Appliance settings
Citrix SD-WAN Orchestrator for On-premises allows you to configure the appliance settings, at the site level and push it to the remote appliances.
You can configure the user, network adapters, NetFlow, AppFlow®, SNMP, Fallback configuration, and Purge flow settings.
Note
The option to configure appliance settings is not available while creating or editing a site template.
If HA is configured, select the primary or secondary appliance for which you want to change the appliance settings.

Administrative interface
The administrative interface allows you to add and manage the local and remote user accounts. The remote user accounts are authenticated through the RADIUS or TACACS+ authentication servers.
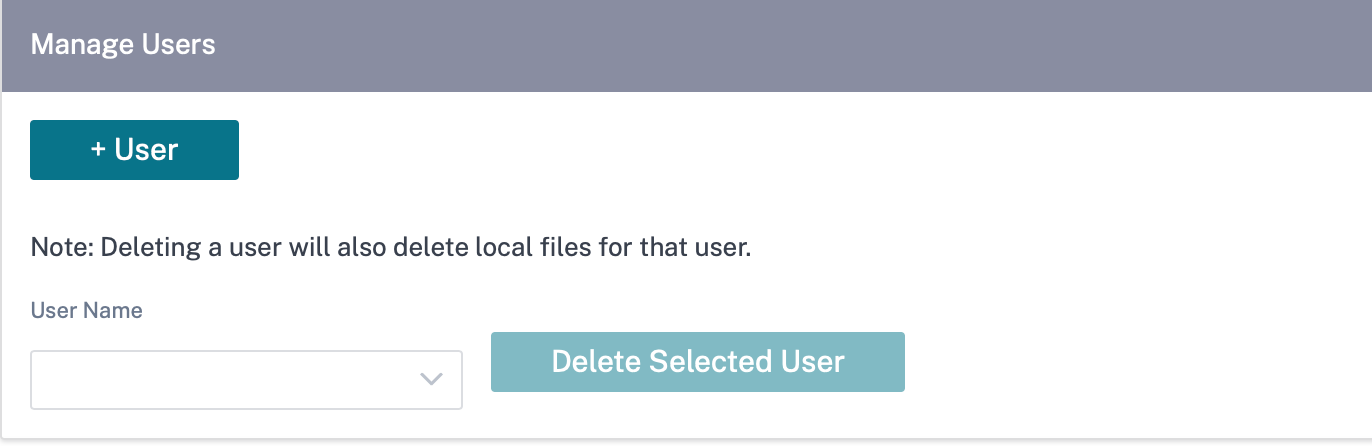
Manage users
You can add new user accounts for the site. To add a new user, navigate to Configuration > Appliance Settings > Administrator Interface > Manage Users, and click +User.
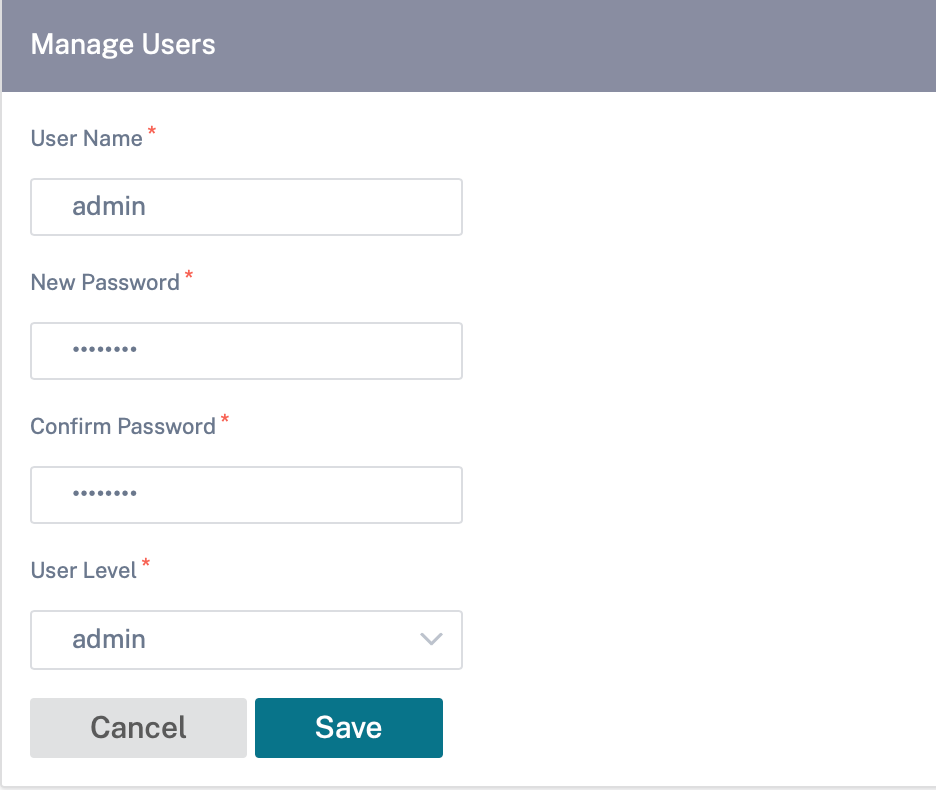
Provide the following details:
- User Name: The user name for the user account.
- New Password: The password for the user account.
- Confirm Password: Reenter the password to confirm it.
-
User level: Select one of the following account privileges:
- Admin: An Admin account has read-write access to all the settings. An admin can perform configuration and software update to the network.
- Viewer: A Viewer account is a read-only account with access to Dashboard, Reporting, and Monitoring sections.
- Network Admin: A Network Administrator has read-write access to the Network setting and read-only access for other settings.
-
Security Admin: A Security Administrator has read-write access for the Firewall / Security related settings read-only access for other settings.
Note
Security administrator has the authority to disable the write access to the firewall for other users (Admin/Viewer).
To delete a user, select a user name and click Delete Selected User. The user account and the local files are deleted.
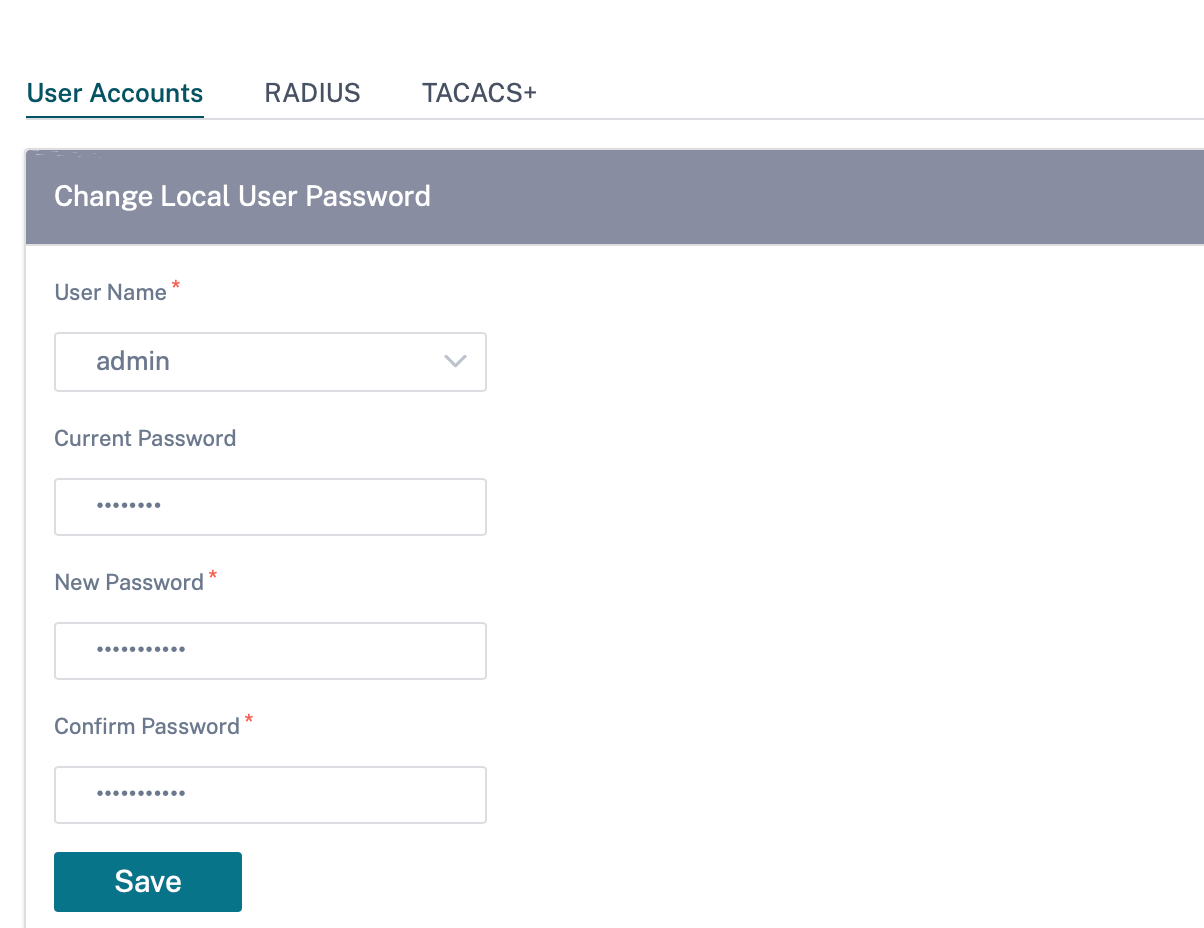
Change local user password
To change the local user password, navigate to Configuration > Appliance Settings > Administrative Interface > User Accounts > Change Local User Password and provide the following values:
- User Name: Select a user name for which you want to change the password from the list of users configured at the site.
- Current Password: Enter the current password. This field is optional for admin users.
- New Password: Enter a new password of your choice.
- Confirm Password: Reenter the password to confirm it.
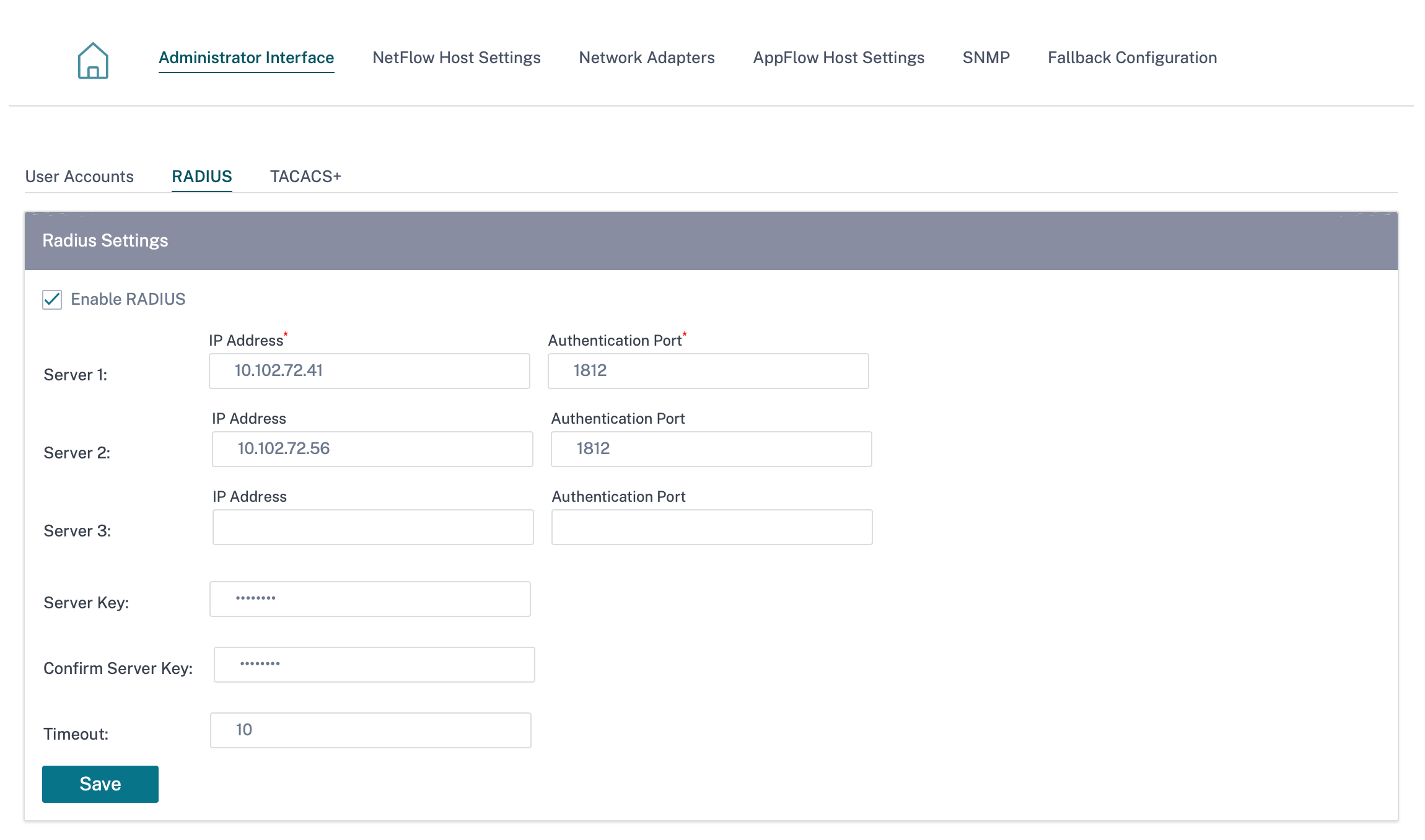
RADIUS authentication server
RADIUS enables remote user authentication on the appliance. To use RADIUS authentication, you must specify and configure at least one RADIUS server. Optionally, you can configure redundant backup RADIUS servers, up to a maximum of three. The servers are checked sequentially. Ensure that the required user accounts are created on the RADIUS authentication server.
To configure RADIUS authentication, navigate to Configuration > Appliance Settings > Administrative Interface > RADIUS, and click Enable RADIUS.
Note
You can either enable RADIUS or TACACS+ authentication on a site. You cannot enable both at the same time.
Provide the host IP address of the RADIUS server and the authentication port number. The default port number is 1812. Enter a Server key and confirm it, it is a secret key used to connect to the RADIUS server. Specify the time interval to wait for an authentication response from the RADIUS server. The timeout value must be less than or equal to 60 seconds.
Note
The Server Key and Timeout settings are applied to all the configured servers.
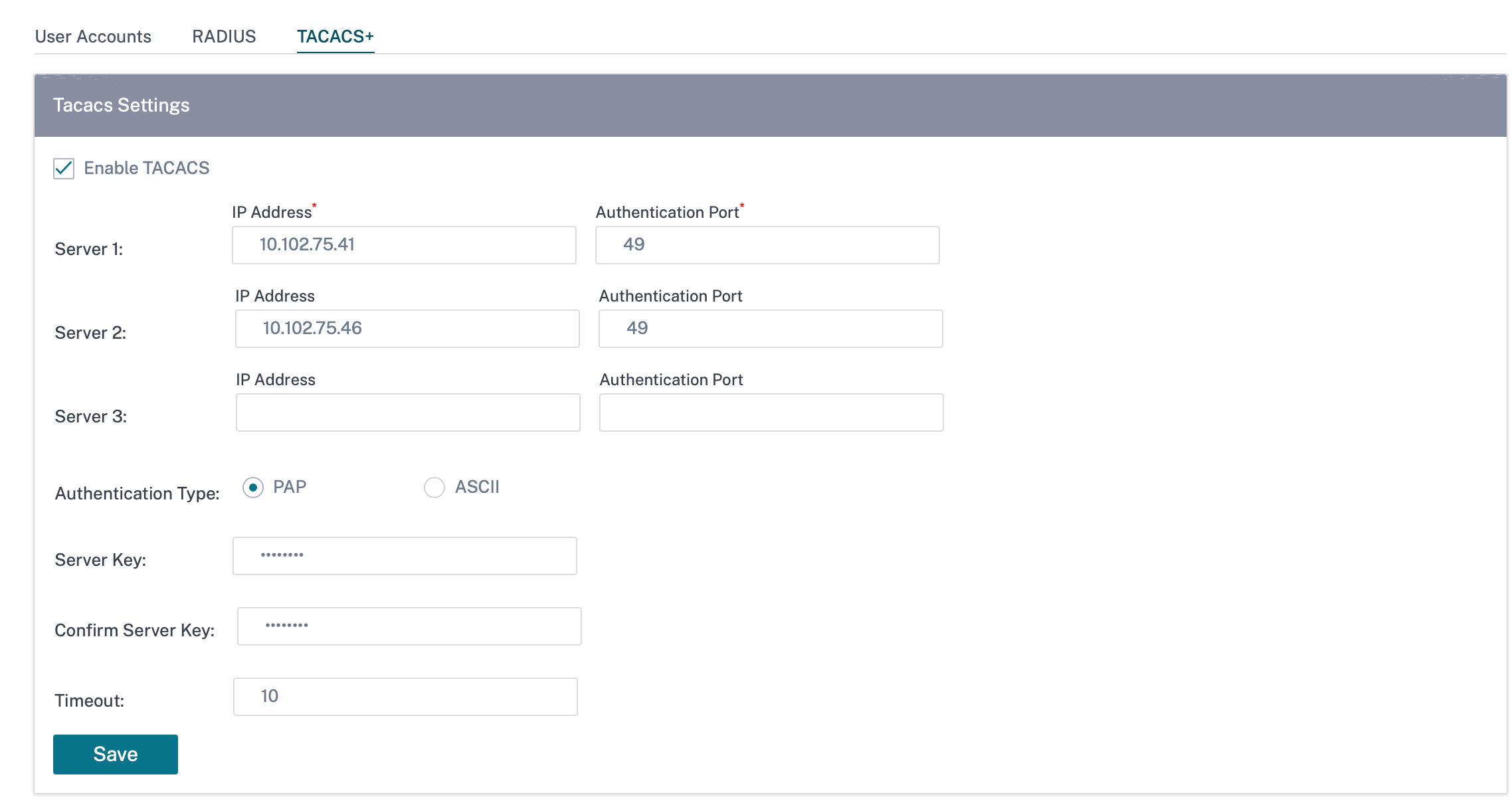
TACACS+ authentication server
TACACS+ enables remote user authentication on the appliance. To use TACACS+ authentication, you must specify and configure at least one TACACS+ server. Optionally, you can configure redundant backup TACACS+ servers, up to a maximum of three. The servers are checked sequentially. Ensure that the required user accounts are created on the TACACS+ authentication server.
To configure TACACS+ authentication, navigate to Configuration > Appliance Settings > Administrative Interface > TACACS+ and click Enable TACACS+.
Note
You can either enable RADIUS or TACACS+ authentication on a site. You cannot enable both at the same time.
- Select the encryption method to send the user name and password to the TACACS+ server.
- Provide the host IP address of the TACACS+ server and the authentication port number. The default port number is 49.
- Enter a Server key and confirm it. It is a secret key used to connect to the TACACS+ server.
- Specify the time interval to wait for an authentication response from the TACACS+ server. The timeout value must be less than or equal to 60 seconds.
Note
The Authentication type, Server Key, and Timeout settings are applied to all the configured servers.
NetFlow host settings
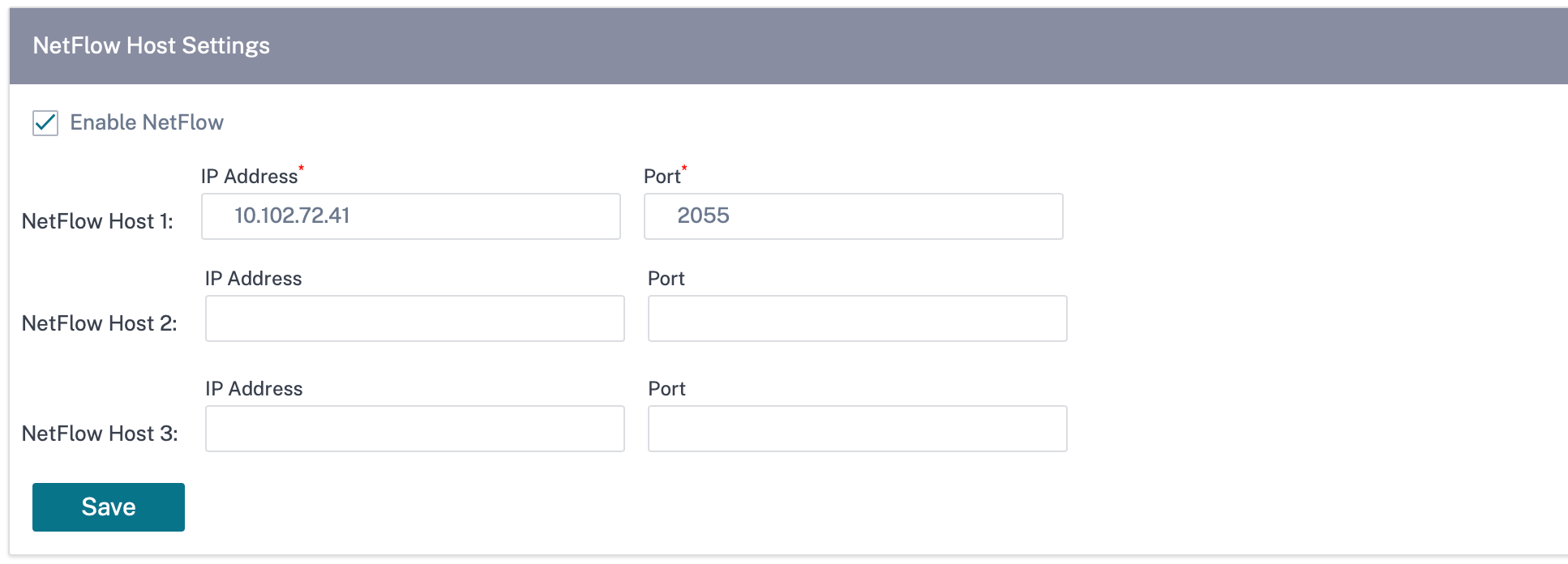
NetFlow Collectors collect IP network traffic as it enters or exits an SD-WAN interface. You can determine the source and destination of traffic, class of service, and the causes for traffic congestion using NetFlow data. For more information, see Multiple NetFlow Collector.
You can configure up to three NetFlow hosts. To configure NetFlow host settings, navigate to Configuration > Appliance Settings > NetFlow Host Settings. Select Enable NetFlow and provide the IP Address, and Port number of the NetFlow host.
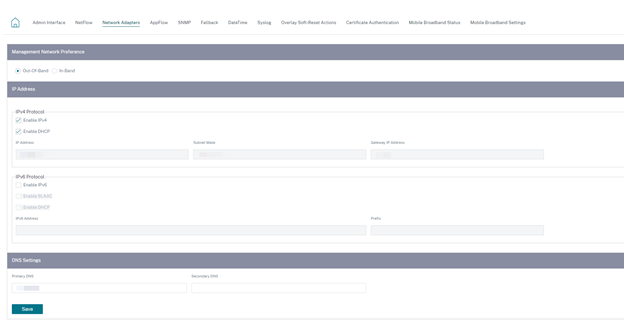
Network adapters
For Citrix SD-WAN appliances, you can manually change the management network preference, management IP address and other network parameters. You can change the IPv4 address, subnet mask, gateway IP address, IPv6 address, and prefix of the appliance or obtain the IP address automatically by enabling DHCP or SLAAC (only for IPv6 addresses). For more information, see Dynamic host configuration protocol.
Note
- You cannot change the IP address, if the interface is used for in-band management. For more information on in-band management, see In-band management.
- The In-band option works only if you have configured a data port as the In-band management port and Internet service is configured. Ensure that you have the configuration to support In-band management for the SD-WAN appliance, prior to setting the management preference.
- The Management Network Preference (In-band and Out-of-band) section is visible if the appliance is running a software version of 11.4.2 or later.
To configure the network adapter settings, navigate to Configuration > Appliance Settings > Network Adapter.
AppFlow host settings
AppFlow and IPFIX are flow export standards used to identify and collect application and transaction data in the network infrastructure. This data gives better visibility into application traffic utilization and performance.
The collected data, called flow records are transmitted to one or more IPv4 collectors. The collectors aggregate the flow records and generate real-time or historical reports. For more information, see AppFlow and IPFIX.
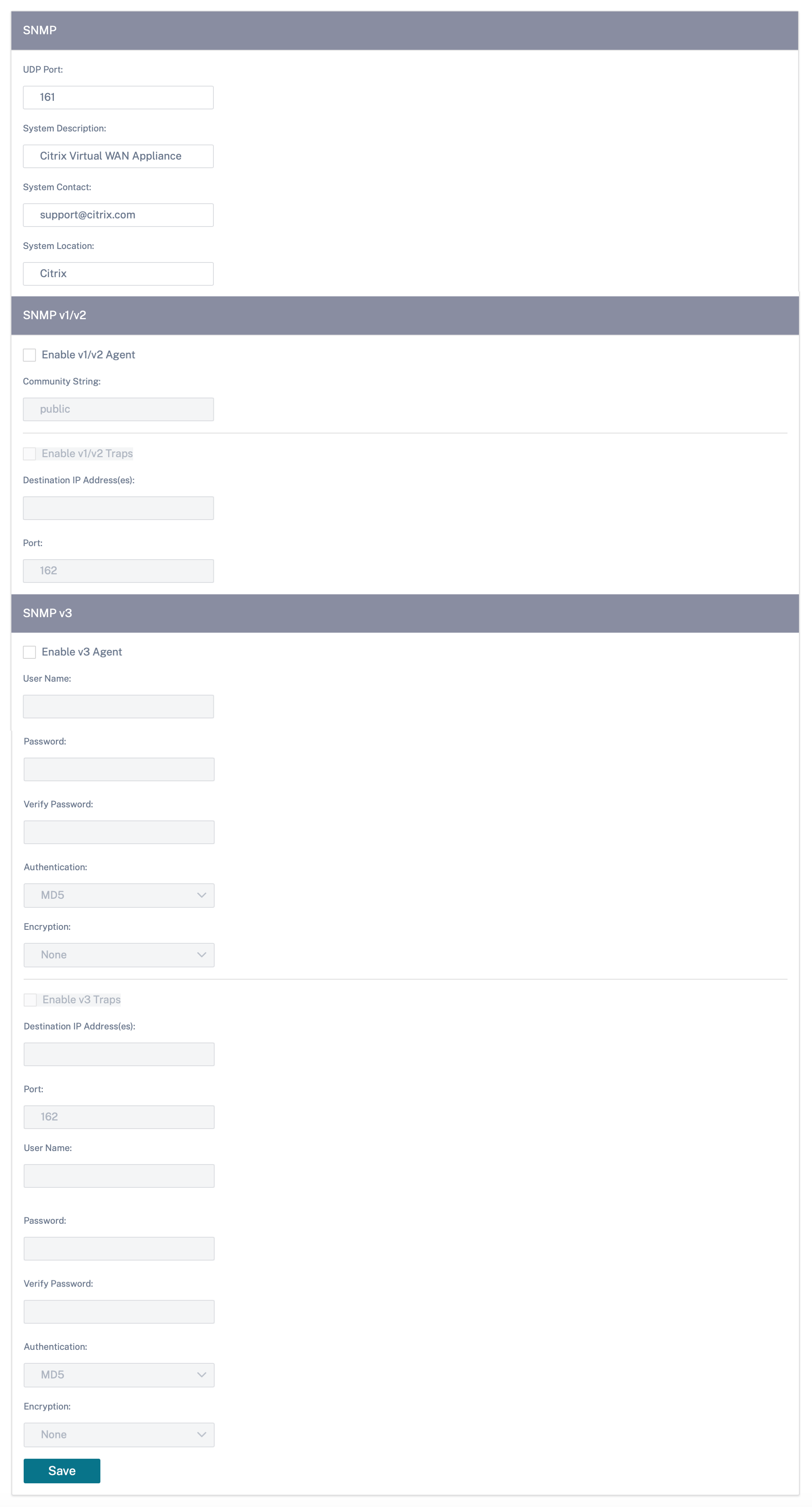
SNMP
SNMP is used for exchanging management information between network devices. SNMPv1 is the first version of the SNMP protocol. SNMPv2 is the revised protocol, which includes enhancements in protocol packet types, transport mappings and MIB structure elements. SNMPv3 defines the secure version of the SNMP. SNMPv3 protocol also facilitates remote configuration of the SNMP entities.
The SNMP agent collects the management information from the appliance locally and sends it to the SNMP manager whenever it is queried. If the agent detects an emergency event on the appliance, it sends out a warning message to the manager without waiting to be queried for data. This emergency message is called a trap. Enable the required SNMP version agents, the corresponding traps, and provide the required information. For more details see, SNMP.
To configure SNMP settings, navigate to Configuration > Appliance Settings > SNMP
Fallback configuration
Fallback configuration ensures that the appliance remains connected to the zero-touch deployment service if there is a link failure, configuration mismatch, or software mismatch. Fallback configuration is enabled by default on the appliances that have a default configuration profile. You can also edit the fallback configuration as per your existing LAN network settings. For more information, see Fallback configuration.
Flows
The flows section allows you to enable or disable Citrix® Virtual WAN service on the appliance. Enabling the service enables and starts the Virtual WAN daemon. An option to enable Citrix Virtual Wan Service is available if the service is disabled.

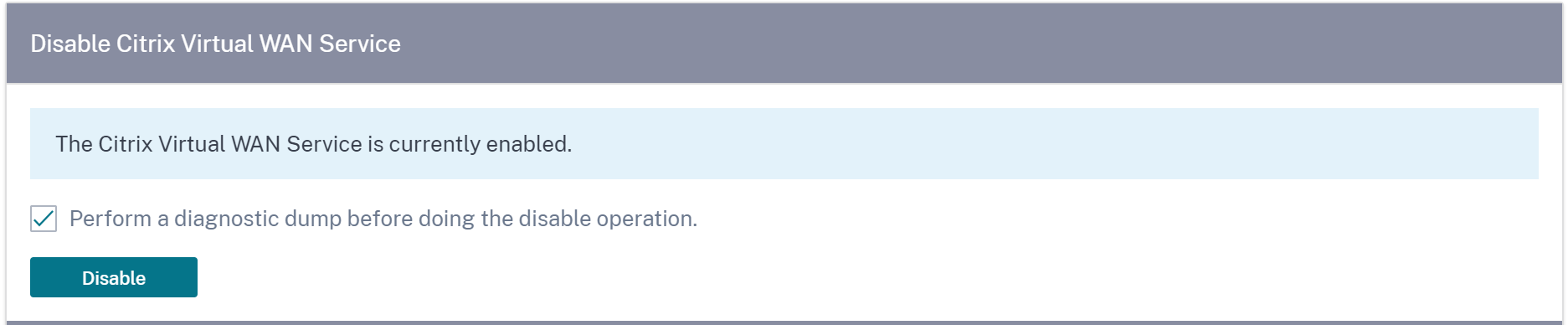
Disable Citrix Virtual WAN service
The Disable Citrix Virtual WAN Service option is available if the service is enabled. Disabling the service stops the Virtual WAN daemon on the appliance.
You can choose to collect a diagnostic dump of the Virtual WAN network before disabling the Citrix Virtual WAN service.
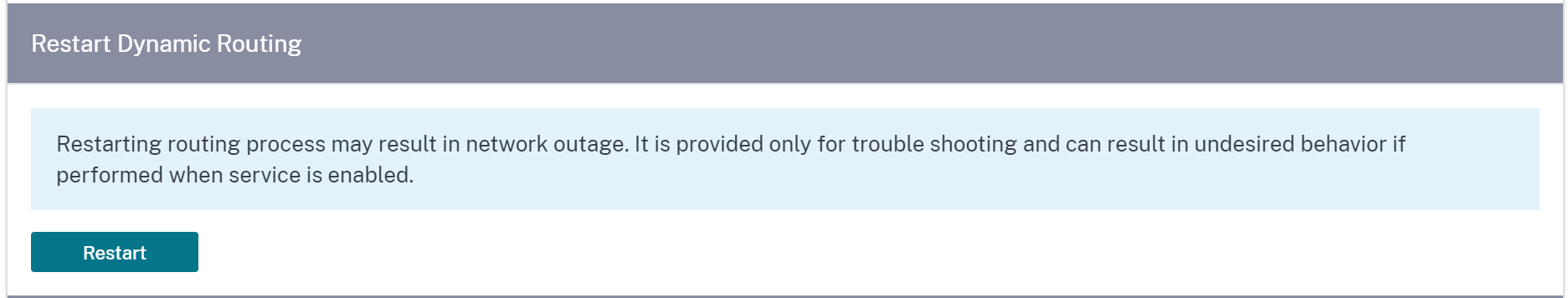
Restart dynamic routing
You can restart the dynamic route learning process through OSPF and BGP routing protocols. The restart dynamic routing option is provided for troubleshooting only.
Warning
Restarting dynamic routing might result in network outage.
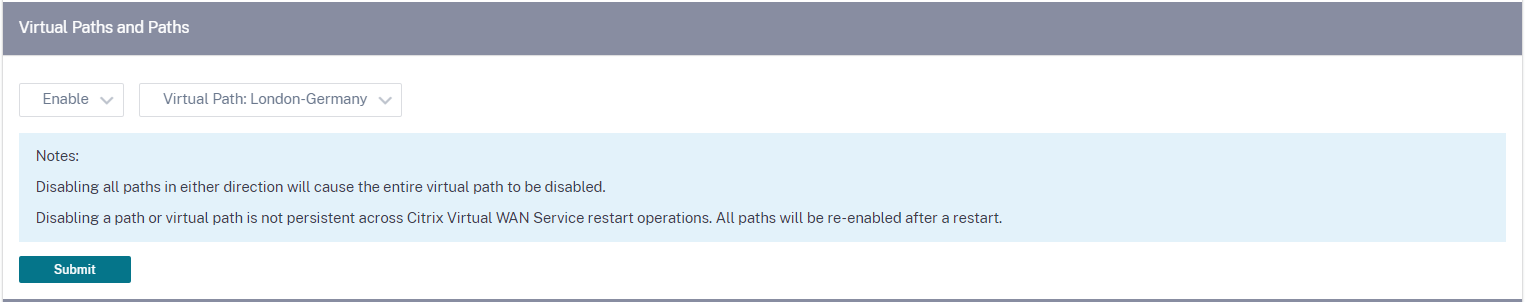
Virtual paths
You can choose to enable or disable the virtual path between 2 sites. You can either choose the underlying individual paths, in either directions, or the overlay virtual path. Disabling individual paths, disables the entire virtual path.
Note
All paths are re-enabled after restarting the Citrix Virtual WAN Service.
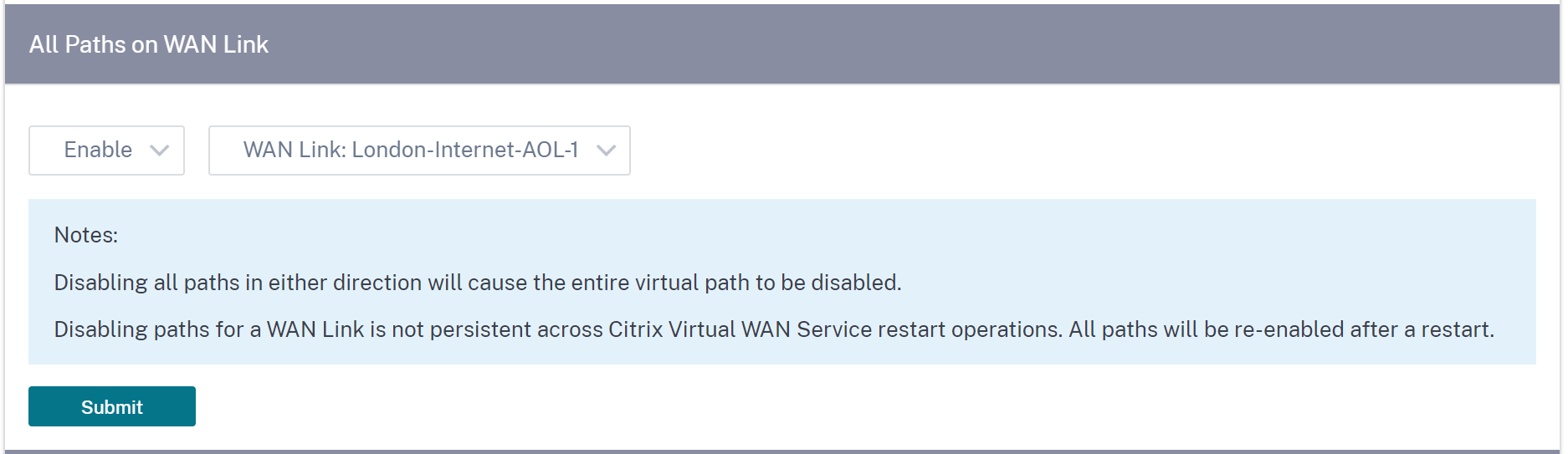
All paths on WAN link
You can choose to enable or disable WAN links between 2 sites Disabling all WAN links, disables the Virtual path.
Note
All the WAN links are re-enabled after restarting the Citrix Virtual WAN Service.
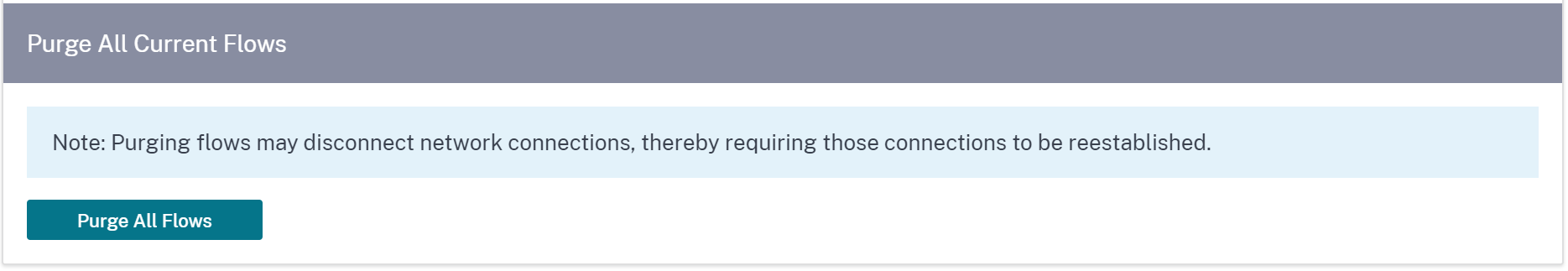
Purge all current flows
Purging flows ends all the current flows, clears the flow tables, re-establishes flow connections, and repopulates the flow table.
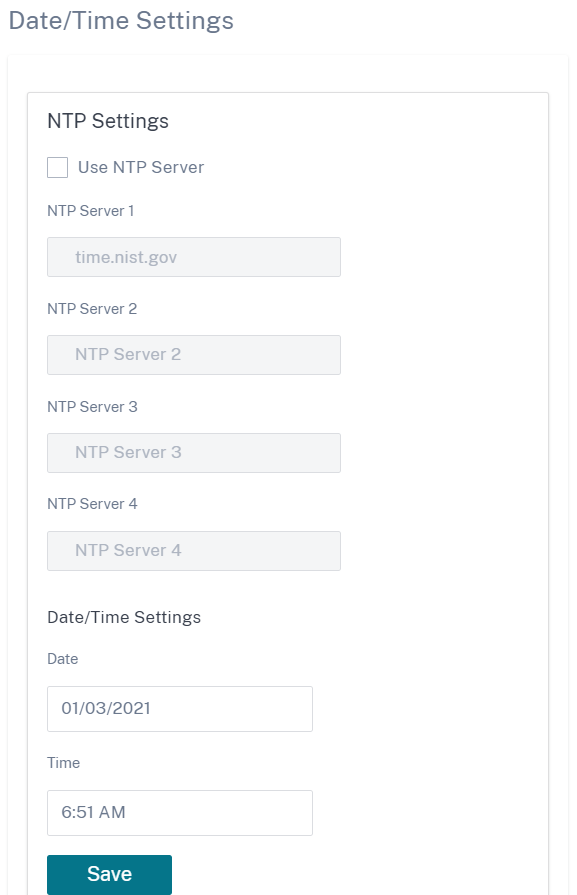
Date and time
You can change the date and time of the appliance either manually or by using an NTP server. To configure date and time manually, ensure that the Use NTP server option is not selected and provide the date and time.
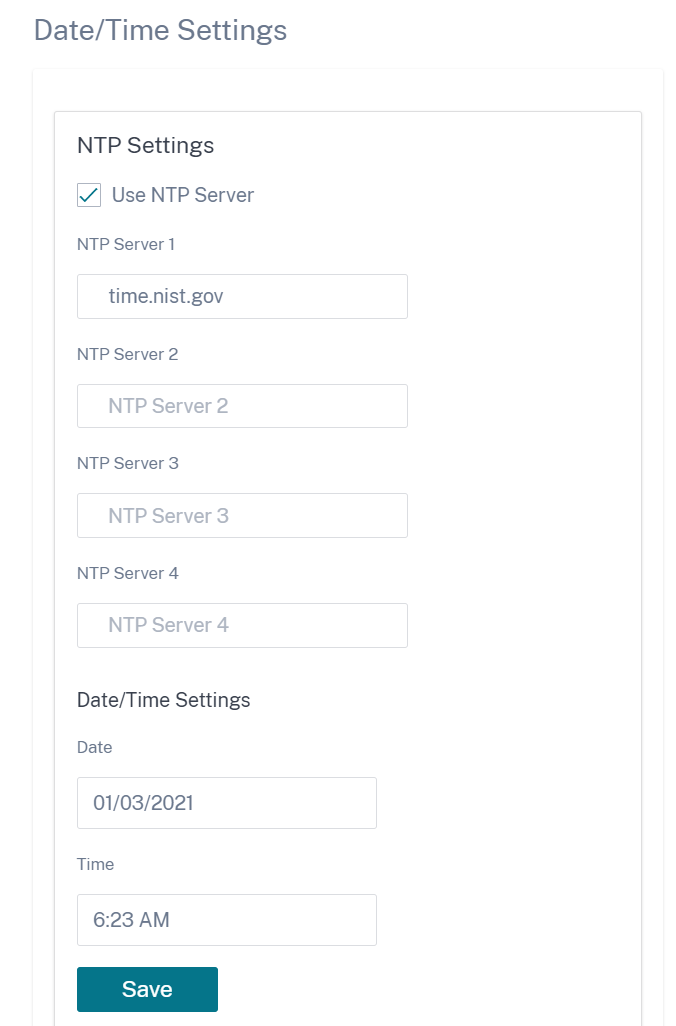
If you select the Use NTP server option, then you cannot manually enter a current date and time. You can specify up to 4 NTP servers, but you must specify at least one. These act as backup NTP servers, if one server is down the appliance automatically synchronizes with the other NTP server. If you specify a domain name for an NTP server, you must also configure a DNS server unless you have already done so.
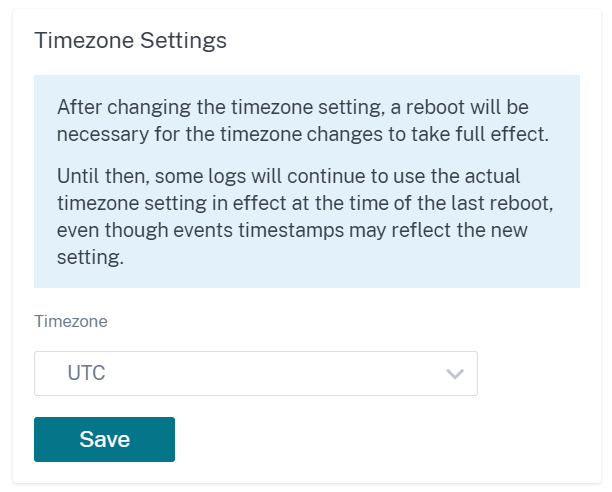
If the time zone has to be changed, change it before setting the date and time, or else your settings do not persist. Reboot the appliance after changing the time zone.
Syslog server settings
You can configure Syslog server settings of SD-WAN appliances using Citrix SD-WAN Orchestrator for On-premises. By enabling Syslog settings, you can send system alerts and event details of SD-WAN appliances to an external Syslog server. However, you must select the event type on the SD-WAN appliance UI by navigating to Configuration > Appliance Settings > Logging/Monitoring > Alarm Options. For more information, see Configure Alarms.
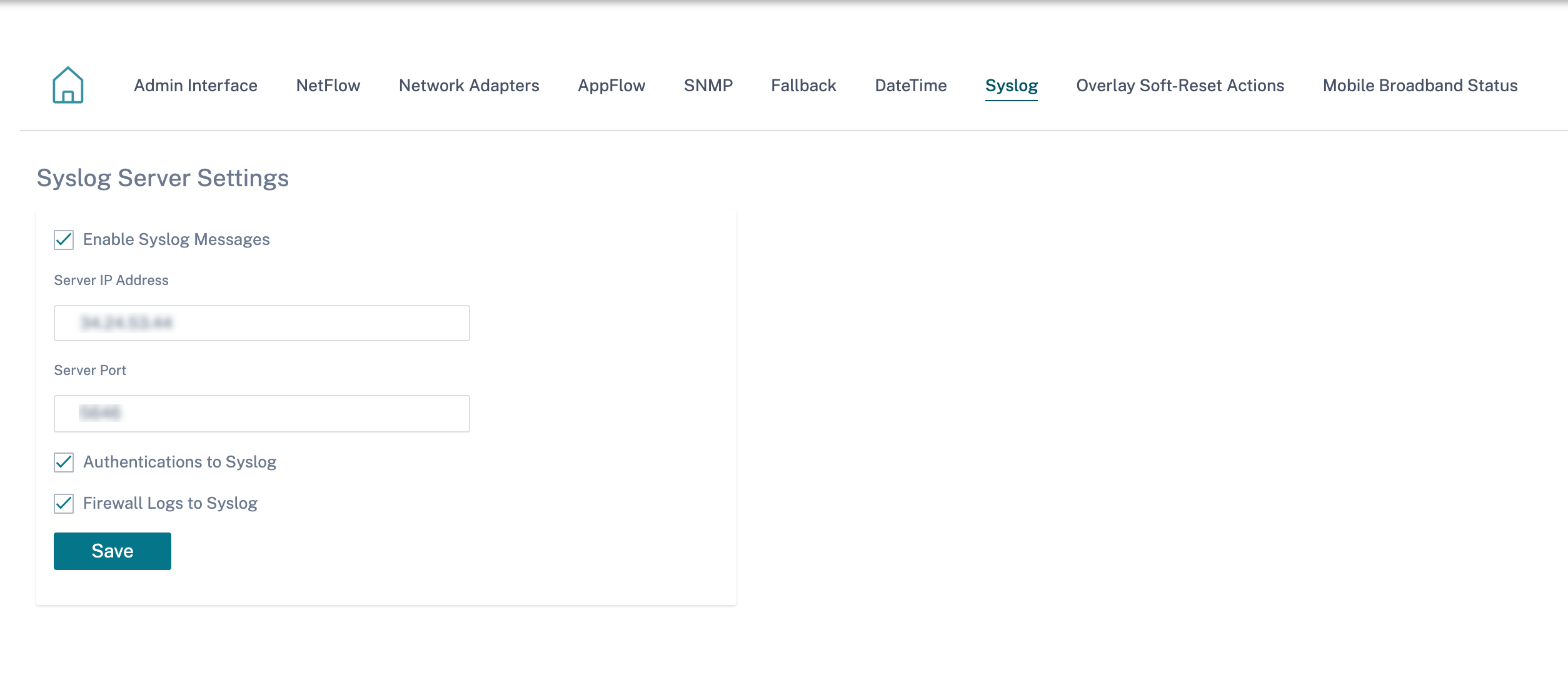
The following Syslog server settings are configurable through Citrix SD-WAN Orchestrator for On-premises:
- Enable Syslog Messages: Enable or disable sending logs or event messages to Syslog server.
- Server IP Address: IP address of the Syslog server.
- Server Port: Port number of the Syslog server.
- Authentication to Syslog: Enable or disable sending authentication logs or event messages to the Syslog server.
- Firewall Logs to Syslog: Enable or disable sending firewall logs to the Syslog server.
Certificate authentication
Citrix SD-WAN Orchestrator for On-premises ensures that secure paths are established between appliances in the SD-WAN network by using security techniques such as network encryption and virtual path IPsec tunnels. In addition to the existing security measures, certificate based authentication is introduced in Citrix SD-WAN Orchestrator for On-premises.
Certificate authentication allows organizations to use certificates issued by their private Certificate Authority (CA) to authenticate appliances. The appliances are authenticated before establishing the virtual paths. For example, if a branch appliance tries to connect to the data center and the certificate from the branch does not match with the certificate that the data center expects, the virtual path is not established.
The certificate issued by the CA binds a public key to the name of the appliance. The public key works with the corresponding private key possessed by the appliance identified by the certificate.
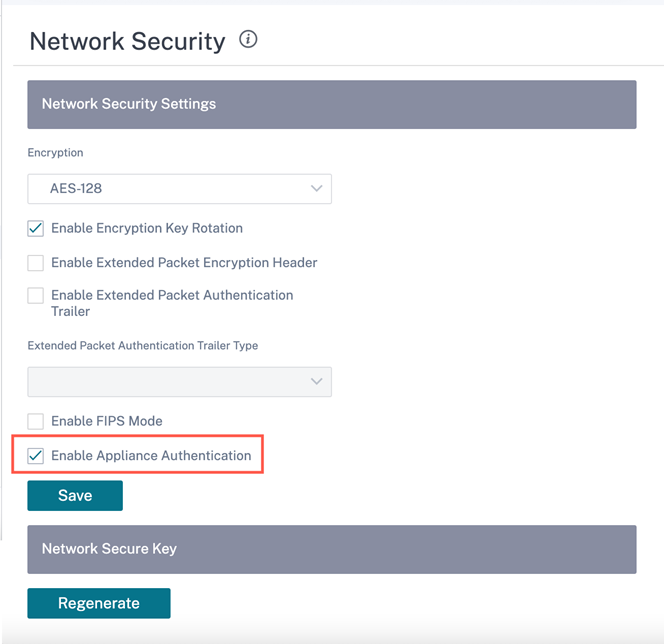
To enable appliance authentication, at network level, navigate to Configuration > Security > Network Security and select Enable Appliance Authentication. Click Save.
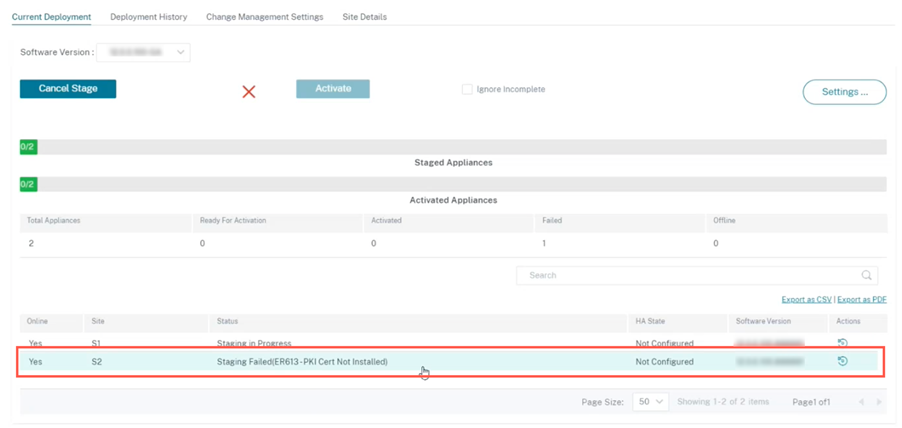
During deployment, if the appliance authentication is enabled but a PKI certificate is not installed in the appliance, then the staging shows failed status.
View certificate
You can go to the device detail page to verify if the PKI Certificate is installed or not. To do that, navigate to Configuration > Network Home > click the Action symbol for the site you want to verify the certificate > click View Details.
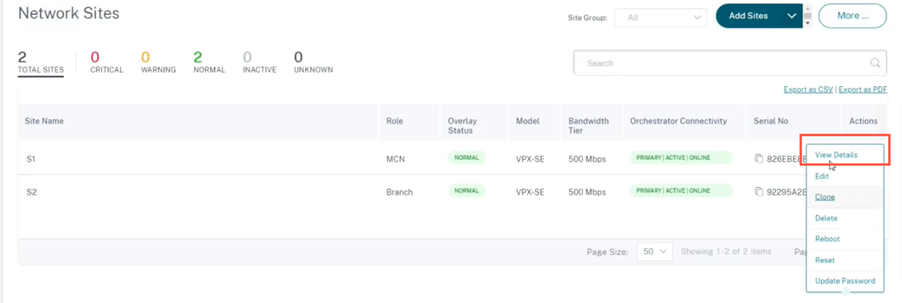
The following screen populates with the site and device details:
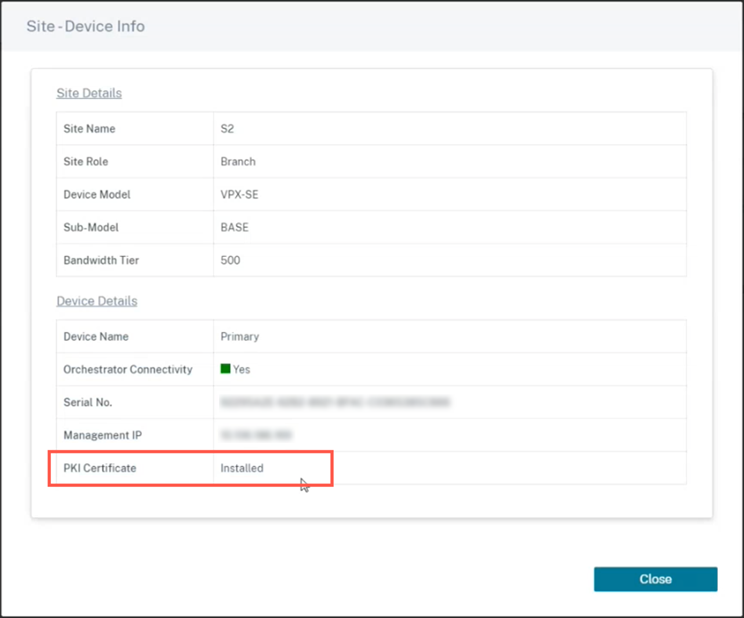
Under the Device Details section, you can view the PKI certificate installation status.
Upload identity bundle
The Identity bundle includes a private key and the certificate associated with the private key. You can upload the appliance certificate issued by the CA into the appliance. The certificate bundle is a PKCS12 file, with .p12 extension. You can choose to protect it with a password. Drag and drop the PKCS12 file, enter a password and click Upload. If you leave the password field blank, it is treated as no password protection.

Upload certificate authority bundle
Upload the PKCS12 bundle that corresponds to the certificate signing authority. The certificate authority bundle includes the complete chain of signatures, the root, and all the intermediate signatory authority. Drag the PKCS12 bundle and click Upload.

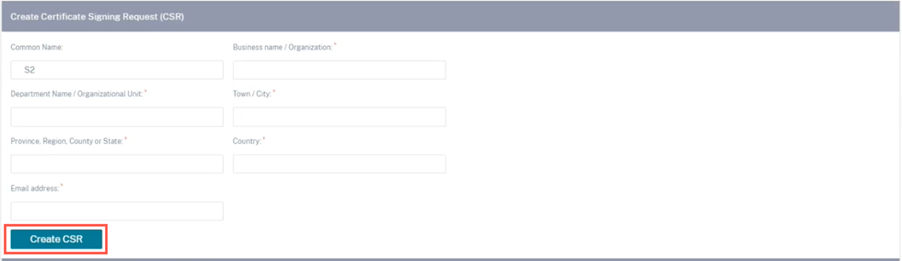
Create certification signing request
The appliance can generate an unsigned certificate and create a Certificate Signing Request (CSR). To create a CSR for an appliance, provide the organization name, unit, town/city, province/region/county/city, country, and email address. The appliance common name is the site name that is auto populated and non-editable. Click Create CSR.
Manage certificate signing request
Once the CSR is generated successfully from the back end, you need to download the CSR from the appliance and get it signed by its CA, upload it back to the appliance in PEM or DER formats. This is used as an Identity certificate for the appliance. First upload the CA to sign the certificate.

Once the CA is uploaded, upload the signed CSR.

Certificate revocation list manager
A Certificate Revocation List (CRL) is a published list of certificate serial numbers that are no longer valid in the network. The CRL file is periodically downloaded and stored locally on all the appliance. When a certificate is being authenticated the responder examines the CRL to see if the initiators certificate was revoked already. Citrix SD-WAN™ currently supports version 1 CRLs in PEM and DER format.
To enable CRL, select the CRL enabled check box. Provide the location where the CRL file is maintained. HTTP, HTTPS, and FTP locations are supported. Specify the time interval to check and download the CRL file, the range is 1–1440 minutes. Click Upload Settings.

Note
The reauthentication period for a virtua1 path can be between 10–15 minutes, if the CRL update interval is set to a shorter duration, the updated CRL list might include a currently active serial number. Make an actively revoked certificate available in your network for a short duration.
Mobile broadband settings
Citrix SD-WAN Orchestrator for On-premises allows you to connect a Citrix SD-WAN appliance from your branch site to a network using a mobile broadband connection.
To configure the mobile broadband settings, at the site level, navigate to Configuration > Appliance Settings > Mobile Broadband Settings.
Currently, the mobile broadband settings can be configured on Citrix SD-WAN 110 and Citrix SD-WAN-210 appliances.
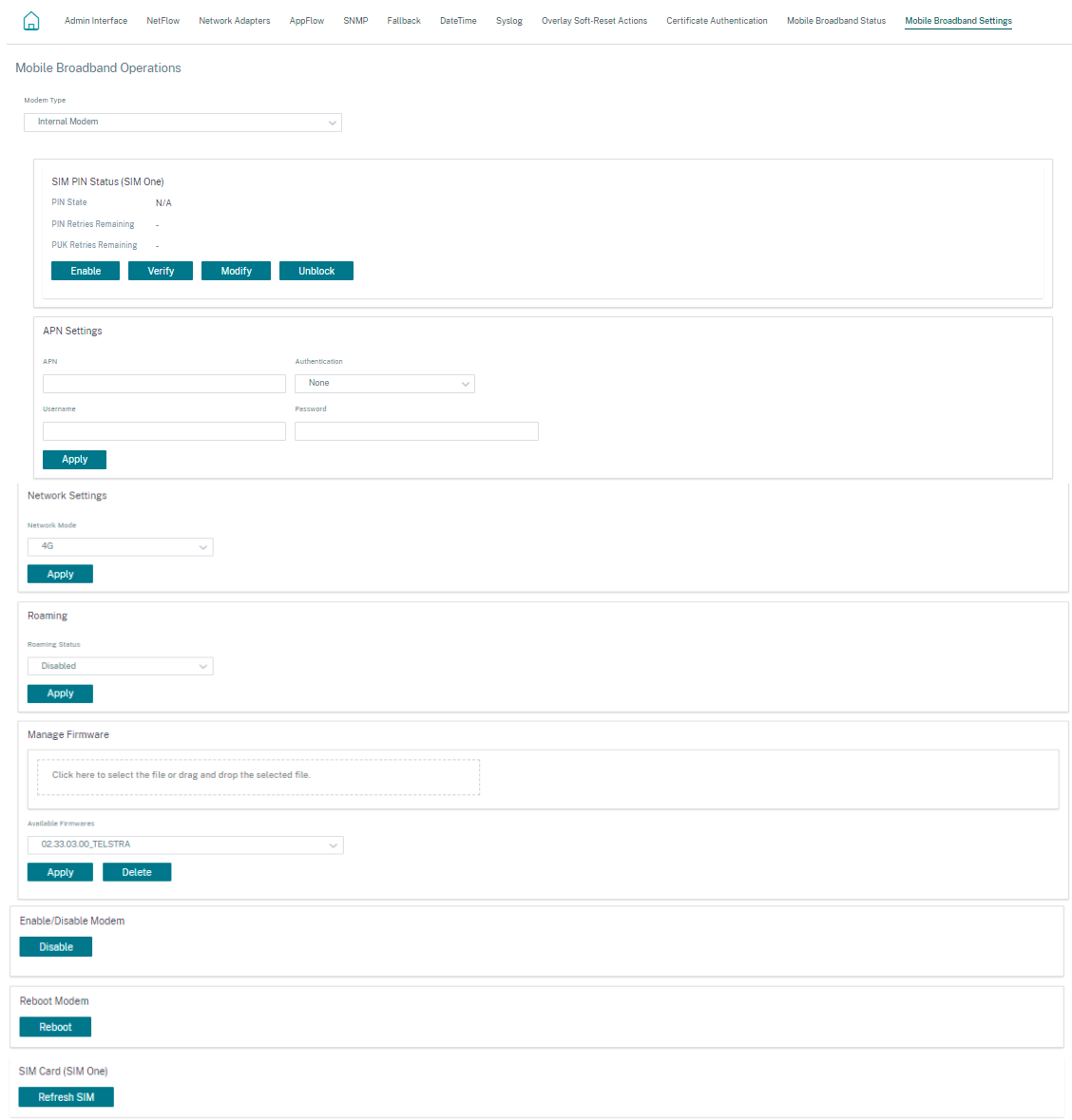
You can configure the following mobile broadband settings on Citrix SD-WAN Orchestrator for On-premises.
SIM PIN status
If you have inserted a SIM card that is locked with a PIN, the SIM state is Enabled. You cannot use the SIM card until it is verified using the SIM PIN. You can obtain the SIM PIN from the carrier. Click Verify.
Enter the SIM PIN provided by the carrier and click Verify.
Disable SIM PIN
You can disable SIM PIN functionality for a SIM for which SIM PIN is enabled and verified. Click Disable. Enter the SIM PIN and click Disable.
Enable SIM PIN
To enable the SIM PIN, click Enable. Enter the SIM PIN provided by the carrier and click Enable.
If the SIM PIN state changes to Enabled and Not Verified, it means that the PIN is not verified, and you cannot perform any operations until the PIN is verified.
Click Verify PIN. Enter the SIM PIN provided by the carrier and click Verify PIN.
Modify SIM PIN
Once the PIN is in Enabled and Verified state you can choose to change the PIN.
Click Modify. Enter the SIM PIN provided by the carrier. Enter the new SIM PIN and confirm it. Click Modify.
Unblock SIM
If you forget the SIM PIN, you can reset the SIM PIN using the SIM PUK obtained from the carrier.
To unblock a SIM, click Unblock. Enter the SIM PIN and SIM PUK obtained from the carrier and click Unblock.
Note
The SIM card gets permanently blocked with 10 unsuccessful attempts of PUK, while unblocking the SIM. Contact the carrier service provider for a new SIM card.
APN settings
To configure the APN settings, enter the APN, username, password, and authentication provided by the carrier. You can choose from PAP, CHAP, or PAPCHAP authentication protocols. If the carrier has not provided any authentication type, set it to None.
Network settings
You can select the mobile network on Citrix SD-WAN appliances that support internal modems.
Roaming
The roaming option is enabled by default on your devices. You can choose to disable it.
Manage Firmware
Every appliance that has LTE enabled will have a set of available firmware. You can select from the existing list of firmware or upload a firmware and apply it. If you are unsure of which firmware to use, select the AUTO-SIM option to allow the LTE modem to choose the most matching firmware based on the SIM card inserted in the appliance.
Note
Currently, the firmware can be applied only on SD-WAN SE 210 LTE appliances.
Enable/Disable modem
Enable or disable the modem depending on your intent to use the broadband functionality. By default, the modem is enabled.
Reboot modem
Reboots the modem. This process can take up to 3-5 minutes for the reboot operation to complete.
Refresh SIM
Use this option when you hot swap the SIM card to detect a new SIM card.
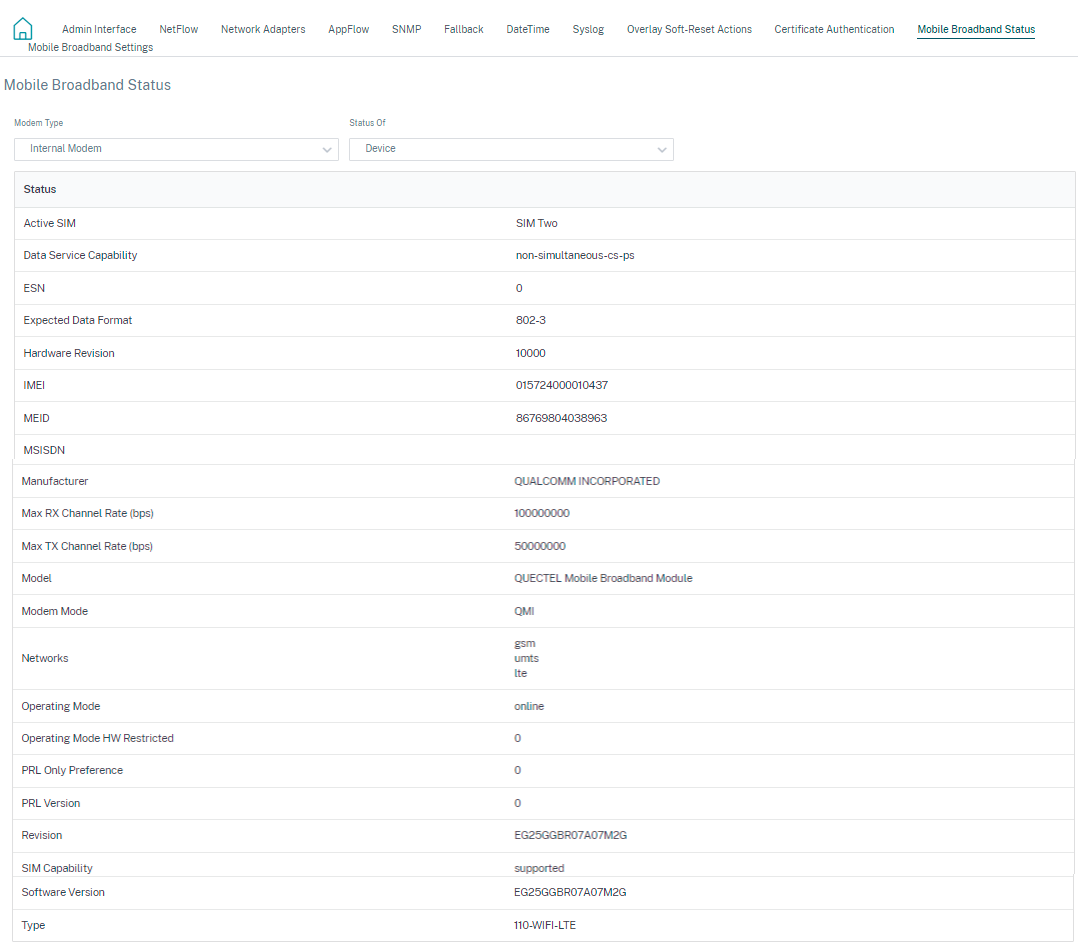
Mobile broadband status
The Mobile broadband status section displays the status of your broadband configuration settings. To view the mobile broadband status, at the site level, navigate to Configuration > Appliance Settings > Mobile Broadband Status. You can view the status of your device and the active SIM.
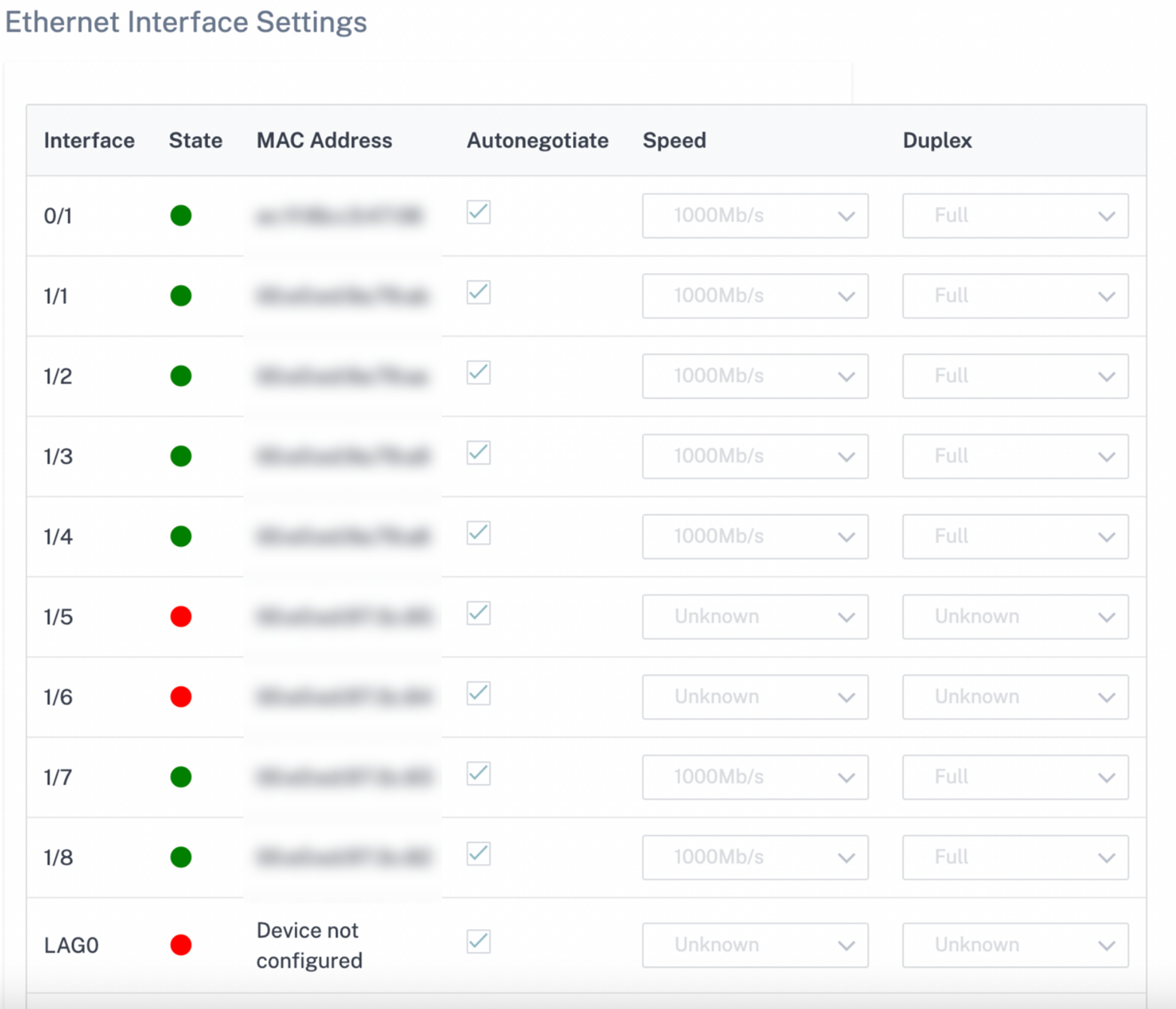
Ethernet Interface Settings
The Ethernet Interface status section displays the connectivity status of the ethernet ports, Interface type, MAC address, auto negotiate, and the duplex setting information. To view the ethernet interface settings, at the site level, navigate to Configuration > Appliance Settings > Ethernet Interface Settings. The ports that are administratively down are indicated in red color.
Note
This setting is currently available in read-only mode on the Citrix SD-WAN Orchestrator for On-premises UI. If you want to modify the Ethernet Interface settings, you can do so by using the new user interface for SD-WAN appliances.
In this article
- Administrative interface
- RADIUS authentication server
- TACACS+ authentication server
- NetFlow host settings
- Network adapters
- AppFlow host settings
- SNMP
- Fallback configuration
- Flows
- Date and time
- Syslog server settings
- Certificate authentication
- Mobile broadband settings
- Mobile broadband status
- Ethernet Interface Settings