-
-
Deploying in the DMZ
-
-
Configuring the VPN User Experience
-
How to Configure Full VPN Setup on a Citrix Gateway Appliance
-
AlwaysOn VPN before Windows logon (Formally AlwaysOn service)
-
Maintaining and Monitoring the System
-
Deploying with Citrix Endpoint Management, Citrix Virtual Apps, and Citrix Virtual Desktops
-
Accessing Citrix Virtual Apps and Desktops Resources with the Web Interface
-
Integrating Citrix Gateway with Citrix Virtual Apps and Desktops
-
Configuring Additional Web Interface Settings on Citrix Gateway
-
Configuring Access to Applications and Virtual Desktops in the Web Interface
-
-
Integrate Citrix Gateway with Citrix Virtual Apps and Desktops
-
Configuring Settings for Your Citrix Endpoint Management Environment
-
Configuring Load Balancing Servers for Citrix Endpoint Management
-
Configuring Load Balancing Servers for Microsoft Exchange with Email Security Filtering
-
Configuring Citrix Endpoint Management NetScaler Connector (XNC) ActiveSync Filtering
-
Allowing Access from Mobile Devices with Citrix Mobile Productivity Apps
-
Configuring Domain and Security Token Authentication for Citrix Endpoint Management
-
Configuring Client Certificate or Client Certificate and Domain Authentication
-
-
Citrix Gateway Enabled PCoIP Proxy Support for VMware Horizon View
-
Proxy Auto Configuration for Outbound Proxy support for Citrix Gateway
-
Integrate Citrix Gateway with Citrix Virtual Apps and Desktops
This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Deploying in the DMZ
Many organizations protect their internal network with a DMZ. A DMZ is a subnet that lies between an organization’s secure internal network and the Internet (or any external network). When you deploy Citrix Gateway in the DMZ, users connect with the Citrix Gateway plug-in or Citrix Receiver.
Figure 1. Citrix Gateway deployed in the DMZ
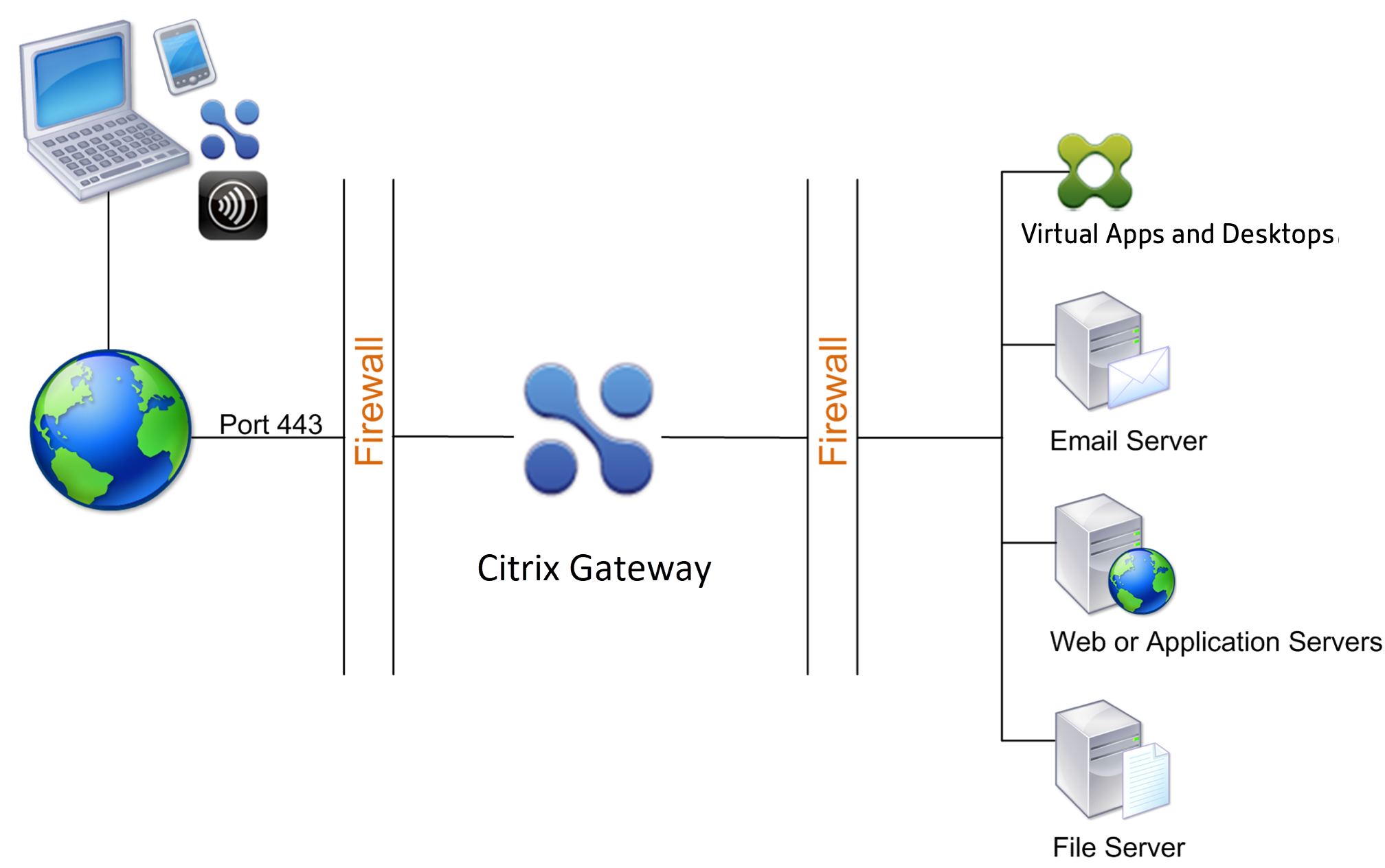
In the configuration shown in the preceding figure, you install Citrix Gateway in the DMZ and configure it to connect to both the Internet and the internal network.
Citrix Gateway Connectivity in the DMZ
When you deploy Citrix Gateway in the DMZ, user connections must traverse the first firewall to connect to Citrix Gateway. By default, user connections use SSL on port 443 to establish this connection. To allow user connections to reach the internal network, you must allow SSL on port 443 through the first firewall.
Citrix Gateway decrypts the SSL connections from the user device and establishes a connection on behalf of the user to the network resources behind the second firewall. The ports that must be open through the second firewall are dependent on the network resources that you authorize external users to access.
For example, if you authorize external users to access a web server in the internal network, and this server listens for HTTP connections on port 80, you must allow HTTP on port 80 through the second firewall. Citrix Gateway establishes the connection through the second firewall to the HTTP server on the internal network on behalf of the external user devices.
This Preview product documentation is Cloud Software Group Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Cloud Software Group Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Cloud Software Group product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.