attacks reported might be false-positives and those need to be provided as an exception.
The centralized learning on NetScaler ADM is a repetitive pattern filter that enables WAF to learn the behavior (the normal activities) of user web applications. Based on monitoring, the engine generates a list of suggested rules or exceptions for each security check applied on the HTTP traffic.
It is much easier to deploy relaxation rules using the learning engine than to manually deploy it as necessary relaxations.
To deploy the learning feature, users must first configure a Web Application Firewall profile (set of security settings) on the user NetScaler. For more information, see Creating Web App Firewall Profiles.
NetScaler ADM generates a list of exceptions (relaxations) for each security check. As an administrator, you can review the list of exceptions in NetScaler ADM and decide to deploy or skip.
Using the WAF learning feature in NetScaler ADM, you can:
-
Configure a learning profile with the following security checks.
-
Buffer Overflow
- HTML Cross-Site Scripting
Note:
The cross-site script limitation of location is only FormField.
- HTML SQL Injection
Note:
For the HTML SQL Injection check, users must configure
set -sqlinjectionTransformSpecialChars ONandset -sqlinjectiontype sqlspclcharorkeywordsin the NetScaler.
-
-
Check the relaxation rules in NetScaler ADM and decide to take the necessary action (deploy or skip).
-
Get the notifications through email, slack, and ServiceNow.
-
Use the dashboard to view relaxation details.
To use the WAF learning in NetScaler ADM:
-
Configure the learning profile: Configure the Learning Profile
-
See the relaxation rules: View Relaxation Rules and Idle Rules
-
Use the WAF learning dashboard: View WAF Learning Dashboard
StyleBooks
StyleBooks simplify the task of managing complex NetScaler configurations for user applications. A StyleBook is a template that users can use to create and manage NetScaler configurations. Here, users are primarily concerned with the StyleBook used to deploy the Web Application Firewall. For more information on StyleBooks, see StyleBooks.
Security insight analytics
Web and web service applications that are exposed to the Internet have become increasingly vulnerable to attacks. To protect applications from attack, users need visibility into the nature and extent of past, present, and impending threats, real-time actionable data on attacks, and recommendations on countermeasures. Security Insight provides a single-pane solution to help users assess user application security status and take corrective actions to secure user applications. For more information, see Security Insight.
Obtain detailed information about security breaches
Users might want to view a list of the attacks on an application and gain insights into the type and severity of attacks, actions taken by the ADC instance, resources requested, and the source of the attacks.
For example, users might want to determine how many attacks on Microsoft Lync were blocked, what resources were requested, and the IP addresses of the sources.
On the Security Insight dashboard, click Lync > Total Violations. In the table, click the filter icon in the Action Taken column header, and then select Blocked.
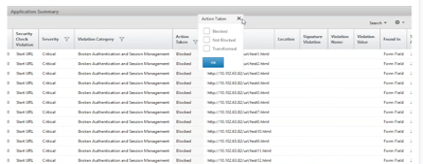
For information about the resources that were requested, review the URL column. For information about the sources of the attacks, review the Client IP column.
View log expression details
NetScaler use log expressions configured with the Application Firewall profile to take action for the attacks on an application in the user enterprise. In Security Insight, users can view the values returned for the log expressions used by the ADC instance. These values include, request header, request body and so on. In addition to the log expression values, users can also view the log expression name and the comment for the log expression defined in the Application Firewall profile that the ADC instance used to take action for the attack.
Prerequisites:
Ensure that users:
-
Configure log expressions in the Application Firewall profile. For more information, see Application Firewall.
-
Enable log expression-based Security Insights settings in NetScaler ADM. Do the following:
-
Navigate to Analytics > Settings, and click Enable Features for Analytics.
-
In the Enable Features for Analytics page, select Enable Security Insight under the Log Expression Based Security Insight Setting section and click OK.
-
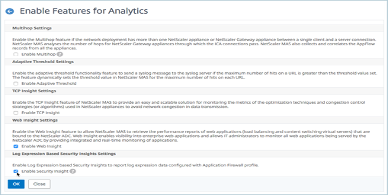
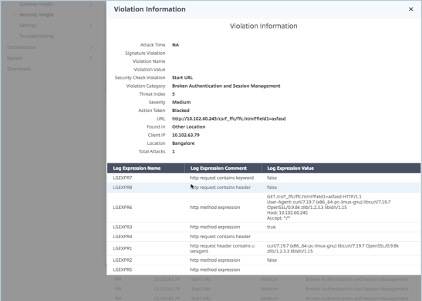
For example, you might want to view the values of the log expression returned by the ADC instance for the action it took for an attack on Microsoft Lync in the user enterprise.
On the Security Insight dashboard, navigate to Lync > Total Violations. In the Application Summary table, click the URL to view the complete details of the violation in the Violation Information page including the log expression name, comment, and the values returned by the ADC instance for the action.
Determine the Safety Index before deploying the Configuration. Security breaches occur after users deploy the security configuration on an ADC instance, but users might want to assess the effectiveness of the security configuration before they deploy it.
For example, users might want to assess the safety index of the configuration for the SAP application on the ADC instance with IP address 10.102.60.27.
On the Security Insight dashboard, under Devices, click the IP address of the ADC instance that users configured. Users can see that both the threat index and the total number of attacks are 0. The threat index is a direct reflection of the number and type of attacks on the application. Zero attacks indicate that the application is not under any threat.
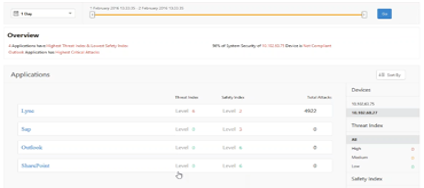
Click Sap > Safety Index > SAP_Profile and assess the safety index information that appears.
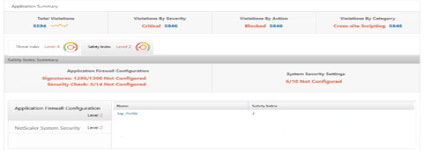
In the application firewall summary, users can view the configuration status of different protection settings. If a setting is set to log or if a setting is not configured, the application is assigned a lower safety index.
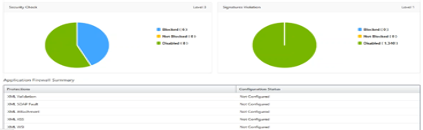
Security violations
Web applications that are exposed to the Internet have become vulnerable to attacks drastically. NetScaler ADM enables you to visualize actionable violation details to protect applications from attacks.
View application security violation details
Web applications that are exposed to the Internet have become drastically more vulnerable to attacks. NetScaler ADM enables users to visualize actionable violation details to protect applications from attacks. Navigate to Security > Security Violations for a single-pane solution to:
-
Access the application security violations based on their categories such as Network, Bot, and WAF
-
Take corrective actions to secure the applications
To view the security violations in NetScaler ADM, ensure:
-
Users have a premium license for the NetScaler (for WAF and BOT violations).
-
Users have applied for a license on the load balancing or content switching virtual servers (for WAF and BOT). For more information, see Manage Licensing on Virtual Servers.
-
Users can enable more settings. For more information, see the procedure available at the Setting up section in the NetScaler product documentation: Setting up.
Violation categories
NetScaler ADM enables users to view the violations available in All Violations:
Setting up
For violations, ensure whether Metrics Collector is enabled. By default, Metrics Collector is enabled on the NetScaler. For more information, see Configure Intelligent App Analytics.
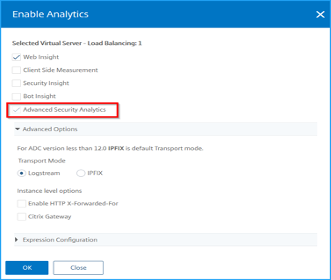
Enable advanced security analytics
-
Navigate to Networks > Instances > NetScaler, and select the instance type. For example, MPX.
-
Select the NetScaler instance and from the Select Action list, select Configure Analytics.
-
Select the virtual server and click Enable Analytics.
-
On the Enable Analytics window:
- Select Web Insight. After users select Web Insight, the read-only Advanced Security Analytics option is enabled automatically.
Note:
The Advanced Security Analytics option is displayed only for premium licensed ADC instances.
-
Select Logstream as Transport Mode
-
The Expression is true by default
-
Click OK
Enable web transaction settings
- Navigate to Analytics > Settings.
The Settings page is displayed.
-
Click Enable Features for Analytics.
-
Under Web Transaction Settings, select All.
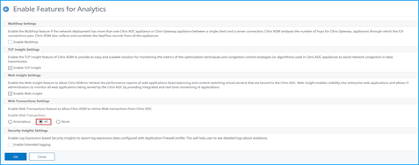
- Click Ok.
Security violations dashboard
In the security violations dashboard, users can view:
- Total violations occurred across all NetScaler and applications. The total violations are displayed based on the selected time duration.

- Total violations under each category.
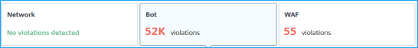
- Total ADCs affected, total applications affected, and top violations based on the total occurrences and the affected applications.
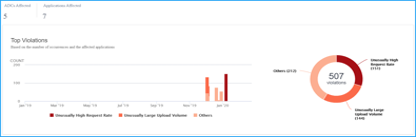
For more information on violations details, see All violations.
Bot insight
Configure BOT insight in NetScaler. For more information, see Bot.
View bots
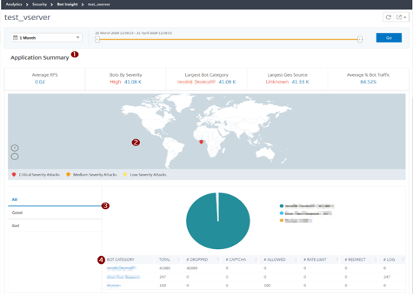
Click the virtual server to view the Application Summary
-
Provides the Application Summary details such as:
-
Average RPS – Indicates the average bot transaction requests per second (RPS) received on virtual servers.
-
Bots by Severity – Indicates that the highest bot transactions occurred based on the severity. The severity is categorized based on Critical, High, Medium, and Low.
For example, if the virtual servers have 11770 high severity bots and 1550 critical severity bots, then NetScaler ADM displays Critical 1.55 K under Bots by Severity.
- Largest Bot Category – Indicates that the highest bot attacks occurred based on the bot category.
For example, if the virtual servers have 8000 block-listed bots, 5000 allow listed bots, and 10000 Rate Limit Exceeded bots, then NetScaler ADM displays Rate Limit Exceeded 10 K under Largest Bot Category.
- Largest Geo Source – Indicates that the highest bot attacks occurred based on a region.
For example, if the virtual servers have 5000 bot attacks in Santa Clara, 7000 bot attacks in London, and 9000 bot attacks in Bangalore, then NetScaler ADM displays Bangalore 9 K under Largest Geo Source.
- Average % Bot Traffic – Indicates the human bot ratio.
-
-
Displays the severity of the bot attacks based on locations in the map view
-
Displays the types of bot attacks (Good, Bad, and all)
-
Displays the total bot attacks along with the corresponding configured actions. For example, if you have configured:
-
IP address range (192.140.14.9 to 192.140.14.254) as block list bots and selected Drop as an action for these IP address ranges
-
IP range (192.140.15.4 to 192.140.15.254) as block list bots and selected to create a log message as an action for these IP ranges
In this scenario, NetScaler ADM displays:
-
Total block listed bots
-
Total bots under Dropped
-
Total bots under Log
-
-
View CAPTCHA bots
In webpages, CAPTCHAs are designed to identify if the incoming traffic is from a human or an automated bot. To view the CAPTCHA activities in NetScaler ADM, users must configure CAPTCHA as a bot action for IP reputation and device fingerprint detection techniques in a NetScaler ADM instance. For more information, see: Configure Bot Management.
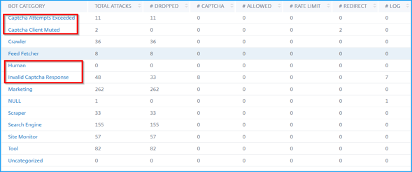
The following are the CAPTCHA activities that NetScaler ADM displays in Bot insight:
-
Captcha attempts exceeded – Denotes the maximum number of CAPTCHA attempts made after login failures
-
Captcha client muted – Denotes the number of client requests that are dropped or redirected because these requests were detected as bad bots earlier with the CAPTCHA challenge
-
Human – Denotes the captcha entries performed from the human users
-
Invalid captcha response – Denotes the number of incorrect CAPTCHA responses received from the bot or human, when NetScaler sends a CAPTCHA challenge
View bot traps
To view bot traps in NetScaler ADM, you must configure the bot trap in NetScaler. For more information, see: Configure Bot Management.
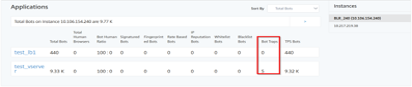
To identify the bot trap, a script is enabled in the webpage and this script is hidden from humans, but not to bots. NetScaler ADM identifies and reports the bot traps, when this script is accessed by the bots.
Click the virtual server and select Zero Pixel Request
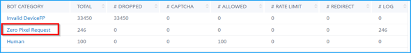
View bot details
For further details, click the bot attack type under Bot Category.
The details such as attack time and total number of bot attacks for the selected captcha category are displayed.
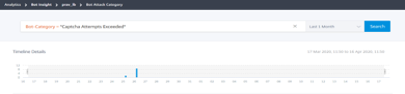
Users can also drag the bar graph to select the specific time range to be displayed with bot attacks.
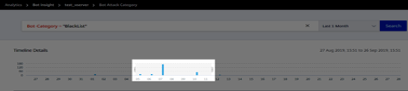
To get additional information of the bot attack, click to expand.
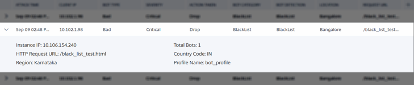
-
Instance IP –Indicates the NetScaler instance IP address.
-
Total Bots –Indicates that the total bot attacks occurred for that particular time.
-
HTTP Request URL –Indicates the URL that is configured for captcha reporting.
-
Country Code – Indicates the country where the bot attack occurred.
-
Region – Indicates the region where the bot attack occurred.
-
Profile Name – Indicates the profile name that users provided during the configuration.
Advanced search
Users can also use the search text box and time duration list, where they can view bot details as per the user requirement. When users click the search box, the search box gives them the following list of search suggestions.
-
Instance IP – NetScaler instance IP address.
-
Client-IP – Client IP address.
-
Bot-Type – Bot type such as Good or Bad.
-
Severity – Severity of the bot attack.
-
Action-Taken – Action taken after the bot attack such as Drop, No action, Redirect.
-
Bot-Category – Category of the bot attack such as block list, allow list, fingerprint. Based on a category, users can associate a bot action to it.
-
Bot-Detection – Bot detection types (block list, allow list, and so on) that users have configured on NetScaler.
-
Location – Region/country where the bot attack has occurred
-
Request-URL – URL that has the possible bot attacks
Users can also use operators in the user search queries to narrow the focus of the user search. For example, if users want to view all bad bots:
-
Click the search box and select Bot-Type
-
Click the search box again and select the operator =
-
Click the search box again and select Bad
-
Click Search to display the results
Unusually high request rate
Users can control the incoming and outgoing traffic from or to an application. A bot attack can perform an unusually high request rate. For example, if users configure an application to allow 100 requests/minute and if users observe 350 requests, then it might be a bot attack.
Using the Unusually High Request Rate indicator, users can analyze the unusual request rate received to the application.
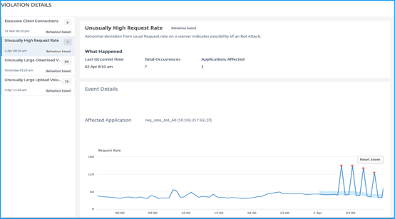
Under Event Details, users can view:
-
The affected application. Users can also select the application from the list if two or more applications are affected with violations.
-
The graph indicating all violations
-
The violation occurrence time
-
The detection message for the violation, indicating the total requests received and % of excessive requests received than the expected requests
-
The accepted range of expected request rates range from the application
Bot Detection
The NetScaler bot management system uses various techniques to detect the incoming bot traffic. The techniques are used as detection rules to detect the bot type.
Configuring Bot management by using GUI
Users can configure NetScaler bot management by first enabling the feature on the appliance. For more information, see Bot Detection.
IP reputation
IP reputation is a tool that identifies IP addresses that send unwanted requests. Using the IP reputation list you can reject requests that are coming from an IP address with a bad reputation.
Configure IP reputation by using GUI
This configuration is a prerequisite for the bot IP reputation feature. For more information, see IP Reputation.
Auto update for Bot signatures
The bot static signature technique uses a signature lookup table with a list of good bots and bad bots. For more information, see Signature auto update.
NetScaler Web App Firewall and OWASP top ten–2021
The Open Web Application Security Project(OWAP) released the OWASP Top 10 for 2021 for web application security. This list documents the most common web application vulnerabilities and is a great starting point to evaluate web security. This section explains on how to configure the NetScaler Web App Firewall to mitigate these flaws. WAF is available as an integrated module in the NetScaler (Premium Edition) and a complete range of appliances.
The full OWASP Top 10 document is available at OWASP Top Ten.
| OWASP Top-10 2021 | NetScaler Web App Firewall Features |
|---|---|
| A1:2021 Broken Access Control | AAA, Authorization security features within AAA module of NetScaler, Form protections, and cookie tampering protections, StartURL, and ClosureURL |
| A2:2021 - Cryptographic Failures | Credit Card protection, Safe Commerce, Cookie proxying, and Cookie encryption |
| A3:2021- Injection | Injection attack prevention (SQL or any other custom injections such as OS Command injection, XPath injection, and LDAP injection), auto update signature feature |
| A5:2021 Security Misconfiguration | This protection including WSI checks, XML message validation & XML SOAP fault filtering check |
| A6:2021 - Vulnerability and Outdated Components | Vulnerability scan reports, Application Firewall Templates, and Custom Signatures |
| A7:2021 - Identification and Authentication Failure | AAA, Cookie tampering protection, Cookie proxying, Cookie encryption, CSRF tagging, Use SSL |
| A8:2021 – Software and Data Integrity Failures | XML Security checks, GWT content type, custom signatures, Xpath for JSON and XML |
| A9:2021 – Security Logging and Monitoring Failures | User configurable custom logging, Management and Analytics System |
A1:2021 Broken Access Control
Restrictions on what authenticated users are allowed to do are often not properly enforced. Attackers can exploit these flaws to access unauthorized functionality and data, such as access other users’ accounts, view sensitive files, modify other users’ data, change access rights.
NetScaler Web App Firewall protections
-
AAA feature that supports authentication, authorization, and auditing for all application traffic allows a site administrator to manage access controls with the ADC appliance.
-
The Authorization security feature within the AAA module of the ADC appliance enables the appliance to verify, which content on a protected server it should allow each user to access.
-
Form field consistency: If object references are stored as hidden fields in forms, then using form field consistency you can validate that these fields are not tampered on subsequent requests.
-
Cookie proxying and cookie consistency: Object references that are stored in cookie values can be validated with these protections.
-
Start URL check with URL closure: Allows user access to a predefined allow list of URLs. URL closure builds a list of all URLs seen in valid responses during the user session and automatically allows access to them during that session.
A2:2021 - Cryptographic failures
Many web applications and APIs do not properly protect sensitive data, such as financial, healthcare, and PII. Attackers may steal or modify such poorly protected data to conduct credit card fraud, identity theft, or other crimes. Sensitive data may be compromised without extra protection, such as encryption at rest or in transit, and requires special precautions when exchanged with the browser.
NetScaler Web App Firewall protections
-
Web Application Firewall protects applications from leaking sensitive data like credit card details.
-
Sensitive data can be configured as safe objects in Safe Commerce protection to avoid exposure.
-
Any sensitive data in cookies can be protected by Cookie proxying and Cookie encryption.
A3:2021- Injection
Injection flaws, such as SQL, NoSQL, OS, and LDAP injection, occur when untrusted data is sent to an interpreter as part of a command or query. The attacker’s hostile data can trick the interpreter into running unintended commands or accessing data without proper authorization.
XSS flaws occur whenever an application includes untrusted data in a new webpage without proper validation or escaping, or updates an existing webpage with user-supplied data using a browser API that can create HTML or JavaScript. XSS allows attackers to run scripts in the victim’s browser, which can hijack user sessions, deface websites, or redirect the user to malicious sites.
NetScaler Web App Firewall protections
-
SQL injection prevention feature protects against common injection attacks. Custom injection patterns can be uploaded to protect against any type of injection attack, including XPath and LDAP. This is applicable for both HTML and XML payloads.
-
The auto update signature feature keeps the injection signatures up to date.
-
The field format protection feature allows the administrator to restrict any user parameter to a regular expression. For instance, you can enforce that a zip-code field contains integers only or even 5-digit integers.
-
Form field consistency validates each submitted user form against the user session form signature to ensure the validity of all form elements.
-
Buffer overflow checks ensure that the URL, headers, and cookies are in the right limits blocking any attempts to inject large scripts or code.
-
XSS protection protects against common XSS attacks. Custom XSS patterns can be uploaded to modify the default list of allowed tags and attributes. The ADC WAF uses a white list of allowed HTML attributes and tags to detect XSS attacks. This is applicable for both HTML and XML payloads.
-
ADC WAF blocks all the attacks listed in the OWASP XSS Filter Evaluation Cheat Sheet.
-
Field format check prevents an attacker from sending inappropriate web form data, which can be a potential XSS attack.
-
Form field consistency.
A5:2021 - Security misconfiguration
Security misconfiguration is the most commonly seen issue. This is commonly a result of insecure default configurations, incomplete or improvised configurations, open cloud storage, misconfigured HTTP headers, and verbose error messages containing sensitive information. Not only must all operating systems, frameworks, libraries, and applications be securely configured, but they must be patched and upgraded in a timely fashion.
Many older or poorly configured XML processors evaluate external entity references within XML documents. External entities can be used to disclose internal files using the file URI handler, internal file shares, internal port scanning, remote code execution, and denial of service attacks.
NetScaler Web App Firewall protections
-
The PCI-DSS report generated by the Application Firewall, documents the security settings on the Firewall device.
-
Reports from the scanning tools are converted to ADC WAF signatures to handle security misconfigurations.
-
NetScaler Web App Firewall Web Application Firewall supports Cenzic, IBM AppScan (Enterprise and Standard), Qualys, TrendMicro, WhiteHat, and custom vulnerability scan reports.
-
In addition to detecting and blocking common application threats that can be adapted for attacking XML-based applications (that is, cross-site scripting, command injection, and so on).
-
NetScaler Web App Firewall Web Application Firewall includes a rich set of XML-specific security protections. These include schema validation to thoroughly verify SOAP messages and XML payloads, and a powerful XML attachment check to block attachments containing malicious executables or viruses.
-
Automatic traffic inspection methods block XPath injection attacks on URLs and forms aimed at gaining access.
-
NetScaler Web App Firewall Web Application Firewall also thwarts various DoS attacks, including external entity references, recursive expansion, excessive nesting, and malicious messages containing either long or many attributes and elements.
A6:2021 - Vulnerable and outdated components
Components, such as libraries, frameworks, and other software modules, run with the same privileges as the application. If a vulnerable component is exploited, such an attack can facilitate serious data loss or server takeover. Applications and APIs using components with known vulnerabilities may undermine application defenses and enable various attacks and impacts.
NetScaler Web App Firewall protections
-
We recommend having the third-party components up to date.
-
Vulnerability scan reports that are converted to ADC signatures can be used to virtually patch these components.
-
Application firewall templates that are available for these vulnerable components can be used.
-
Custom signatures can be bound with the firewall to protect these components.
A7:2021–Broken authentication
Application functions related to authentication and session management are often implemented incorrectly, allowing attackers to compromise passwords, keys, or session tokens, or to exploit other implementation flaws to assume other users’ identities temporarily or permanently.
NetScaler Web App Firewall protections
-
NetScaler AAA module performs user authentication and provides Single Sign-On functionality to back-end applications. This is integrated into the NetScaler AppExpert policy engine to allow custom policies based on user and group information.
-
Using SSL offloading and URL transformation capabilities, the firewall can also help sites to use secure transport layer protocols to prevent stealing of session tokens by network sniffing.
-
Cookie proxying and cookie encryption can be employed to completely mitigate cookie stealing.
A8:2021 - Software and data integrity failure
Insecure deserialization often leads to remote code execution. Even if deserialization flaws do not result in remote code execution, they can be used to perform attacks, including replay attacks, injection attacks, and privilege escalation attacks.
NetScaler Web App Firewall protections
-
JSON payload inspection with custom signatures.
-
XML security: protects against XML denial of service (xDoS), XML SQL and Xpath injection and cross-site scripting, format checks, WS-I basic profile compliance, XML attachments check.
-
Field format checks and Cookie Consistency and Field Consistency can be used.
A9:2021 - Security logging and monitoring failures
Insufficient logging and monitoring, coupled with missing or ineffective integration with incident response, allows attackers to further attack systems, maintain persistence, pivot to more systems, and tamper, extract, or destroy data. Most breach studies show the time to detect a breach is over 200 days, typically detected by external parties rather than internal processes or monitoring.
NetScaler Web App Firewall protections
-
When the log action is enabled for security checks or signatures, the resulting log messages provide information about the requests and responses that the application firewall has observed while protecting your websites and applications.
-
The application firewall offers the convenience of using the built-in ADC database for identifying the locations corresponding to the IP addresses from which malicious requests are originating.
-
Default format (PI) expressions give the flexibility to customize the information included in the logs with the option to add the specific data to capture in the application firewall-generated log messages.
-
The application firewall supports CEF logs.
References
In this article
- NetScaler Web App Firewall deployment strategy
- Configuring the Web Application Firewall
- Application security analytics
- Centralized learning on ADM
- StyleBooks
- Security insight analytics
- Security violations
- Security violations dashboard
- Bot insight
- NetScaler Web App Firewall and OWASP top ten–2021
- A1:2021 Broken Access Control
- A2:2021 - Cryptographic failures
- A3:2021- Injection
- A5:2021 - Security misconfiguration
- A6:2021 - Vulnerable and outdated components
- A7:2021–Broken authentication
- A8:2021 - Software and data integrity failure
- A9:2021 - Security logging and monitoring failures
- References