-
-
-
SSL certificate for services of type LoadBalancer through the Kubernetes secret resource
-
BGP advertisement for type LoadBalancer services and Ingresses using NetScaler CPX
-
NetScaler CPX integration with MetalLB in layer 2 mode for on-premises Kubernetes clusters
-
Advanced content routing for Kubernetes Ingress using the HTTPRoute CRD
-
IP address management using the NetScaler IPAM controller for Ingress resources
-
Deploy NetScaler ingress controller for NetScaler with admin partitions
-
This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
TLS client authentication support in NetScaler
In TLS client authentication, a server requests a valid certificate from the client for authentication and ensures that it is only accessible by authorized machines and users.
You can enable TLS client authentication using NetScaler SSL-based virtual servers. With client authentication enabled on a NetScaler SSL virtual server, the NetScaler asks for the client certificate during the SSL handshake. The appliance checks the certificate presented by the client for normal constraints, such as the issuer signature and expiration date.
The following diagram explains the TLS client authentication feature on NetScaler.
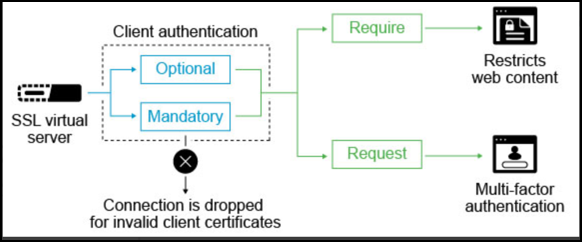
TLS client authentication can be set to mandatory, or optional. If the SSL client authentication is set as mandatory and the SSL Client does not provide a valid client certificate, then the connection is dropped. A valid client certificate means that it is signed or issued by a specific Certificate Authority, and not expired or revoked. If it is marked as optional, then the NetScaler requests the client certificate, but the connection is not dropped. The NetScaler proceeds with the SSL transaction even if the client does not present a certificate or the certificate is invalid. The optional configuration is useful for authentication scenarios like two-factor authentication.
Configuring TLS client authentication
Perform the following steps to configure TLS client authentication.
-
Enable the TLS support in NetScaler.
The NetScaler Ingress Controller uses the TLS section in the Ingress definition as an enabler for TLS support with NetScaler. The following is a sample snippet of the Ingress definition:
spec: tls: - secretName: -
Apply a CA certificate to the Kubernetes environment.
To generate a Kubernetes secret for an existing certificate, use the following kubectl command:
kubectl create secret generic tls-ca --from-file=tls.crt=cacerts.pemNote:
You must specify ‘tls.crt=’ while creating a secret. This file is used by the NetScaler Ingress Controller while parsing a CA secret.
-
Configure Ingress to enable client authentication.
You need to specify the following annotation to attach the generated CA secret which is used for client certificate authentication for a service deployed in Kubernetes.
ingress.citrix.com/ca-secret: '{"frontend-hotdrinks": "hotdrink-ca-secret"}'By default, client certificate authentication is set to
mandatorybut you can configure it tooptionalusing thefrontend_sslprofileannotation in the front end configuration.ingress.citrix.com/frontend_sslprofile: '{"clientauth":"ENABLED", “clientcert”: “optional”}'Note:
The
frontend_sslprofileonly supports the front end Ingress configuration. For more information, see front end configuration.
Share
Share
In this article
This Preview product documentation is Cloud Software Group Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Cloud Software Group Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Cloud Software Group product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.