Palo Alto Network Integration
Palo Alto networks deliver cloud-based security infrastructure for protecting remote networks. It provides security by allowing organizations to set up regional, cloud-based firewalls that protect the SD-WAN fabric.
Prisma Access service for remote networks allows you to onboard remote network locations and deliver security for users. It removes the complexity in configuring and managing devices at every remote location. The service provides an efficient way to easily add new remote network locations and minimize the operational challenges with ensuring that users at these locations are always connected and secure, and it allows you to manage policy centrally from Panorama for consistent and streamlined security for your remote network locations.
To connect your remote network locations to the Prisma Access service, you can use the Palo Alto Networks next-generation firewall or a third-party, IPSec-compliant device including SD-WAN, which can establish an IPsec tunnel to the service.
-
Plan the Prisma Access Service for Remote Networks
-
Configure the Prisma Access Service for Remote Networks
-
Onboard Remote Networks with Configuration Import
The Citrix SD-WAN™ solution already provided the ability to break out Internet traffic from the branch. This is critical to delivering a more reliable, low-latency user experience, while avoiding the introduction of an expensive security stack at each branch. Citrix SD-WAN and Palo Alto Networks now offer distributed enterprises a more reliable and secure way to connect users in branches to applications in the cloud.
Citrix SD-WAN appliances can connect to the Palo Alto cloud service (Prisma Access Service) network through IPsec tunnels from SD-WAN appliances locations with minimal configuration. You can configure Palo Alto network in Citrix SD-WAN Center.
Before you begin to configure the Prisma Access Service for Remote Networks, make sure you have the following configuration ready to ensure that you are able to successfully enable the service and enforce policy for users in your remote network locations:
- Service Connection— If your remote network locations require access to infrastructure in your corporate headquarters to authenticate users or to enable access to critical network assets, you must set up Access to Your Corporate Network so that headquarters and the remote network locations are connected.
If the remote network location is autonomous and does not need to access to infrastructure at other locations, you do not need to set up the service connection (unless your mobile users need access).
-
Template— The Prisma Access service automatically creates a template stack (Remote_Network_Template_Stack) and a top-level template (Remote_Network_Template) for the Prisma Access service for remote networks. To Configure the Prisma Access Service for Remote Networks, you configure the top-level template from scratch or leverage your existing configuration, if you are already running a Palo Alto networks firewall on premise.
The template requires the settings to establish the IPsec tunnel and Internet Key Exchange (IKE) configuration for protocol negotiation between your remote network location and the Prisma Access service for remote networks, zones that you can reference in security policy, and a log forwarding profile so that you can forward logs from the Prisma Access service for remote networks to the Logging Service.
-
Parent Device Group— The Prisma Access service for remote networks requires you to specify a parent device group that includes your security policy, security profiles, and other policy objects (such as application groups and objects, and address groups), as well as authentication policy so that the Prisma Access service for remote networks can consistently enforce policy for traffic that is routed through the IPsec tunnel to the Prisma Access service for remote networks. You need to either define policy rules and objects on Panorama or use an existing device group to secure users in the remote network location.
Note:
If you use an existing device group that references zones, make sure to add the corresponding template that defines the zones to the Remote_Network_Template_Stack.
This allows you to complete the zone mapping when you configure the Prisma Access Service for Remote Networks.
-
IP Subnets— In order for the Prisma Access service to route traffic to your remote networks, you must provide routing information for the subnetworks that you want to secure using the Prisma Access service. You can either define a static route to each subnetwork at the remote network location, or configure BGP between your service connection locations and the Prisma Access service, or use a combination of both methods.
If you configure both static routes and enable BGP, the static routes take precedence. While it might be convenient to use static routes if you have just a few subnetworks at your remote network locations, in a large deployment with many remote networks with overlapping subnets, BGP will enable you to scale more easily.
Palo Alto network in SD-WAN Center
Ensure that the following prerequisites are met:
-
Obtain panorama IP address from PRISMA ACCESS service.
-
Obtain user name and password user in the PRISMA ACCESS service.
-
Configure IPsec tunnels in the SD-WAN appliance GUI.
-
Make sure the site is not onboarded to a Region, which already has a different site configured with ike/ipsec profiles other than Citrix-IKE-Crypto-Default/Citrix-IPSec-Crypto-Default.
-
Make sure that Prisma Access configuration is not changed manually when config is updated by SD-WAN Center.
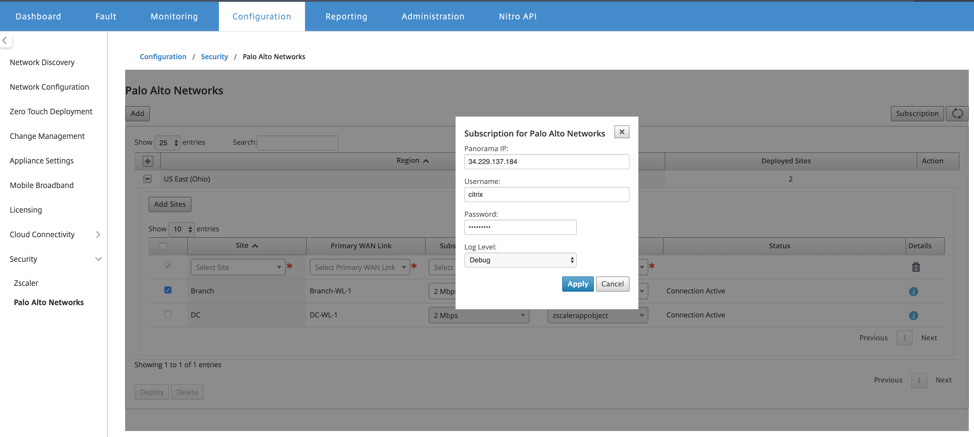
In the Citrix SD-WAN Center GUI, provide Palo Alto subscription information.
-
Configure panorama IP address. You can obtain this IP address from Palo Alto (PRISMA ACCESS service).
-
Configure user name and password used in the PRISMA ACCESS service.
Add and deploy sites
-
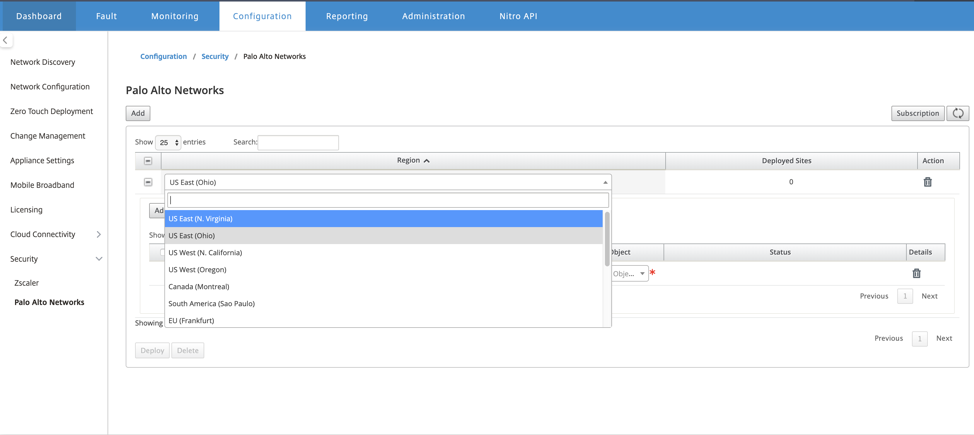
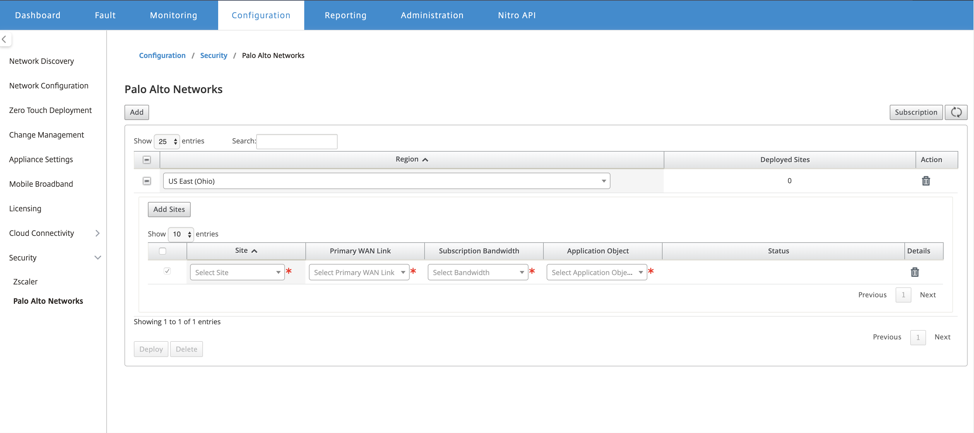
To deploy the sites, choose the PRISMA ACCESS network region and the SD-WAN site to be configured for the Prisma Access region, and then select the site WAN link, bandwidth, and application object for traffic selection.
Note:
Traffic flow is impacted if the selected bandwidth exceeds available bandwidth range.
You can choose to redirect all internet bound traffic to the PRISMA ACCESS service by selecting the All traffic option under the Application object selection.
-
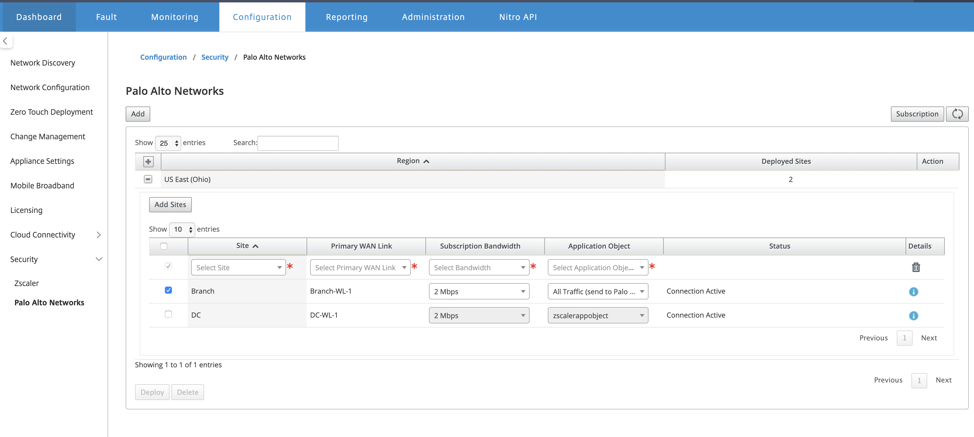
You can continue to add more SD-WAN branch sites as required.
-
Click Deploy. The change management process is initiated. Click Yes to continue.
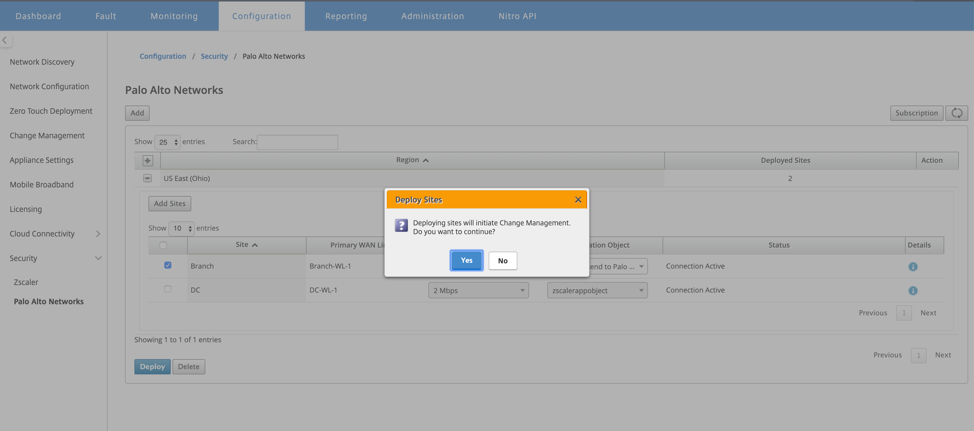
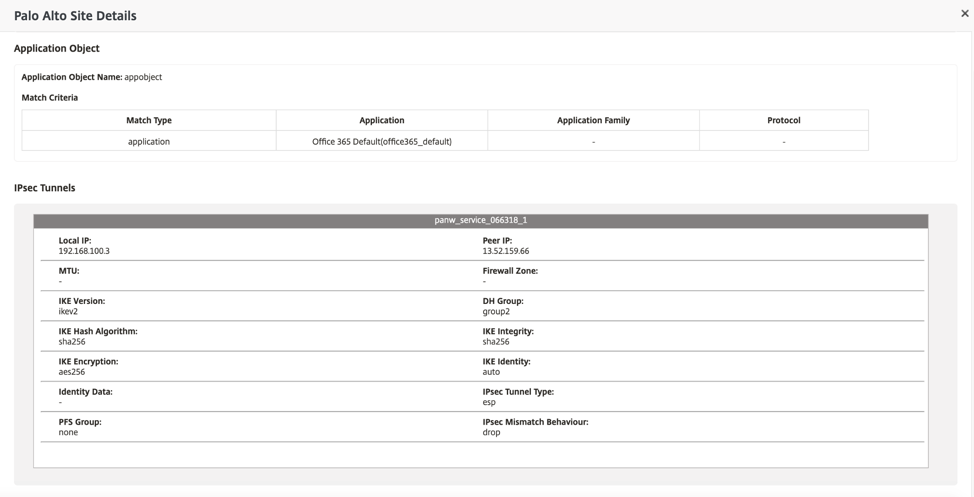
After deployment, the IPsec Tunnel configuration used to establish the tunnels is as follows.
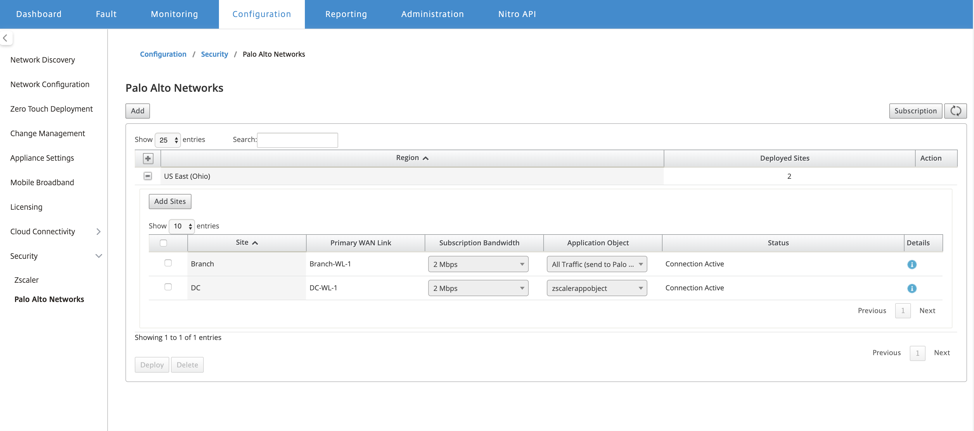
The landing page shows the list of all sites configured and grouped under different SD-WAN regions.
Verify end-to-end traffic connection:
-
From LAN subnet of branch, access internet resources.
-
Verify that traffic goes through Citrix SD-WAN IPsec tunnel to the Palo Alto Prisma Access.
-
Verify that Palo Alto security policy is applied on traffic under the Monitoring tab.
-
Verify response from internet to host in a branch comes through.