Office 365 optimization
The Office 365 Optimization features adhere to the Microsoft Office 365 Network Connectivity Principles, to optimize Office 365. Office 365 is provided as a service through several service endpoints (front doors) located globally.
To achieve optimal user experience for Office 365 traffic, Microsoft recommends redirecting Office365 traffic directly to the Internet from branch environments. Avoid practices such as backhauling to a central proxy. Office 365 traffic such as Outlook, Word are sensitive to latency and backhauling traffic introduces more latency resulting in poor user experience. Citrix SD-WAN™ allows you to configure policies to break out Office 365 traffic to the Internet.
The Office 365 traffic is directed to the nearest Office 365 service endpoint, which exists at the edges of Microsoft Office 365 infrastructure worldwide. Once traffic reaches a front door, it goes over Microsoft network and reaches the actual destination. It minimizes latency as the round trip time from the customer network to the Office 365 endpoint reduces.
How Office 365 optimization works
The Microsoft endpoint signatures are updated at most once a day. Agent on the appliance polls the Citrix service (sdwan-app-routing.citrixnetworkapi.net), every day to obtain the latest set of end-point signatures. The SD-WAN appliance polls the Citrix service (sdwan-app-routing.citrixnetworkapi.net), once every day, when the appliance is turned on.
If there are new signatures available, the appliance downloads it and stores it in the database. The signatures are essentially a list of URLs and IPs used to detect Office 365 traffic based on which traffic steering policies can be configured.
Note
Except for the Office 365 Default category, first packet detection and classification of Office 365 traffic is performed by default, irrespective of whether the Office 365 breakout feature is enabled or not.
When a request for the Office 365 application arrives, the application classifier, does a first packet classifier database lookup, identifies, and marks Office 365 traffic. Once the Office 365 traffic is classified, the auto created application route and firewall policies take effect and breaks out the traffic directly to the Internet. The Office 365 DNS requests are forwarded to specific DNS services like Quad9.
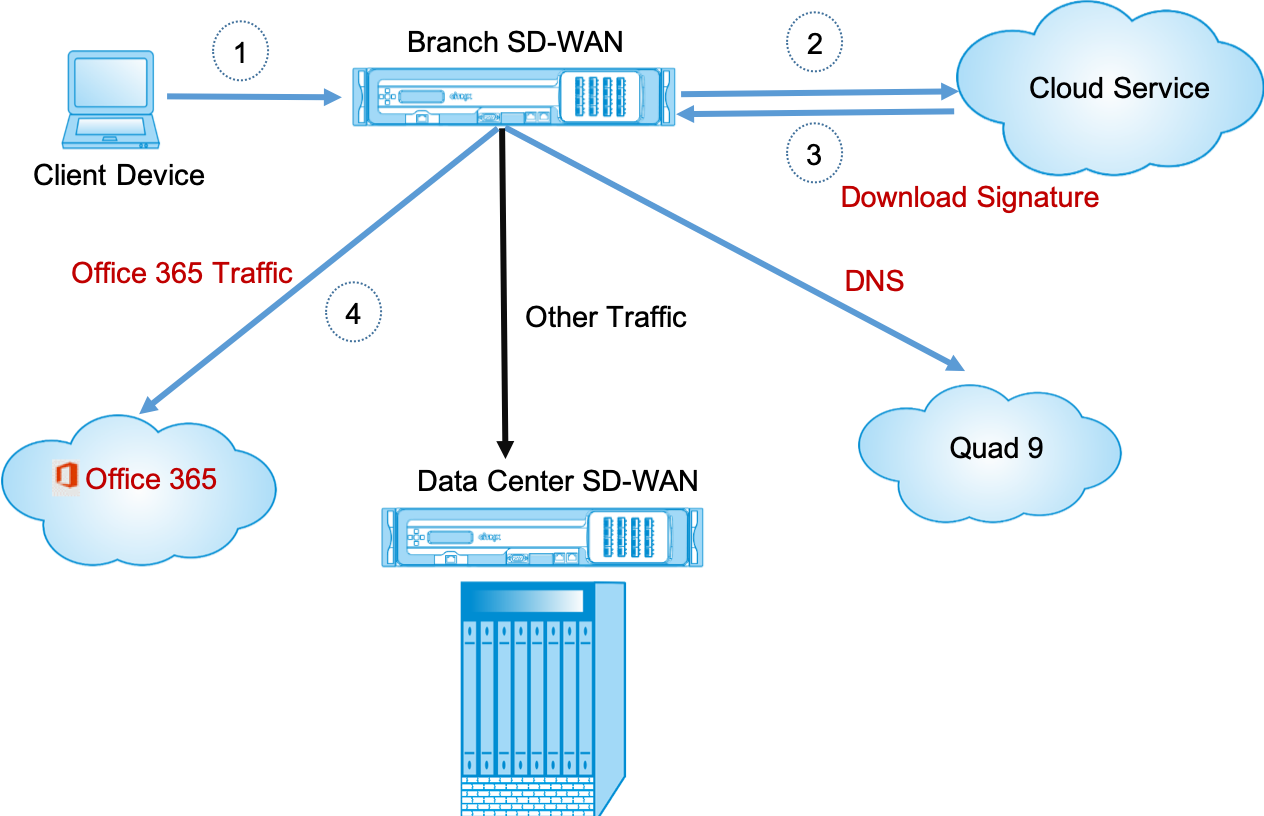
The signatures are downloaded from Cloud Service (sdwan-app-routing.citrixnetworkapi.net).
Configure Office 365 breakout
The Office 365 breakout policy allows you to specify which category of Office 365 traffic you can directly break out from the branch. On enabling Office 365 breakout and compiling the configuration, a DNS object, application object, application route, and a firewall policy template is auto-created and applied to branch sites with the Internet service.
Prerequisites
Ensure that you have the following:
-
To perform Office 365 breakout, an internet service has to be configured on the appliance.
-
Ensure that the Management interface has internet connectivity.
-
Ensure that the management DNS is configured.
In Citrix SD-WAN Orchestrator service, by-default every network have the office 365 rule under Application Group. To navigate, go to Network Configuration > Routing > Routing Policies > Application Routes.
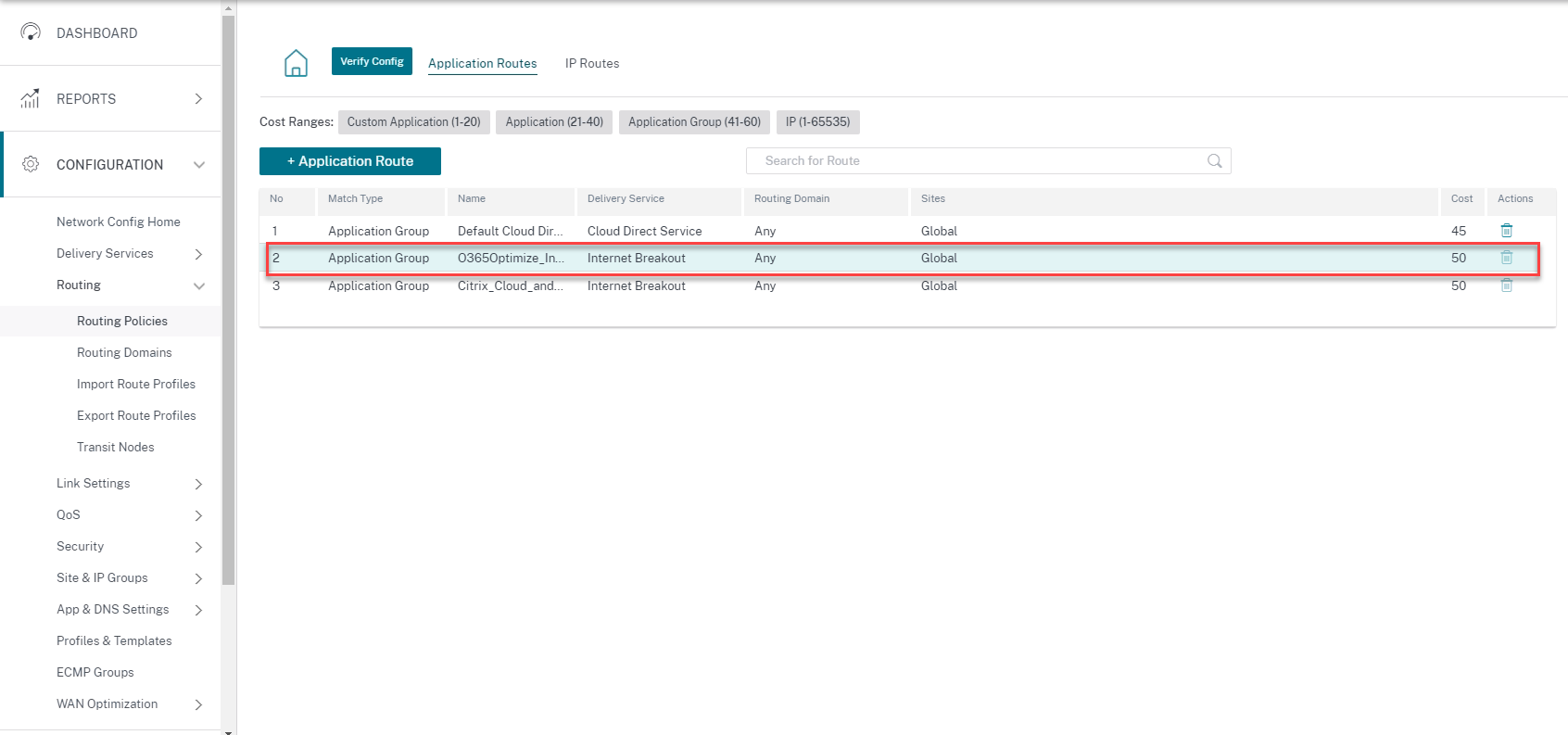
You cannot delete the rule but can configure the settings as required.
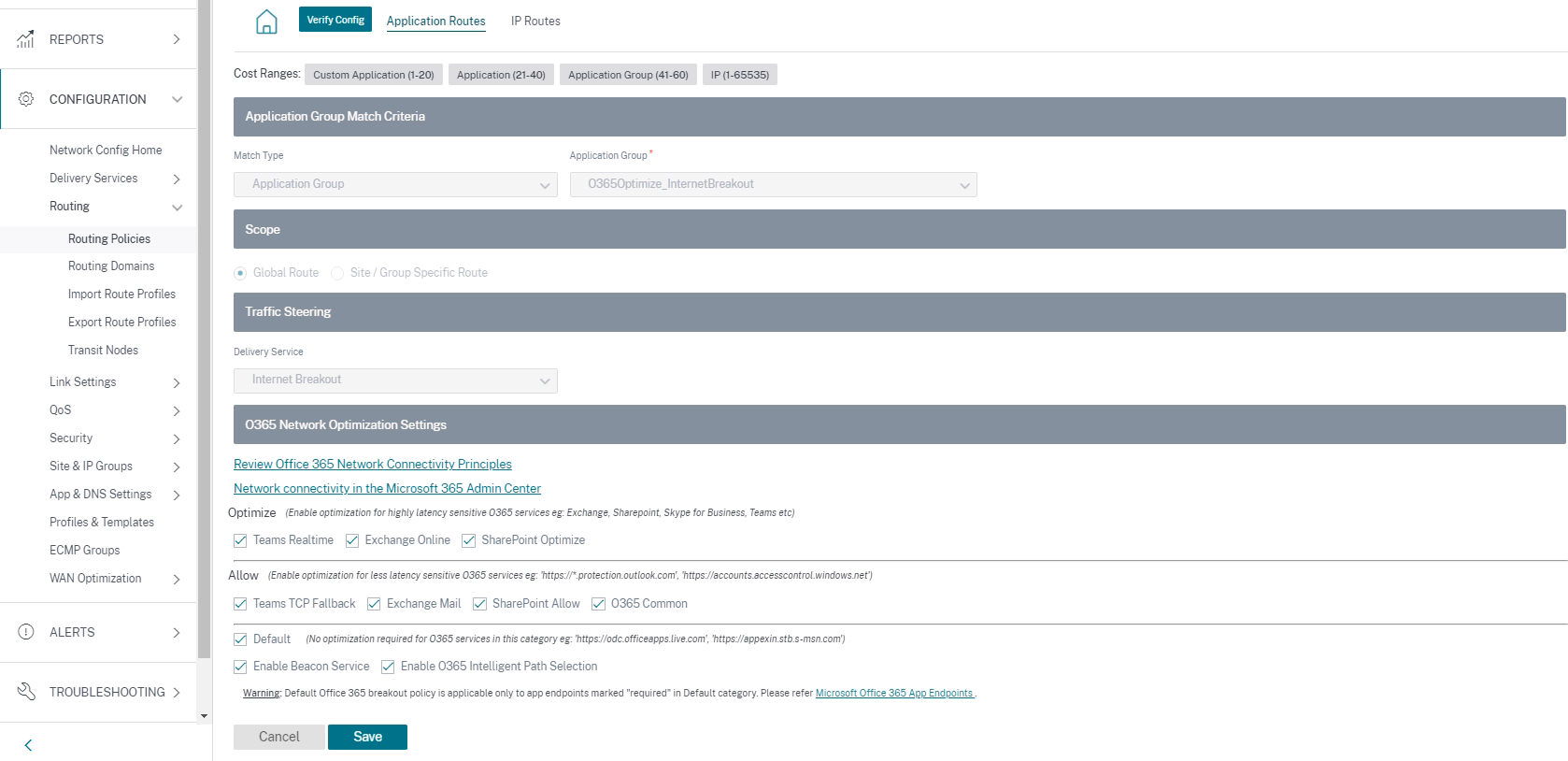
Click the office 365 rule to view the default settings Match Type, Application Group, Delivery Service, and so on. You cannot modify these default settings.
Office 365 endpoints are a set of network addresses and subnets. From Citrix SD-WAN 11.4.0 onwards, Office 365 endpoints are classified into Optimize, Allow, and Default categories. Citrix SD-WAN provides a more granular classification of the Optimize and Allow categories, enabling selective bookending to improve the performance of network-sensitive Office 365 traffic. Directing network-sensitive traffic to SD-WAN in the cloud (Cloud Direct or an SD-WAN VPX on Azure), or from an at-home SD-WAN device to an SD-WAN at a nearby location with more reliable Internet connectivity, enables QoS and superior connection resilience compared to simply steering the traffic to the nearest Office 365 front door, at the cost of an increase in latency. A bookended SD-WAN solution with QoS reduces VoIP dropouts and disconnects, reduces jitter and improves media-quality mean opinion scores for Microsoft Teams. Endpoints are segregated into the following three categories:
-
Optimize - These endpoints provide connectivity to every Office 365 service and feature, and are sensitive to availability, performance, and latency. It represents over 75% of Office 365 bandwidth, connections, and volume of data. All the Optimize endpoints are hosted in Microsoft data centers. Service requests to these endpoints must be breakout from the branch to the Internet and must not go through the data center.
The Optimize category is classified into the following subcategories:
- Microsoft Teams Realtime
- Exchange Online
- SharePoint Optimize
-
Allow - These endpoints provide connectivity to specific Office 365 services and features only, and are not so sensitive to network performance and latency. The representation of Office 365 bandwidth and connection count is also lower. These endpoints are hosted in Microsoft data centers. Service requests to these endpoints might be breakout from the branch to the Internet or might go through the data center.
The Allow category is classified into the following subcategories:
- Teams TCP Fallback
- Exchange Mail
- SharePoint Allow
- O365 Common
NOTE
The Teams Realtime subcategory uses the UDP real-time transport protocol to manage Microsoft Teams traffic, whereas the Teams TCP Fallback subcategory uses the TCP transport layer protocol. As media traffic is highly latency sensitive, you might prefer this traffic to take the most direct path possible and to use UDP instead of TCP as the transport layer protocol (most preferred transport for interactive real-time media in terms of quality). While UDP is a preferred protocol for Teams media traffic, it requires certain ports to be allowed in the firewall. If the ports are not allowed, Teams traffic uses TCP as a fallback, and enabling optimization for Teams TCP Fallback ensures better delivery of the Teams application in this scenario. For more information, see Microsoft Teams call flows.
-
Default - These endpoints provide Office 365 services that do not require any optimization, and can be treated as normal Internet traffic. Some of these endpoints might not be hosted in Microsoft data centers. The traffic in this category is not susceptible to variations in latency. Therefore, direct breaking out of this type of traffic does not cause any performance improvement when compared to Internet breakout. In addition, the traffic in this category may not always be Office 365 traffic, hence it is recommended to disable this option when enabling the Office 365 breakout in your network.
NOTE
By default, options of the Default category and the Optimize and Allow subcategories are disabled. You cannot delete these settings but can enable as needed.
-
Enable Beacon Service - Citrix SD-WAN allows you to perform beacon probing and determines the latency to reach Office 365 endpoints through each WAN link. Office 365 Beacon services are enabled by default. You can disable it by clearing this option. For more information, see Office 365 Beacon service.
-
Enable O365 Intelligent Path Selection - Citrix SD-WAN allows you to choose the best available WAN link to manage Office 365 traffic. For example, if there are 2 WAN links configured for an Internet service, out of which one WAN link has a higher latency and the other WAN link has a lower latency, enabling intelligent path selection would select the WAN link with the lowest latency provided, the probes from the WAN link are not lossy.
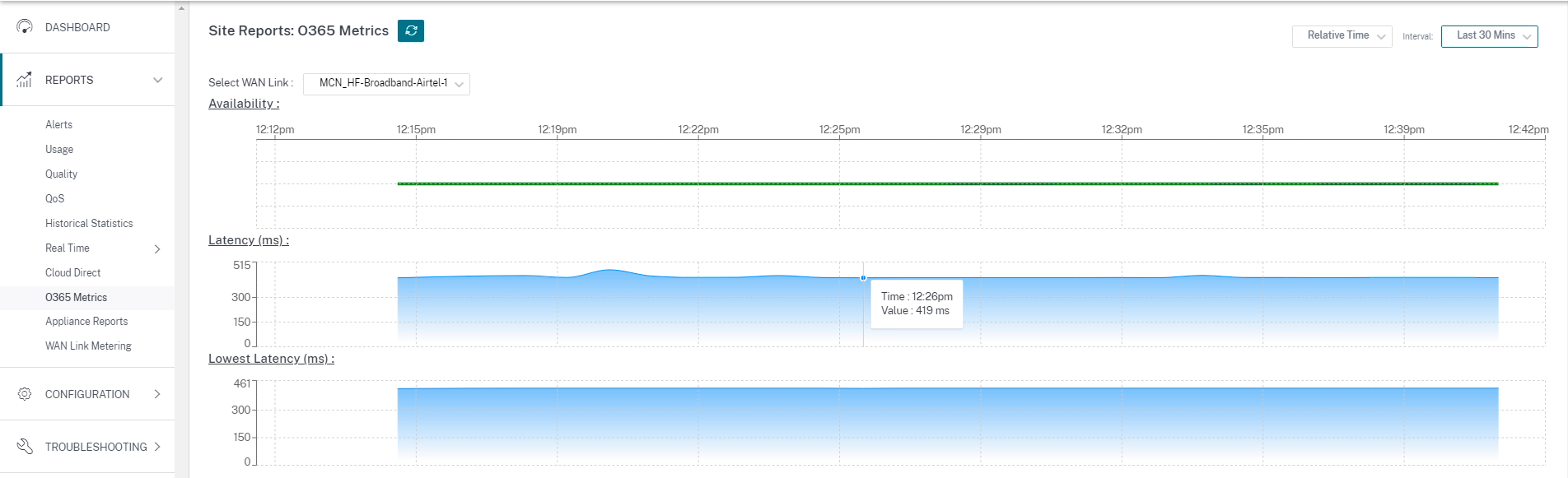
You can view details about the WAN links with lowest latency and the total decisions taken at O365 Metrics.
Note
If probes are lossy, Citrix SD-WAN uses the default Internet load-balancing logic to select the best WAN link although intelligent path selection is enabled.
Transparent forwarder for Office 365
The branch breaks out for Office 365 begins with a DNS request. The DNS request going through Office 365 domains have to be steered locally. If Office 365 Internet break out is enabled, the internal DNS routes are determined and the transparent forwarders list is auto populated. Office 365 DNS requests are forwarded to open source DNS service Quad 9 by default. Quad 9 DNS service is secure, scalable, and has multi pop presence. You can change the DNS service if necessary.
Transparent forwarders for Office 365 applications are created at every branch that has Internet service and office 365 breakout enabled.
If you are using another DNS proxy or if SD-WAN is configured as the DNS proxy, the forwarder list is auto populated with forwarders for Office 365 applications.
Important considerations for upgrade
Optimize and Allow categories
If you have enabled the Internet breakout policy for the Optimize and Allow Office 365 categories, Citrix SD-WAN automatically enables the Internet breakout policy for the corresponding subcategories upon upgrade to Citrix SD-WAN 11.4.0.
When you downgrade to a software version older than Citrix SD-WAN 11.4.0, you must manually enable Internet breakout for the Optimize or Allow Office 365 category irrespective of whether you enabled the corresponding subcategories in the Citrix SD-WAN 11.4.0 version or not.
Office 365 application objects
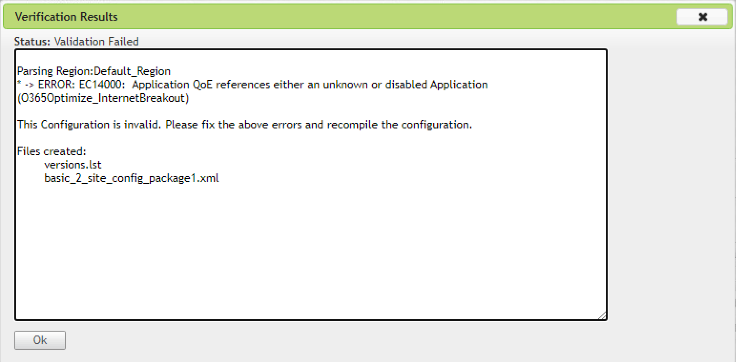
If you have created rules/routes using the O365Optimize_InternetBreakout and O365Allow_InternetBreakout auto-generated application objects, ensure to delete the rules/routes before upgrading to Citrix SD-WAN 11.4.0. After the upgrade, you can create rules/ routes using the corresponding new application objects.
If you proceed with Citrix SD-WAN 11.4.0 upgrade without deleting the rules/routes, you see an error and thus, the upgrade becomes unsuccessful. In the below example, a user has configured an Application QoE profile and is seeing an error while trying to upgrade to Citrix SD-WAN 11.4.0 without deleting the rules/routes:
Note
This upgrade is not required for auto-created rules/routes. It applies only to rules/ routes that you have created.
DNS
If you have created DNS Proxy rules or DNS transparent forwarder rules using the Office 365 Optimize and Office 365 Allow applications, ensure to delete the rules before upgrading to Citrix SD-WAN 11.4.0. After the upgrade, you can create the rules again using the corresponding new applications.
If you proceed with Citrix SD-WAN 11.4.0 upgrade without deleting the old DNS proxy or transparent forwarder rules, you do not see any error and upgrade becomes successful too. However, the DNS proxy rules and transparent forwarding rules do not take effect in Citrix SD-WAN 11.4.0.
Note
This activity does not apply to the auto-created DNS rules. It applies only to DNS rules that you have created.
Limitations
- If the Office 365 breakout policy is configured, deep packet inspection is not performed on connections destined to the configured category of IP addresses.
- The auto created firewall policy and application routes are uneditable.
- The auto created firewall policy has the lowest priority and is uneditable.
- The route cost for the auto created application route is five. You can override it with a lower cost route.
Office 365 beacon service
Microsoft provides the Office 365 beacon service to measure the Office 365 reachability through the WAN links. The beacon service is basically a URL - sdwan.measure.office.com/apc/trans.gif, which is probed at regular intervals. Probing is done on each appliance for every internet enabled WAN link. With each probe, an HTTP request is sent to the beacon service and an HTTP response is expected. The HTTP response confirms the availability and reachability of the Office 365 service.
Citrix SD-WAN allows you to not only perform beacon probing, but also determines the latency to reach Office 365 endpoints through each WAN link. The latency is the round trip time taken to send a request and get a response from the Office 365 beacon service over a WAN link. This enables network administrators to view the beacon service latency report and manually choose the best internet link for direct Office 365 breakout. Beacon probing is enabled only through Citrix SD-WAN Orchestrator. By default, beacon probing is enabled on all Internet enabled WAN links when Office 365 break-out is enabled through Citrix SD-WAN Orchestrator.
Note
Office 365 beacon probing is not enabled on metered links.
To disable Office 365 beacon service, in SD-WAN Orchestrator, at network level navigate to Configuration > Routing > Routing Policies > O365 Network Optimization Settings and clear Enable Beacon Service.
![]()
To view the beacon probing availability and latency reports, in Citrix SD-WAN Orchestrator, at network level navigate to Reports > O365 Metrics.
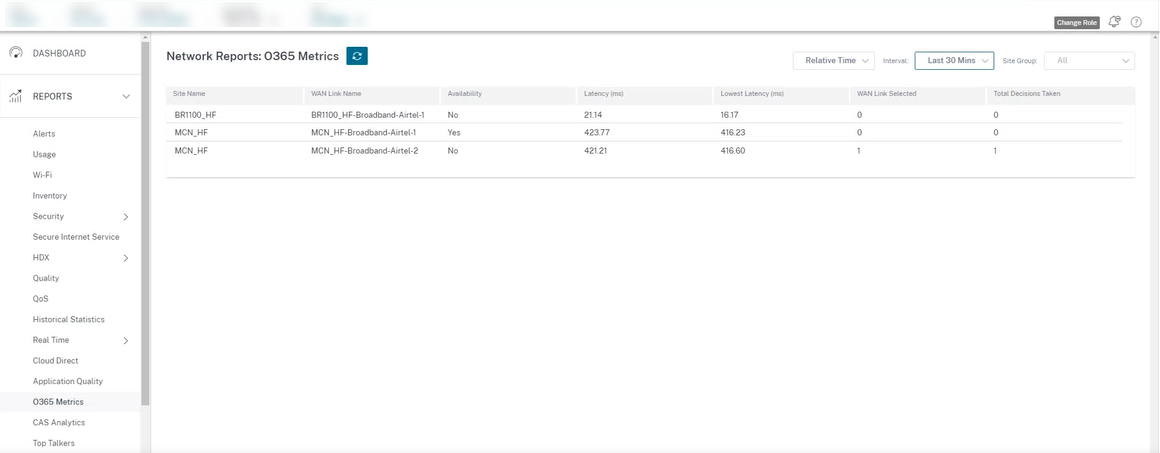
To view a detailed site level report of beacon service, in SD-WAN Orchestrator, at site level navigate to Reports > O365 Metrics.