HTML command injection protection check
The HTML command injection check examines if the incoming traffic has unauthorized commands that break the system security or modify the system. If the traffic has any malicious commands when detected, the appliance blocks the request or performs the configured action.
The NetScaler Web App Firewall profile is now enhanced with a new security check for command injection attacks. When the command injection security check examines the traffic and detects any malicious commands, the appliance blocks the request or performs the configured action.
In a command injection attack, the attacker aims to run unauthorized commands on the NetScaler operation system. To achieve this, the attacker injects operating system commands using a vulnerable application. A NetScaler appliance is vulnerable to injection attacks if the application passes any unsafe data (forms, cookies, or header) to the system shell.
How command injection protection works
-
For an incoming request, WAF examines the traffic for keywords or special characters. If the incoming request has no patterns that match any of the denied keywords or special characters, the request is allowed. Otherwise, the request is blocked, dropped, or redirected based on the configured action.
- If you prefer to exempt a keyword or a special character from the list, you can apply a relaxation rule to bypass the security check under specific conditions.
- You can enable logging to generate log messages. You can monitor the logs to determine whether responses to legitimate requests are getting blocked. A large increase in the number of log messages can indicate attempts to launch an attack.
- You can also enable the statistics feature to gather statistical data about violations and logs. An unexpected surge in the stats counter might indicate that your application is under attack. If legitimate requests are getting blocked, you might have to revisit the configuration to see if you must configure the new relaxation rule or modify the existing one.
Keywords and special characters denied for command injection check
To detect and block command injection attacks, the appliance has a set of patterns (keywords and special characters) defined in the default signature file. Following is a list of keywords blocked during command injection detection.
<commandinjection>
<keyword type="LITERAL" builtin="ON">7z</keyword>
<keyword type="LITERAL" builtin="ON">7za</keyword>
<keyword type="LITERAL" builtin="ON">7zr</keyword>
…
</commandinjection>
<!--NeedCopy-->
Special characters defined in the signature file are:
| ; & $ > < ' \ ! >> #
Configuring command injection check by using the CLI
In the command line interface, you can use either the set the profile command or the add the profile command to configure the command injection settings. You can enable the block, log, and stats actions. You must also set the key words and string characters that you want to detect in the payloads.
At the command prompt, type:
set appfw profile <profile-name> –cmdInjectionAction <action-name> -CMDInjectionType <CMDInjectionType>]
Note:
By default, the command injection action is set as “None.” Also, the default command injection type is set as
CmdSplCharANDKeyWord.
Example:
set appfw profile profile1 -cmdInjectionAction block -CMDInjectionType CmdSplChar
Where, the available command injection actions are:
- None - Disable command injection protection.
- Log - Log command injection violations for the security check.
- Block - blocks traffic that violates the command injection security check.
- Stats - Generates statistics for command injection security violations.
Where, the available command injection types are:
- Cmd SplChar. Checks special characters
- CmdKeyWord. Checks command injection Keywords
- CmdSplCharANDKeyWord. Checks special characters and command injection. Keywords and blocks only if both are present.
- CmdSplCharORKeyWord. Checks special characters and command injection Keywords and blocks if either of them is found.
Configuring relaxation rules for command injection protection check
If your application requires you to bypass the command injection inspection for a specific ELEMENT or ATTRIBUTE in the payload, you can configure a relaxation rule.
The command Injection inspection relaxation rules have the following syntax:
bind appfw profile <profile name> –cmdInjection <string> <URL> -isregex <REGEX/NOTREGEX>
Example for relaxation rule for Regex in header
bind appfw profile sample -CMDInjection hdr "http://10.10.10.10/" -location heaDER -valueType Keyword '[a-z]+grep' -isvalueRegex REGEX
As a result, the injection exempts the command injection check allows header hdr containing variants of “grep.”
Example for relaxation rule with valueType as regex in cookie
bind appfw profile sample -CMDInjection ck_login "http://10.10.10.10/" -location cookie -valueType Keyword 'pkg[a-z]+' -isvalueRegex REGEX
Configuring command injection check by using NetScaler GUI
Complete the following steps to configure the command injection check.
- Navigate to Security > NetScaler Web App Firewall and Profiles.
- On the Profiles page, select a profile and click Edit.
- On the NetScaler Web App Firewall Profile page, go to the Advanced Settings section and click Security Checks.
- In the Security Checks section, select HTML Command Injection and click Action settings.
-
In the HTML Command Injection Settings page, set the following parameters:
- Actions. Select one or more actions to perform for command injection security check.
- Check Request Containing. Select a command injection pattern to check if the incoming request has the pattern.
- Click OK.
View or customize command injection patterns by using the GUI
You can use the GUI to view or customize the HTML command injection patterns.
The default command injection patterns are specified in default signatures file. If you do not bind any signature object to your profile, the default HTML command injection patterns specified in the default signatures object will be used by the profile for the command injection security check processing. The rules and patterns, specified in the default signatures object, are read-only. You cannot edit or modify them. If you want to modify or change these patterns, make a copy of the default sSignatures object to create a User-Defined signature object. Make changes in the command injection patterns in the new User-defined signature object and use this signature object in your profile that is processing the traffic for which you want to use these customized patterns.
For more information, see Signatures
To view the default command injection patterns by using the GUI:
-
Navigate to Application Firewall > Signatures, select *Default Signatures, and click Edit.
-
Click Manage CMD/SQL/XSS patterns. The CMD/SQL/XSS Paths (read-only) table shows patterns pertaining to
CMD/SQL/XSSinjection:
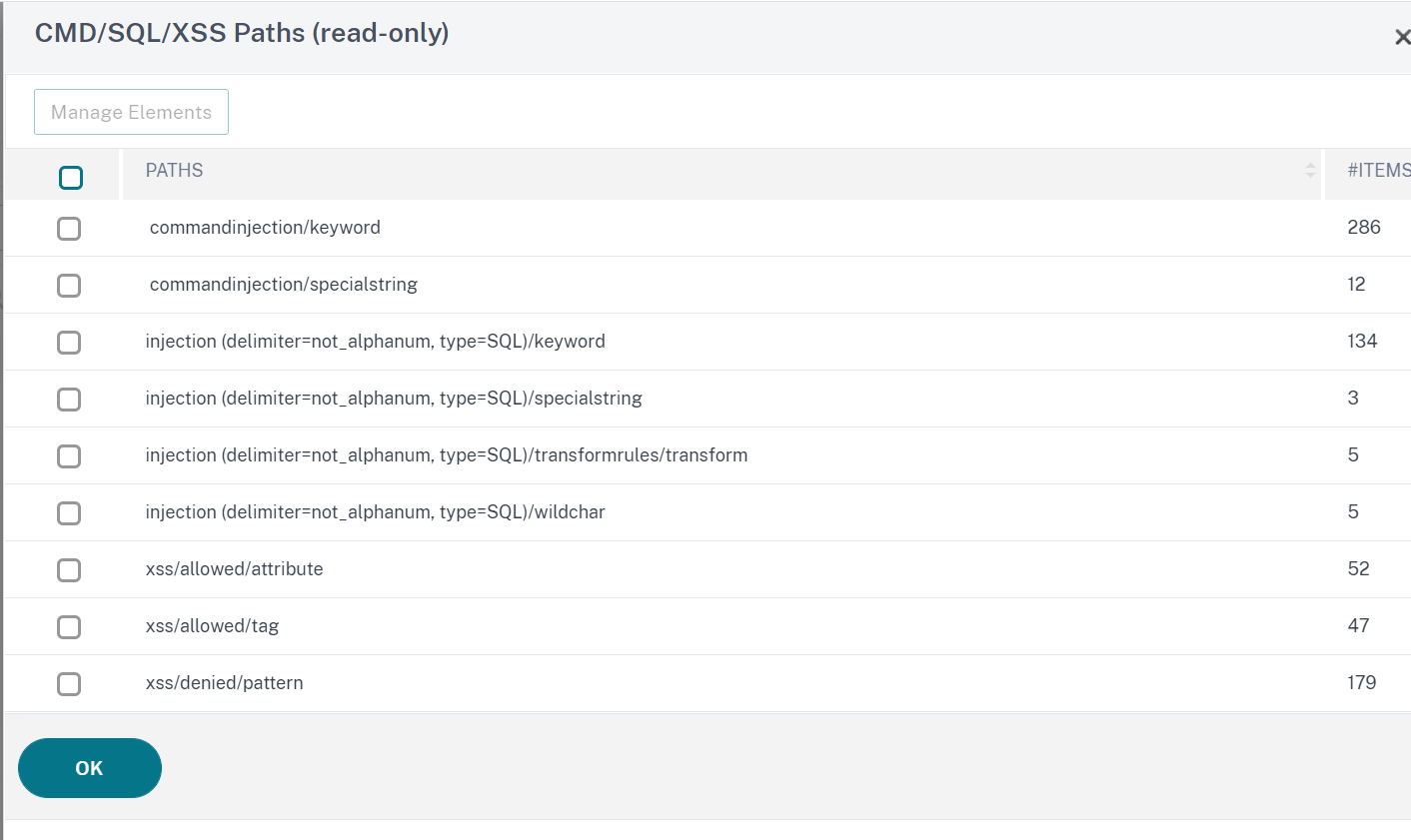
- Select a row and click Manage Elements to display the corresponding command injection patterns (keywords, special strings, transformation rules, or wildcard characters) used by the Web App Firewall command injection check.
To customize a command injection pattern by using the GUI
You can edit the user-defined signature object to customize the CMD key words, special strings, and wildcard characters. You can add new entries or remove the existing ones. You can modify the transformation rules for the command injection special strings.
- Navigate to Application Firewall > Signatures, highlight the target User-defined signature, and click Add. Click Manage CMD/SQL/XSS patterns.
- In the Manage CMD/SQL/XSS paths page, select the target CMD injection row.
-
Click Manage Elements, Add, or Remove a command injection element.
Warning:
You must be careful before you remove or modify any default command injection element, or delete the CMD path to remove the entire row. The signature rules and the command injection security check rely on these elements for detecting command injection attacks to protect your applications. Customizing the SQL patterns can make your application vulnerable to command injection attacks if the required pattern is removed during editing.
Viewing command injection traffic and violation statistics
The NetScaler Web App Firewall Statistics page shows security traffic and security violation details in a tabular or graphical format.
To view security statistics by using the command interface.
At the command prompt, type:
stat appfw profile profile1
| Appfw profile Traffic Statistics | Rate (/s) | Total |
|---|---|---|
| Requests | 0 | 0 |
| Request Bytes | 0 | 0 |
| Responses | 0 | 0 |
| Response Bytes | 0 | 0 |
| Aborts | 0 | 0 |
| Redirects | 0 | 0 |
| Long Term Ave Response Time (ms) | – | 0 |
| Recent Ave Response Time (ms) | – | 0 |
| HTML/XML/JSON Violation Statistics | Rate (/s) | Total |
|---|---|---|
| Start URL | 0 | 0 |
| Deny URL | 0 | 0 |
| Referer header | 0 | 0 |
| Buffer overflow | 0 | 0 |
| Cookie consistency | 0 | 0 |
| Cookie hijacking | 0 | 0 |
| CSRF form tag | 0 | 0 |
| HTML Cross-site scripting | 0 | 0 |
| HTML SQL injection | 0 | 0 |
| Field format | 0 | 0 |
| Field consistency | 0 | 0 |
| Credit card | 0 | 0 |
| Safe object | 0 | 0 |
| Signature Violations | 0 | 0 |
| Content Type | 0 | 0 |
| JSON Denial of Service | 0 | 0 |
| JSON SQL injection | 0 | 0 |
| JSON Cross-Site Scripting | 0 | 0 |
| File Upload Types | 0 | 0 |
| Infer Content Type XML Payload | 0 | 0 |
| HTML CMD Injection | 0 | 0 |
| XML Format | 0 | 0 |
| XML Denial of Service (XDoS) | 0 | 0 |
| XML Message Validation | 0 | 0 |
| Web Services Interoperability | 0 | 0 |
| XML SQL Injection | 0 | 0 |
| XML Cross-Site Scripting | 0 | 0 |
| XML Attachment | 0 | 0 |
| SOAP Fault Violations | 0 | 0 |
| XML Generic Violations | 0 | 0 |
| Total Violations | 0 | 0 |
| HTML/XML/JSON Log Statistics | Rate (/s) | Total |
|---|---|---|
| Start URL logs | 0 | 0 |
| Deny URL logs | 0 | 0 |
| Referer header logs | 0 | 0 |
| Buffer overflow logs | 0 | 0 |
| Cookie consistency logs | 0 | 0 |
| Cookie hijacking logs | 0 | 0 |
| CSRF from tag logs | 0 | 0 |
| HTML cross-site scripting logs | 0 | 0 |
| HTML cross-site scripting transform logs | 0 | 0 |
| HTML SQL Injection logs | 0 | 0 |
| HTML SQL transform logs | 0 | 0 |
| Field format logs | 0 | 0 |
| Field consistency logs | 0 | 0 |
| Credit cards | 0 | 0 |
| Credit card transform logs | 0 | 0 |
| Safe object logs | 0 | 0 |
| Signature logs | 0 | 0 |
| Content Type logs | 0 | 0 |
| JSON Denial of Service logs | 0 | 0 |
| JSON SQL injection logs | 0 | 0 |
| JSON Cross-Site Scripting logs | 0 | 0 |
| File upload types logs | 0 | 0 |
| Infer Content Type XML Payload L | 0 | 0 |
| HTML Command Injection logs | 0 | 0 |
| XML Format logs | 0 | 0 |
| XML Denial of Service(XDoS) logs | 0 | 0 |
| XML Message Validation logs | 0 | 0 |
| WSI logs | 0 | 0 |
| XML SQL Injection logs | 0 | 0 |
| XML cross-site scripting logs | 0 | 0 |
| XML Attachment logs | 0 | 0 |
| SOAP Fault logs | 0 | 0 |
| XML Generic logs | 0 | 0 |
| Total log messages | 0 | 0 |
| Server Error Response Statistics Rate (/s) > Total | ||
|---|---|---|
| HTTP Client Errors (4xx Resp) | 0 | 0 |
| HTTP Server Errors (5xx Resp) | 0 | 0 |
Viewing HTML command injection statistics by using the NetScaler GUI
Complete the following steps to view the command injection statistics:
- Navigate to Security > NetScaler Web App Firewall > Profiles.
- In the details pane, select a Web App Firewall profile and click Statistics.
- The NetScaler Web App Firewall Statistics page displays the HTML command injection traffic and violation details.
- You can select Tabular View or switch to Graphical View to display the data in a tabular or graphical format.
In this article
- How command injection protection works
- Keywords and special characters denied for command injection check
- Configuring command injection check by using the CLI
- Configuring relaxation rules for command injection protection check
- Configuring command injection check by using NetScaler GUI
- View or customize command injection patterns by using the GUI
- Viewing command injection traffic and violation statistics
- Viewing HTML command injection statistics by using the NetScaler GUI