-
-
-
-
Role-based access control
-
-
View recommendations and manage your ADCs and applications efficiently
-
-
Use ADM log messages for managing and monitoring your infrastructure
This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Role-based access control
NetScaler® ADM provides fine-grained, role based access control (RBAC), with which you can grant access permissions based on the roles of individual users within your enterprise. In this context, access is the ability to perform a specific task, such as view, create, modify, or delete a file. Roles are defined according to the authority and responsibility of the users within the enterprise. For example, one user might be allowed to perform all network operations, while another user can observe the traffic flow in applications and help creating configuration templates.
Roles are determined by in policies. After creating policies, you create roles, bind each role to one or more policies, and assign roles to users. You can also assign roles to groups of users.
A group is a collection of users who have permissions in common. For example, users who are managing a particular data center can be assigned to a group. A role is an identity granted to users or groups based on specific conditions. In NetScaler ADM, creating roles and policies are specific to the RBAC feature in NetScaler. Roles and policies can be easily created, changed, or discontinued as the needs of the enterprise evolve, without having to individually update the privileges for every user.
Roles can be feature based or resource based. For example, consider an SSL/security administrator and an application administrator. An SSL/security administrator must have complete access to SSL Certificate management and monitoring features, but must have read-only access for system administration operations. An application administrator must be able to access only the resources within the scope.
Example:
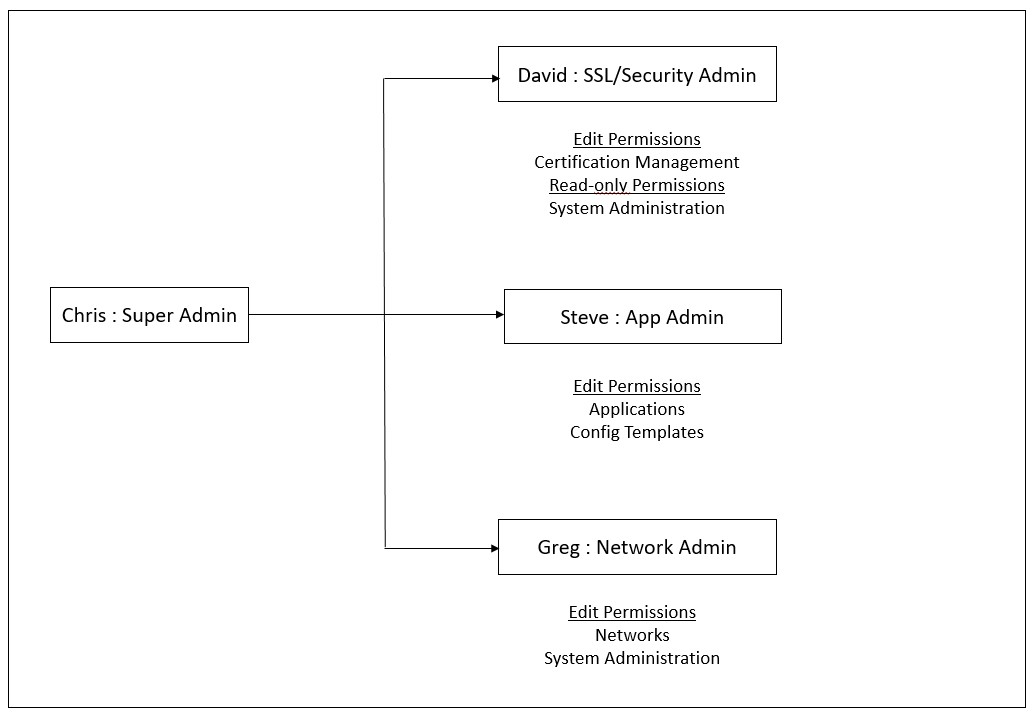
Chris, the ADC group head, is the super administrator of NetScaler ADM in his organization. Chris creates three administrator roles: security administrator, application administrator, and network administrator.
David, the security admin, must have complete access for SSL Certificate management and monitoring but also have read-only access for system administration operations.
Steve, an application admin, needs access to only specific applications and only specific configuration templates.
Greg, a network admin, needs access to system and network administration.
Chris also must provide RBAC for all users, irrespective of the fact that they are local or external.
NetScaler ADM users can be locally authenticated or can be authenticated through an external server (RADIUS/LDAP/TACACS). RBAC settings must be applicable to all users irrespective of the authentication method adopted.
The following image shows the permissions that the administrators and other users have and their roles in the organization.
Limitations
RBAC is not fully supported for the following NetScaler ADM features:
- Analytics - RBAC is not supported fully in the analytics modules. RBAC support is limited to instance level, and it is not applicable at application level in the Web Insight, SSL Insight, Gateway Insight, HDX™ Insight, and WAF Security Violations analytics modules. For example:
Example 1: Instance based RBAC (Supported)
An administrator who has been assigned a few instances can see only those instances under Web Insight > Instances, and only the corresponding virtual servers under Web Insight > Applications, because RBAC is supported at instance level.
Example 2: Application based RBAC (Not Supported)
An administrator who has been assigned a few applications can see all virtual servers under Web Insight > Applications but cannot access them, because RBAC is not supported at applications level.
-
StyleBooks – RBAC is not fully supported for StyleBooks.
-
In NetScaler ADM, StyleBooks and configuration packs are considered as separate resources. Access permissions, either view, edit, or both, can be provided for StyleBook and configuration packs separately or concurrently. A view or edit permission on configuration packs implicitly allows the user to view the StyleBooks, which is essential for getting the configuration pack details and creating configuration packs.
-
Access permission for specific StyleBook or configuration packs is not supported
Example: If there is already a configuration pack on the instance, users can modify the configuration on a target NetScaler instance even if they don’t have access to that instance.
-
-
Orchestration - RBAC is not supported for Orchestration.
Share
Share
This Preview product documentation is Cloud Software Group Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Cloud Software Group Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Cloud Software Group product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.