-
Low-touch onboarding of NetScaler instances using Console Advisory Connect
This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Bot
A bot is a software program that automatically performs certain actions over and over at a much faster rate than a human. Over 35 percent of your web traffic comprises bots and 80 percent of organizations suffer from bot attacks. They can interact with a webpage, submit forms, click links, scan text, or download content. Bots can even access videos, post comments, and tweet on social media platforms. Some bots can even hold basic conversations with human users. These bots are known as chatbots.
A bot that performs a needful or helpful service such as customer service, chatbots, search engine crawlers are known as good bots. Some malicious bots can scrape or download content from a website, steal user credentials, spread spam content, and perform various other kinds of cyberattacks. These malicious bots are known as bad bots. It is essential to identify bad bots and protect your appliance from advanced security attacks. You can achieve this using a bot management system.
For more information on Bot, see Bot Management.
Configure bot detection techniques in NetScaler Console
Note:
You can also use the Unified Security dashboard to configure protections, enable analytics, and deploy the protections on your application. For more information, see Unified Security dashboard.
In NetScaler Console, you can:
-
Configure bot detection techniques and deploy them on the NetScaler instances build 13.0 36.27 or later with premium license.
-
View bot analytics by enabling the Bot Security Violations option for the existing virtual servers configured with bot detection techniques either through StyleBook or directly from the NetScaler instance.
Along with the existing StyleBook configuration, this enhancement further simplifies the process to configure the bot detection techniques and deploy on the NetScaler instances.
-
Navigate to Settings > Analytics Configuration.
-
Under Virtual Server Analytics Summary, click Configure Analytics.
-
Select the virtual servers and click Enable Security & Analytics.
-
In the Enable Security & Analytics page, under Security, click Bot Protections.
-
Select the bot options, configure, and click Deploy on NetScaler(s).
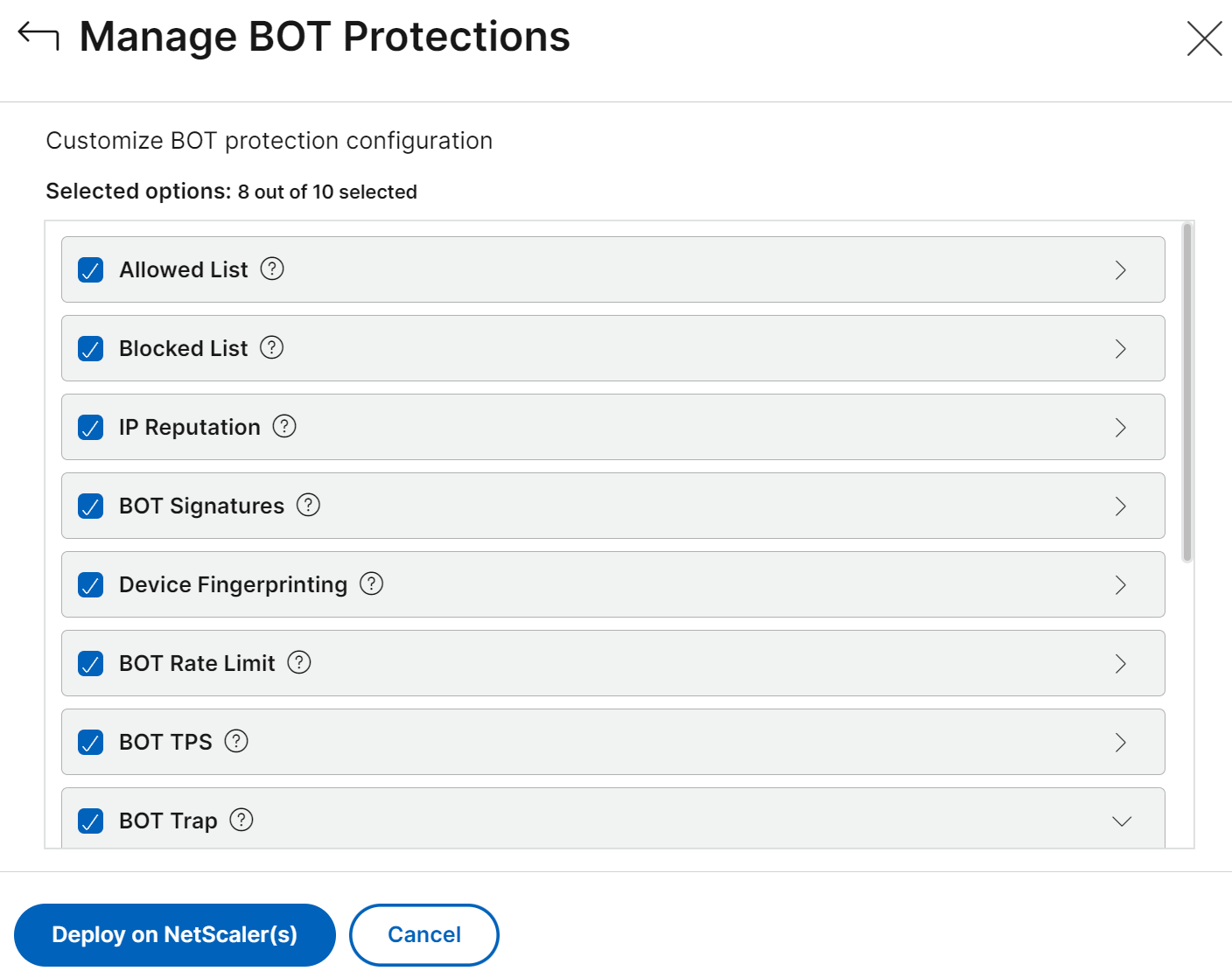
A dialog box appears that the current configuration replaces the existing configuration for the selected applications. Click Yes, continue.
After the configuration is successfully deployed, the All Virtual Servers page shows the configuration details.
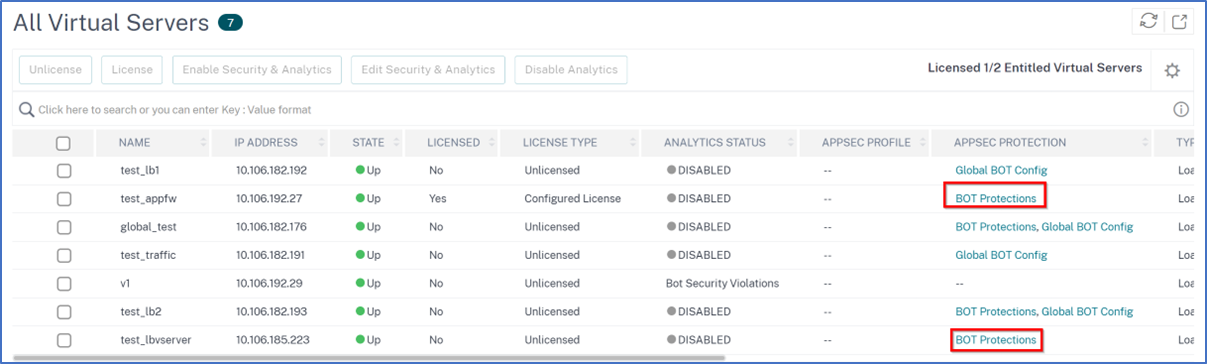
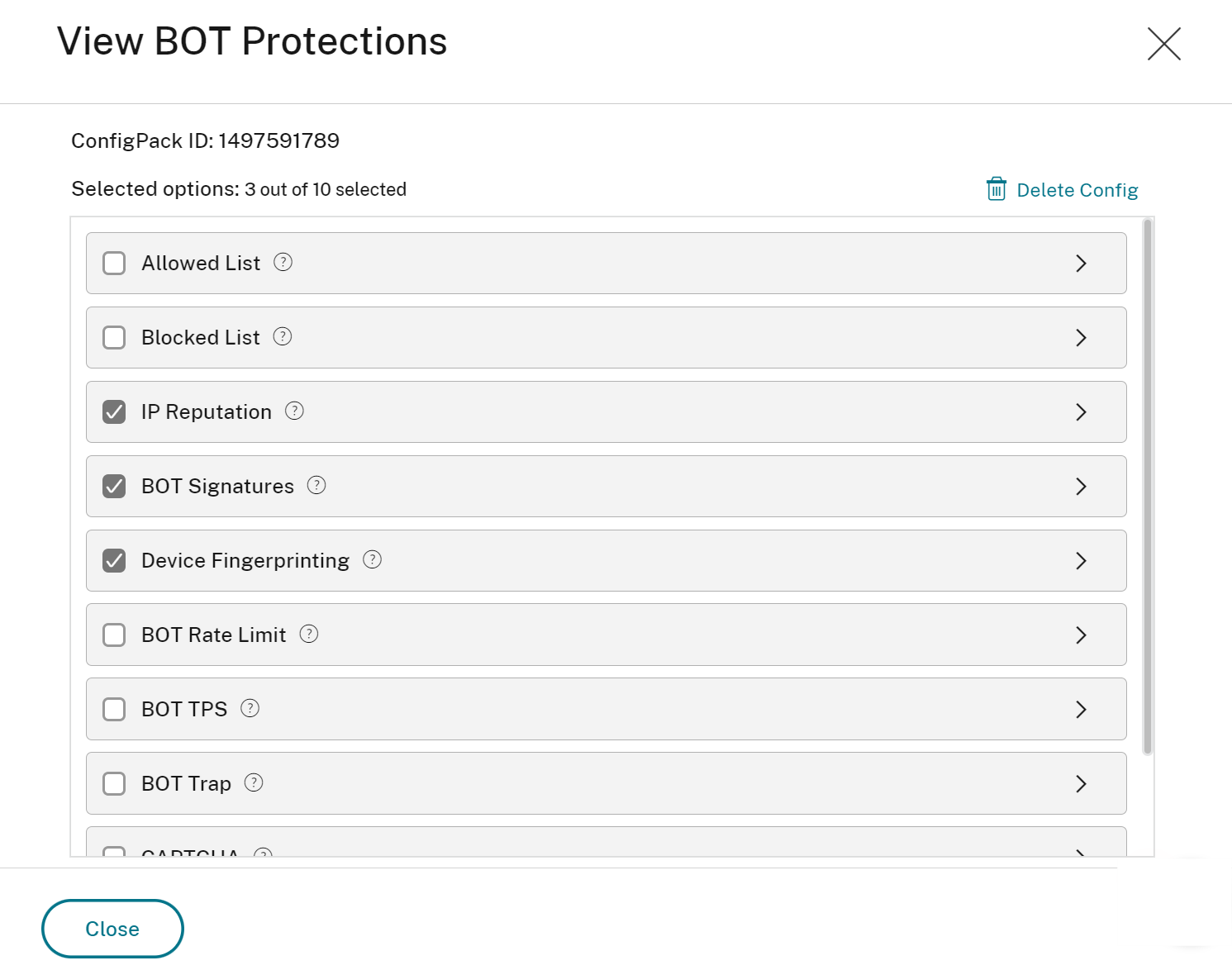
Click Bot Protections to view the configuration in read-only mode.
Additionally, you can also customize the global bot configuration details such as:
-
Enable or disable the signature auto-update to get the latest signatures that provide better protection and traffic management from both good and bad bots.
-
Configure the trap URL that is effective in blocking attacks from automated bots.
-
-
Under Advanced Settings (optional), click the Global BOT config to customize the settings, and then click Deploy on NetScaler(s).
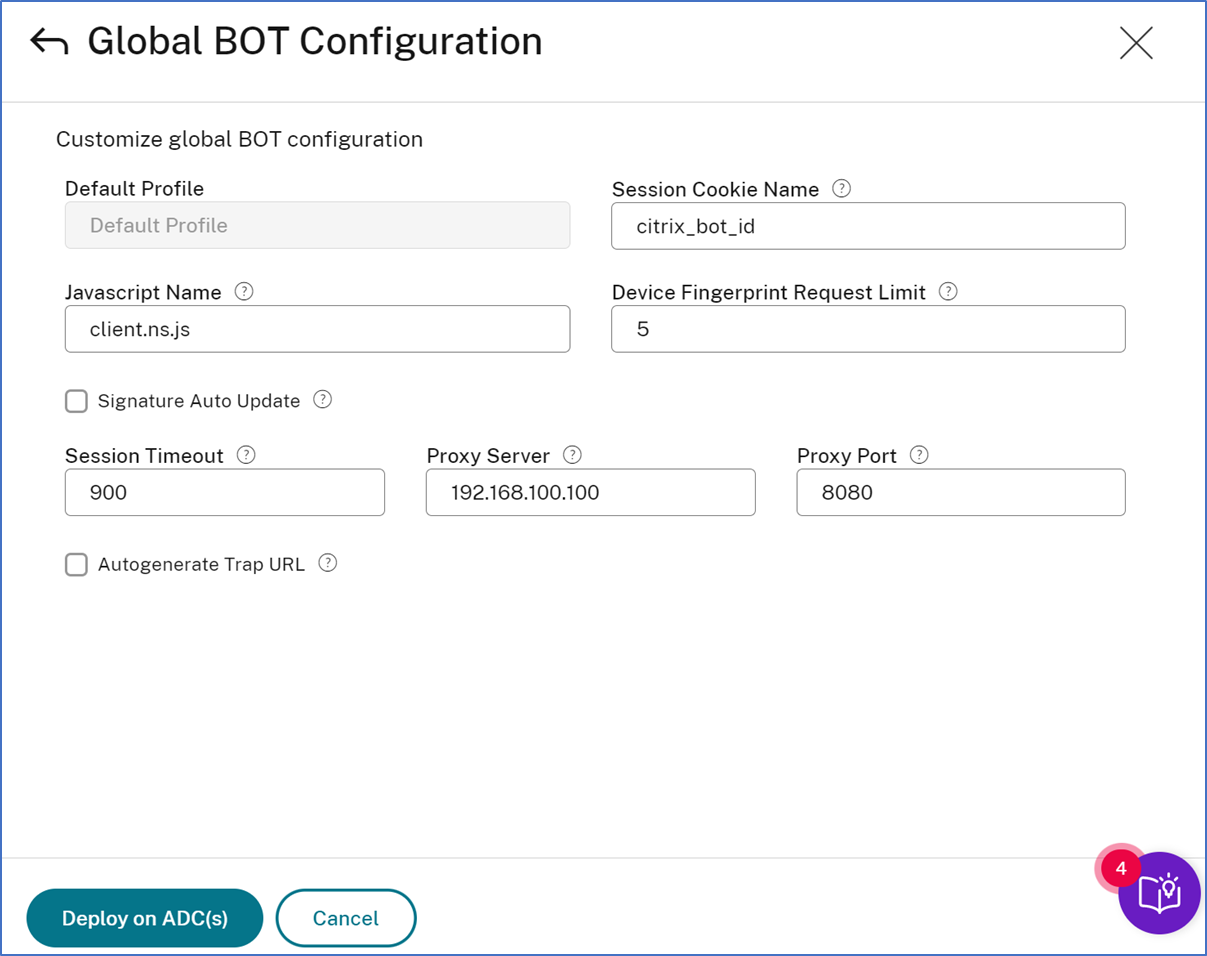
A dialog box appears that the current configuration replaces the existing configuration for the selected applications. Click Yes, continue.
You can also edit configuration by selecting the virtual server from the All Virtual Servers page and clicking the Edit Security & Analytics option.
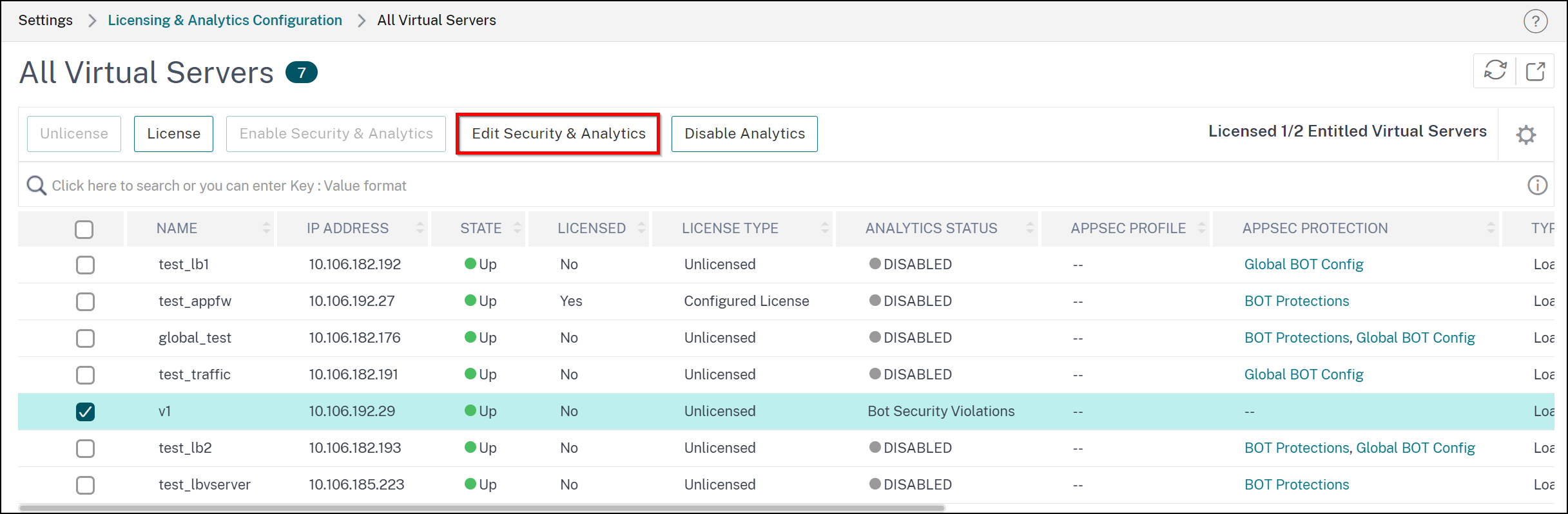
Points to note:
-
You can also enable Bot Security Violations to view bot analytics for the virtual servers that are already configured with bot detection techniques.
-
If you edit any configuration, the same gets replaced with the existing configuration and applied to all applications.
-
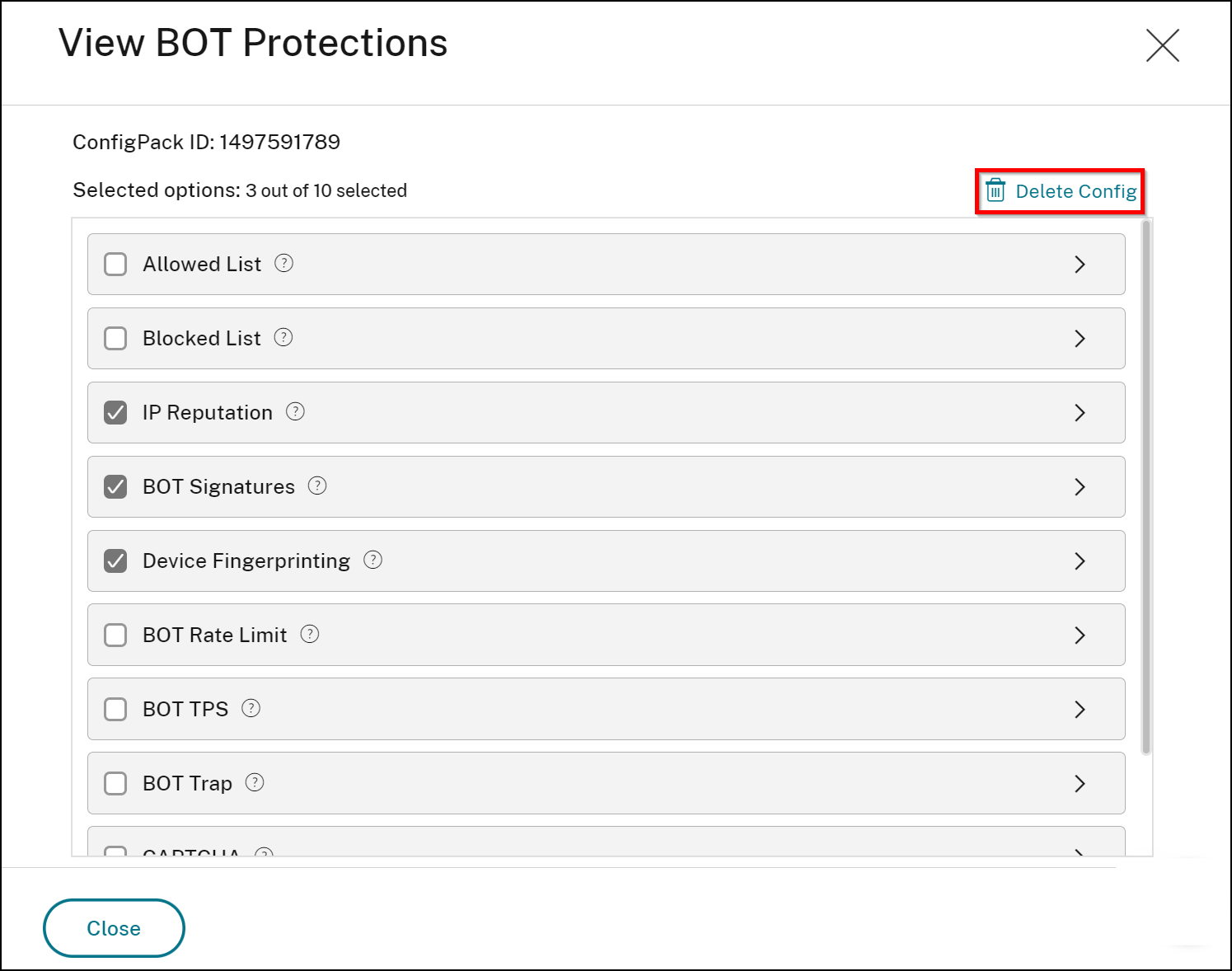
You can delete the configuration. In the All Virtual Servers page, click Bot Protections from the Appsec Protection column, and click Delete Config.
-
If you delete a configuration, it also gets removed immediately from all virtual servers that are using the configuration.
Configure bot security violations in NetScaler Console
You can also continue to enable Bot Security Violations on the existing virtual servers that are already configured with bot detection techniques either through StyleBook or directly from the NetScaler instance to view bot insights in NetScaler Console.
To enable Bot Security Violations:
-
Navigate to Infrastructure > Instances > NetScaler and select the instance type. For example, VPX.
-
Select the instance and from the Select Action list, select Configure Analytics.
-
Select the virtual servers and click Enable Security & Analytics.
-
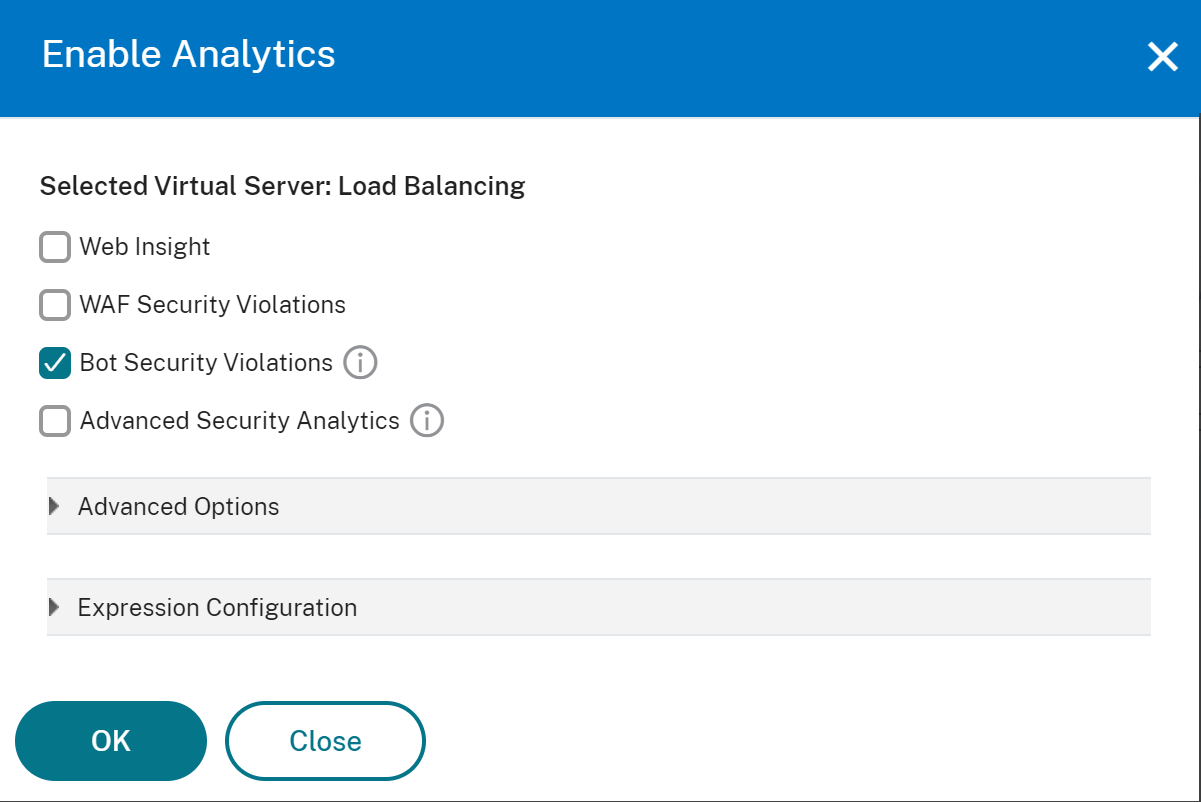
On the Enable Analytics window:
-
Select Bot Security Violations
-
Under Advanced Option, select Logstream.
-
Click OK.
Note
- If you are not on the Flexed license and you select virtual servers that are not licensed, then NetScaler Console first licenses those virtual servers and then enables analytics.
-
After enabling Bot Security Violations, navigate to Security > Security Violations. Under Bot, select the application and view details. For more details, see Application overview.
Share
Share
This Preview product documentation is Cloud Software Group Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Cloud Software Group Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Cloud Software Group product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.