Palo Alto Networks firewall integration on SD-WAN 1100 platform
Citrix SD-WAN™ supports hosting Palo Alto Networks Next-Generation Virtual Machine (VM)-Series Firewall on the SD-WAN 1100 platform. The following are the supported virtual machine models:
- VM 50
- VM 100
The Palo Alto Network virtual machine series firewall runs as a virtual machine on SD-WAN 1100 platform. The firewall virtual machine is integrated in Virtual Wire mode with two data virtual interfaces connected to it. Required traffic can be redirected to the firewall virtual machine by configuring policies on SD-WAN.
Benefits
The following are the primary goals or benefits of Palo Alto Networks integration on the SD-WAN 1100 platform:
-
Branch device consolidation: A single appliance that does both SD-WAN and advanced security
-
Branch office security with on-prem NGFW (Next Generation Firewall) to protect LAN-to-LAN, LAN-to-Internet, and Internet-to-LAN traffic
Configuration steps
The following configurations are needed to integrate the Palo Alto Networks virtual machine on SD-WAN:
-
Provision the Firewall Virtual Machine
-
Enable traffic redirection to Security Virtual Machine
Note
Firewall virtual machine must be provisioned first before enabling the traffic redirection.
Provisioning Palo Alto Network virtual machine
There are two ways to provision the firewall virtual machine:
-
Provisioning through SD-WAN Center
-
Provisioning through SD-WAN appliance GUI
Firewall virtual machine provisioning through SD-WAN Center
Prerequisites
-
Add the secondary storage to SD-WAN Center to store the Firewall VM image files. For more information, see System requirements and installation.
-
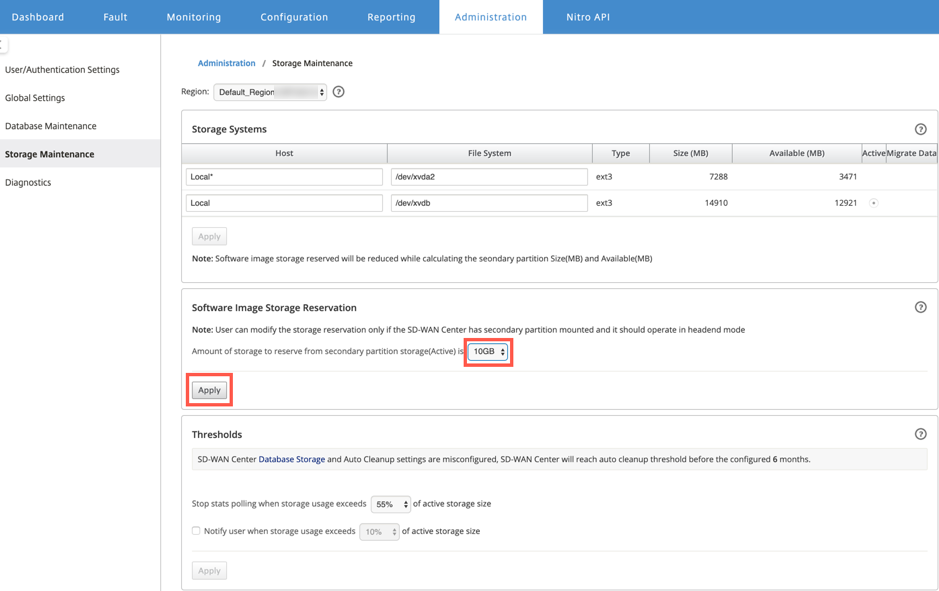
Reserve the storage from the secondary partition for the Firewall VM image files. To configure the storage limit, navigate to Administration > Storage Maintenance.
-
Select the required storage amount from the list.
-
Click Apply.
-
Note
Storage is reserved from the secondary partition which is active if the condition is met.
Perform the following steps for provisioning the firewall virtual machine through SD-WAN Center platform:
-
From Citrix SD-WAN Center GUI, navigate to Configuration > select Hosted Firewall.
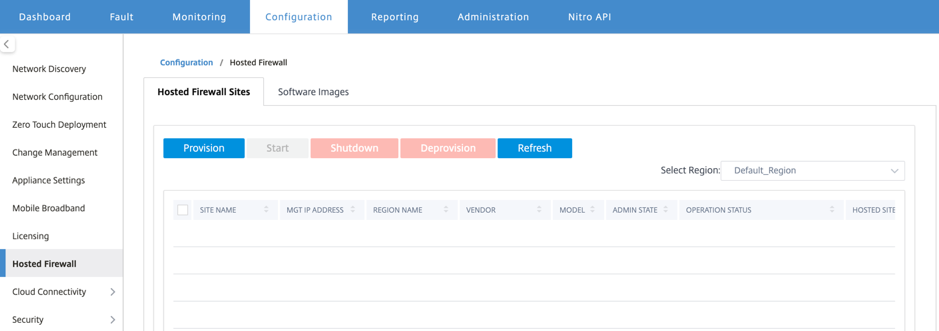
You can select the Region from the drop-down list to view the provisioned site details for that selected region.
-
Upload the software image.
Note
Ensure that you have enough disk space to upload the software image.
Navigate to Configuration > Hosted Firewall > Software Images and select the Vendor name as Palo Alto Networks from the drop-down list. Click or drop the software image file in the box to upload.
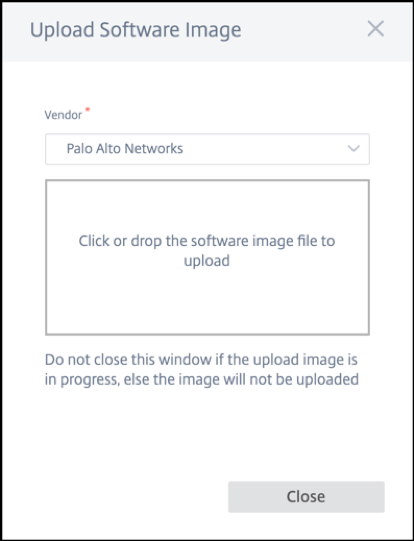
A status bar appears with the ongoing upload process. Do not click Refresh or perform any other action until the image file shows 100% uploaded.
-
Refresh: Click the Refresh option to get the latest image file details.
-
Delete: Click the Delete option to delete any existing image file.
Note
-
To provision firewall virtual machine on the sites part of non-default region, upload the image file on each of the collector node.
-
Deleting the Palo Alto VM image from SDWAN Center, will delete the image from the SDWAN Center storage, and NOT from the appliance.
-
-
For provisioning, go back to Hosted Firewall Sites tab and click Provision.
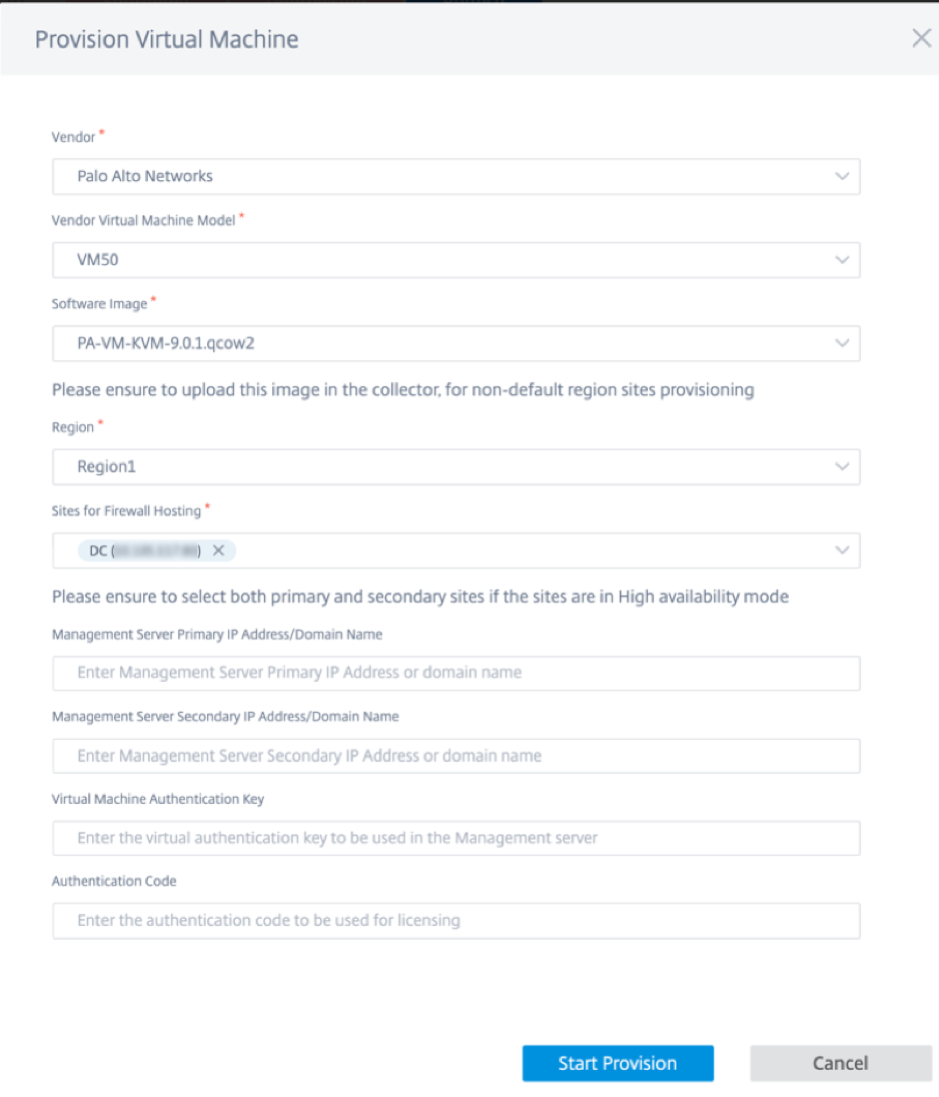
- Vendor: Select the vendor name as Palo Alto Networks from the drop-down list.
- Vendor Virtual Machine Model: Select the virtual machine model number from the list.
- Software Image: Select the Image file to provision.
- Region: Select the region from the list.
-
Sites for Firewall Hosting: Select sites for the list for firewall hosting. You must select both primary and secondary sites if the sites are in high availability mode.
- Management Server Primary IP Address/Domain Name: Enter the management primary IP address or fully qualified domain name (Optional).
-
Management Server Secondary IP Address/Domain Name: Enter the management server secondary IP address or fully qualified domain name (Optional).
-
Virtual Machine Authentication Key: Enter the virtual authentication key to be used in the management server.
- Authentication Code: Enter the virtual authentication code to be used for licensing.
- Click Start Provision.
- Click Refresh to get the latest status. After the Palo Alto Networks virtual machine is completely bootup, it will reflect on the SD-WAN Center UI.
You can Start, Shutdown, and Deprovision the virtual machine as needed.
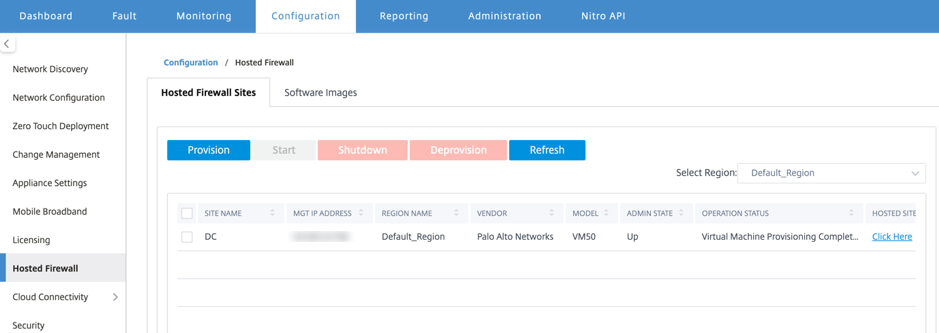
- Site Name: Displays the site name.
- Management IP: Displays the management IP address of the site.
- Region Name: Displays the region name.
- Vendor: Displays the vendor name (Palo Alto Networks).
- Model: Displays the model number (VM50/VM100).
- Admin State: State of the vendor virtual machine (Up/Down).
- Operation Status: Displays the operational status message.
- Hosted Site: Use the Click Here link to access the Palo Alto Networks virtual machine GUI.
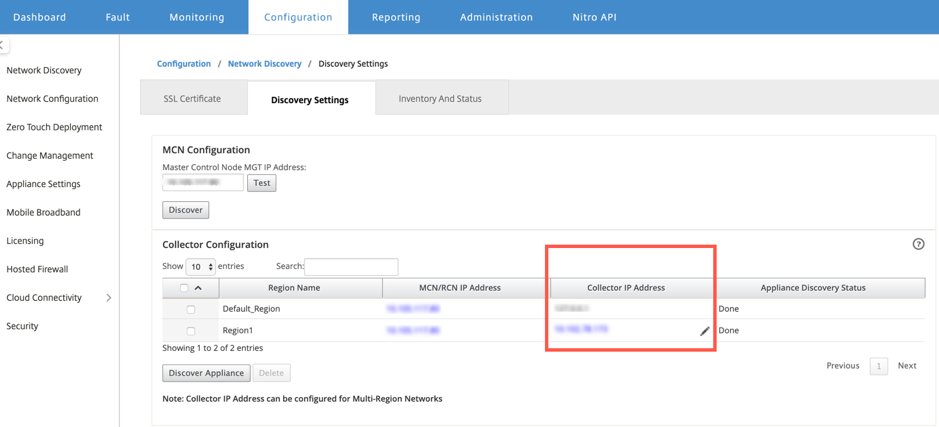
To provision the non-default region sites, you need to upload the software image on the SD-WAN Center Collector. You can provision the Palo Alto Networks both from SD-WAN Center head end GUI or SD-WAN Center Collector.
To get the SD-WAN Center Collector’s IP address, navigate to Configuration > Network Discovery > select Discovery Settings tab.
To provision the Palo Alto Networks from SD-WAN Collector:
-
From SD-WAN Collector GUI, navigate to Configuration > select Hosted Firewall.
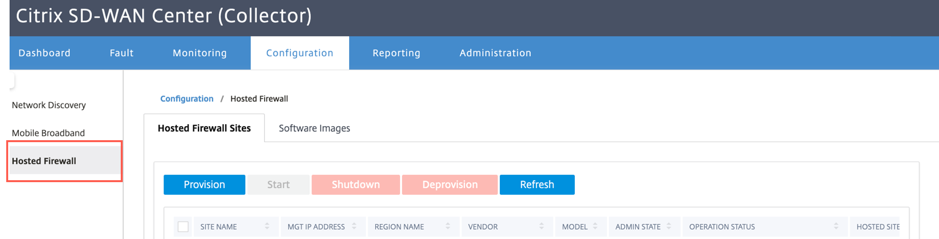
- Go to Software Images tab to upload the software image.
- Click Provision under Hosted Firewall Sites tab.
-
Provide the following details and click Start Provision.
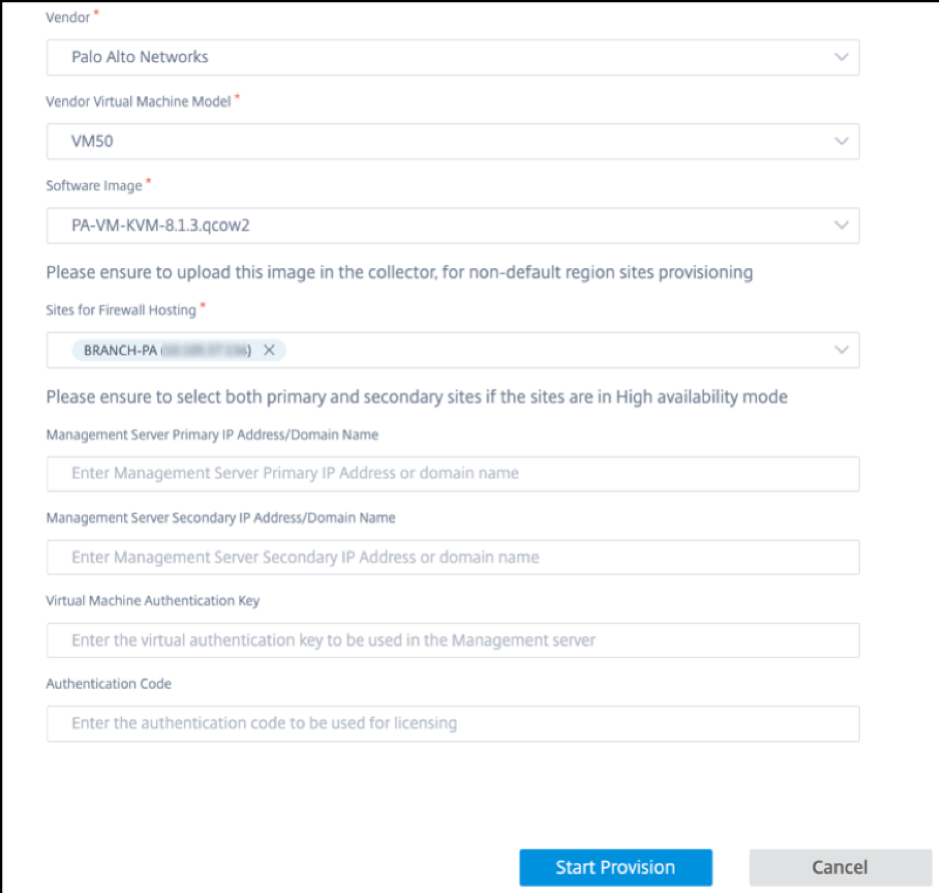
- Vendor: Select the vendor name as Palo Alto Networks from the drop-down list.
- Vendor Virtual Machine Model: Select the virtual machine model number from the list.
- Software Image: Select the Image file to provision.
- Region: Select the region from the list.
-
Sites for Firewall Hosting: Select sites for the list for firewall hosting. You must select both primary and secondary sites if the sites are in high availability mode.
- Management Server Primary IP Address/Domain Name: Enter the management primary IP address or fully qualified domain name (Optional).
-
Management Server Secondary IP Address/Domain Name: Enter the management server secondary IP address or fully qualified domain name (Optional).
-
Virtual Machine Authentication Key: Enter the virtual authentication key to be used in the management server.
- Authentication Code: Enter the virtual authentication code to be used for licensing.
- Click Start Provision.
Firewall virtual machine provisioning through SD-WAN appliance GUI
On SD-WAN platform, provision and boot up the hosted virtual machine. Perform the following steps for provisioning:
-
From Citrix SD-WAN GUI, navigate to Configuration > expand Appliance Settings > select Hosted Firewall.
- Upload the software image:
- Select the Software Images tab. Select the Vendor name as Palo Alto Networks.
- Choose the software image file.
- Click Upload.
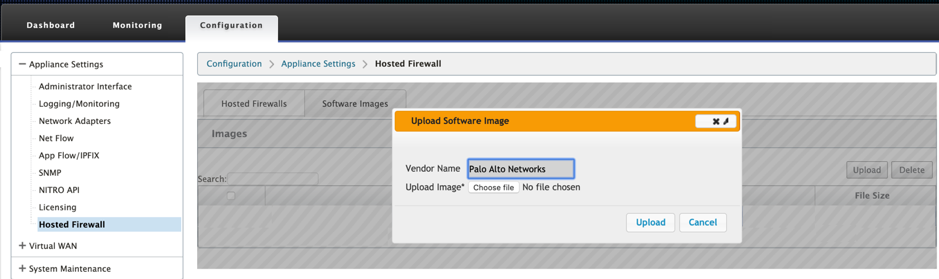
Note Maximum of two software image can be uploaded. Uploading of the Palo Alto Networks virtual machine image might take longer time depending on the bandwidth availability.
You can see a status bar to track the upload process. The file detail reflects, once the image is uploaded successfully. The image that is used for provisioning cannot be deleted. Do not perform any action or go back to any other page until the image file shows 100% uploaded.
-
For provisioning, select Hosted Firewalls tab and click Provision button.
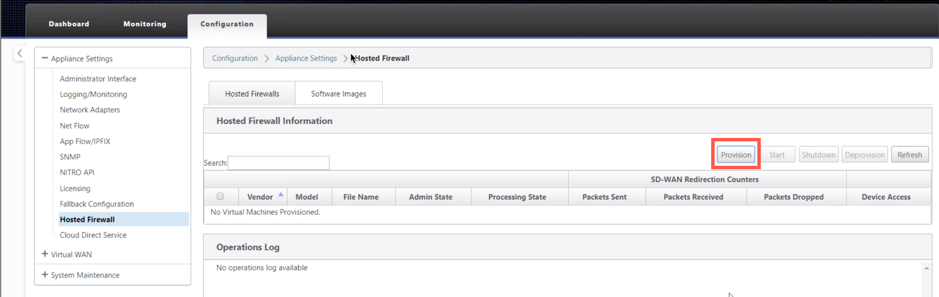
-
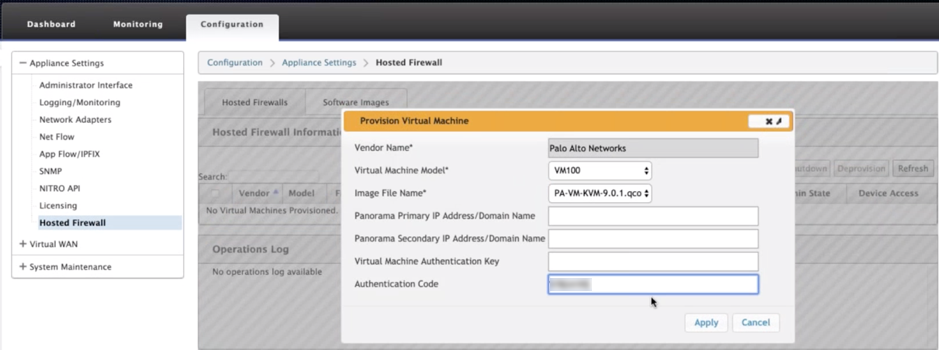
Provide the following details for provisioning.
- Vendor Name: Select the Vendor as Palo Alto Networks.
- Virtual Machine Model: Select the virtual machine model number from the list.
- Image File Name: Select the Image file.
- Panorama Primary IP Address/Domain Name: Provide the Panorama primary IP address or fully qualified domain name (Optional).
- Panorama Secondary IP Address/Domain Name: Provide the Panorama secondary IP address or fully qualified domain name (Optional).
-
Virtual Machine Authentication Key: Provide the virtual machine authentication key (Optional).
Virtual Machine Authentication Key is needed for automatic registration of the Palo Alto Networks virtual machine to the Panorama.
- Authentication Code: Enter the authentication code (virtual machine license code) (Optional).
- Click Apply.
-
Click Refresh to get the latest status. After the Palo Alto Networks virtual machine is completely bootup, it will reflect on the SD-WAN UI with the operations Log detail.
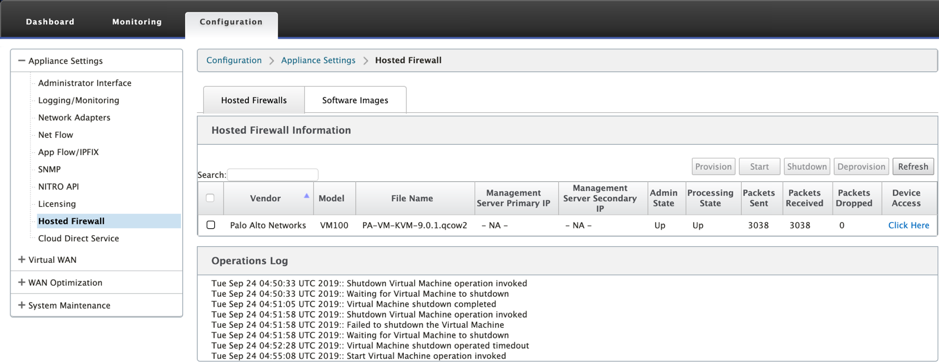
- Admin State: Indicates if the virtual machine is up or down.
- Processing State: Datapath processing state of the virtual machine.
- Packet Sent: Packets sent from SD-WAN to the security virtual machine.
- Packet Received: Packets received by SD-WAN from the security virtual machine.
- Packet Dropped: Packets dropped by SD-WAN (for example, when the security virtual machine is down).
- Device Access: Click the link to get the GUI access to the security virtual machine.
You can Start, Shutdown, and Deprovision the virtual machine as needed. Use Click Here option to access the Palo Alto Networks virtual machine GUI or use your management IP along with 4100 port (management IP: 4100).
Note Always use incognito mode to access the Palo Alto Networks GUI.
Traffic redirection
Traffic redirection configuration can be done both through the Configuration Editor on MCN or Configuration Editor on SD-WAN Center.
To navigate through Configuration Editor on SD-WAN Center:
-
Open Citrix SD-WAN Center UI, navigate to Configuration > Network Configuration Import. Import the virtual WAN configuration from the active MCN and click Import.
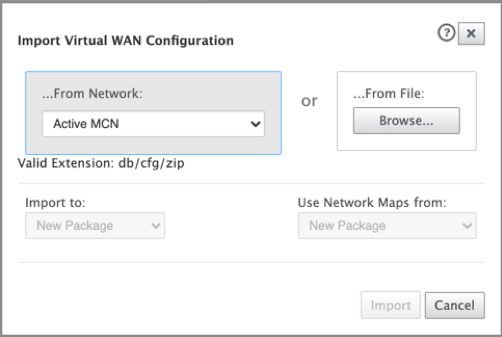
Remaining steps are similar as following - the traffic redirection configuration through MCN.
To navigate through Configuration Editor on MCN:
-
Set Connection Match Type to Symmetric under Global > Networking Settings.
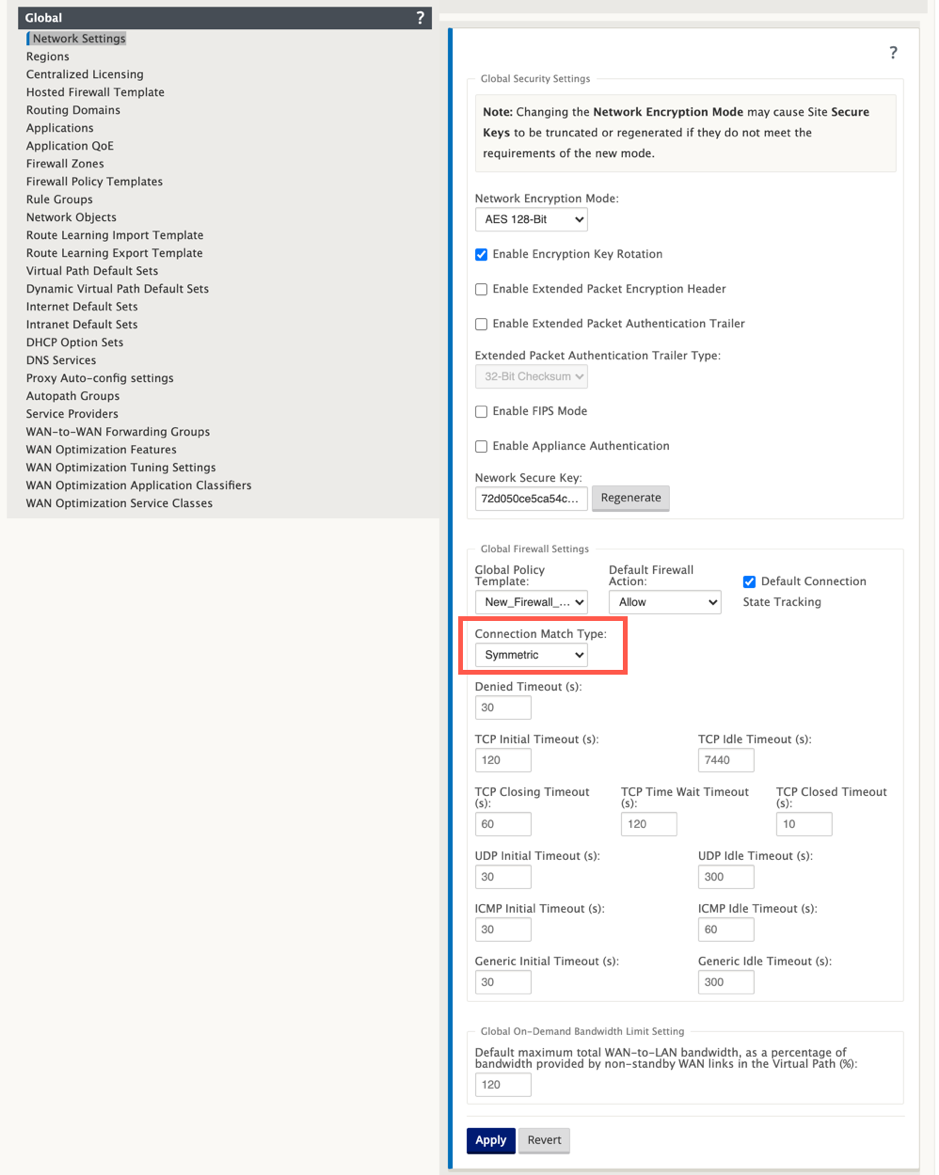
By default, SD-WAN firewall policies are direction specific. The Symmetric match type match the connections using specified match criteria and apply policy action on both directions.
-
Open Citrix SD-WAN UI, navigate to Configuration > expand Virtual WAN > select Configuration Editor > select Hosted Firewall Template under Global section.
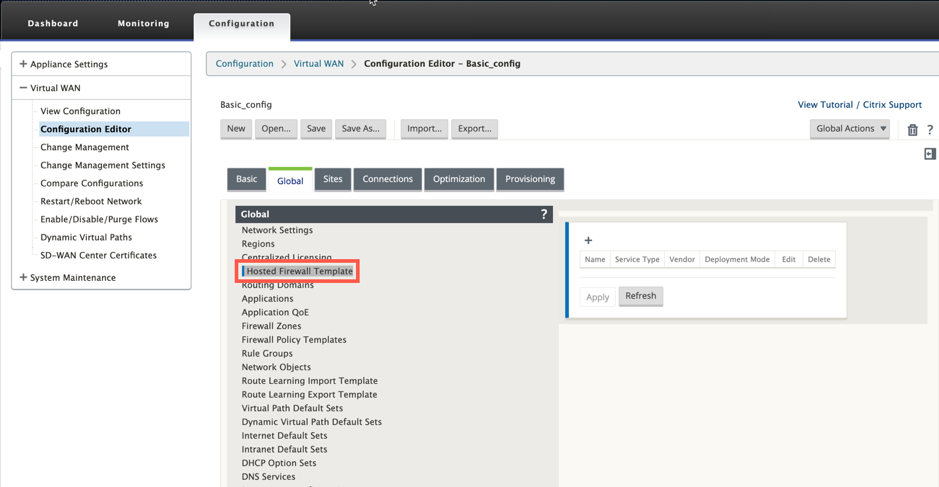
-
Click + and provide the required information available in the following screenshot to add the Hosted Firewall template and click Add.
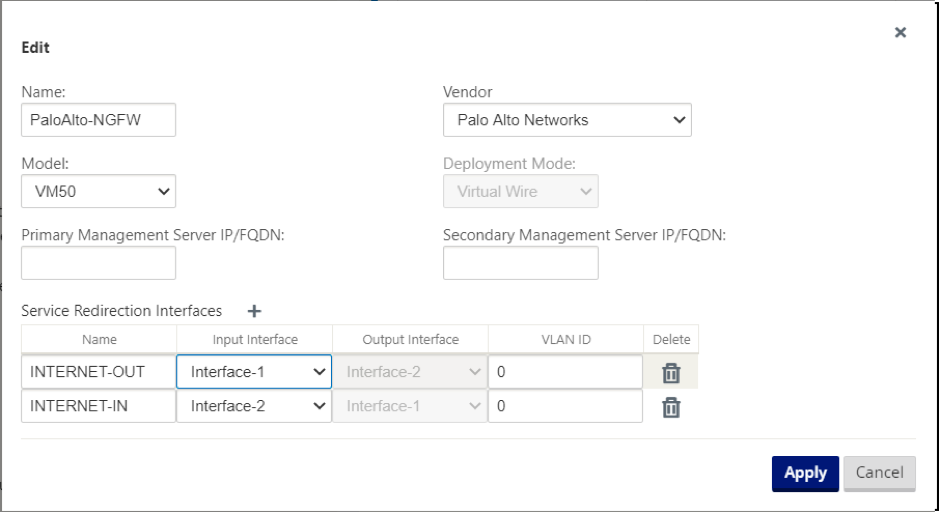
Hosted Firewall Template allows you to configure the traffic redirection to the Firewall virtual machine hosted on SD-WAN appliance. The following are the inputs needed to configure the template:
- Name: Name of the hosted firewall template.
- Vendor: Name of the firewall vendor.
- Deployment Mode: The Deployment Mode field is auto populated and grayed out. For the Palo Alto Networks vendor, the deployment mode is Virtual Wire.
- Model: Virtual Machine model of the hosted firewall. You can select the virtual machine model number as VM 50/VM 100 for the Palo Alto Networks vendor.
- Primary Management Server IP/FQDN: Primary management server IP/FQDN of Panorama.
- Secondary Management Server IP/FQDN: Secondary management server IP/FQDN of Panorama.
- Service Redirection Interfaces: These are logical interfaces used for traffic redirection between SD-WAN and hosted firewall.
Interface-1, Interface-2 refers to first two interfaces on the hosted firewall. If VLANs are used for traffic redirection then, same VLANs must be configured on the hosted firewall. VLANs configured for traffic redirection are internal to the SD-WAN and hosted firewall.
Note
Redirection input interface has to be selected from connection initiator direction, redirection interface is automatically chosen for the response traffic. For Example, if outbound internet traffic is redirected to hosted firewall on Interface-1 then, response traffic is automatically redirected to hosted firewall on Interface-2. There is no need of Interface-2 in the above example, if there is no internet inbound traffic.
Only two physical interfaces are assigned to host the Palo Alto Networks firewall. If traffic from multiple zones needs to be redirected to the hosted firewall then, multiple subinterfaces can be created using internal VLANs and associated to different firewall zones on the hosted firewall.
Through SD-WAN firewall policies or site level policies, you can redirect all the traffic to the Palo Alto Networks virtual machine.
Note
SD-WAN firewall policies are auto created to Allow the traffic to/from hosted firewall management servers. This avoids redirection of the management traffic that is originated from (or) destined to hosted firewall.
Traffic redirection to firewall virtual machine can be done using SD-WAN firewall policies. There are two methods to create SD-WAN firewall policies - either through firewall policy templates in Global section or site level.
Method - 1
-
From Citrix SD-WAN GUI, navigate to Configuration > expand Virtual WAN > Configuration Editor. Navigate to the Global tab and select Firewall Policy Templates. Click + Policy Template. Provide a name to the policy template and click Add.
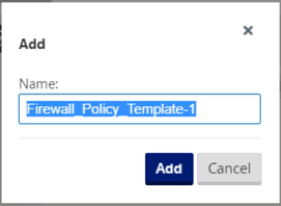
-
Click + Add next to Pre-Appliance Template Policies.
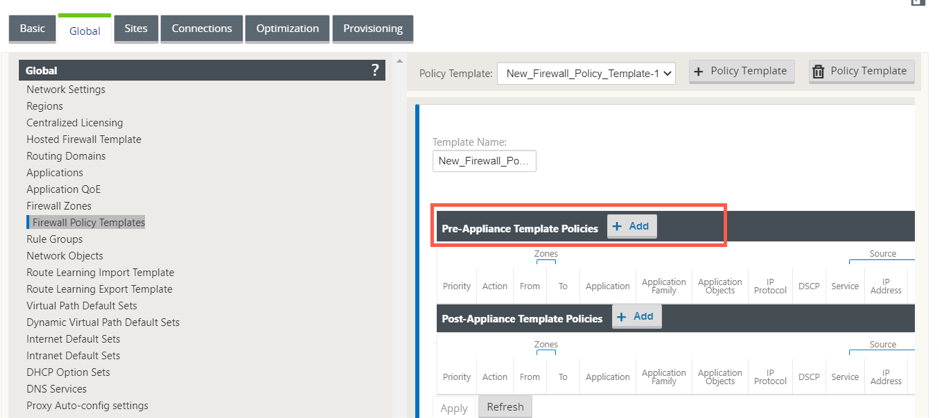
-
Change the Policy Type to Hosted Firewall. The Action field is auto filled to Redirect. Select the Hosted Firewall Template and the Service Redirection Interface from the drop-down list. Fill the other match criteria as required.
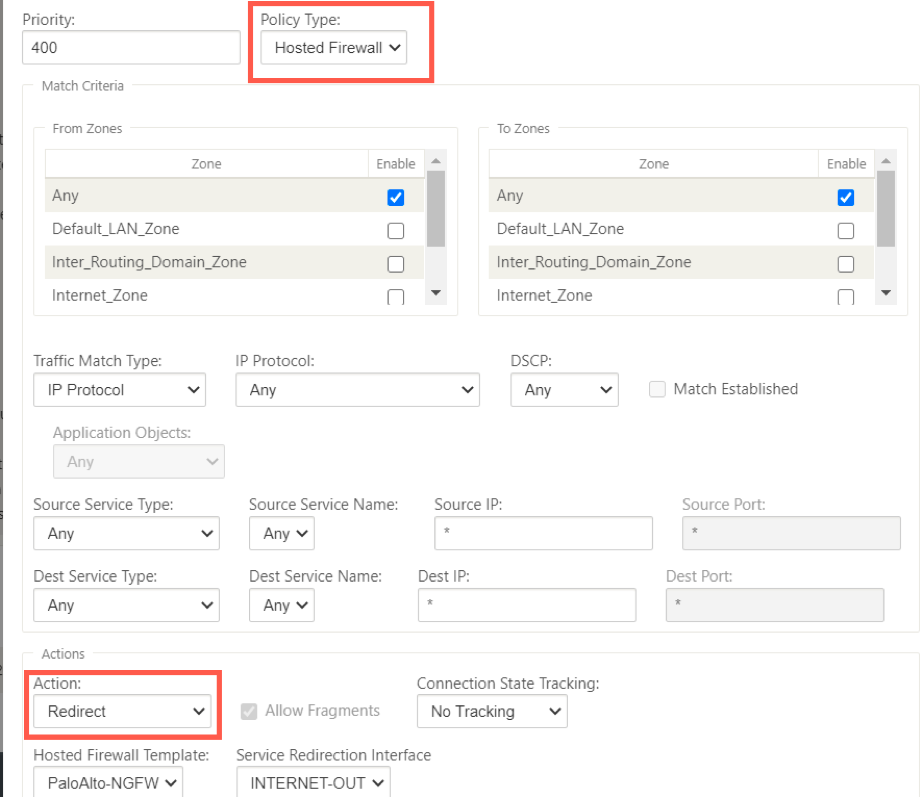
-
Navigate to the Connections > Firewall, then select the firewall policy (that you have created) under the name field. Click Apply.
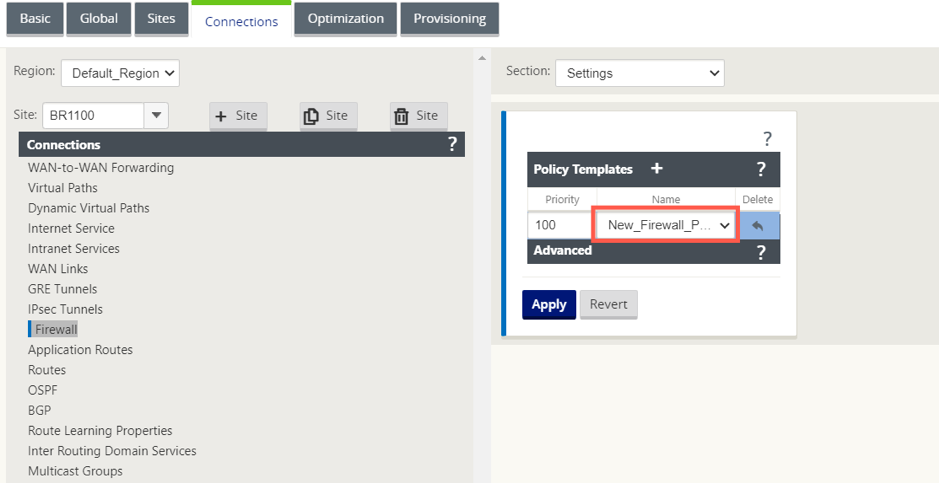
Method - 2
-
To redirect all the traffic, under the Configuration Editor > Virtual WAN, navigate to the Connection tab and select Firewall.
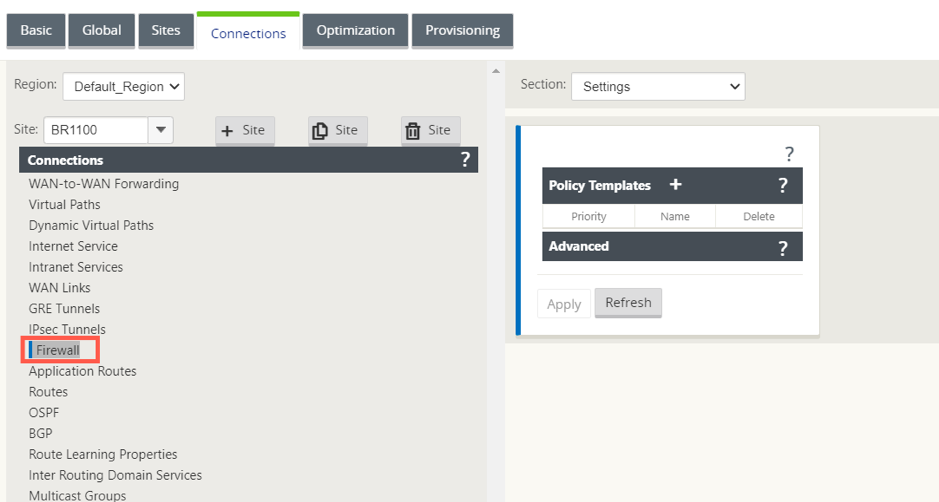
-
Select Policies from the Section drop-down list and click +Add to create a new firewall policy.
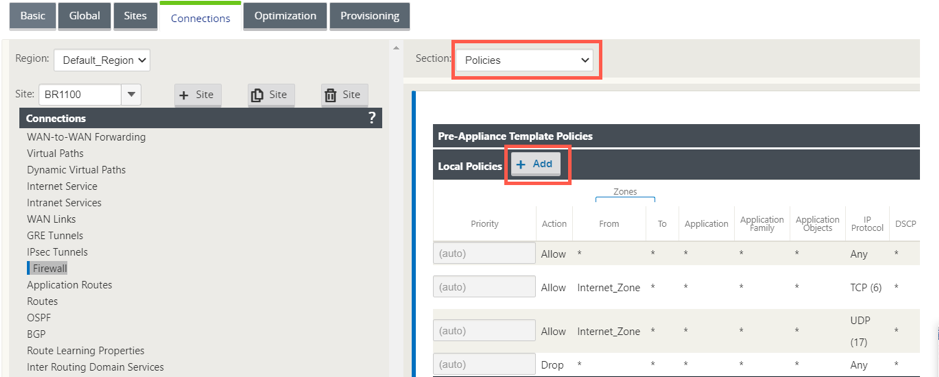
-
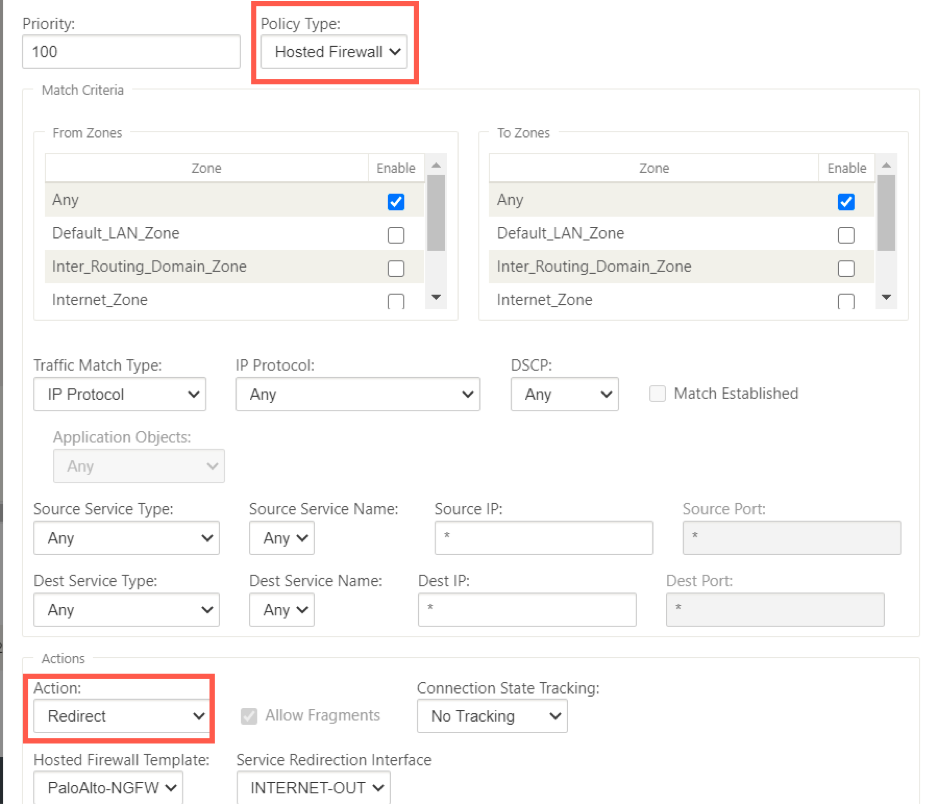
Change the Policy Type to Hosted Firewall. The Action field is auto filled to Redirect. Select the Hosted Firewall Template and the Service Redirection Interface from the drop-down list. Click Add.
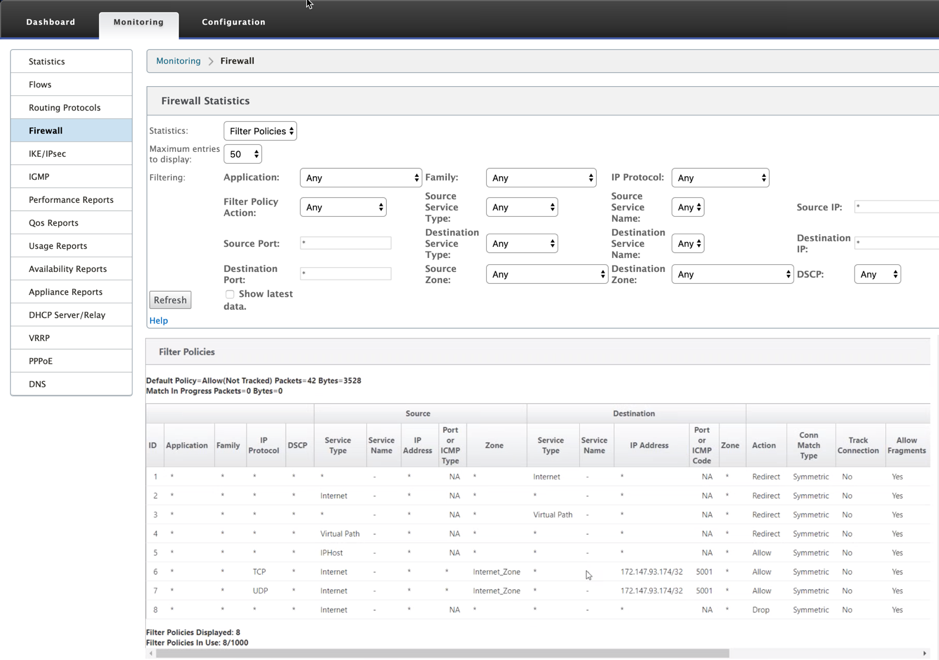
While all the network configuration is up and running mode, you can monitor the connection under Monitoring > Firewall > under Statistics list, select Filter Policies.
You can verify the mapping between the configuration you did on SD-WAN service chain template and Palo Alto Network configuration using the Palo Alto Networks UI.
NOTE
Palo Alto Networks virtual machine cannot be provisioned if Cloud Direct or SD-WAN WANOP(PE) is already provisioned on the 1100 appliance.
Use-cases – Hosted Firewall on SD-WAN 1100
The following are some of the use case scenarios implemented by using Citrix SD-WAN 1100 appliance:
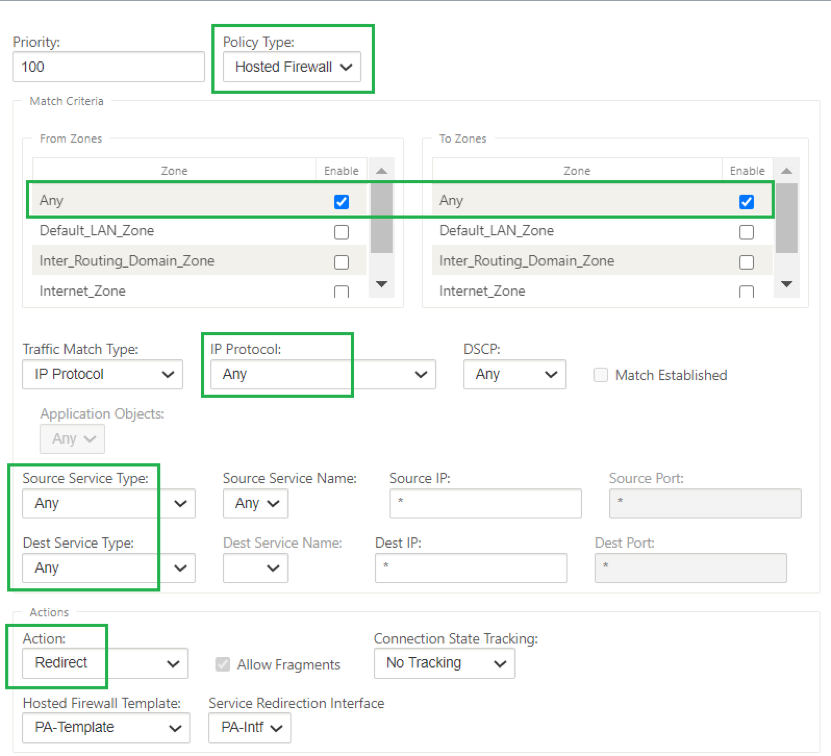
Use case 1: Redirect all the traffic towards Hosted Firewall
This use case is applicable for small branch use cases where all the traffic is processed by the hosted Next-Generation firewall. Bandwidth requirements must be taken into considerations as the amount of redirected traffic throughput is limited to 100 Mbps.
To achieve this, create a firewall rule to match any traffic and with Action as Redirect, as shown in the following screenshot:
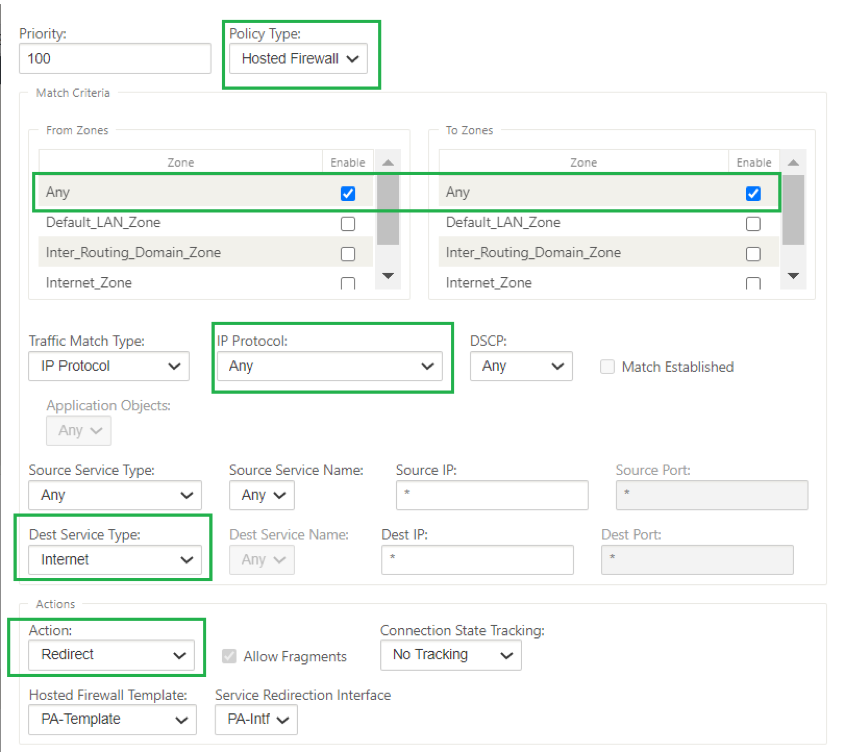
Use case 2: Redirect only Internet traffic towards Hosted Firewall
This use case is applicable to any branch sites where Internet bound traffic not exceeding the amount of supported redirected traffic throughput. In this case, Branch to data center traffic is processed by security appliances/service deployed at data centers.
To achieve this, create a firewall rule to match any traffic and with Action as Redirect as shown in the following screenshot:
Use case 3: Direct Internet breakout for trusted Internet SaaS applications and redirect remaining all traffic to the Hosted VM
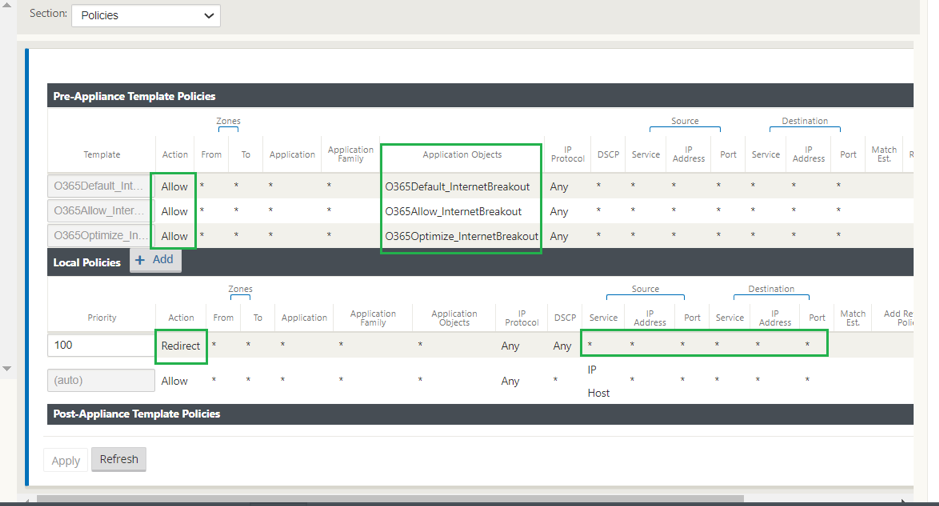
In this use case, a firewall rule is added to perform direct Internet breakout for trusted SaaS applications such as office 365. First enable office 365 break out policy as shown in the following screenshot:
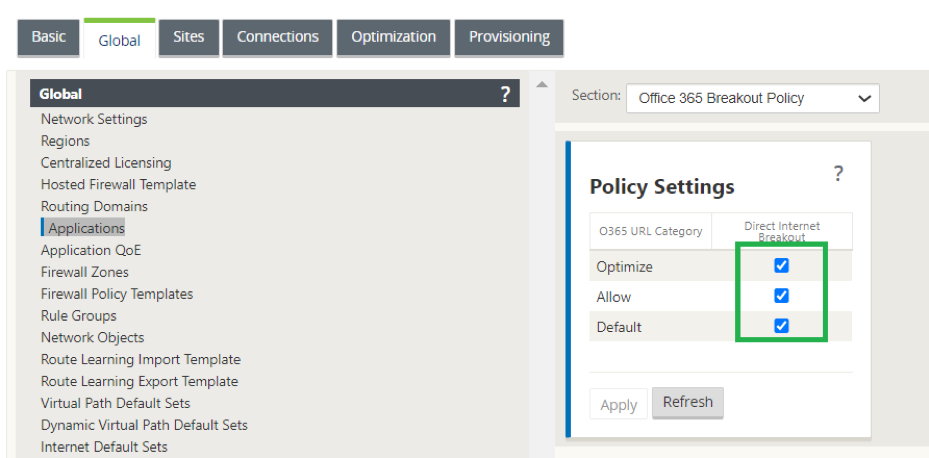
This automatically adds Pre-Appliance Template Policies to allow office 365 traffic as shown in the following screenshot. Now add a firewall rule to redirect remaining all traffic to Hosted firewall as mentioned below.
Note
Hosted firewall configuration is independent of Citrix SD-WAN configuration. So, the hosted firewall can be configured as per enterprise security requirements.