-
-
Authentication
-
-
-
Scenarios for Flexed or Pooled license expiry and connectivity issues behavior
-
Configure NetScaler Console as the Flexed or Pooled license server
This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Authentication
Users can be authenticated either internally by NetScaler Console, externally by an authenticating server, or both. If local authentication is used, the user must be in the NetScaler Console security database. If the user is authenticated externally, the user “external name” must match the external user identity registered with the authenticating server, depending on the selected authentication protocol.
NetScaler Console supports external authentication by RADIUS, LDAP, and TACACS servers. This unified support provides a common interface to authenticate and authorize all the local and external Authentication, Authorization, and Accounting server users who are accessing the system. NetScaler Console can authenticate users regardless of the actual protocols they use to communicate with the system. When a user attempts to access a NetScaler Console implementation that is configured for external authentication, the requested application server sends the user name and password to the RADIUS, LDAP, or TACACS server for authentication. If the authentication is successful, the user is granted access to NetScaler Console.
External authentication servers
NetScaler Console sends all authentication, authorization, and auditing service requests to the remote RADIUS, LDAP, or TACACS server. The remote authentication, authorization, and auditing server receive the request, validates the request, and sends a response to NetScaler Console. When configured to use a remote RADIUS, TACACS, or LDAP server for authentication, NetScaler Console becomes a RADIUS, TACACS, or LDAP client. In any of these configurations, authentication records are stored in the remote host server database. The account name, assigned permissions, and time-accounting records are also stored on the authentication, authorization, and auditing server for each user.
Also, you can use the internal database of NetScaler Console to authenticate users locally. You create entries in the database for users and their passwords and default roles. You can also select the authentication order for specific types of authentication. The list of servers in a server group is an ordered list. The first server in the list is always used unless it is unavailable, in which case the next server in the list is used. You can configure servers to include the internal database as a fallback authentication backup to the configured list of authentication, authorization, and auditing servers.
You can configure and add the following servers in NetScaler Console:
Authenticate users in NetScaler Console
You can authenticate your users in NetScaler Console in two ways:
-
Local users configured in NetScaler Console
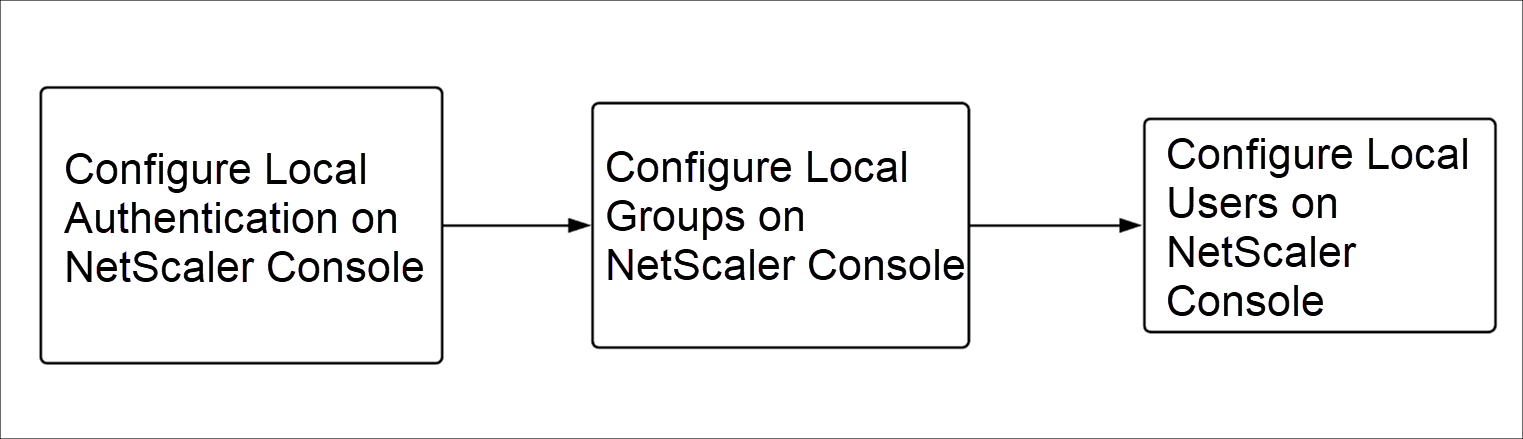
After configuration, the following is the workflow for user authentication in the local server.
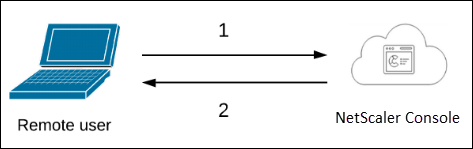
1 – The user logs on to NetScaler Console
2 – NetScaler Console prompts the users for credentials for authentication and checks if the credentials match in the NetScaler Console database.
-
Using external authentication servers
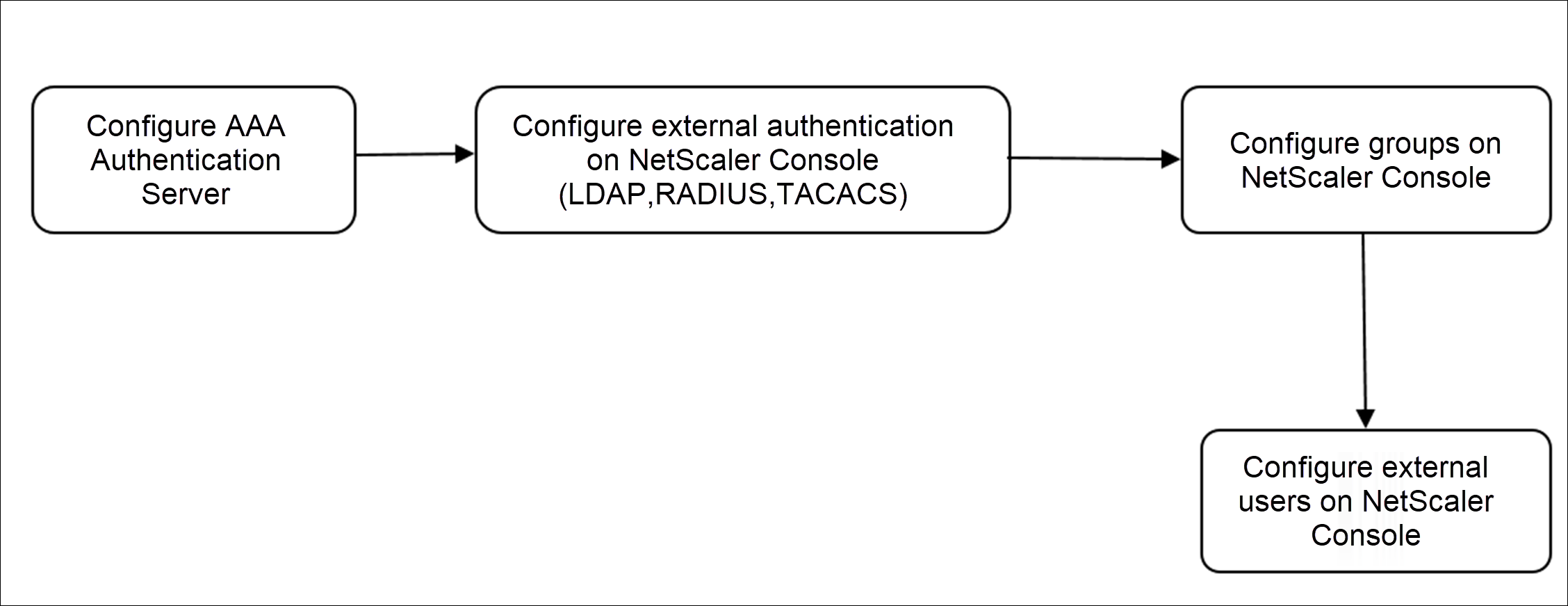
After configuration, the following is the workflow for user authentication in the external authentication, authorization, and auditing server:
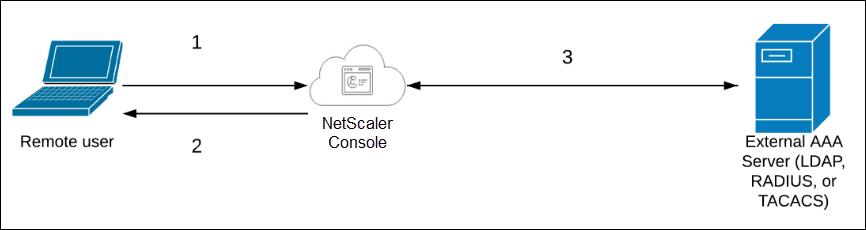
1 – The user connects with NetScaler Console
2 – NetScaler Console prompts the user for credentials
3 – NetScaler Console validates the user credentials with the external authentication, authorization, and auditing server. If the validation is successful, the user can continue to log on
Share
Share
This Preview product documentation is Cloud Software Group Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Cloud Software Group Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Cloud Software Group product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.