-
-
-
SSL certificate for services of type LoadBalancer through the Kubernetes secret resource
-
BGP advertisement for type LoadBalancer services and Ingresses using NetScaler CPX
-
NetScaler CPX integration with MetalLB in layer 2 mode for on-premises Kubernetes clusters
-
Advanced content routing for Kubernetes Ingress using the HTTPRoute CRD
-
IP address management using the NetScaler IPAM controller for Ingress resources
-
Deploy NetScaler ingress controller for NetScaler with admin partitions
-
This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Configure cross-origin resource sharing policies with NetScaler Ingress Controller
NetScaler provides a Custom Resource Definition (CRD) called the CORS CRD for Kubernetes. You can use the CORS CRD to configure the cross-origin resource sharing (CORS) policies with NetScaler Ingress Controller on the NetScaler.
What is CORS
Cross-Origin resource sharing is a mechanism that allows the browser to determine whether a specific web application can share resources with another web application from a different origin. It allows users request resources (For example, images, fonts, and videos) from domains outside the original domain.
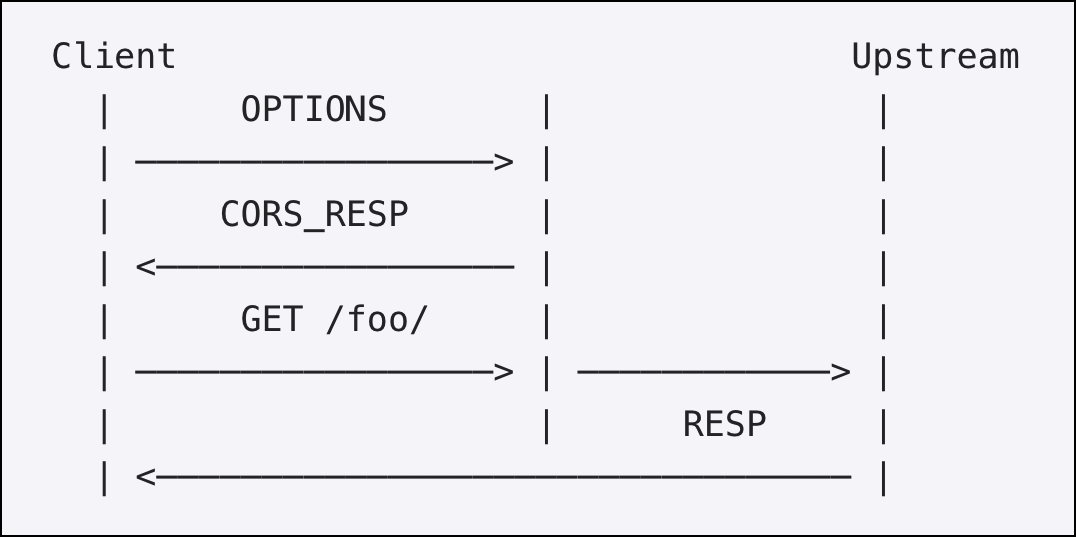
CORS pre-flight
Before a web browser allowing Javascript to issue a POST to a URL, it performs a pre-flight request. A pre-flight request is a simple request to the server with the same URL using the method OPTIONS rather than POST. The web browser checks the HTTP headers for CORS related headers to determine if POST operation on behalf of the user is allowed.
CORS CRD definition
The CORS CRD is available in the NetScaler Ingress Controller GitHub repo at: cors-crd.yaml. The CORS CRD provides attributes for the various options that are required to define the CORS policy on the Ingress NetScaler that acts as an API gateway. The required attributes include: servicenames, allow_origin, allow_methods, and allow_headers.
The following are the attributes provided in the CORS CRD:
| Attribute | Description |
|---|---|
ingressclass |
Specifies the ingress class so that only the ingress controller associated with the specified ingress class processes the resource. Otherwise, all the controllers in the cluster will process this resource. |
servicenames |
Specifies the list of Kubernetes services to which you want to apply the CORS policies. |
allow_origin |
Specifies the list of allowed origins. Incoming origin is screened against this list. |
allow_methods |
Specifies the list of allowed methods as part of the CORS protocol. |
allow_headers |
Specifies the list of allowed headers as part of the CORS protocol. |
max_age |
Specifies the number of seconds the information provided by the Access-Control-Allow-Methods and Access-Control-Allow-Headers headers can be cached. The default value is 86400. |
allow_credentials |
Specifies whether the response can be shared when the credentials mode of the request is “include”. The default value is ‘true’. |
Deploy the CORS CRD
Perform the following to deploy the CORS CRD:
-
Download the CORS CRD.
-
Deploy the CORS CRD using the following command:
kubectl create -f cors-crd.yamlFor example:
$ kubectl create -f cors-crd.yaml customresourcedefinition.apiextensions.k8s.io/corspolicies.citrix.com created $ kubectl get crd NAME CREATED AT corspolicies.citrix.com 2021-05-21T20:01:13Z
How to write a CORS policy configuration
After you have deployed the CORS CRD provided by NetScaler in the Kubernetes cluster, you can define the CORS policy configuration in a .yaml file. In the .yaml file, use corspolicy in the kind field and in the spec section add the CORS CRD attributes based on your requirement for the policy configuration.
The following YAML file applies the configured policy to the services listed in the servicenames field. NetScaler responds with a 200 OK response code for the pre-flight request if the origin is one of the allow_origins [“random1234.com”, “hotdrink.beverages.com”]. The response includes configured allow_methods, allow_headers, and max_age.
apiVersion: citrix.com/v1beta1
kind: corspolicy
metadata:
name: corspolicy-example
spec:
servicenames:
- "cors-service"
allow_origin:
- "random1234.com"
- "hotdrink.beverages.com"
allow_methods:
- "POST"
- "GET"
- "OPTIONS"
allow_headers:
- "Origin"
- "X-Requested-With"
- "Content-Type"
- "Accept"
- "X-PINGOTHER"
max_age: 86400
allow_credentials: true
<!--NeedCopy-->
After you have defined the policy configuration, deploy the .yaml file using the following commands:
user@master:~/cors$ kubectl create -f corspolicy-example.yaml
corspolicy.citrix.com/corspolicy-example created
The NetScaler Ingress Controller applies the policy configuration on the Ingress NetScaler device.
Share
Share
In this article
This Preview product documentation is Cloud Software Group Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Cloud Software Group Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Cloud Software Group product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.