Application settings and groups
This section enables users to custom define applications, group applications for use in policies, QoS Profiles, and also DNS settings.
You can define an Application Group for both predefined and custom applications. An Application Group contains applications that need similar treatment when defining a security policy.
You can reuse the Application Groups frequently when defining policies such as application steering or firewall rules. It eliminates the need to create multiple entries for each individual application. Similarly, while using any application services, Application Groups supports common applications with a unique name for simplified and consistent reuse.
To view Application Groups, navigate to Configuration > App Settings & Groups.
Domains and applications
You can create internal applications based on domain names which are not available in the list of published applications from the Domains & Apps page. To create applications based on domain name, at the network level, navigate to App Settings & Groups > Domains & Apps > Domain Name Based Apps tab, and click New Domain Name Based Application. Enter the application name and add the domain names or patterns. You can either enter the full domain name or use wild cards at the beginning.
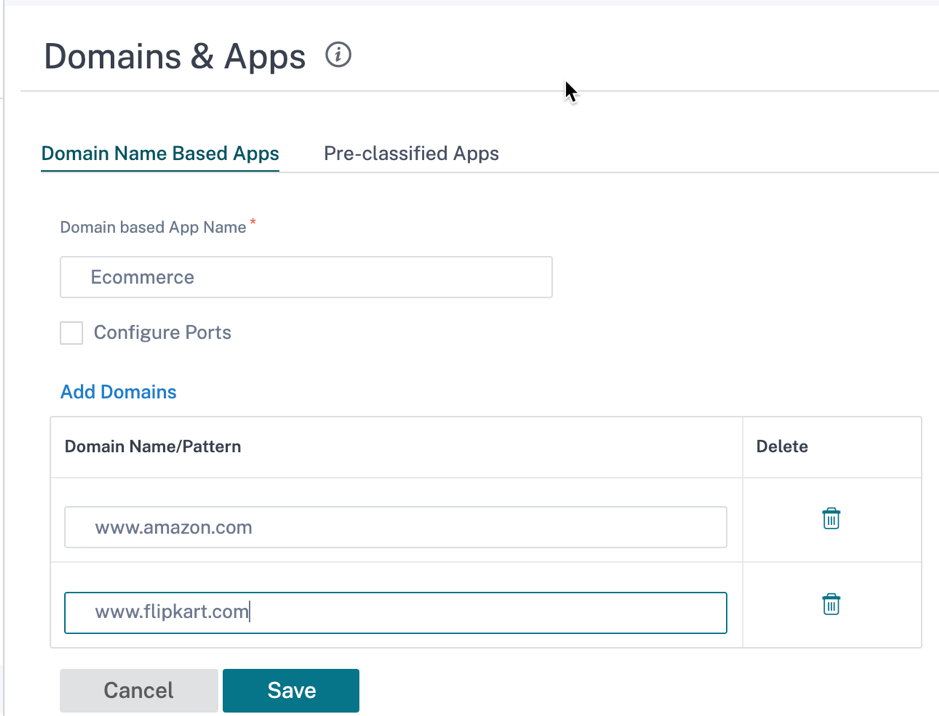
All the domain name based applications are visible in Application Routing, Application Rule, and Firewall Policies.
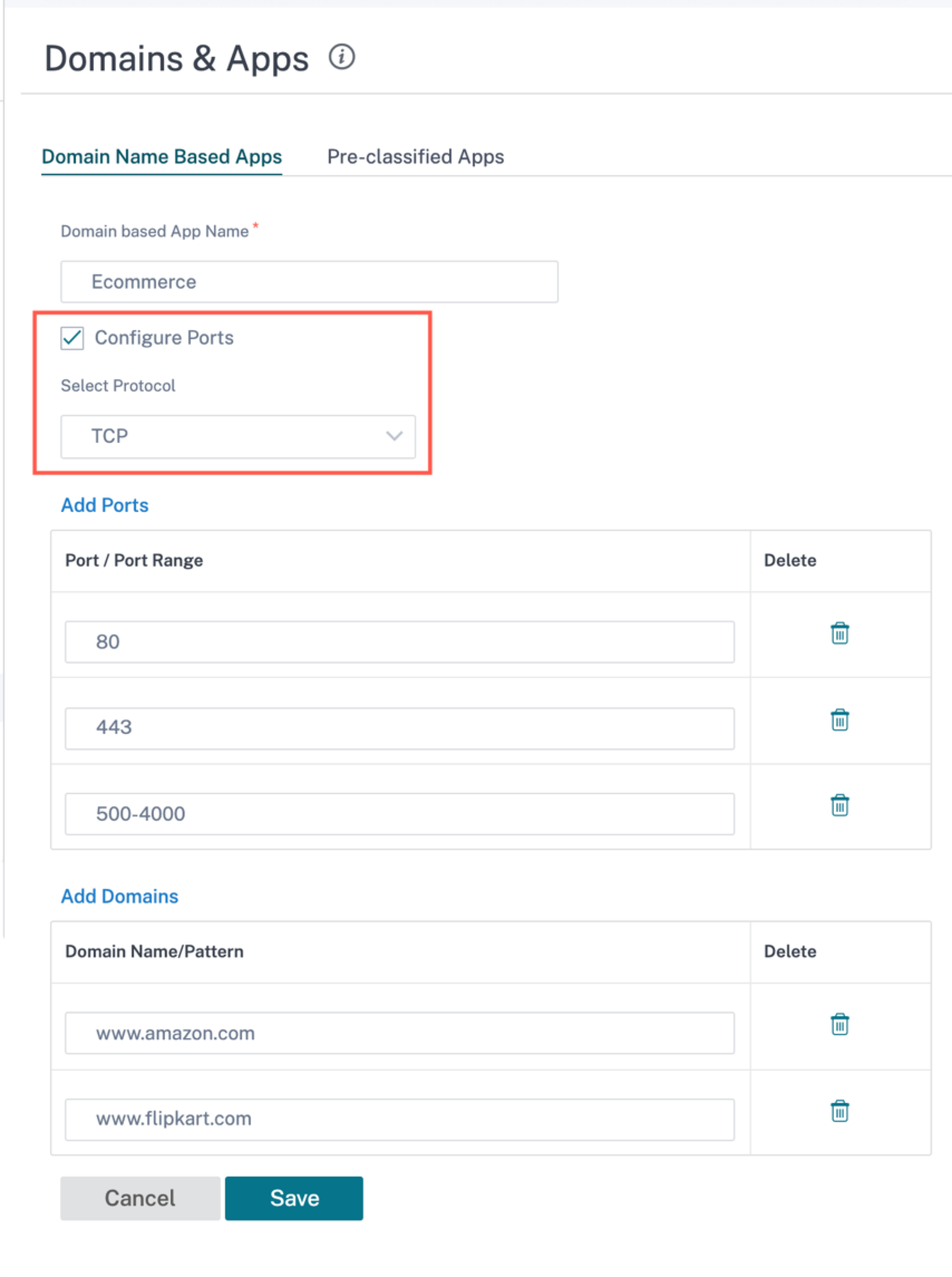
From Citrix SD-WAN 11.4.2 release onwards, the Configure Ports check box option is made available under Domain Name Based Applications. When the Configure Ports check box is enabled, it presents the flexibility to configure a group of multiple ports, port-ranges, and a protocol (TCP/UDP/Any) for the domain-based application.
Previously, ports 80 and 443, and protocol Any were supported for domains grouped under an application. You can see the same behavior if the Configure Ports check box is cleared. By default, the Configure Ports check box is disabled.
When you select the Configure Port check box, you can edit, add, or delete any port or the port range as required along with the protocol selection as TCP, UDP, or Any. By default, the protocol value is set to Any and the ports are set to 80 and 443.
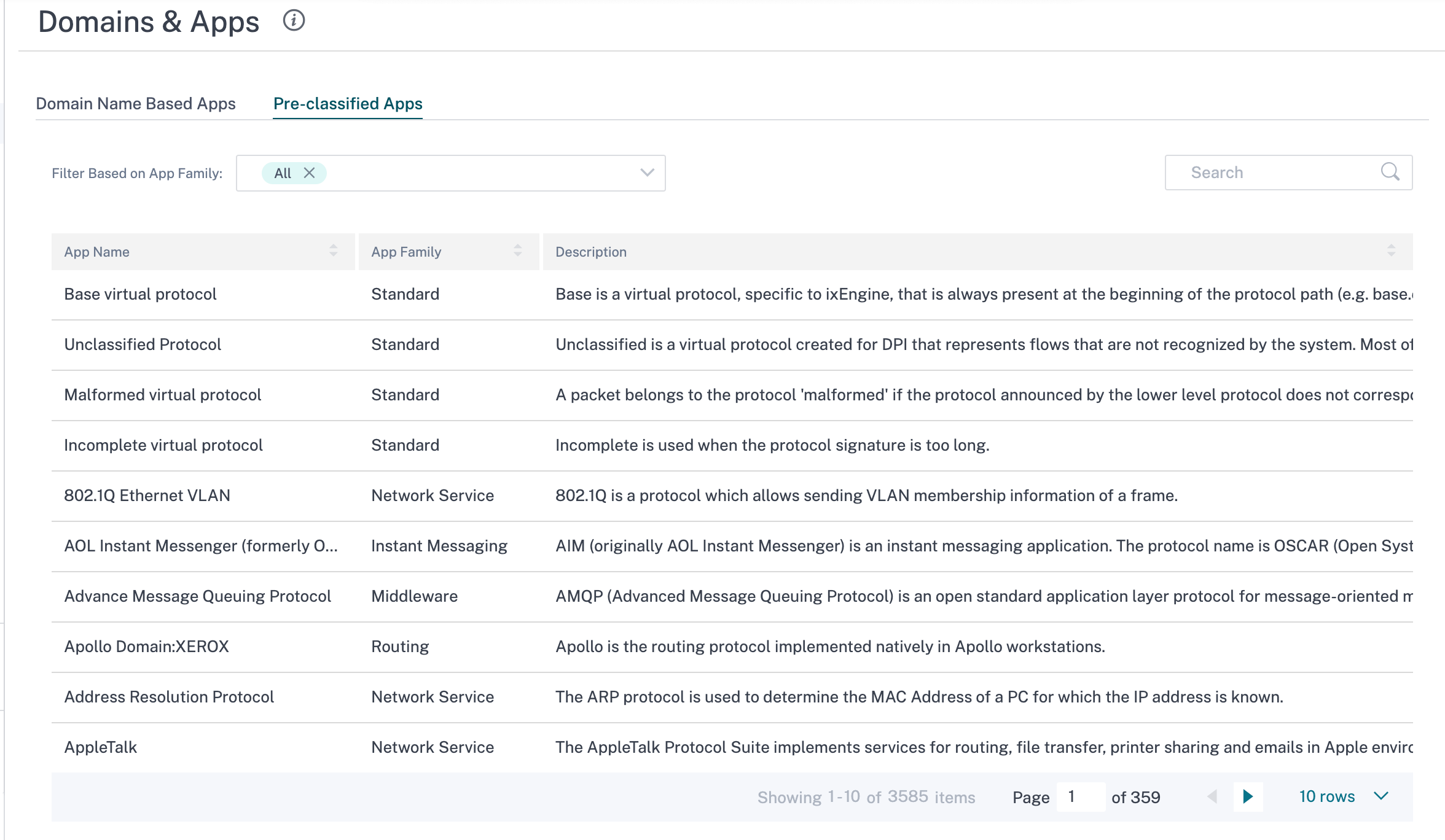
You can also view the list of pre-defined applications under the Pre-classified Apps tab. You can search for a specific application using the Search bar or filter the list based on the application family.
Custom application
The Custom Applications are used to create internal applications or IP-port combinations which are not available in the list of published applications. The administrator needs to define a custom application based on the IP protocol that can be used in multiple policies as needed, without referring the IP address and port number details each time.
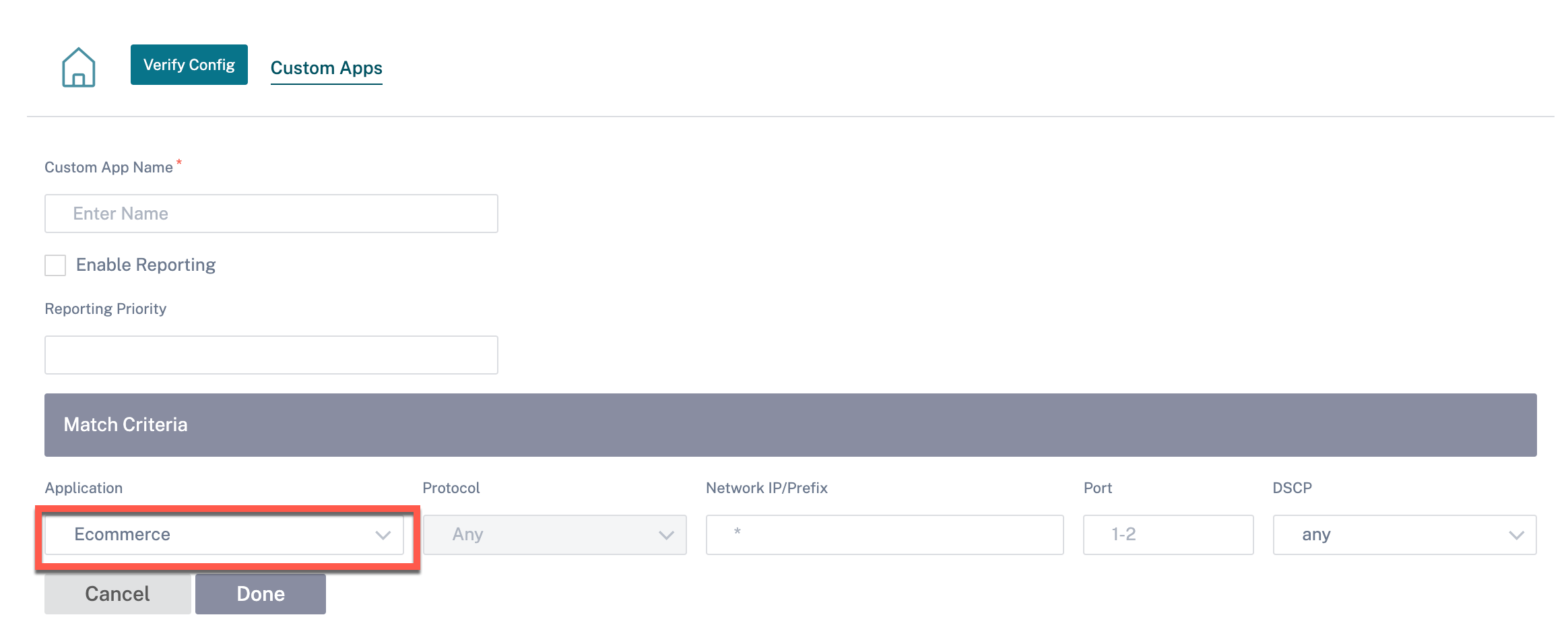
To create a custom application, at the network level, navigate to App Settings & Groups > Custom Apps, click + Custom Application and provide a name for the custom application. Specify the match criteria such as IP protocol, network IP address, port number, and, DSCP tag. The data flow matching this criteria is grouped as the custom application.
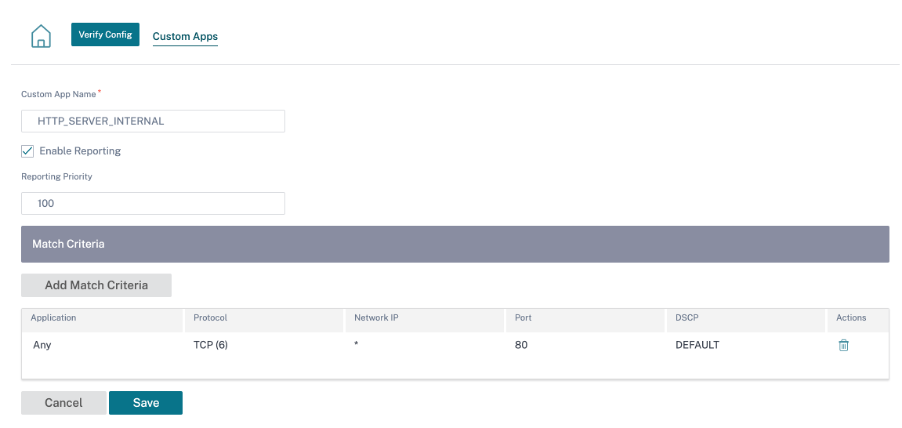
Once saved, the custom applications show up in a list and can be edited or deleted, as required.
The Enable Reporting check box is added for the IP Protocol-based custom applications and application groups. You must select the Enable Reporting check box and provide the reporting priority.
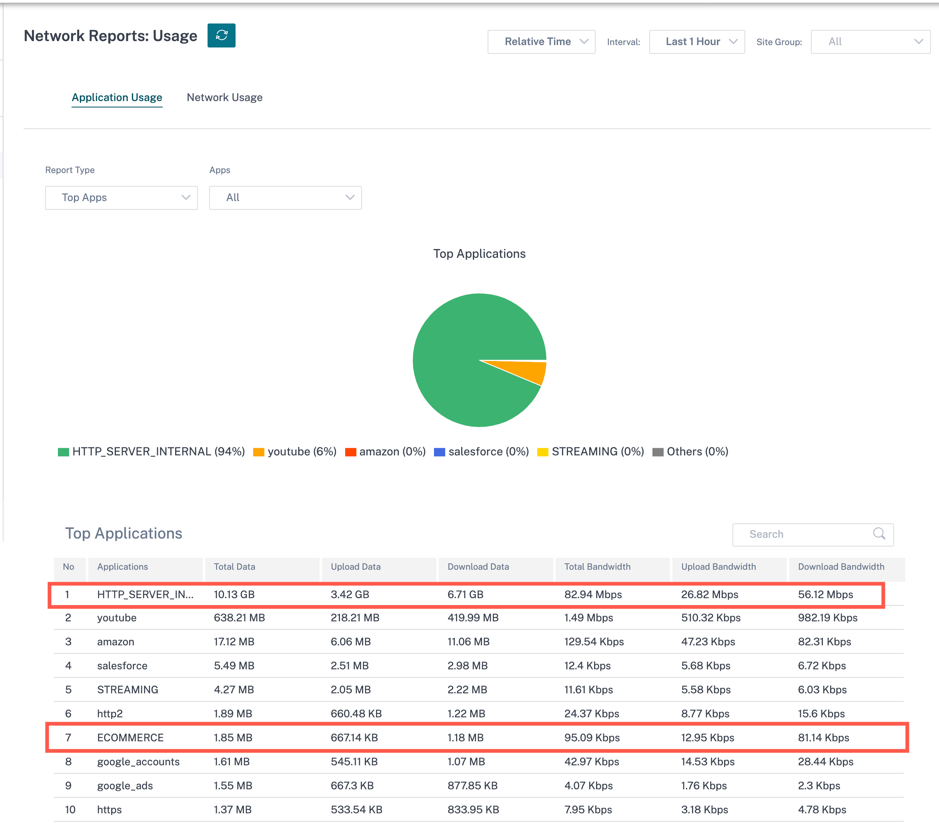
When the Enable Reporting check box is selected, you can view the IP custom application traffic under Reports > Usage.
Reporting priority is the order in which IP protocol-based custom applications or application groups are selected for the reporting. It helps to choose the high-priority custom application or application group for reporting, when there are multiple matches with reporting enabled. For example, if the reporting priority of a custom application is set to 1, it means that the custom application gets the highest priority in reporting. Whereas if the reporting priority is set to 100, the custom application takes a much lesser precedence in reporting.
Note
- For you to use a domain name-based application, Apps & Domains must be listed as the match criteria while creating the Application Route, QoS policy, and firewall policy.
- For you to use a custom application, Custom Application must be listed as the match criteria while creating the Application Route, QoS policy, and firewall policy.
Once you have created the custom application, to perform the application routing, navigate to Routing > Routing Policies > + Application Route, select Custom Application from the Match Type drop-down list. Similarly for the domain name-based application, select Apps & Domains from the Match Type drop-down list.
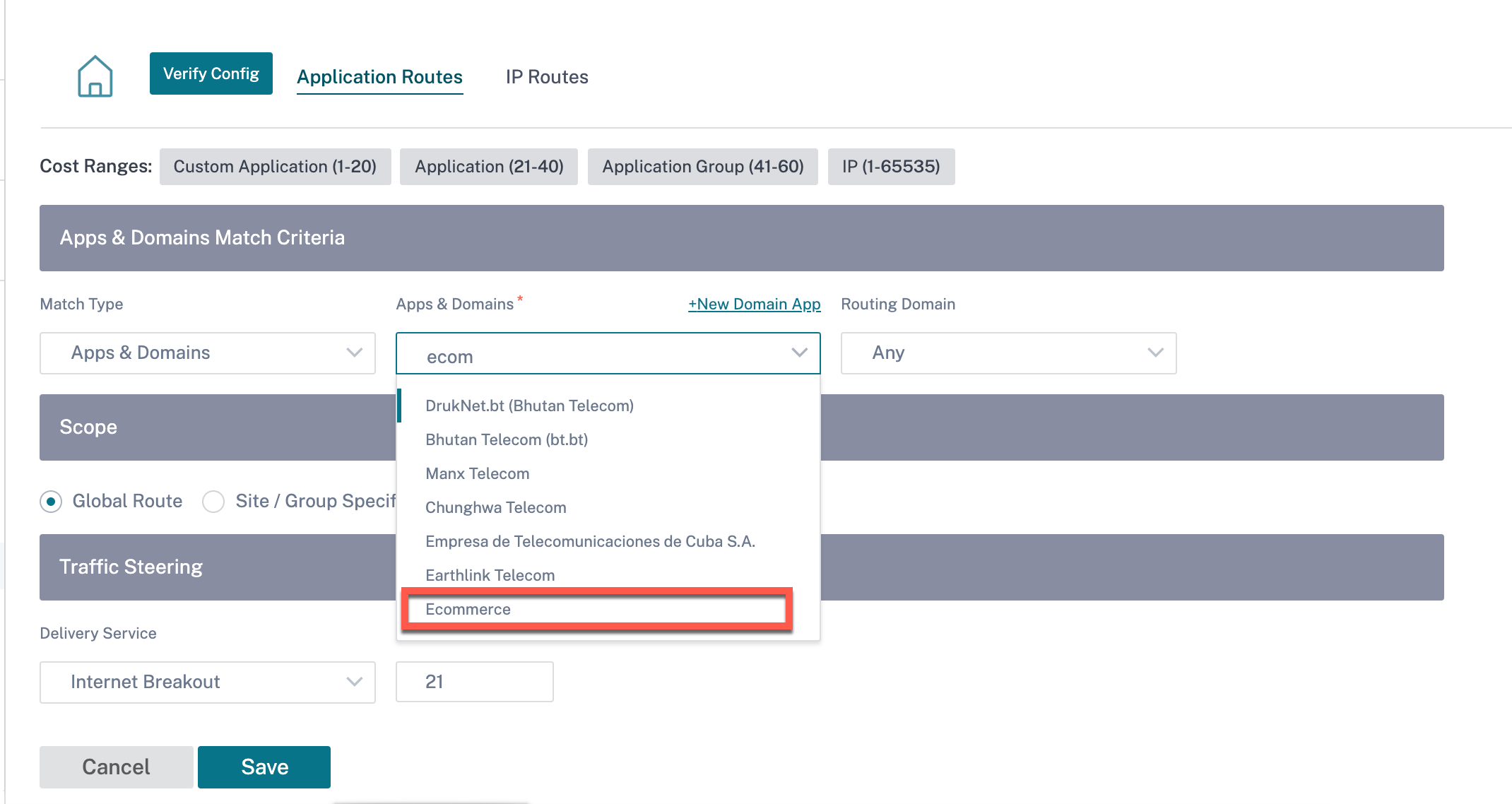
You can also select a domain name-based application under the match criteria while creating an IP Protocol custom application.
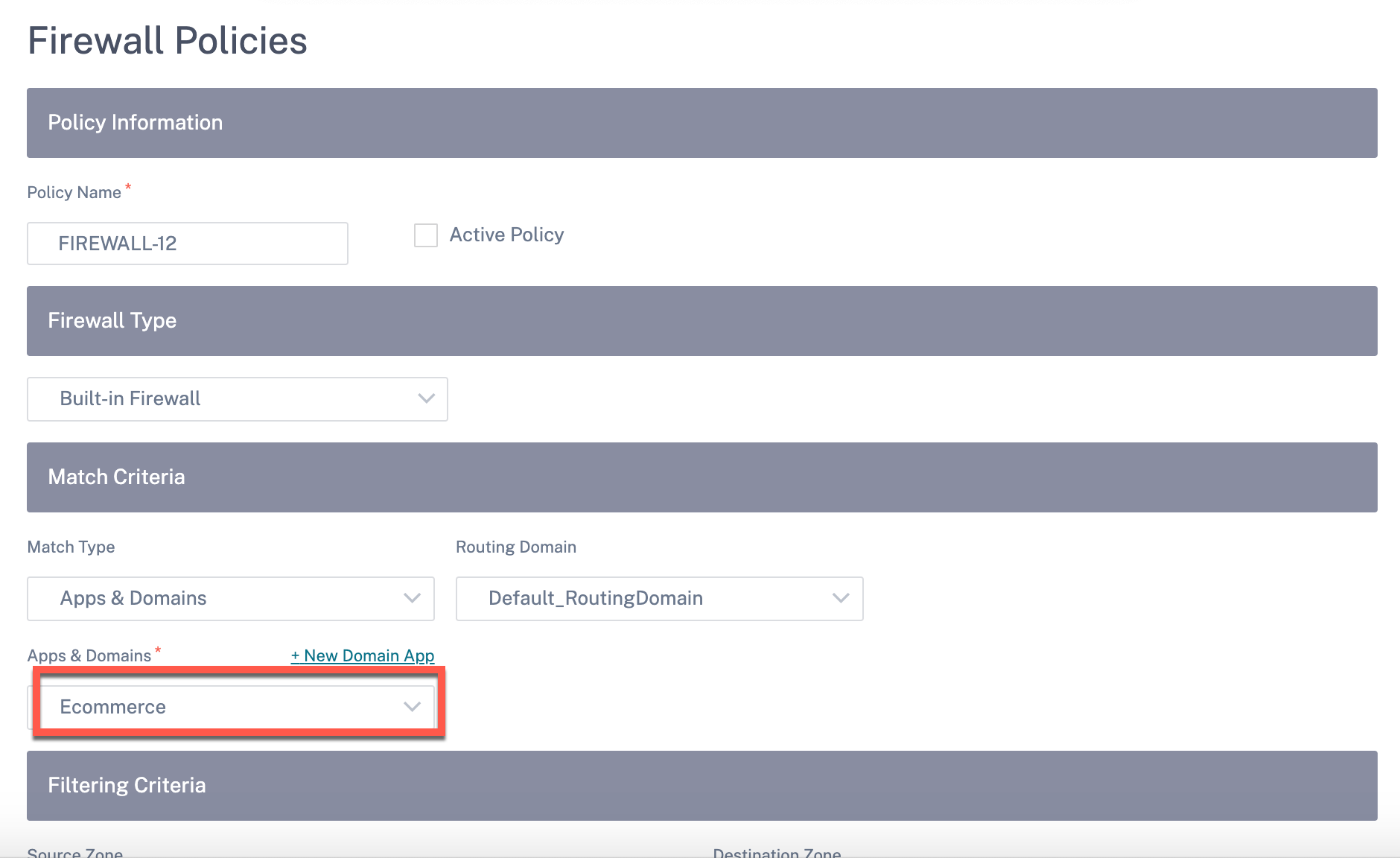
Similarly, to view the custom application under the Firewall Policies, navigate to Security > Firewall Policies. The application can be used for any type of policy (Global override/Site Specific/Global Policies). Click Create New Rule and under Match Criteria, select Custom Application from the Match Type drop-down list. To view the domain name-based application, select Apps & Domains from the Match Type drop-down list.
You can view the domain name-based custom applications both under Global or Site/Group Specific Rule. To view the domain name-based applications, navigate to QoS > QoS Policies > Global Rules > Application Rule > + Application Rule, and select the required domain name-based application from the Apps & Domains drop-down list. To view custom applications, navigate to QoS > QoS Policies > Global Rules > Custom Application Rules > + Custom Application Rule, and select the required custom application from the Custom Application drop-down list.
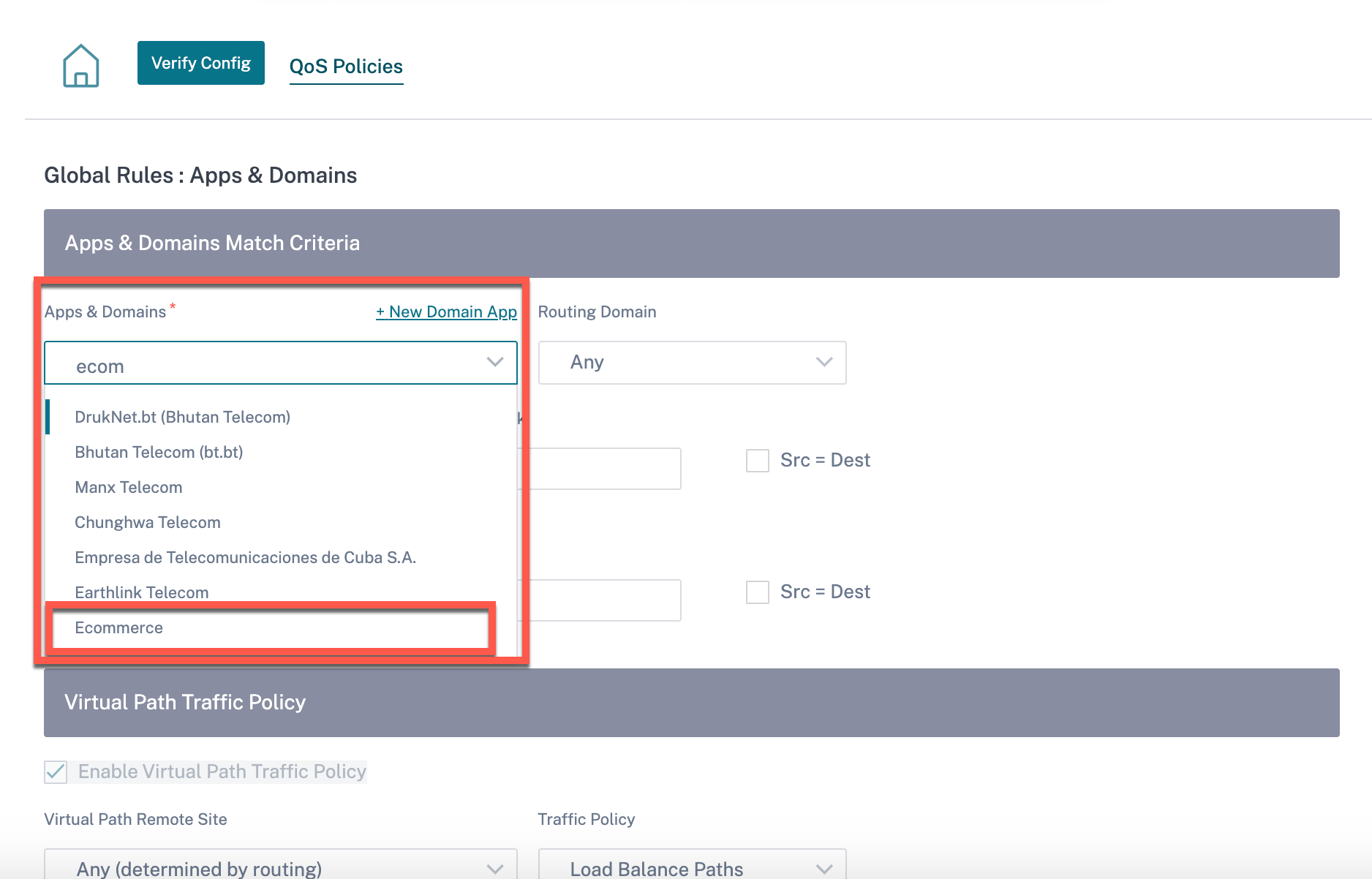
Click Verify Config to validate any audit error.
Application groups
An Application Group helps administrators group similar applications together for use in common policies, without necessarily having to create a policy for each individual application.
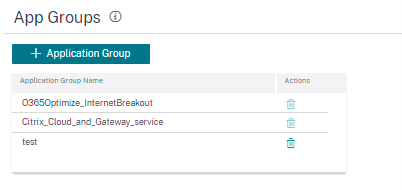
You can create an Application Group by using the Add Application Groups option. You can refer the same Application Group while creating a policy as per the application role. The policy that is defined for the particular group is applied to each application that matches to the specific category.
For example, you can create an Application Group as Social Networking and add social networks such as Facebook, LinkedIn, and Twitter to the group to define certain policies for social networking applications.
To create an Application Group, specify a group name, search, and add apps from the Applications list. You can always go back and edit your settings or delete Application Group as needed.
Click Verify Configuration on the Configuration > App Settings and Groups > App Groups page to validate any audit error.
Application quality profiles
This section enables you to view and create application quality profiles.
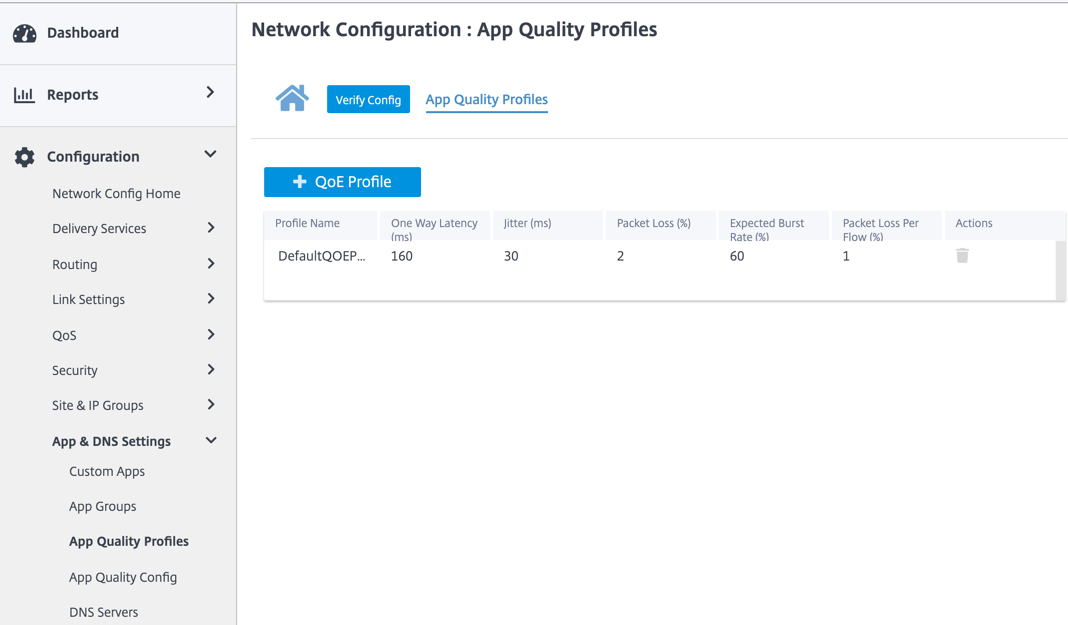
Application QoE is a measure of Quality of Experience of applications in the SD-WAN network. It measures the quality of applications that flow through the virtual paths between two SD-WAN appliances.
The Application QoE score is a value between 0 and 10. The score range that it falls in determines the quality of an application.
| Quality | Range |
|---|---|
| Good | 8–10 |
| Fair | 4–8 |
| Poor | 0–4 |
Application QoE score can be used to measure the quality of applications and identify problematic trends.
Profile configuration
Click + QoE Profile to create a QoE profile, specify a profile name, and select a traffic type from the drop-down list.
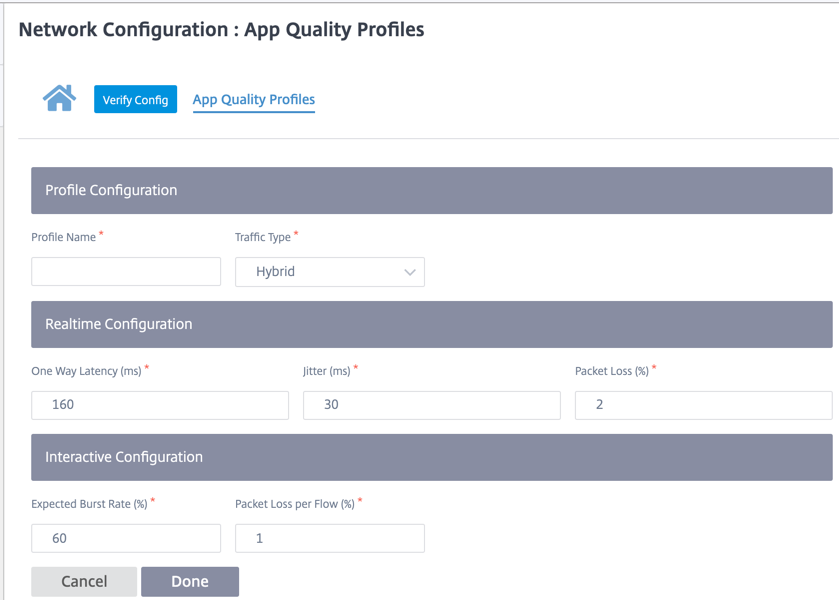
Real-time configuration
You can define the quality thresholds for real-time and interactive appliances using QoE profiles, and map these profiles to applications or applications objects.
The Application QoE calculation for real-time applications uses a Citrix® innovative technique, which is derived from the MOS score.
The default threshold values are:
- Latency threshold (ms): 160
- Jitter Threshold (ms): 30
- Packet loss threshold (%): 2
A flow of a real-time application that meets the thresholds for latency, loss, and jitter is considered to be of good quality.
QoE for Real-time applications is determined from the percentage of flows that meet the threshold divided by the total number of flow samples.
QoE for Real-time = (No of flow samples that meet the threshold / Total no of flow samples) * 100
It is represented as QoE score ranging from 0 to 10.
Interactive configuration
The Application QoE for interactive applications uses a Citrix innovative technique based on packet loss and burst rate thresholds.
Interactive applications are sensitive to packet loss and throughput. Therefore, we measure the packet loss percentage, and the burst rate of ingress and egress traffic in a flow.
The configurable thresholds are:
- Packet loss percentage.
- Percentage of expected egress burst rate in comparison to the ingress burst rate.
The default threshold values are:
- Packet loss threshold: 1%
- Burst rate: 60%
A flow is of good quality if the following conditions are met:
-
The percentage loss for a flow is less that the configured threshold.
-
The egress burst rate is at least the configured percentage of ingress burst rate.
Application quality configuration
Map application or application objects to default or custom QoE profiles. You can create custom QoE profiles for real-time and interactive traffic.
Click +QoE Configuration to create custom QoE profiles:
- Type: Select the DPI application or an application object (Application, Custom Apps, and Application Groups).
- Application: Search and select an application or application object based on the selected Type.
- QoE Profile: Select a QoE profile to map to the application or application object.
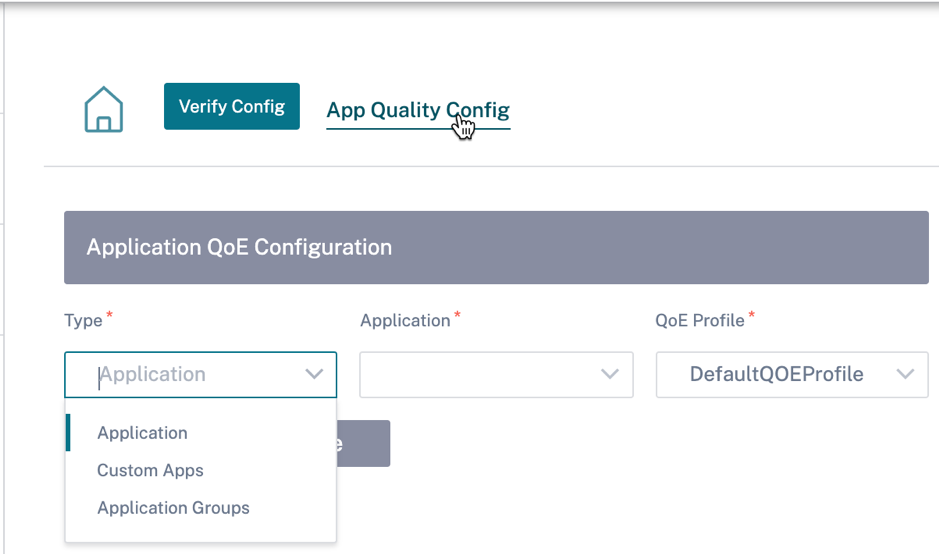
Click Done.
Click Verify Config to validate any audit error.
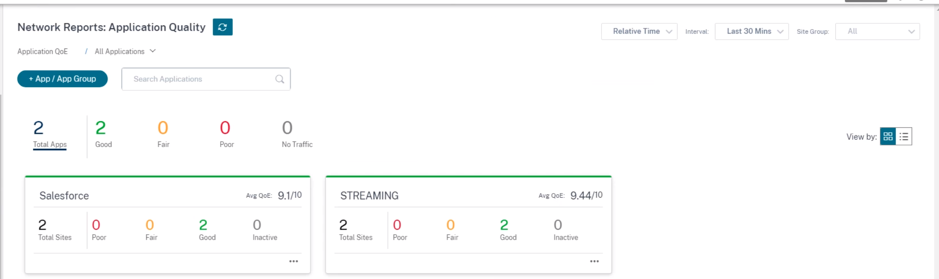
Once you configure the application QoE with the custom application type, a relevant application report tile is auto generated under the Reports > Application Quality. Any traffic that is matching with the selected application goes over the virtual path for the custom application.
Proxy Auto Config
With the increase in enterprise adoption of mission-critical SaaS applications and distributed workforce, it becomes highly critical to reduce latency and congestion. Latency and congestion are inherent in traditional methods of backhauling traffic through the Data Center. Citrix SD-WAN allows direct internet break out of SaaS applications such as Office 365. For more information, see Office 365 Optimization.
If there are explicit web proxies configured on the enterprise deployment all traffic are steered to the web proxy making it difficult for classification and direct internet breakout. The solution is to exclude SaaS application traffic from getting proxied by customizing the enterprise PAC (Proxy Auto-Config) file.
Citrix SD-WAN 11.0 allows proxy bypass and local Internet breakout for Office 365 application traffic by dynamically generating and serving a custom PAC file. PAC file is a JavaScript function that defines whether web browser requests go directly to the destination or to a web proxy server.
How PAC file customization works
Ideally, the enterprise network host PAC file on the internal web server, these proxy settings are distributed via group policy. The Client browser requests for PAC files from the enterprise web server. The Citrix SD-WAN™ appliance serves the customized PAC files for sites where Office 365 breakout is enabled.
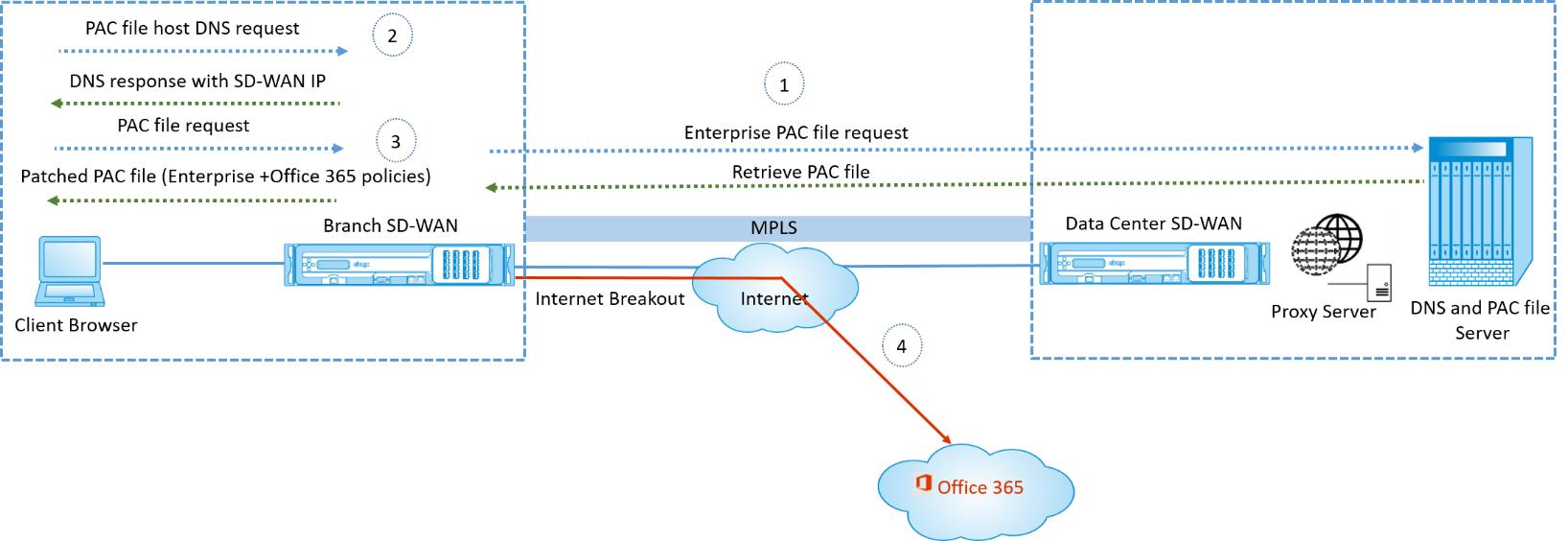
-
Citrix SD-WAN periodically requests and retrieves the latest copy of the enterprise PAC file from the enterprise web server. The Citrix SD-WAN appliance patches office 365 URLs to the enterprise PAC file. The enterprise PAC file is expected to have a placeholder (SD-WAN specific tag) where the Office 365 URLs are seamlessly patched.
-
The Client browser raises a DNS request for the enterprise PAC file host. Citrix SD-WAN intercepts the request for the proxy configuration file FQDN and responds with the Citrix SD-WAN VIP.
-
The Client browser requests for the PAC file. Citrix SD-WAN appliance serves the patched PAC file locally. The PAC file includes enterprise proxy configuration and Office 365 URL exclusion policies.
-
On receiving a request for the Office 365 application, the Citrix SD-WAN appliance performs a direct internet breakout.
Prerequisites
-
The enterprises must have a PAC file hosted.
-
The PAC file must have a placeholder SDWAN_TAG or one occurrence of the
findproxyforurlfunction for patching Office 365 URLs. -
The PAC file URL must be domain based and not IP based.
-
The PAC file is served only over the trusted identity VIPs.
-
Citrix SD-WAN appliance must be able to download the enterprise PAC file over its management interface.
Configure Proxy Auto Config
In the Citrix SD-WAN Orchestrator service UI, at the network level, navigate to Configuration > App Setting & Groups > Proxy Auto Config and click + PAC file profile.
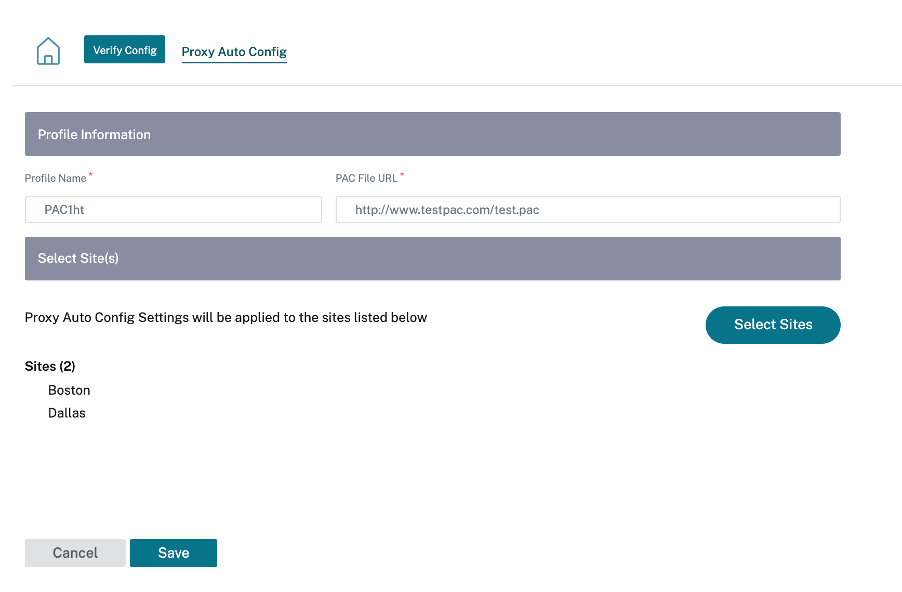
Enter a name for the PAC file profile, provide the URL of the enterprise PAC file server. The Office 365 breakout rules are dynamically patched to the enterprise PAC file.
Select the sites to which the PAC file profile is applied. If there are different URLs for each site, create a different profile per site.
Limitations
-
HTTPS PAC file server requests are not supported.
-
Multiple PAC files in a network are not supported, including PAC files for routing domains or security zones.
-
Generating a PAC file on Citrix SD-WAN from scratch is not supported.
-
WPAD through DHCP is not supported.
DPI Settings
The Citrix SD-WAN appliances perform Deep Packet Inspection (DPI) to identify and classify applications. The DPI library recognizes thousands of commercial applications. It enables real-time discovery and classification of applications. Using the DPI technology, the SD-WAN appliance analyses the incoming packets and classifies the traffic as belonging to a particular application or application family.
DPI is enabled globally, by default, for all the sites in your network. Disabling DPI stops DPI classification capability on the appliance. You can no longer use DPI classified application / application categories to configure firewall, QoS, and routing policies. You will also not be able to view the top applications and application categories report.
To disable global DPI, at the Network level, navigate to Configuration > App Settings & Groups > DPI Settings and clear the Enable Global DPI check box option.
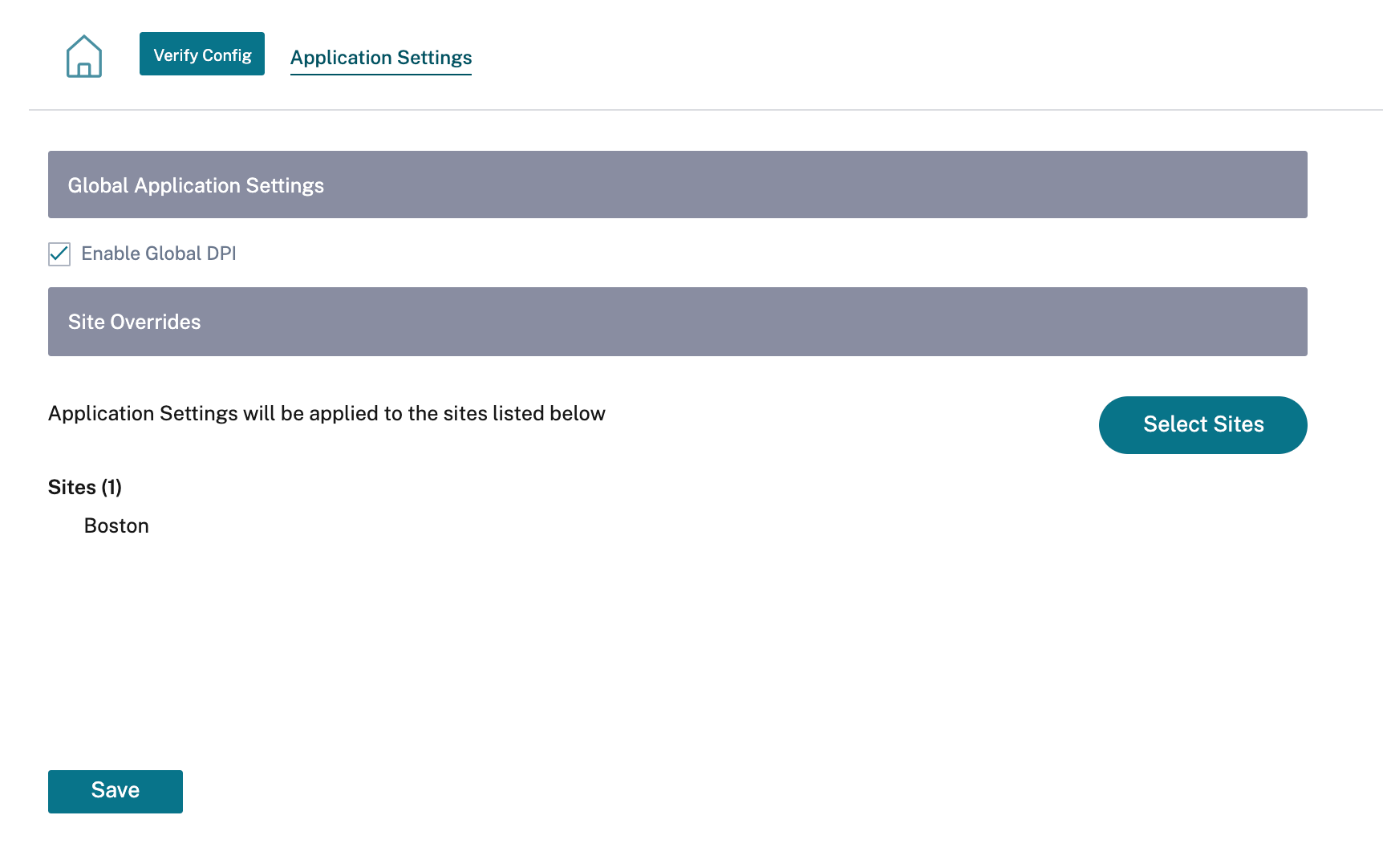
You can also choose to disable DPI for certain sites only by overriding the global DPI settings. To disable DPI for selected sites, add the sites to the Site Overrides list.