IP rules
IP Rules help you to create rules for your network and take certain Quality of Service (QoS) decisions based on the rules. You can create custom rules for your network. For example, you can create a rule as – If source IP address is 172.186.30.74 and destination IP address is 172.186.10.89, set Traffic Policy as Persistent Path and Traffic Type as Realtime.
You can create rules for traffic flow and associate the rules with applications and classes. You can specify criteria to filter traffic for a flow, and can apply general behavior, LAN to WAN behavior, WAN to LAN behavior, and packet inspection rules.
You can create global and site-specific IP rules at the network level. If a site is associated with the globally created rule, you can create site specific rules. In such cases, site specific rules take precedence and override the globally created rule.
The default IP protocol rules HTTP, HTTPS, and ALTHTTPS always appear at the top of the list on the Rules table. However, site-specific IP rules (once created) appear above HTTP, HTTPS, ALTHTTPS, and global IP rules on the Rules table.
Create IP rules
To create IP rules, navigate to Configuration > QoS > QoS Policies > IP Rules. Select the Global Rules tab for creating IP rules at the global level or Site/Group Specific Rules for creating rules at a site level.
Click New IP Rule under the IP Rules section.
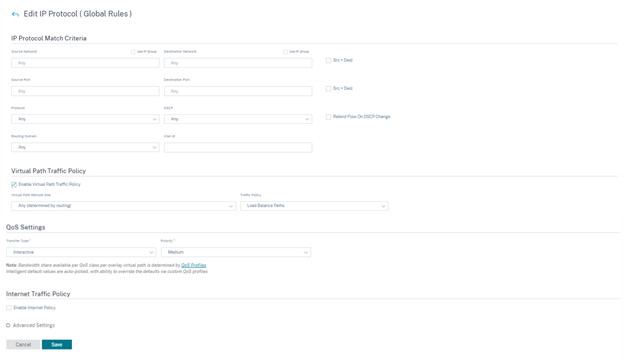
-
IP Protocol Match Criteria
- Add/Remove Sites: (available only while creating site-specific IP rule) Select the sites, click Review, and Done.
- Source Network: The source IP address and subnet mask that the rule matches.
- Destination Network: The destination IP address and subnet mask that the rule matches.
- Use IP Group: Select the Use IP Group check box to choose any existing IP group from the drop-down list.
- Src = Dst: If selected, the source IP address is also used for the destination IP address.
- Source Port: The source port (or source port range) that the rule matches.
- Destination Port: The destination port (or destination port range) that the rule matches.
- Src = Dst: If selected, the source port is also used for the destination port.
- Protocol: The protocol with which the rule matches. You can select one of the predefined protocols, or select Any, or Number.
- Protocol Number: This field appears only when you select Number from the Protocol drop-down list. When you select a protocol number, the integer associated with the protocol is used for the back-end configurations.
- DSCP: The DSCP tag in the IP header that the rule matches.
- Routing Domain: The routing domain that the rule matches.
- VLAN ID: Enter the VLAN ID for the rule. The VLAN ID identifies the traffic to and from the virtual interface. Use VLAN ID as 0 to designate native or untagged traffic.
- Rebind Flow On DSCP Change: When selected, flows that are otherwise identical in terms of match criteria are treated as separate if their DSCP fields differ.
-
Virtual Path Traffic Policy
Select the Enable Virtual Path Traffic Policy check box.
- Virtual Path Remote Site: Select the virtual path for the remote site.
-
Traffic Policy: Choose one of the following traffic policies as needed.
- Load Balance Paths: Application traffic for the flow is balanced across multiple paths. Traffic is sent through the best path until that path is used. The remaining packets are sent through the next best path.
-
Persistent Path: Application traffic remains on the same path until the path is no longer available. Select one of the following Persistence Policies:
- Persist on the originating link: The application traffic remains on the originating link until the path is no longer available.
- Persist on MPLS link if available, else on the originating link: The application traffic remains on the MPLS link. If the MPLS link is unavailable, then the traffic remains on the originating link.
- Persist on Internet link if available, else on the originating link: The application traffic remains on the internet link. If the internet link is unavailable, then the traffic remains on the originating link.
- Persist on Private Intranet link if available, else on the originating link: The application traffic remains on the private intranet link. If the private intranet link is unavailable, then the traffic remains on the originating link.
Persistence Impedance is the time (in ms) until which the application traffic remains on the link.
- Duplicate Paths: Application traffic is duplicated across multiple paths, increasing reliability.
- Override Service: Traffic for the flow overrides to a different service. Select the service type as Intranet, Internet, pass-through, or Discard to which the virtual path service overrides.
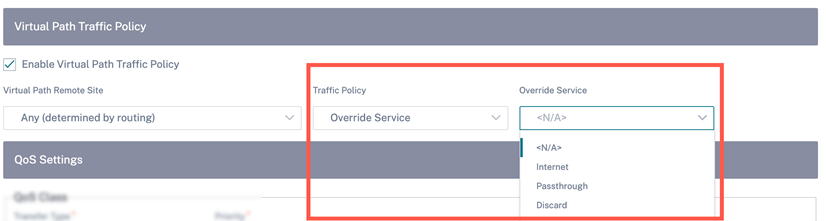
-
QoS Settings (QoS Class)
-
Transfer Type: Choose one of the following transfer types:
- Realtime: Used for low latency, low bandwidth, time-sensitive traffic. Real-time applications are time-sensitive but don’t really need high bandwidth (for example voice over IP). Real-time applications are sensitive to latency and jitter but can tolerate some loss.
- Interactive: Used for interactive traffic with low to medium latency requirements and low to medium bandwidth requirements. The interaction is typically between a client and a server. The communication might not need high bandwidth but is sensitive to loss and latency.
- Bulk: Used for high bandwidth traffic and applications that can tolerate high latency. Applications that handle file transfer and need high bandwidth are categorized as a bulk class. These applications involve little human interference and are mostly handled by the systems themselves.
- Priority: Choose a priority for the selected transfer type.
-
Transfer Type: Choose one of the following transfer types:
-
Internet Traffic Policy
- Select the Enable Internet Policy check box to configure internet traffic policy.
- Mode: The method of transmitting and receiving packets for flows that match the rule. You can choose Override Service or WAN link as needed.
- WAN link: The WAN link to be used by flows matching the rule when Internet Load Balancing is enabled.
- Override Service: The destination service for flows matching the rule.
Note
A virtual path service cannot override another virtual path service.
Advanced Settings
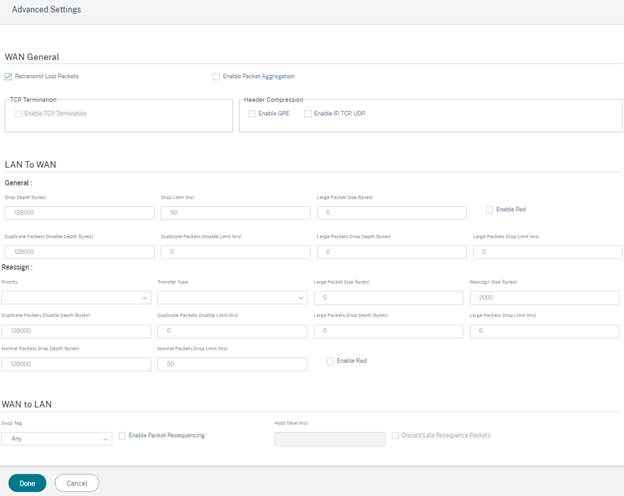
-
WAN General
- Retransmit Lost Packets: Sends traffic that matches this rule to the remote appliance over a reliable service and retransmits lost packets.
- Enable Packet Aggregation: Aggregates small packets into larger packets.
- Enable TCP Termination: Enables TCP termination of traffic for this flow. The round-trip time for acknowledgment of packets is reduced, and therefore improves throughput.
- Enable GRE: Compresses headers in GRE packets.
-
Enable IP, TCP, and UDP: Compresses headers in IP, TCP, and UDP packets.
Note
IPv6 packets do not support header compression.
-
LAN to WAN
General
- Drop Depth(bytes): Queue depth threshold after which packets are dropped.
- Drop Limit: Time after which packets waiting in the class scheduler are dropped. Not applicable for a bulk class.
- Large Packet Size: Packets smaller than or equal to this size are assigned the Drop Limit and Drop Depth values specified in the Large Packets Drop Depth(bytes) and Large Packets Drop Limit(ms) fields. Packets larger than this size are assigned the values specified in the default Drop Limit and Drop Depth fields.
- Enable RED: Random Early Detection (RED) ensures fair sharing of class resources by discarding packets when congestion occurs.
- Duplicate Packet Disable Depth(bytes): The queue depth of the class scheduler at which point the duplicate packets are not generated.
- Duplicate Packet Disable Limit: Time for which duplication can be disabled to prevent duplicate packets from consuming bandwidth.
- Large Packets Drop Depth(bytes): If the queue depth exceeds this threshold, the packets are discarded and statistics are counted.
- Large Packets Drop Limit(ms): The maximum amount of estimated time that packets larger than or equal to the Large Packet Size must wait in the class scheduler. If the estimated time exceeds this threshold, the packets are discarded and statistics are counted. Not valid for Bulk classes.
Reassign
- Priority: You can set the priority of the standby WAN link as needed. The standby WAN link priority indicates the order in which a standby WAN link becomes active. A high priority standby WAN link becomes active first. A low-priority WAN link becomes active last.
- Transfer Type: Select a transfer type with which to associate this rule.
- Duplicate Packet Disable Depth(bytes): The queue depth of the class scheduler at which point duplicate packets are not generated.
- Duplicate Packet Disable Limit: Designates the amount of time a packet waits in the queue before duplication is not performed, which prevents duplicate packets from consuming bandwidth when bandwidth is limited.
- Large Packets Drop Depth(bytes): If the queue depth exceeds this threshold, the packets are discarded and statistics are counted.
- Large Packets Drop Limit(ms): If the estimated time exceeds this threshold, the packets are discarded and statistics are counted. Not valid for Bulk classes.
- Normal Packets Drop Depth (bytes): If the queue depth exceeds this threshold, the packets are discarded and statistics are counted.
- Normal Packets Drop Limit (ms): If the estimated time exceeds this threshold, the packets are discarded and statistics are counted. Not valid for Bulk classes.
-
WAN to LAN
- DSCP Tag: DSCP tag applied to the packets that match this rule on WAN to LAN, before sending them to the LAN.
- Enable Packets Resequencing: The traffic flows that match the rule gets tagged for sequence order, and the packets gets reordered (if necessary) at the WAN to LAN appliance.
-
Hold Time: Time interval for which the packets are held for resequencing, after which the packets are sent to the LAN. When the timer expires, the packets are sent to the LAN without waiting any further for the prerequisite sequence numbers.
If the rule has a traffic policy as duplicate path, the default hold time is 80 ms. Otherwise, the default is 900 ms for TCP rules and 250 ms for non-TCP rules.
- Discard Late Resequencing Packets: Discards out-of-order packets that arrived after the packets needed for resequencing have been sent to the LAN.
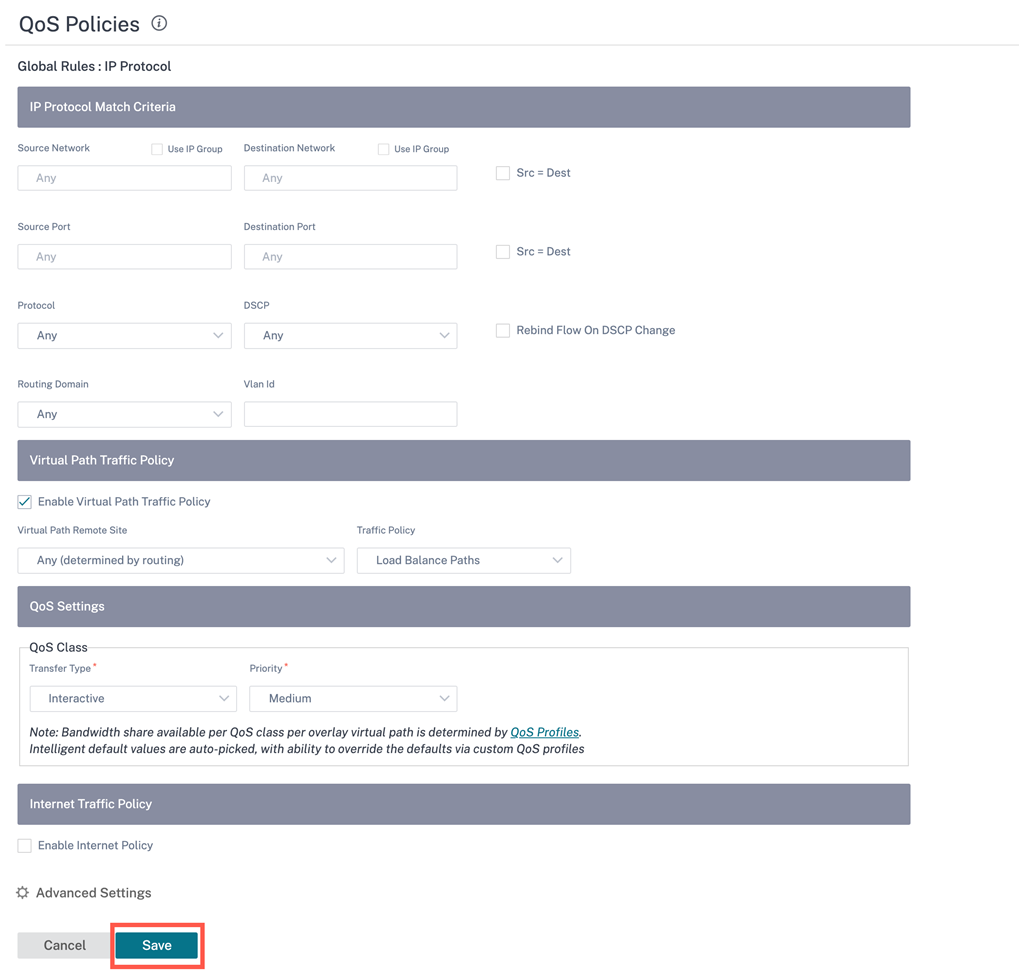
Click Save to save the configuration settings. Click Verify Configuration on the Configuration > QoS Policies page to validate any audit error.

Verify IP rules
To verify IP rules, navigate to Reports > Real Time > Flows. Select the site for which you want to view the flow information and the number of flows to display. Click Customize Columns and select the check boxes corresponding to the flow information you want to view. Verify if the flow information is according to the configured rules.
Navigate to Reports > Real Time > Statistics and select Rules. Choose the site and click Retrieve latest data. Verify the configured rules. For more information, see Site reports.