-
-
-
SSL certificate for services of type LoadBalancer through the Kubernetes secret resource
-
BGP advertisement for type LoadBalancer services and Ingresses using NetScaler CPX
-
NetScaler CPX integration with MetalLB in layer 2 mode for on-premises Kubernetes clusters
-
Advanced content routing for Kubernetes Ingress using the HTTPRoute CRD
-
IP address management using the NetScaler IPAM controller for Ingress resources
-
Deploy NetScaler ingress controller for NetScaler with admin partitions
-
-
Traffic management for external services
This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Traffic management for external services
Sometimes, all the available services of an application may not be deployed completely on a single Kubernetes cluster. You may have applications that rely on the services outside of one cluster as well. In this case, micro services need to define an ExternalName service to resolve the domain name. However, in this approach, you would not be able to get features such as traffic management, policy enforcement, fail over management and so on. As an alternative, you can configure NetScaler to resolve the domain names and leverage the features of NetScaler.
Configure NetScaler to reach external services
You can configure NetScaler as a domain name resolver using NetScaler Ingress Controller. When you configure NetScaler as domain name resolver, you need to resolve:
- Reachability of NetScaler from microservices
- Domain name resolution at NetScaler to reach external services
Configure a service for reachability from Kubernetes cluster to NetScaler
To reach NetScaler from microservices, you have to define a headless service which would be resolved to a NetScaler service and thus the connectivity between microservices and NetScaler establishes.
apiversion: v1
kind: Service
metadata:
name: external-svc
spec:
selector:
app: cpx
ports:
- protocol: TCP
port: 80
Configure NetScaler as a domain name resolver using NetScaler Ingress Controller
You can configure NetScaler through NetScaler Ingress Controller to create a domain based service group using the ingress annotation ingress.citrix.com/external-service. The value for ingress.citrix.com/external-service is a list of external name services with their corresponding domain names. For NetScaler VPX, name servers are configured on NetScaler using the ConfigMap.
Note:
ConfigMaps are used to configure name servers on NetScaler only for NetScaler VPX. For NetScaler CPX, CoreDNS forwards the name resolution request to the upstream DNS server.
Traffic management using NetScaler CPX
The following diagram explains NetScaler CPX deployment to reach external services. An Ingress is deployed where the external service annotation is specified to configure DNS on NetScaler CPX.
Note: A ConfigMap is used to configure name servers on NetScaler VPX.
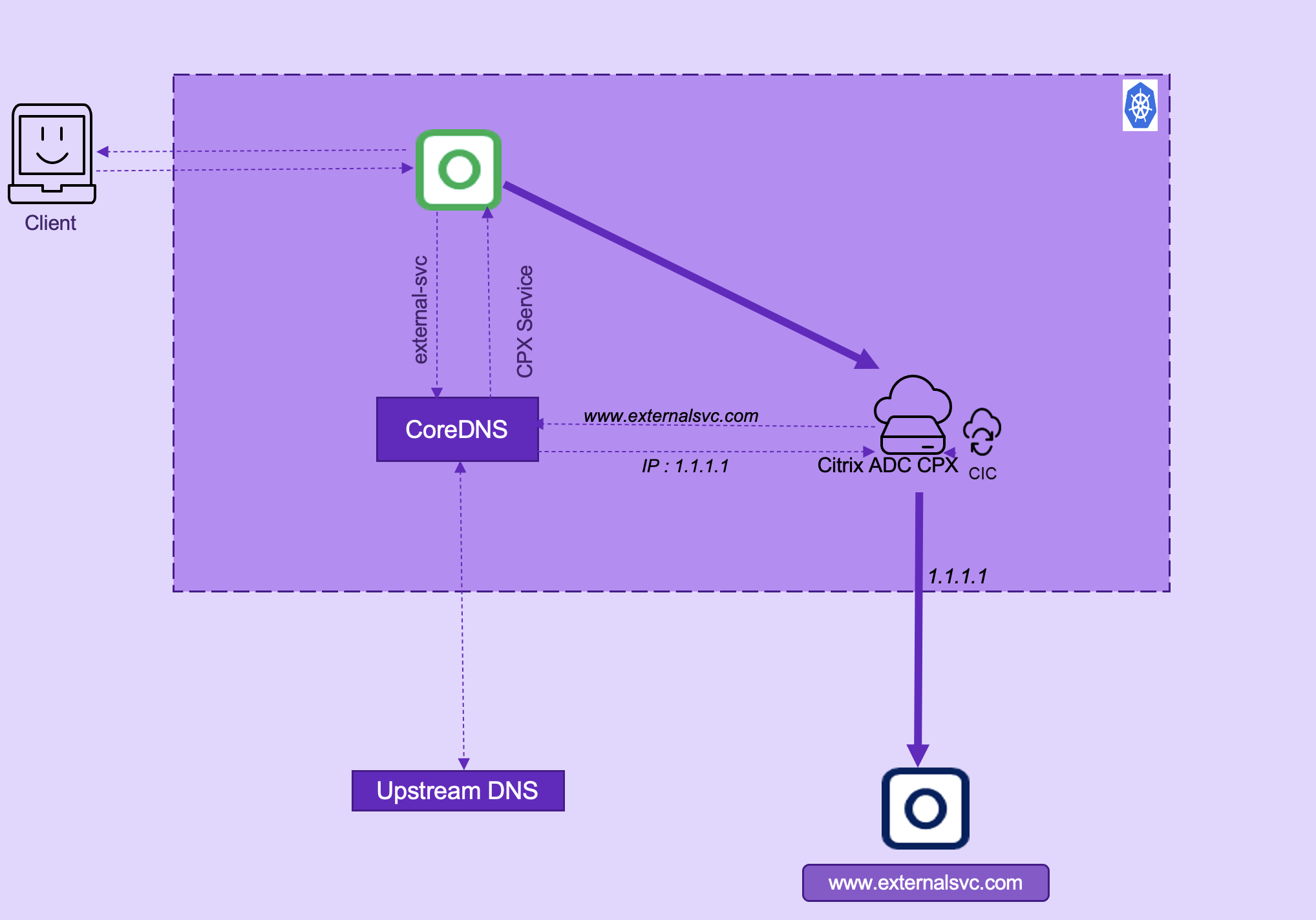
In this deployment:
- A microservice sends the DNS query for www.externalsvc.com which would get resolved to the NetScaler CPX service.
- NetScaler CPX resolves www.externalsvc.com and reaches external service.
Following are the steps to configure NetScaler CPX to load balance external services:
-
Define a headless service to reach NetScaler.
apiVersion: v1 kind: Service metadata: name: external-svc spec: selector: app: cpx ports: - protocol: TCP port: 80 -
Define an ingress and specify the external-service annotation as specified in the dbs-ingress.yaml file. When you specify this annotation, NetScaler Ingress Controller creates DNS servers on NetScaler and binds the servers to the corresponding service group.
annotations: ingress.citrix.com/external-service: '{"external-svc": {"domain": "www.externalsvc.com"}}' -
Add the IP address of the DNS server on NetScaler using ConfigMap.
Note:
This step is applicable only for NetScaler VPX.
apiVersion: v1 kind: ConfigMap metadata: name: nameserver-cmap namespace: default data: NS_DNS_NAMESERVER: '[]' <!--NeedCopy-->
Share
Share
In this article
This Preview product documentation is Cloud Software Group Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Cloud Software Group Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Cloud Software Group product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.