Application classification
The Citrix SD-WAN™ appliances perform deep packet inspection (DPI) to identify and classify applications using the following techniques:
- DPI library classification
- Citrix-proprietary Independent Computing Architecture (ICA®) classification
- Application vendor APIs (for example Microsoft REST APIs for Office 365)
- Domain name based application classification
DPI library classification
The Deep Packet Inspection (DPI) library recognizes thousands of commercial applications. It enables real-time discovery and classification of applications. Using the DPI technology, the SD-WAN appliance analyses the incoming packets and classifies the traffic as belonging to a particular application or application family. Application classification for each connection takes a few packets.
To enable DPI library classification on Citrix SD-WAN Orchestrator service, see DPI library classification.
ICA classification
Citrix SD-WAN appliances can also identify and classify Citrix HDX™ traffic for virtual apps and desktops. Citrix SD-WAN recognizes the following variations of the ICA protocol:
- ICA
- ICA-CGP
- Single Stream ICA (SSI)
- Multi-Stream ICA (MSI)
- ICA over TCP
- ICA over UDP/EDT
- ICA over non-standard ports (including Multi-Port ICA)
- HDX Adaptive Transport
- ICA over WebSocket (used by HTML5 Receiver)
Note
Classification of ICA traffic delivered over SSL/TLS or DTLS is not supported in SD-WAN Standard Edition.
Classification of network traffic is done during initial connections or flow establishment. Therefore, pre-existing connections are not classified as ICA. Classification of connections is also lost when the connection table is cleared manually.
Framehawk traffic and Audio-over-UDP/RTP are not classified as HDX applications. They are reported as either “UDP” or “Unknown Protocol.”
Since release 10 version 1, the SD-WAN appliance can differentiate each ICA data stream in multi-stream ICA even in a single-port configuration. Each ICA stream is classified as a separate application with its own default QoS class for prioritization.
For Multi-Stream ICA functionality to work properly, you must have SD-WAN Standard Edition 10.1 or above.
For HDX user based reports to be shown on SDWAN-Center, you must have SD-WAN Standard Edition 11.0 or above.
Minimum software requirements for HDX information virtual channel:
A Current Release of Citrix Virtual Apps and Desktops (formerly XenApp and XenDesktop), since the prerequisite functionality was introduced in XenApp and XenDesktop 7.17 and is not included in the 7.15 Long-Term Service Release.
A version of the Citrix Workspace app (or its predecessor, Citrix Receiver) that supports multi-stream ICA and the HDX Insights information virtual channel, CTXNSAP. Look for HDX Insight with NSAP VC and Multiport/Multi-stream ICA in the Citrix Workspace app Feature Matrix. See the currently supported release versions at HDX Insights.
From 11.2 release onwards, packet duplication is now enabled by default for HDX real-time traffic when multi-stream ICA is in use.
Once classified, the ICA application can be used in application rules and to view application statistics similar to other classified applications.
There are five default application rules for ICA applications one each for the following priority tags:
- Independent Computing Architecture (Citrix)(ICA)
- ICA Real-time (ica_priority_0)
- ICA Interactive (ica_priority_1)
- ICA Bulk-Transfer (ica_prority_2)
- ICA Background(ica_priority_3)
For more information, see Rules by Application Name
If you are running a combination of software that does not support Multi-Stream ICA over a single port, then to perform QoS you must configure multiple ports, one for each ICA stream. To classify HDX on non-standard ports as configured in XA/XD server policy, you must add those ports in ICA port configurations. Also, to match traffic on those ports to valid IP rules, you must update the ICA IP rules.
In the ICA IP and port list you can specify non-standard ports used in XA/XD policy to process for HDX classification. IP address is used to further restrict the ports to a specific destination. Use ‘*’ for port destined to any IP address. IP address with combination of SSL port is also used to indicate that the traffic is likely ICA even though the traffic is not finally classified as ICA. This indication is used to send L4 AppFlow records to support multi-hop reports in Citrix Application Delivery Management.
To enable ICA based classification on Citrix SD-WAN Orchestrator service, see ICA classification.
Application vendor API based classification
Citrix SD-WAN supports the following application vendor API based classification:
-
Office 365. For more information, see Office 365 optimization.
-
Citrix Cloud and Citrix Gateway service. For more information, see Gateway Service Optimization.
Domain name based application classification
The DPI classification engine is enhanced to classify applications based on the domain name and patterns. After the DNS forwarder intercepts and parses the DNS requests, the DPI engine uses the IP classifier to perform first packet classification. Further DPI library and ICA classification are done and the domain name based application ID is appended.
The Domain name based application feature allows you to group several domain names and treat it as a single application. Making it easier to apply firewall, application steering, QoS, and other rules. A maximum of 64 domain name based applications can be configured.
To define domain name based applications on Citrix SD-WAN Orchestrator service, see Domain name based application classification.
Note
From 11.4.2 release onwards, the Domain name-based applications support configurable ports and protocol in Citrix SD-WAN Orchestrator service. For more information, see Domains and applications.
From Citrix SD-WAN 11.5.0 release onwards, AAAA records are supported on Citrix SD-WAN Orchestrator service.
Limitations
- If there are no DNS request/response corresponding to a domain name based application, the DPI engine does not classify the domain name based application and hence does not apply the application rules corresponding to the domain name based application.
- If an Application Object is created such that the port range includes port 80 and/or port 443, with a specific IP address match type that corresponds to a domain name based application, the DPI engine does not classify the domain name based application.
- If explicit web proxies are configured, you have to add all the domain name patterns to the PAC file, to ensure that the DNS response does not always return the same IP address.
- The domain name based application classifications are reset on configuration upgrade. Reclassification happens based on pre 11.0.2 release classification techniques such as DPI library classification, ICA classification and Vendor application APIs based classification.
- The application signatures learned (destination IP addresses) by domain name based application classification are reset on configuration update.
- Only the standard DNS queries and their responses are processed.
- DNS response records split over multiple packets are not processed. Only DNS responses in a single packet are processed.
- DNS over TCP is not supported.
- Only top-level domains are supported as domain name patterns.
Classifying encrypted traffic
Citrix SD-WAN appliance detects and reports encrypted traffic, as part of application reporting, in the following two methods:
- For HTTPS traffic, the DPI engine inspects the SSL certificate to read the common name, which carries the name of the service (for example - Facebook, Twitter). Depending on the application architecture only one certificate might be used for several service types (for example - email, news, and so on). If different services use different certificates, the DPI engine would be able to differentiate between services.
- For applications that use their own encryption protocol, the DPI engine looks for binary patterns in the flows for instance in case of Skype the DPI engine looks for a binary pattern inside the certificate and determines the application.
Application Objects
Application objects enable you to group different types of match criteria into a single object that can be used in firewall policies and application steering. IP Protocol, Application, and Application Family are the available match types.
The following features use the application object as a match type:
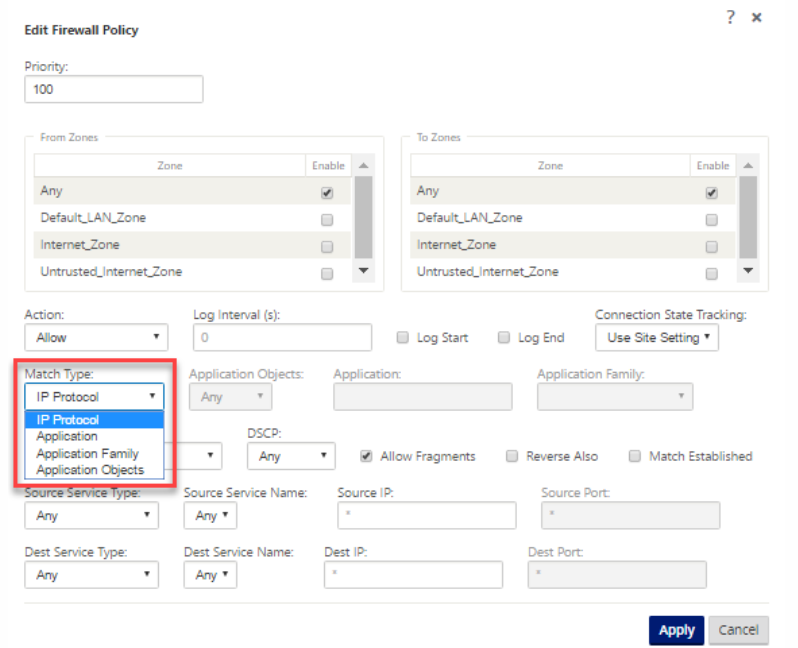
Using Application Classification with a Firewall
The classification of traffic as applications, application families or domain names enables you to use the application, application families, and application objects as match types to filter traffic and apply firewall policy and rules. It applies for all Pre, Post, and local policies. For more information about firewall, see Stateful Firewall and NAT Support.
 –>
–>
Viewing Application Classification
After enabling application classification, you can view the application name and application family details in the following reports:
-
Firewall connection Statistics
-
Flows information
-
Application statistics
Firewall connection statistics
Navigate to Monitoring > Firewall. Under Connections section, the Application and Family columns list the applications and its associated family.
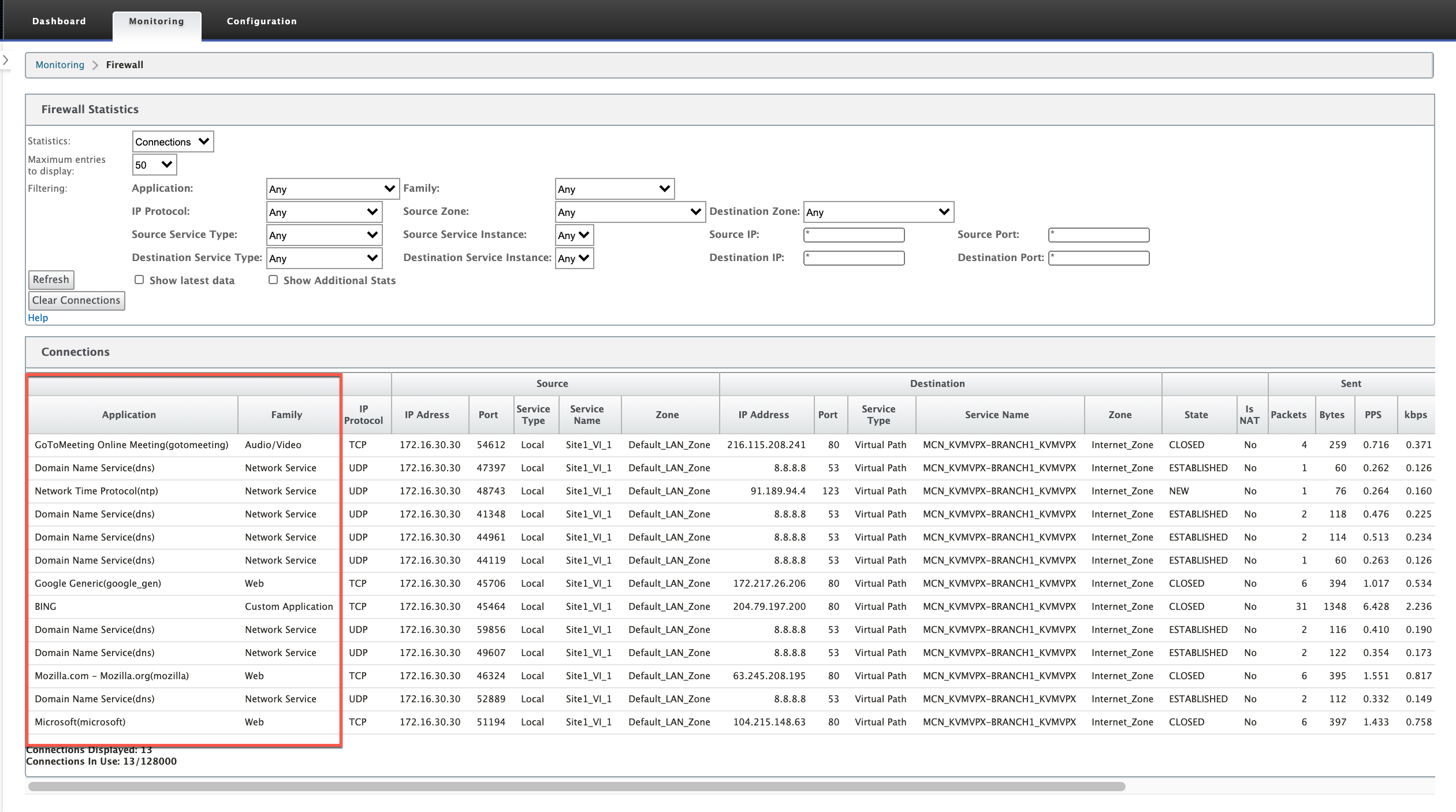
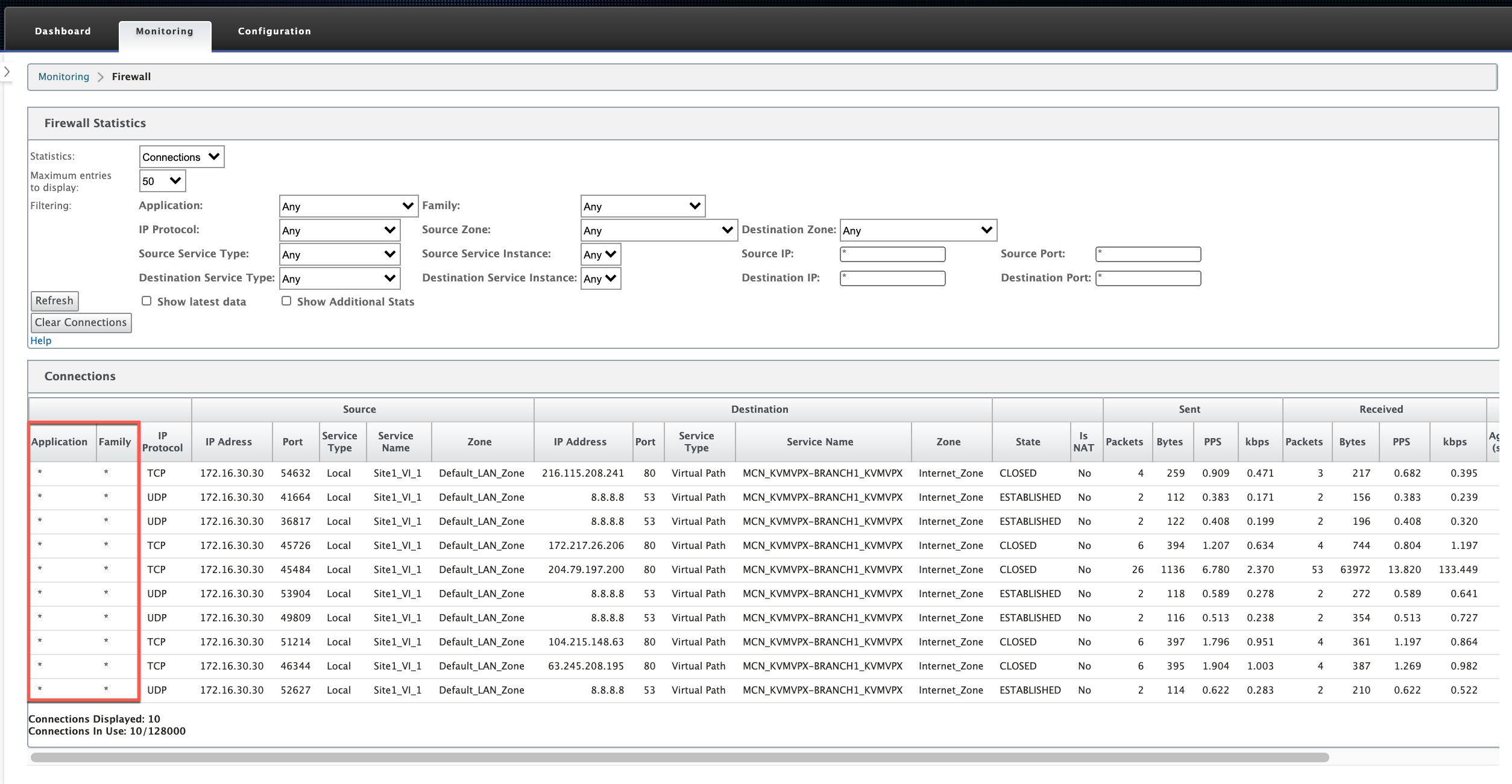
If you do not enable application classification, the Application and Family columns do not show any data.
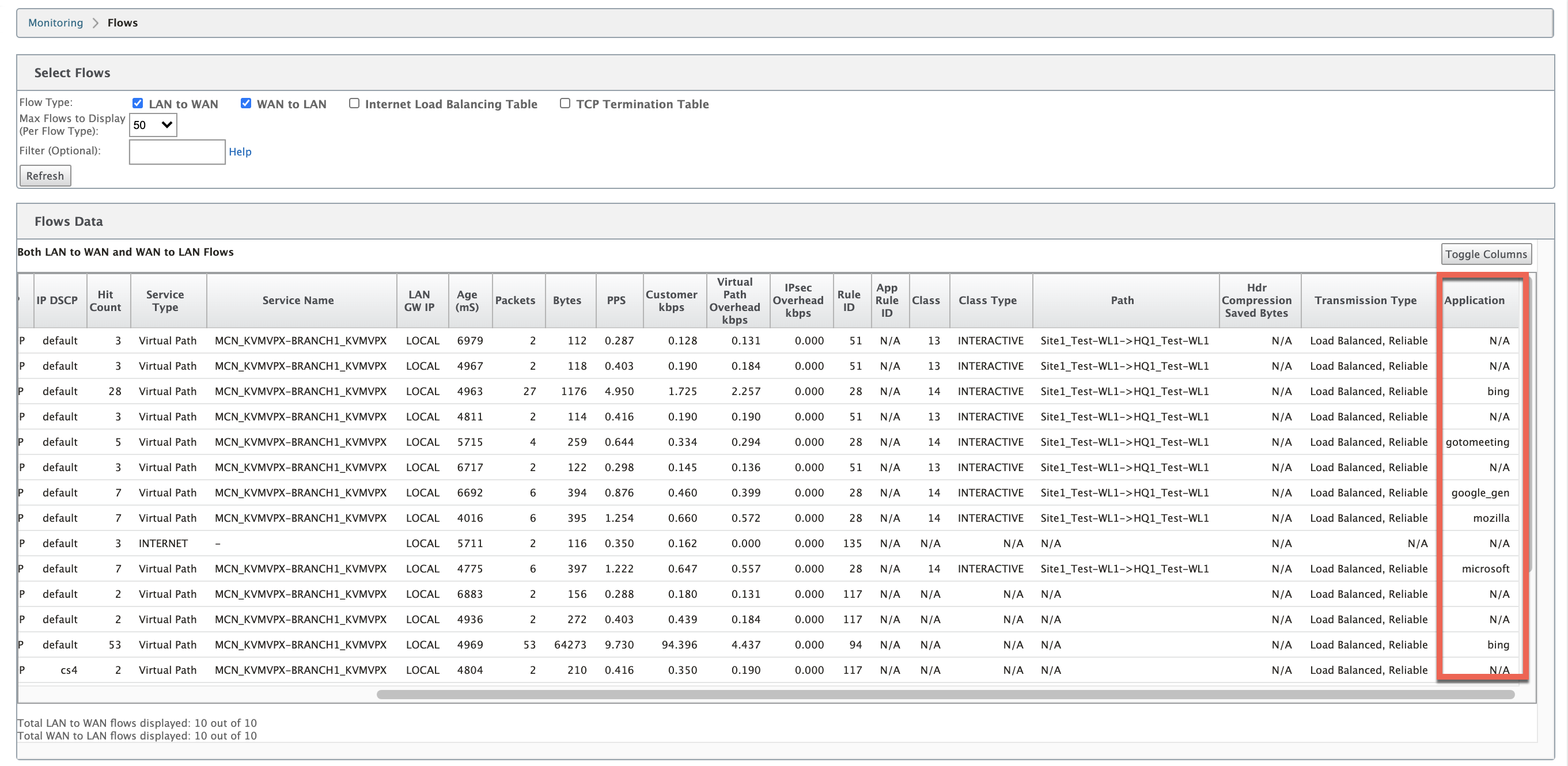
Flows Information
Navigate to Monitoring > Flows. Under Flows Data section, the Application column lists the application details.
Application statistics
Navigate to Monitoring > Statistics. Under Application Statistics section, the Application column lists the application details.
Troubleshooting
After enabling application classification, you can view the reports under the Monitoring section and ensure that they show application details. For more information, see Viewing Application Classification.
If there is any unexpected behavior, collect the STS diagnostics bundle while the issue is being observed, and share it with the Citrix Support team.
The STS bundle can be created and downloaded using Configuration > System Maintenance > Diagnostics > Diagnostic Information.