-
Configuring the VPN User Experience
-
How to Configure Full VPN Setup on a Citrix Gateway Appliance
-
Integrating the Citrix Gateway plug-in with Citrix Receiver™
-
AlwaysOn VPN before Windows logon (Formally AlwaysOn service)
-
Maintaining and Monitoring the System
-
Deploying with Citrix Endpoint Management, Citrix Virtual Apps, and Citrix Virtual Desktops™
-
Accessing Citrix Virtual Apps and Desktops™ Resources with the Web Interface
-
Integrating Citrix Gateway with Citrix Virtual Apps and Desktops
-
Configuring Additional Web Interface Settings on Citrix Gateway
-
Configuring Access to Applications and Virtual Desktops in the Web Interface
-
-
Integrate Citrix Gateway with Citrix Virtual Apps and Desktops
-
Configuring Settings for Your Citrix Endpoint Management Environment
-
Configuring Load Balancing Servers for Citrix Endpoint Management
-
Configuring Load Balancing Servers for Microsoft Exchange with Email Security Filtering
-
Configuring Citrix Endpoint Management NetScaler® Connector (XNC) ActiveSync Filtering
-
Allowing Access from Mobile Devices with Citrix Mobile Productivity Apps
-
Configuring Domain and Security Token Authentication for Citrix Endpoint Management
-
Configuring Client Certificate or Client Certificate and Domain Authentication
-
-
Citrix Gateway Enabled PCoIP Proxy Support for VMware Horizon View
-
Proxy Auto Configuration for Outbound Proxy support for Citrix Gateway
-
Integrate Citrix Gateway with Citrix Virtual Apps and Desktops
This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Configuring Settings for Your Citrix Endpoint Management™ Environment
The Citrix® ADC for Citrix Endpoint Management wizard guides you through the configuration of Citrix ADC features for your Citrix Endpoint Management deployment. You can use the wizard to:
-
Set up a Micro VPN. In this scenario, remote users can access apps and desktops in the internal network.
-
For Citrix Endpoint Management MAM-only mode, you must use Citrix Gateway for authentication.
-
For MDM deployments, Citrix recommends Citrix Gateway for mobile device VPN.
-
For ENT deployments, if a user opts out of MDM enrollment, the device operates in the legacy MAM mode and enrolls using the Citrix Gateway FQDN.
-
- Configure certificate-based authentication. The default configuration for Citrix Endpoint Management is user name and password authentication. To add another layer of security for enrollment and access to the Citrix Endpoint Management environment, consider using certificate-based authentication.
- Load balance Citrix Endpoint Management servers. Citrix ADC load balancing is required for all Citrix Endpoint Management device modes if you have multiple Citrix Endpoint Management servers or if the Citrix Endpoint Management is inside your DMZ or internal network (and therefore traffic flows from devices to Citrix ADC to Citrix Endpoint Management). In this scenario, the Citrix ADC appliance resides in the DMZ between the user device and the Citrix Endpoint Management servers to load balance encrypted sent data from mobile devices to the Citrix Endpoint Management servers.
- Load balance Microsoft Exchange servers with email filtering. In this scenario, the Citrix ADC appliance is between the user device and the Citrix Endpoint Management Citrix ADC Connector (XNC), and between the user device and the Microsoft Exchange CAS servers. All requests from user devices go to the Citrix Gateway appliance, which then communicates with the XNC to retrieve information about the device. Depending on the response from the XNC, the Citrix ADC appliance either forwards the request from a whitelisted device to the server in the internal network, or drops the connection from a blacklisted device.
-
Load balance ShareFile StorageZones Connectors based on the type of content requested. This scenario prompts you for basic information about your StorageZones Controller environment and then generates a configuration that does the following:
- Load balances traffic across storage zones controllers.
- Provides user authentication for StorageZones Connectors.
- Validates URI signatures for ShareFile uploads and downloads.
- Terminates SSL connections at the Citrix ADC appliance.
For more information about configuring ShareFile, see Configure Citrix ADC for storage zones controller.
Important
Before you use the Citrix Endpoint Management wizard, be sure to refer to these Citrix Endpoint Management Deployment articles for design and deployment information and recommendations:
Citrix Endpoint Management Integration
Integrating with Citrix Gateway and Citrix ADC
SSO and Proxy Considerations for MDX Apps
You can use the Citrix ADC for Citrix Endpoint Management wizard only once. If you want multiple Citrix Endpoint Management instances, such as for test, development, and production environments, you must configure Citrix ADC for the additional environments manually. The following support articles list the commands run by the wizard and provide instructions for running them to create a Citrix ADC instance:
Commands Generated by Citrix Endpoint Management Wizard on Citrix ADC - SSL Bridge
Commands Generated by Citrix Endpoint Management Wizard on Citrix ADC - SSL Offload
License Requirements for Citrix ADC Features
You must install licenses to enable the following Citrix ADC features:
- Citrix Endpoint Management MDM load balancing requires a Citrix ADC standard license.
- ShareFile load balancing with StorageZones requires a Citrix ADC standard license.
- Exchange load balancing requires a Citrix ADC license or an Enterprise license with the addition of an Integrated Caching license.
Citrix ADC for Citrix Endpoint Management Wizard
This section provides an example of using the Citrix ADC for Citrix Endpoint Management wizard to:
- Set up micro VPN access for remote user connections to Citrix Endpoint Management-managed resources in your internal network
- Configure certificate-based authentication. For information about obtaining and installing a public SSL certificate, see Installing and Managing Certificates.
- Configure load balancing for Citrix Endpoint Management servers.
To use the wizard:
-
In the configuration utility, click the Configuration tab and then click Citrix Endpoint Management.
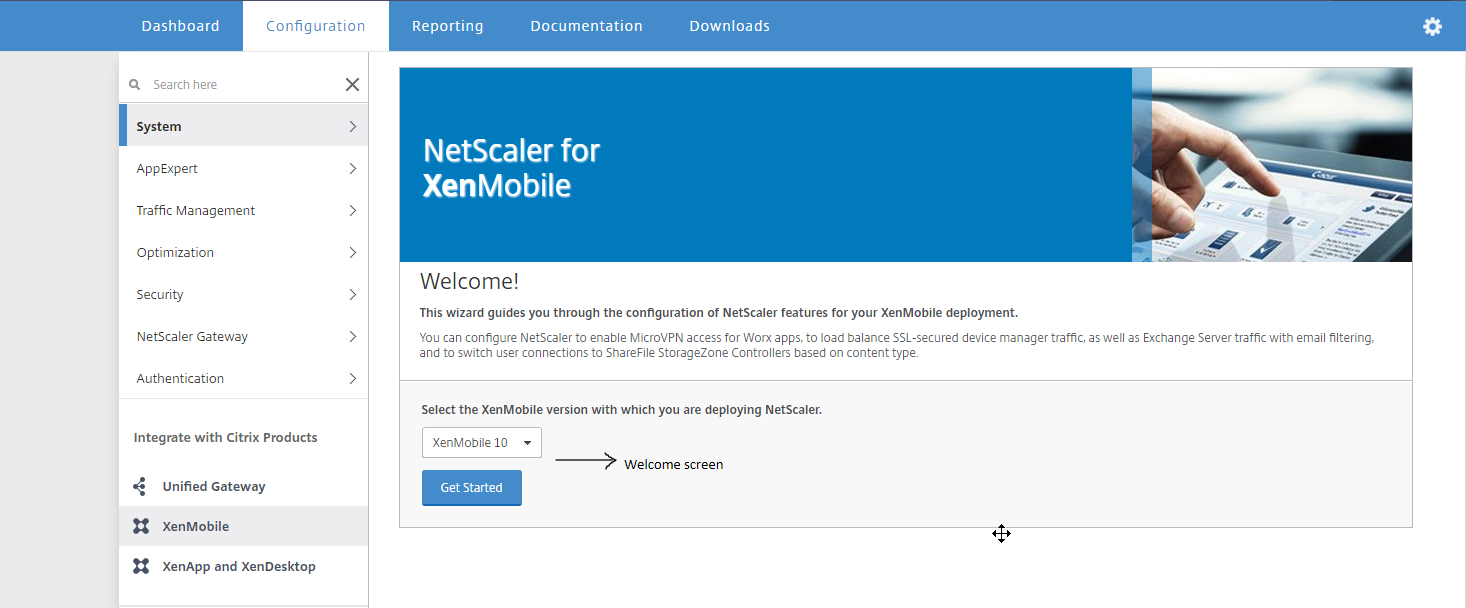
- Select your Citrix Endpoint Management version and then click Get Started.
-
Select the check boxes for the features you want to configure. Keep in mind that you can use this wizard only once, so you need to perform subsequent configuration manually. These instructions assume that you select the following settings: Access through Citrix Gateway (for Citrix Endpoint Management running in ENT or MAM modes) Load Balance Citrix Endpoint Management Servers

-
On the Citrix Gateway Settings page, enter values for the external facing Citrix Gateway IP Address, Port, and Virtual Server Name.

-
On the Server Certificate for Citrix Gateway page, from the Certificate File drop-down menu, choose the certificate file from Local or Appliance. If your certificate is on a local machine:

If your certificate is on the appliance:

-
In the Authentication Settings page, in the Primary authentication method field, select Client Certificate.
This will automatically select Use existing certificate policy and Cert Auth in the next two fields. The following steps assume that you already have a certificate policy.
If you must create a certificate policy, click Create certificate policy and complete the settings. On the Citrix Endpoint Management Certificate screen, choose an existing server certificate or install a new certificate. If you’re running multiple Citrix Endpoint Management servers, you add a certificate for each one. For Server Logon Name Attribute, specify userPrincipalName or samAccountName, per your requirements.

-
a. Select Click here to change the CA certificate and then in the Browse list, navigate to the CA certificate you want.

-
b. With the client certificate as your primary authentication type, you have the option of configuring LDPA (or RADIUS) as the secondary authentication type.
To use client certificate authentication only, leave Second authentication method as None and then click Continue.
To use client certificate + domain (LDAP) authentication, change Second authentication method to LDAP and configure the authentication server settings.
-
c. On the Device certificate screen, if the certificate is not already installed, you must export this certificate from the Citrix Endpoint Management console: From the console, click the gear icon in the upper-right corner to open the Settings screen.
-
d. Click Certificate and then choose the CA certificate from the list.
-
e. Click Export.
-
f. Return to the Citrix ADC wizard and select the certificate you exported (downloaded) to install it.
-
g. Click Continue.
The Citrix Endpoint Management IP addresses that you’ve configured appear.
-
-
Configure the Citrix Endpoint Management App Management Settings.
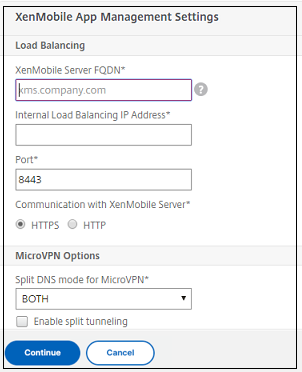
- Enter the Citrix Endpoint Management FQDN. This is the load balancing FQDN for MAM.
- Enter a MAM-only Internal Load Balancing IP Address for the virtual server that load balances Citrix Endpoint Management servers. Citrix Gateway communicates with the Citrix Endpoint Management through this MAM load balancing virtual IP.
- This is an SSL offload deployment, so select HTTP in Communication with Citrix Endpoint Management Server.
- The Split DNS mode for MicroVPN field automatically sets to BOTH.
If your deployment requires split tunneling, select Enable split tunneling. You must configure Intranet Application Binding, next, if you enable split tunneling.
By default, Secure Web access is tunneled to the internal network, which means that Secure Web uses a per-application VPN tunnel back to the internal network for all network access and the Citrix ADC appliance uses split tunnel settings.
-
To configure interception rules for user connections on Citrix Gateway, you must configure Intranet Application Binding. Click + to add a binding.
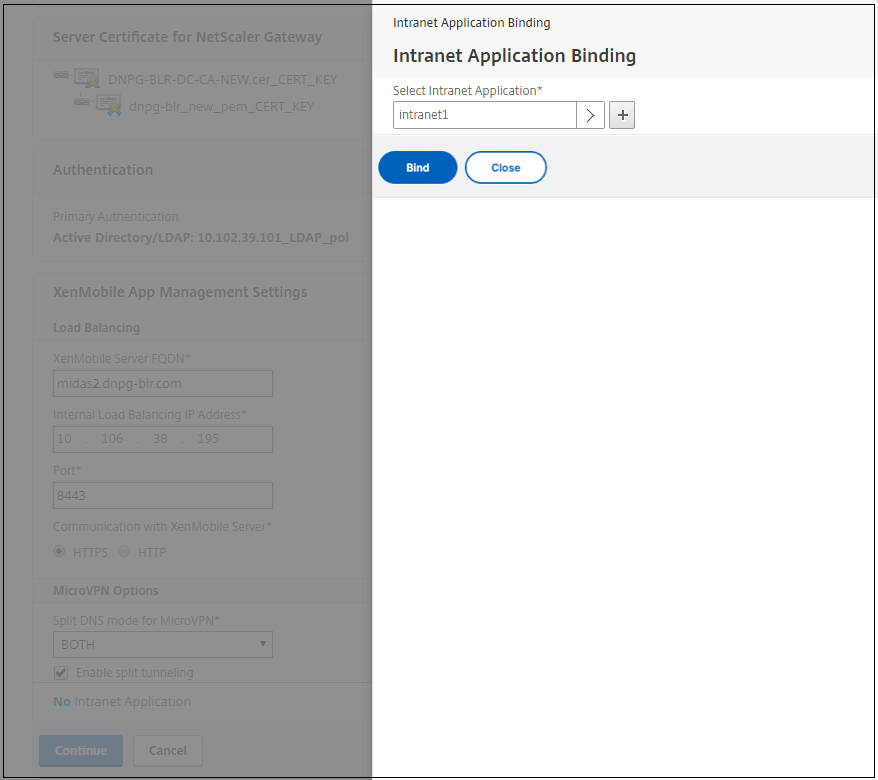
-
Complete the parameters for allowing network access and then click Create.
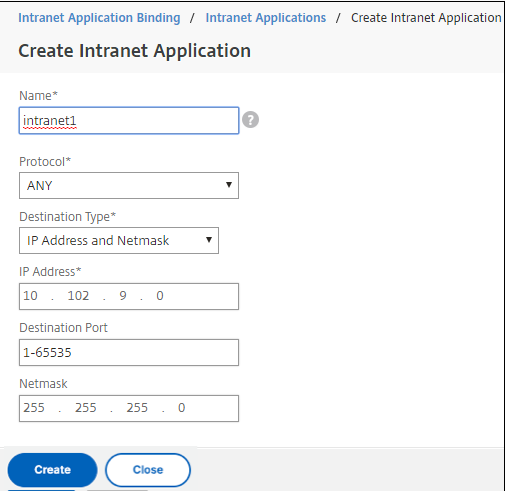
-
Add the Citrix Endpoint Management certificate. This will be used for the MAM load balancing virtual server.
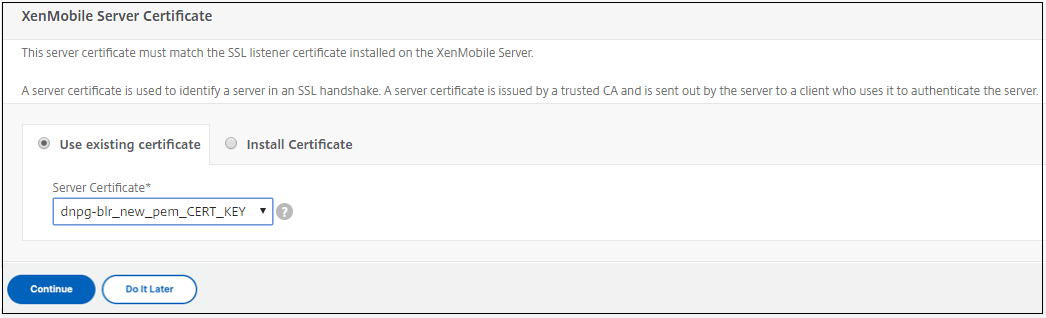
-
Under Citrix Endpoint Management Servers, click Add Server to add the Citrix Endpoint Management IP Address to bind to the load balancing virtual IP.
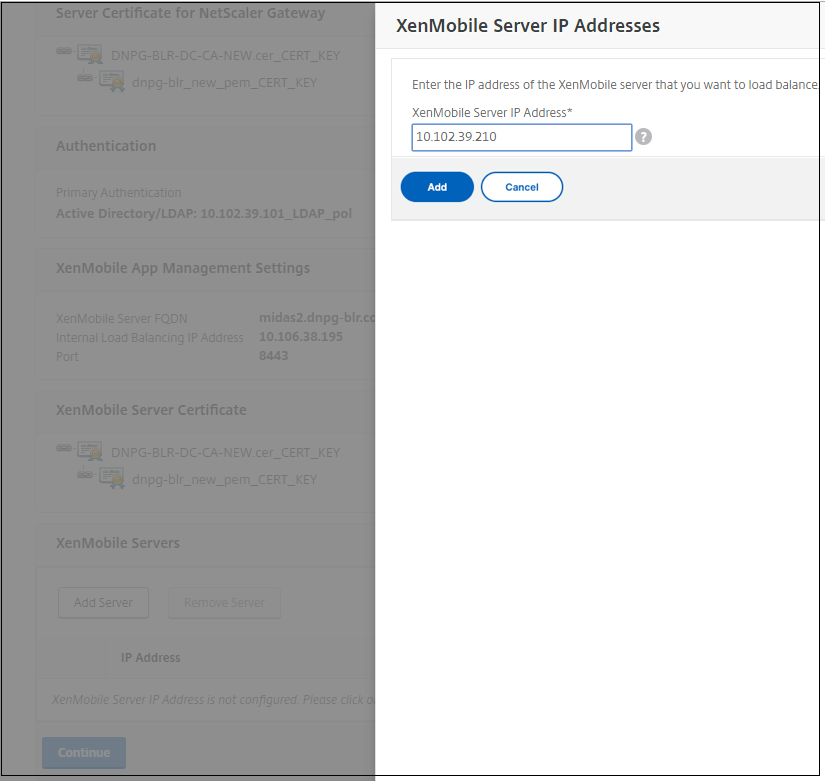
-
On the Citrix ADC dashboard, confirm that Citrix Gateway and Citrix Endpoint Management load balancing are configured as follows.
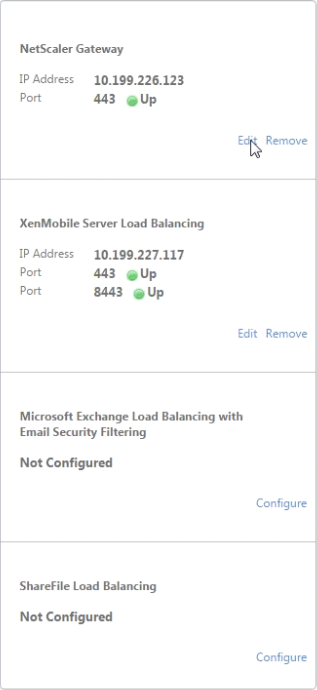
If you will use sAMAccount attributes in the user certificates as an alternative to User Principal Name (UPN), configure the certificate profile as described in Manually Configuring Citrix Gateway for Client Certificate Authentication.
Share
Share
This Preview product documentation is Cloud Software Group Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Cloud Software Group Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Cloud Software Group product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.