-
Configuring the VPN User Experience
-
How to Configure Full VPN Setup on a Citrix Gateway Appliance
-
Integrating the Citrix Gateway plug-in with Citrix Receiver™
-
AlwaysOn VPN before Windows logon (Formally AlwaysOn service)
-
Maintaining and Monitoring the System
-
Deploying with Citrix Endpoint Management, Citrix Virtual Apps, and Citrix Virtual Desktops™
-
Accessing Citrix Virtual Apps and Desktops™ Resources with the Web Interface
-
Integrating Citrix Gateway with Citrix Virtual Apps and Desktops
-
Configuring Additional Web Interface Settings on Citrix Gateway
-
Configuring Access to Applications and Virtual Desktops in the Web Interface
-
-
Integrate Citrix Gateway with Citrix Virtual Apps and Desktops
-
Configuring Settings for Your Citrix Endpoint Management Environment
-
Configuring Load Balancing Servers for Citrix Endpoint Management
-
Configuring Load Balancing Servers for Microsoft Exchange with Email Security Filtering
-
Configuring Citrix Endpoint Management NetScaler® Connector (XNC) ActiveSync Filtering
-
Allowing Access from Mobile Devices with Citrix Mobile Productivity Apps
-
Configuring Domain and Security Token Authentication for Citrix Endpoint Management
-
Configuring Client Certificate or Client Certificate and Domain Authentication
-
-
Citrix Gateway Enabled PCoIP Proxy Support for VMware Horizon View
-
Proxy Auto Configuration for Outbound Proxy support for Citrix Gateway
-
Integrate Citrix Gateway with Citrix Virtual Apps and Desktops
-
Native OTP Support for Authentication
This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Native OTP support for authentication
Citrix® Gateway supports one-time passwords (OTPs) without having to use a third-party server. One-time password is a highly secure option for authenticating to secure servers as the number or passcode generated is random. Previously, specialized firms, such as RSA with specific devices that generate random numbers offered the OTPs. This system must be in constant communication with the client to generate a number expected by the server.
In addition to reducing capital and operating expenses, this feature enhances the administrator’s control by keeping the entire configuration on the Citrix ADC appliance.
Note: Because third-party servers are no longer needed, the Citrix ADC administrator has to configure an interface to manage and validate user devices.
User must be registered with a Citrix Gateway virtual server to use the OTP solution. Registration is required only once per unique device, and can be restricted to certain environments. Configuring and validation of a registered user is similar to configuring an extra authentication policy.
Advantages of having Native OTP support
- Reduces operating cost by eliminating the need to have an extra infrastructure on an authenticating server in addition to the Active Directory.
- Consolidates configuration only to Citrix ADC appliance thus offering great control to administrators.
- Eliminates the client’s dependence on an extra authentication server for generating a number expected by clients.
Native OTP workflow
The native OTP solution is a two-fold process and the workflow is classified as the following:
- Device registration
- End user login
Important: You can skip the registration process if you are using third-party solutions or managing other devices apart from the Citrix ADC appliance. The final string that you add must be in the Citrix ADC specified format.
The following figure depicts the device registration flow to register a new device to receive OTP.
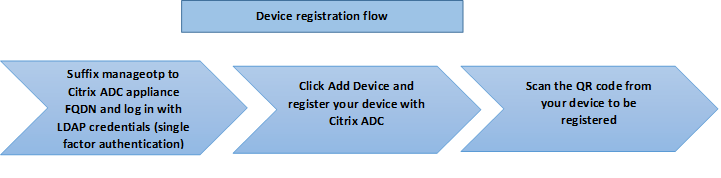
Note: The device registration can be done using any number of factors. The single factor (as specified in the previous figure) is used as an example to explain the device registration process.
The following figure depicts the verification of OTP through the registered device.
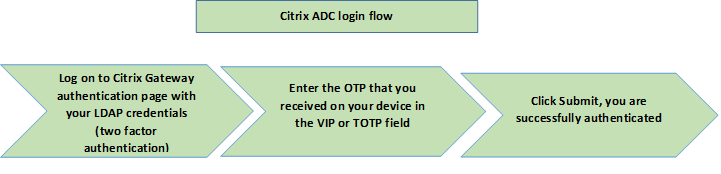
Prerequisites
To use the native OTP feature, make sure the following prerequisites are met.
- Citrix ADC feature release version is 12.0 build 51.24 and later.
- Advanced or Premium edition license is installed on Citrix Gateway.
- Citrix Gateway is configured with management IP and the management console is accessible both using a browser and command line.
- Citrix ADC is configured with authentication, authorization, and auditing virtual server to authenticate users.
- Citrix ADC appliance is configured with Unified Gateway and the authentication, authorization, and auditing profile is assigned to the Gateway virtual server.
- Native OTP solution is restricted to nFactor authentication flow. Advanced policies are required to configure the solution. For more details, see article CTX222713.
Also ensure the following for Active Directory:
- A minimum attribute length of 256 characters.
- Attribute type must be ‘DirectoryString’ such as UserParameters. These attributes can hold string values.
- Attribute string type must be Unicode, if device name is in non-English characters.
- Citrix ADC LDAP administrator must have write access to the selected AD attribute.
- Citrix ADC appliance and client machine must be synced to a common Network Time Server.
Configure Native OTP using the GUI
The native OTP registration is not just a single factor authentication. The following sections help you to configure the single and second factor authentication.
Create Login Schema for first factor
- Navigate to Security AAA > Application Traffic > Login Schema.
- Go to Profiles and click Add.
- On the Create Authentication Login Schema page, enter lschema_single_auth_manage_otp under the Name field and click Edit next to noschema.
- Click the LoginSchema folder.
- Scroll down to select SingleAuth.xml and click Select.
- Click Create.
- Click Policies and Click Add.
-
On the Create Authentication Login Schema Policy screen, enter the following values.
Name: lpol_single_auth_manage_otp_by_url Profile: select lpol_single_auth_manage_otp_by_url from the list. Rule: HTTP.REQ.COOKIE.VALUE(“NSC_TASS”).EQ(“
manageotp”)
Configure authentication, authorization, and auditing virtual server
- Navigate to Security > AAA – Application Traffic > Authentication Virtual Servers. Click to edit the existing virtual server.
- Click the + icon next to Login Schemas under Advanced Settings in the right pane.
- Select No Login Schema.
- Click the arrow and select the lpol_single_auth_manage_otp_by_url Policy.
- Select the lpol_single_auth_manage_otp_by_url policy and Click Select.
- Click Bind.
- Scroll up and select 1 Authentication Policy under Advanced Authentication Policy.
- Right-click the nFactor Policy and select Edit Binding.
- Click the + icon present under Select Next Factor, create a Next Factor, and click Bind.
-
On the Create Authentication
PolicyLabelscreen, enter the following, and click Continue:Name: manage_otp_flow_label
Login Schema: Lschema_Int
-
On the Authentication PolicyLabel screen, click the + icon to create a Policy.
-
On the Create Authentication Policy screen, enter the following:
Name: auth_pol_ldap_otp_action
- Select the Action type using the Action Type list.
- In the Action field, click the + icon to create an Action.
-
In the Create Authentication LDAP server page, select Server IP radio button, deselect the check box next to Authentication, enter the following values, and select Test Connection.
Name: ldap_otp_action
IP Address: 192.168.10.11
Base DN: DC=training, DC=lab
Administrator: Administrator@training.lab
Password:
xxxxx - Scroll down to the Other Settings section. Use the drop-down menu to select the following options. Server Logon Name Attribute as New and type userprincipalname.
- Use the drop-down menu to select SSO Name Attribute as New and type userprincipalname.
- Enter “UserParameters” in the OTP Secret field and click More.
-
Enter the following Attributes.
Attribute 1 = mail Attribute 2 = objectGUID Attribute 3 = immutableID
- Click OK.
- On the Create Authentication Policy page, set the Expression to true and click Create.
- On the Create Authentication Policylabel page, click Bind, and click Done.
- On the Policy Binding page, click Bind.
- On the Authentication policy page, click Close and click Done.
Note
The authentication virtual server must be bound to the RFWebUI portal theme. Bind a server certificate to the server. The server IP ‘1.2.3.5’ must have a corresponding FQDN that is, otpauth.server.com, for later use.
Create login schema for second factor OTP
- Navigate to Security > AAA-Application Traffic > Virtual Servers. Select the virtual server to be edited.
- Scroll down and select 1 Login Schema.
- Click Add Binding.
- Under the Policy Binding section, click the + icon to add a policy.
- On the Create Authentication Login Schema Policy page, enter Name as OTP, and click the + icon to create a profile.
- On the Create Authentication Login Schema page, enter Name as OTP, and click the icon next to noschema.
- Click the LoginSchema folder, select DualAuthManageOTP.xml, and then click Select.
- Click Create.
- In the Rule section, enter True. Click Create.
- Click Bind.
- Notice the two factors of authentication. Click Close and click Done.
Configure content switching policy for manage OTP
The following configurations are required if you are using Unified Gateway.
-
Navigate to Traffic Management > Content Switching > Policies. Select the content switching policy, right click, and select Edit.
-
Edit the expression to evaluate the following OR statement and click OK:
| is_vpn_url |
Configure Native OTP using the CLI
You must have the following information to configure the OTP device management page:
- IP assigned to authentication virtual server
- FQDN corresponding to the assigned IP
- Server certificate for authentication virtual server
Note: Native OTP is a web-based solution only.
To configure the OTP device registration and management page
Create authentication virtual server
add authentication vserver authvs SSL 1.2.3.5 443
bind authentication vserver authvs -portaltheme RFWebUI
bind ssl vserver authvs -certkeyname otpauthcert
<!--NeedCopy-->
Note: The authentication virtual server must be bound to the RFWebUI portal theme. Bind a server certificate to the server. The server IP ‘1.2.3.5’ must have a corresponding FQDN that is, otpauth.server.com, for later use.
To create LDAP logon action
add authentication ldapAction <LDAP ACTION NAME> -serverIP <SERVER IP> - serverPort <SERVER PORT> -ldapBase <BASE> -ldapBindDn <AD USER> -ldapBindDnPassword <PASSWO> -ldapLoginName <USER FORMAT>
<!--NeedCopy-->
Example:
add authentication ldapAction ldap_logon_action -serverIP 1.2.3.4 -serverPort 636 -ldapBase "OU=Users,DC=server,DC=com" -ldapBindDn administrator@ctxnsdev.com -ldapBindDnPassword PASSWORD -ldapLoginName userprincipalname
<!--NeedCopy-->
To add authentication policy for LDAP Logon
add authentication Policy auth_pol_ldap_logon -rule true -action ldap_logon_action
<!--NeedCopy-->
To present UI via LoginSchema
Show user name field and password field to users upon logon
add authentication loginSchema lschema_single_auth_manage_otp -authenticationSchema "/nsconfig/loginschema/LoginSchema/SingleAuthManageOTP.xml"
<!--NeedCopy-->
Display device registration and management page
Citrix recommends two ways of displaying the device registration and management screen: URL or host name.
-
Using URL
When the URL contains ‘/manageotp’
add authentication loginSchemaPolicy lpol_single_auth_manage_otp_by_url -rule "http.req.cookie.value("NSC_TASS").contains("manageotp")" -action lschema_single_auth_manage_otpbind authentication vserver authvs -policy lpol_single_auth_manage_otp_by_url -priority 10 -gotoPriorityExpression END
-
Using hostname
When the host name is ‘alt.server.com’
add authentication loginSchemaPolicy lpol_single_auth_manage_otp_by_host -rule "http.req.header("host").eq("alt.server.com")" -action lschema_single_auth_manage_otpbind authentication vserver authvs -policy lpol_single_auth_manage_otp_by_host -priority 20 -gotoPriorityExpression END
To configure the user login page using the CLI
You must have the following information to configure the User Logon page:
- IP for a load balancing virtual server
- Corresponding FQDN for the load balancing virtual server
-
Server certificate for the load balancing virtual server
bind ssl vserver lbvs_https -certkeyname lbvs_server_cert
Back-end service in load balancing is represented as follows:
add service iis_backendsso_server_com 1.2.3.210 HTTP 80
bind lb vserver lbvs_https iis_backendsso_server_com
<!--NeedCopy-->
To create OTP passcode validation action
add authentication ldapAction <LDAP ACTION NAME> -serverIP <SERVER IP> -serverPort <SERVER PORT> -ldapBase <BASE> -ldapBindDn <AD USER> -ldapBindDnPassword <PASSWORD> -ldapLoginName <USER FORMAT> -authentication DISABLED -OTPSecret <LDAP ATTRIBUTE>
<!--NeedCopy-->
Example:
add authentication ldapAction ldap_otp_action -serverIP 1.2.3.4 -serverPort 636 -ldapBase "OU=Users,DC=server,DC=com" -ldapBindDn administrator@ctxnsdev.com -ldapBindDnPassword PASSWORD -ldapLoginName userprincipalname -authentication DISABLED -OTPSecret userParameters
<!--NeedCopy-->
Important: The difference between the LDAP logon and OTP action is the need to disable the authentication and introduce a new parameter
OTPSecret. Do not use the AD attribute value.
To add authentication policy for OTP passcode validation
add authentication Policy auth_pol_otp_validation -rule true -action ldap_otp_action
<!--NeedCopy-->
To present the two-factor authentication through LoginSchema
Add the UI for two factor authentication.
```add authentication loginSchema lscheme_dual_factor -authenticationSchema “/nsconfig/loginschema/LoginSchema/DualAuth.xml” add authentication loginSchemaPolicy lpol_dual_factor -rule true -action lscheme_dual_factor
#### To create passcode validation factor via the policy label
Create a manage OTP flow policy label for the next factor (first factor is LDAP logon)
add authentication loginSchema lschema_noschema -authenticationSchema noschema add authentication policylabel manage_otp_flow_label -loginSchema lschema_noschema
#### To bind the OTP policy to the policy label
bind authentication policylabel manage_otp_flow_label -policyName auth_pol_otp_validation -priority 10 -gotoPriorityExpression NEXT
#### To bind the UI flow
Bind the LDAP logon followed by the OTP validation with the authentication virtual server.
bind authentication vserver authvs -policy auth_pol_ldap_logon -priority 10 -nextFactor manage_otp_flow_label -gotoPriorityExpression NEXT bind authentication vserver authvs -policy lpol_dual_factor -priority 30 -gotoPriorityExpression END ```
Register your device with Citrix ADC
- Navigate to your Citrix ADC FQDN (first public facing IP), with a /manageotp suffix. For example, https://otpauth.server.com/manageotp Login with user credentials.
-
Click the + icon to add a device.

- Enter a device name and press Go. A barcode appears on the screen.
- Click Begin Setup and then click Scan Barcode.
-
Hover the device camera over the QR code. You can optionally enter the 16 digit code.
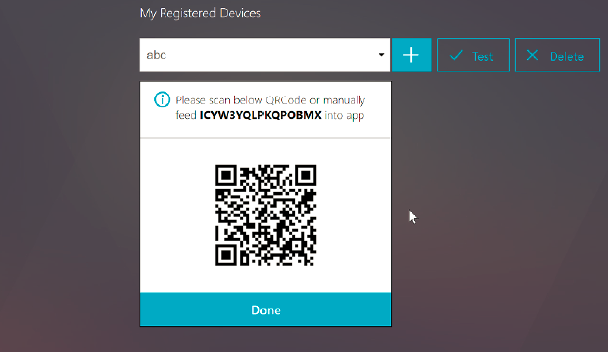
Note: The displayed QR code is valid for 3 minutes.
-
Upon successful scan, you are presented with a 6 digit time sensitive code that can be used to log in.
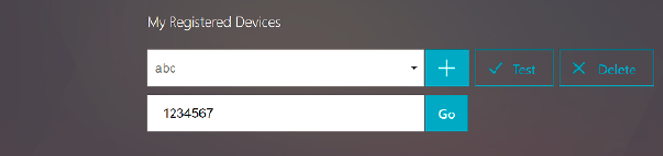
- To test, click Done on the QR screen, then click the green check mark on the right.
- Select your device from the drop-down menu and enter the code from Google Authenticator (must be blue, not red) and click Go.
- Make sure to log out using the drop-down menu at the top right corner of the page.
Log in to Citrix ADC using the OTP
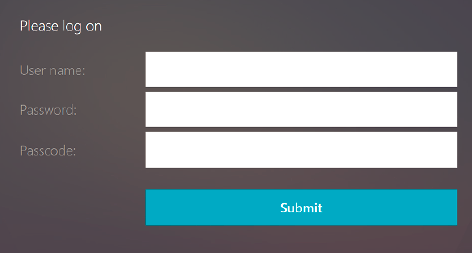
- Navigate to your first public facing URL and enter your OTP from Google Authenticator to log on.
-
Authenticate to the Citrix ADC splash page.
Share
Share
This Preview product documentation is Cloud Software Group Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Cloud Software Group Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Cloud Software Group product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.