Configure CIFS and SMB2/SMB3 acceleration
The CIFS acceleration feature provides a suite of protocol-specific performance enhancements to CIFS-based (Windows and Samba) file transfer and directory browsing, including enhancements to CIFS transport and to related protocols such as DCERPC.
CIFS acceleration has three parts:
-
TCP flow-control acceleration—This is performed on all accelerated CIFS connections, regardless of protocol version (SMB1, SMB2, or SMB3) or degree of authentication and encryption.
-
CIFS protocol acceleration—These optimizations increase CIFS performance by reducing the number of round trips needed for running a CIFS command. These optimizations are performed automatically on SMB1 and SMB2 CIFS connections that either do not use CIFS packet authentication (“signing”), or where signing is used and the appliances have joined the Windows domain in a “security delegate” role.
-
CIFS compression—CIFS connections are compressed automatically whenever they meet the requirements for CIFS protocol acceleration. In addition, SMB3 connections are compressed when unsigned and unsealed.
On networks where CIFS signing is enabled, CIFS protocol acceleration and compression require that you either disable CIFS packet authentication (signing), or have your datacenter appliances join the Windows domain, and create a secure peer relationship between the datacenter appliances and your remote appliances and Citrix SD-WAN WANOP Plug-ins.
Table 1. CIFS acceleration features, by SMB protocol version and whether the appliance has joined the Windows domain.
| SMB Version | TCP Flow Control | Compression | Protocol Acceleration |
|---|---|---|---|
| Signing disabled | |||
| SMB 1.0 | Y | Y | Y |
| SMB 2.0 | Y | Y | Y |
| SMB 2.1 | Y | Y | N |
| SMB 3.0 | Y | Y | N |
| Signing enabled, Citrix SD-WAN WANOP has joined domain ** | |||
| SMB 1.0 | Y | Y | Y |
| SMB 2.0 | Y | Y | Y |
| SMB 2.1 | Y | Y | Y |
| SMB 3.0 | Y | Y | Y * |
| Signing enabled, Citrix SD-WAN WANOP has not joined domain | |||
| SMB 1.0 | Y | N | N |
| SMB 2.0 | Y | N | N |
| SMB 2.1 | Y | N | N |
| SMB 3.0 | Y | N | N |
* SMB 3.0 Support was added in release 7.4.2.
** Citrix SD-WAN WANOP does not support NTLMv2 authentication (default for Windows 7) up with SMB 1/ SMB 2/ SMB 3 and with NetApp server. Enabling Kerberos authentication allows acceleration.
Table 2. Which SMB protocol version is used, by client and server operating system.
| Client/Server OS | Windows 8, Windows 10, or Windows Server 2012 | Windows 7 or Windows Server 2008 R2 | Windows Vista or Windows Server 2008 | Earlier versions of Windows |
|---|---|---|---|---|
| Windows 8, Windows 10, or Windows Server 2012 | SMB 3.0 | SMB 2.1 | SMB 2.0 | SMB 1.0 |
| Windows 7 or Windows Server 2008 R2 | SMB 2.1 | SMB 2.1 | SMB 2.0 | SMB 1.0 |
| Windows Vista or Windows Server 2008 | SMB 2.0 | SMB 2.0 | SMB 2.0 | SMB 1.0 |
| Earlier versions of Windows | SMB 1.0 | SMB 1.0 | SMB 1.0 | SMB 1.0 |
Supported Versions of CIFS:
Not every CIFS implementation uses request patterns that are recognized by the appliance. These unsupported versions do not achieve acceleration in the full range of cases, as shown in the following table.
Table 3. Citrix SD-WAN WANOP Support for CIFS Servers and Clients.
| Product | Server | Client |
|---|---|---|
| Windows Server 2003-2012 | Yes* | Yes* |
| Windows XP, Vista, 7, 8, 2000 | Yes* | Yes* |
| NetApp | Yes** | N/A |
| Hitachi | Yes** | N/A |
| Windows NT | Yes | No |
| Windows ME and earlier | No | No |
| Others | See Note | See Note |
* SMB 3.0 support was introduced in release 7.4.2.
** Operation with SMB 3.0 has not been tested as of release 7.4.2.
Note: Most third-party CIFS implementations emulate one of the servers or clients listed above. To the extent that the emulation is successful, traffic is accelerated, or not, as shown in the above table. If the emulation behaves differently from what the CIFS accelerator expects, CIFS acceleration is terminated for that connection.
The behavior of CIFS acceleration with a given CIFS implementation cannot be known for certain until it has been tested.
The modes of CIFS acceleration are:
-
Large file reads and writes
-
Small file reads and writes
-
Directory browsing.
Large file reads and writes—These SMB1 optimizations are for file transfers of at least 640 KB. Safe read-ahead and write-behind techniques are used to stream the data without pauses for every transfer (a transfer is 64 KB or less).
These optimizations are enabled only if the transfer has a BATCH or EXCLUSIVE lock and is “simple.” File copies are always simple. Files opened through applications might or might not be, depending on how they are handled within the application.
Speedup ratios of 10x are readily obtainable with CIFS acceleration, provided that your link and disks are fast enough to accommodate ten times your current transfer speeds. 50x speedup can be obtained if necessary, but is not normally enabled, because of memory consumption. Contact your Citrix representative if 10x is not sufficient.
Small file reads and writes—Small-file enhancements center more around metadata (directory) optimizations than around data streaming. Native CIFS does not combine metadata requests in an efficient way. CIFS acceleration does. As with large-file acceleration, these optimizations are not performed unless they are safe (for example, they are not performed if the CIFS client was not granted an exclusive lock on the directory.) When the SMB2 protocol is used, file metadata is cached locally for even greater improvements.
Directory browsing—Standard CIFS clients perform directory browsing in an extremely inefficient way, requiring an enormous number of round trips to open a remote folder. CIFS acceleration reduces the number of round trips to 2 or 3. When the SMB2 protocol is used, directory data is cached locally for even greater improvements.
CIFS protocol acceleration
CIFS acceleration is supported on all models. CIFS is a TCP based protocol and benefits from flow control. However, CIFS is implemented in a way that is highly inefficient on long-haul networks, requiring an excessive number of round trips to complete an operation. Because the protocol is very sensitive to link latency, full acceleration must be protocol-aware.
CIFS acceleration reduces the number of round-trips through a variety of techniques. The pattern of requests from the client is analyzed and its next action is predicted. In many cases, it is safe to act on the prediction even if it is wrong, and these safe operations are the basis of many optimizations.
For example, SMB1 clients issue sequential file reads in a non-overlapping fashion, waiting for each 64KB read to complete before issuing the next one. By implementing read-ahead, the appliance can safely deliver up to 10x acceleration by fetching the anticipated data in advance.
Additional techniques accelerate directory browsing and small-file operations. Acceleration is applied not only to CIFS operations, but also to the related RPC operations.
Prerequisites
CIFS acceleration is supported on all models. CIFS is a TCP based protocol and benefits from flow control. However, CIFS is implemented in a way that is highly inefficient on long-haul networks, requiring an excessive number of round trips to complete an operation. Because the protocol is very sensitive to link latency, full acceleration must be protocol-aware.
CIFS acceleration reduces the number of round-trips through a variety of techniques. The pattern of requests from the client is analyzed and its next action is predicted. In many cases, it is safe to act on the prediction even if it is wrong, and these safe operations are the basis of many optimizations.
For example, SMB1 clients issue sequential file reads in a non-overlapping fashion, waiting for each 64KB read to complete before issuing the next one. By implementing read-ahead, the appliance can safely deliver up to 10x acceleration by fetching the anticipated data in advance.
Additional techniques accelerate directory browsing and small-file operations. Acceleration is applied not only to CIFS operations, but also to the related RPC operations.
If your network uses CIFS signing, the appliance must be a trusted member of the domain. To make the appliance a trusted member of the domain, see Adding a Citrix SD-WAN WANOP Appliance to the Windows Security Infrastructure.
Configure CIFS protocol acceleration
CIFS acceleration is enabled by default for connections that do not use CIFS signing. If your network uses signing, it can either be disabled or the server-side appliances can join the Windows domain.
Disable CIFS signing
Depending on their security settings, Windows servers or domain servers might need to have their security settings adjusted.
Figure 1. Windows Server Security Options, Windows Server 2003 and Windows Server 2008.
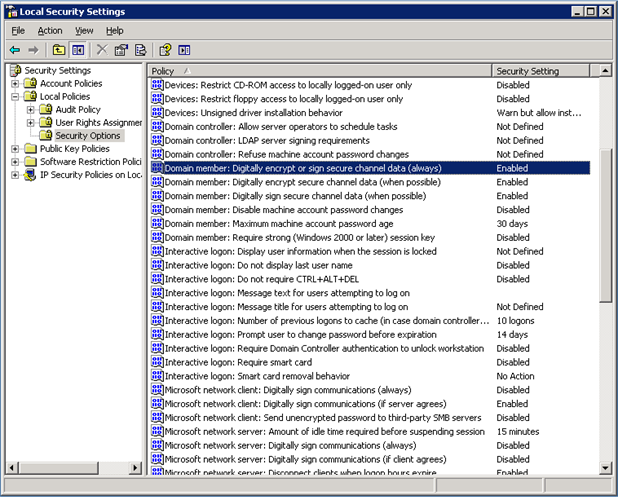
Windows file servers have two security modes: “sealing” and “signing.”
Sealing encrypts the data stream and prevents CIFS protocol acceleration altogether.
Signing adds authentication data to every data packet, without encrypting the data stream. This prevents acceleration unless you have implemented the procedures described in Adding a Citrix SD-WAN WANOP Appliance to the Windows Security Infrastructure. When this requirement is met, signing is accelerated automatically. Otherwise, signing must be disabled (if it is not disabled already) for protocol acceleration to take place.
By default, Windows file servers offer signing but do not require it, except for domain servers, which require it by default.
To achieve CIFS acceleration with systems that currently require signing, you must change the system security settings to disable this requirement. You can do so in the local security settings on the file server, or in group policies. The following examples, for Windows Server 2003 and Windows Server 2008, show the local settings. The group-policy changes are, of course, almost identical.
Citrix SD-WAN WANOP
To change the server’s setting to allow CIFS acceleration
-
Navigate to the system’s Local Security Settings page.
-
Set Domain member: Digitally encrypt or sign secure channel data (always) to Disabled.
-
Set Microsoft network client: Digitally sign communications (always) to Disabled.
-
Set Microsoft network server: Digitally sign communications (always) to Disabled.
Interpret CIFS statistics
The Monitoring: Filesystem (CIFS/SMB) page shows a list of accelerated CIFS connections. These connections are divided into “optimized” and “non-optimized” connections. Because all these connections are accelerated (with flow control and compression), “optimized” connections have CIFS optimizations in addition to flow control and compression, while “non-optimized” connections have flow control and compression only.
CIFS management summary
-
CIFS acceleration provides significant improvement even at relatively short link distances.
-
CIFS acceleration begins when a file system is first accessed by the client. If acceleration is enabled with the file server and client already up and running, no acceleration occurs for many minutes, until the preexisting CIFS connections are fully closed. CIFS connections are very persistent and last a long time before closing themselves, even when idle. This behavior is annoying during test, but has little importance in normal deployment.
-
Dismounting and remounting a file system in Windows does not close the CIFS connections, because Windows does not really dismount the file system fully. Rebooting the client or server works. For a less invasive measure, use the NET USE devicename /DELETE command from the Windows command line to fully dismount the volume. In Linux, smbmount and umount fully dismount the volume.
-
Disabling and then reenabling CIFS read and write optimizations on the appliance raises similar issues. Existing connections do not become accelerated when CIFS is enabled, and the number of “protocol errors detected” on the Monitoring: Filesystem (CIFS/SMB) page increases briefly.
-
CIFS statistics can be confusing, because only the appliance farthest from the fileserver reports CIFS acceleration with full statistics. The other appliance sees it as ordinary acceleration.
-
CIFS acceleration is not supported in proxy mode.
-
If CIFS acceleration does not take place with a Windows server, check the server’s security settings.