System requirements
Before you install NetScaler Console, you must understand the software requirements, browser requirements, port information, license information, and limitations.
Requirements for NetScaler Console
| Component | Requirement |
|---|---|
| RAM | 32 GB |
| Virtual CPU | 8 CPUs |
| Note: We recommend using solid-state drive (SSD) technology for NetScaler Console deployments. | |
| Storage space | The default storage space required is 120 GB. The actual storage requirement depends on NetScaler Console sizing estimation. |
| If your NetScaler Console storage requirement exceeds 120 GB, you to have to attach an additional disk. You can add only one additional disk. | |
| We recommend that you estimate storage and attach additional disks at the time of initial deployment. | |
| For more information, see How to Attach an Additional Disk to NetScaler Console. | |
| Virtual network interfaces | 1 |
| Throughput | 1 Gbps or 100 Mbps |
Requirements for NetScaler Console on-prem agent
| Component | Requirement |
|---|---|
| RAM | 32 GB |
| Virtual CPU | 8 CPUs |
| Storage space | 30 GB |
| Virtual network interfaces | 1 |
| Throughput | 1 Gbps |
Note
AMD processor is supported in:
NetScaler Console 13.1 build 4.43 or later.
NetScaler agent 13.1 build 17.42 or later.
Minimum NetScaler version required for NetScaler Console features
Important
The NetScaler Console version and build must be equal to or higher than your NetScaler version and build. For example, if you have installed NetScaler Console 12.1 Build 50.39, then ensure you have installed NetScaler 12.1 Build 50.28/50.31 or earlier.
| NetScaler Console Feature | NetScaler Software Version |
|---|---|
| StyleBooks | 10.5 and later |
| OpenStack/CloudStack Support | 11.0 and later, if a partition is required |
| 11.1 and later, if a partition on a shared virtual LAN is required | |
| NSX Support | 11.1 Build 47.14 and later (VPX) |
| Mesos/Marathon Support | 10.5 and later |
| Backup/Restore | For NetScaler, 10.1 and later |
| For NetScaler SDX, 11.0 and later | |
| Monitoring/Reporting and Configuration using Jobs | 10.1 and later |
| Analytics Features | |
| Web Insight | 10.5 and later |
| HDX Insight | 10.1 and later |
| WAF Security Violations | 11.0.65.31 and later |
| Gateway Insight | 11.0.65.31 and later |
| Cache Insight | 10.5 and later* |
| SSL Insight | 12.0 and later |
* Integrated Cache Metrics are not supported in NetScaler Console with NetScaler instances running version 11.0 build 66.x.
Requirements for NetScaler Console analytics
Minimum Citrix Virtual Apps and Desktops versions required for NetScaler Console features
| NetScaler Console Feature | Citrix Virtual Apps and Desktops Version |
|---|---|
| HDX Insight | Citrix Virtual Apps and Desktops 7.0 and later |
Note
The NetScaler Gateway feature (branded as Access Gateway Enterprise for versions 9.3 and 10.x) must be available on the NetScaler instance. NetScaler Console does not support standalone Access Gateway Standard appliances.
NetScaler Console can generate reports for applications that are published on Citrix Virtual Apps or Citrix Virtual Desktops and accessed through Citrix Workspace. However, this capability depends on the operating system on which Workspace is installed. Currently, a NetScaler does not parse ICA traffic for applications or desktops that are accessed through Citrix Workspace running on iOS or Android operating systems.
Thin clients supported for HDX™ insight
-
Dell Wyse Windows based Thin Clients
-
Dell Wyse Linux-based Thin Clients
-
Dell Wyse ThinOS based Thin Clients
-
10ZiG Ubuntu-based Thin Clients
-
IGEL UD3 W7+ (M340)
-
IGEL UD3 W7 (M340C)
NetScaler instance license required for HDX insight
The data collected by NetScaler Console for HDX Insight depends on the version and licenses of the NetScaler instances being monitored. HDX Insight reports are displayed only for NetScaler Premium and Advanced appliances running release 10.5 and later.
| NetScaler License/Duration | 5 Minutes | 1 Hour | 1 Day | 1 Week |
|
|---|---|---|---|---|---|
| Standard | No | No | No | No | No |
| Advanced | Yes | Yes | No | No | No |
| Premium | Yes | Yes | Yes | Yes | Yes |
Supported hypervisors
The following table lists the hypervisors supported by NetScaler Console:
| Hypervisor | Versions |
|---|---|
| XenServer | 7.1, 7.4, and 8.0 |
| VMware ESX | 6.0, 6.5, 6.7, 7.0, 8.0 (from 14.1-21.x and later), and 8.0.2b (from 14.1-25.x and later) |
| Microsoft Hyper-V | 2012 R2, 2016, 2019, and 2022 |
| Generic KVM | RHEL 7.4, RHEL 8.0, Ubuntu 16.04, and Ubuntu 18.04 |
| Nutanix Hypervisor (AHV) | 6.5.2 (from 14.1-38.x and later) |
Supported operating systems and Workspace versions
The following table lists the operating systems supported by NetScaler Console, and the Citrix Workspace versions currently supported with each system:
| Operating System | Workspace Version |
|---|---|
| Windows | 4.0 Standard Edition |
| Linux | 13.0.265571 and later |
| Mac | 11.8, build 238301 and later |
| HTML5 | 1.5 |
| Chrome App | 1.5 |
Supported browsers
The following table lists the web browsers supported by NetScaler Console:
| Web Browser | Version |
|---|---|
| Microsoft Edge | 79 and later |
| Google Chrome | 51 and later |
| Safari | 10 and later |
| Mozilla Firefox | 52 and later |
Supported ports
NetScaler Console uses the NetScaler IP (known as NSIP) address to communicate with NetScaler. You can use an agent as an intermediary between the NetScaler instance and NetScaler Console. To establish a communication with these servers, open the required ports.
- For AppFlow and log stream communication from NetScaler to NetScaler Console, Subnet IP address (known as SNIP) is used.
- For license related communication from NetScaler to NetScaler Console, NSIP address is used.
- If the SNIP address is enabled for management access and if NetScaler is added in NetScaler Console by using SNIP address, then SNIP address is used as the source IP address for events and Syslogs.
Note
If you have configured NetScalers in High Availability mode, NetScaler Console uses NSIP to communicate with NetScaler and the required ports remain the same.
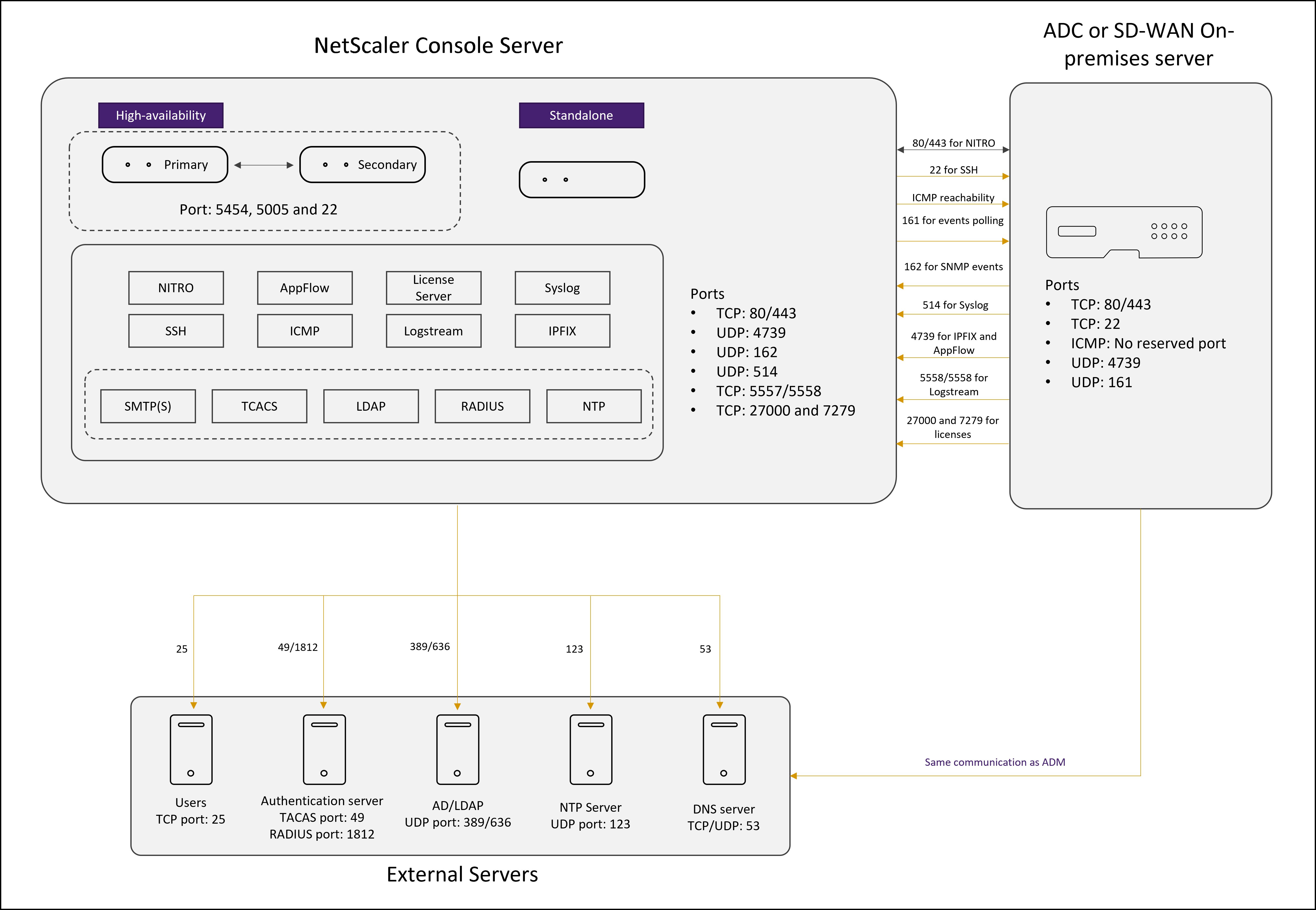
Network port diagram for agentless deployment:
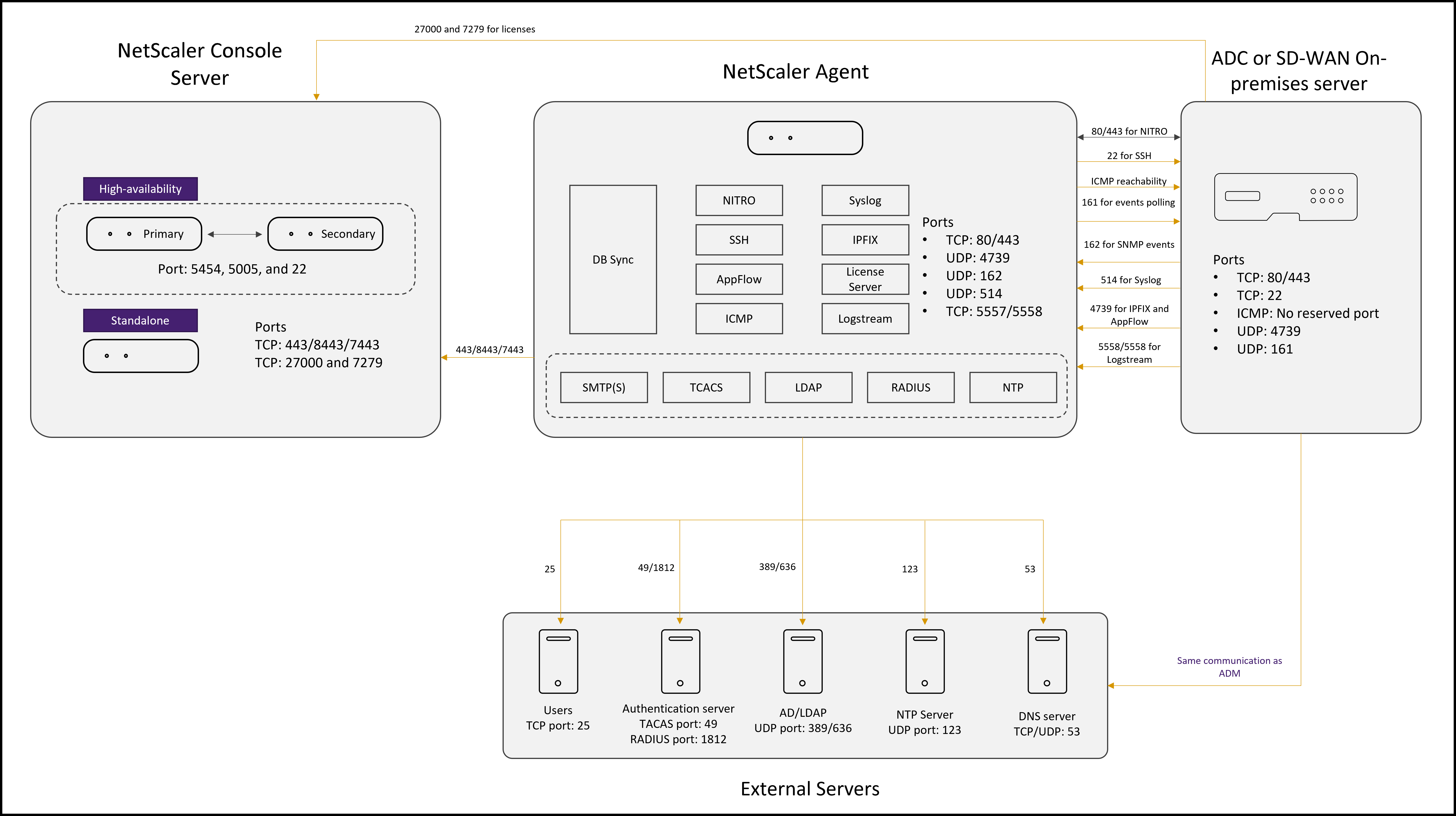
Network port diagram for the deployment that includes NetScaler® agent:
Network port diagram for the NetScaler Console High Availability deployment:
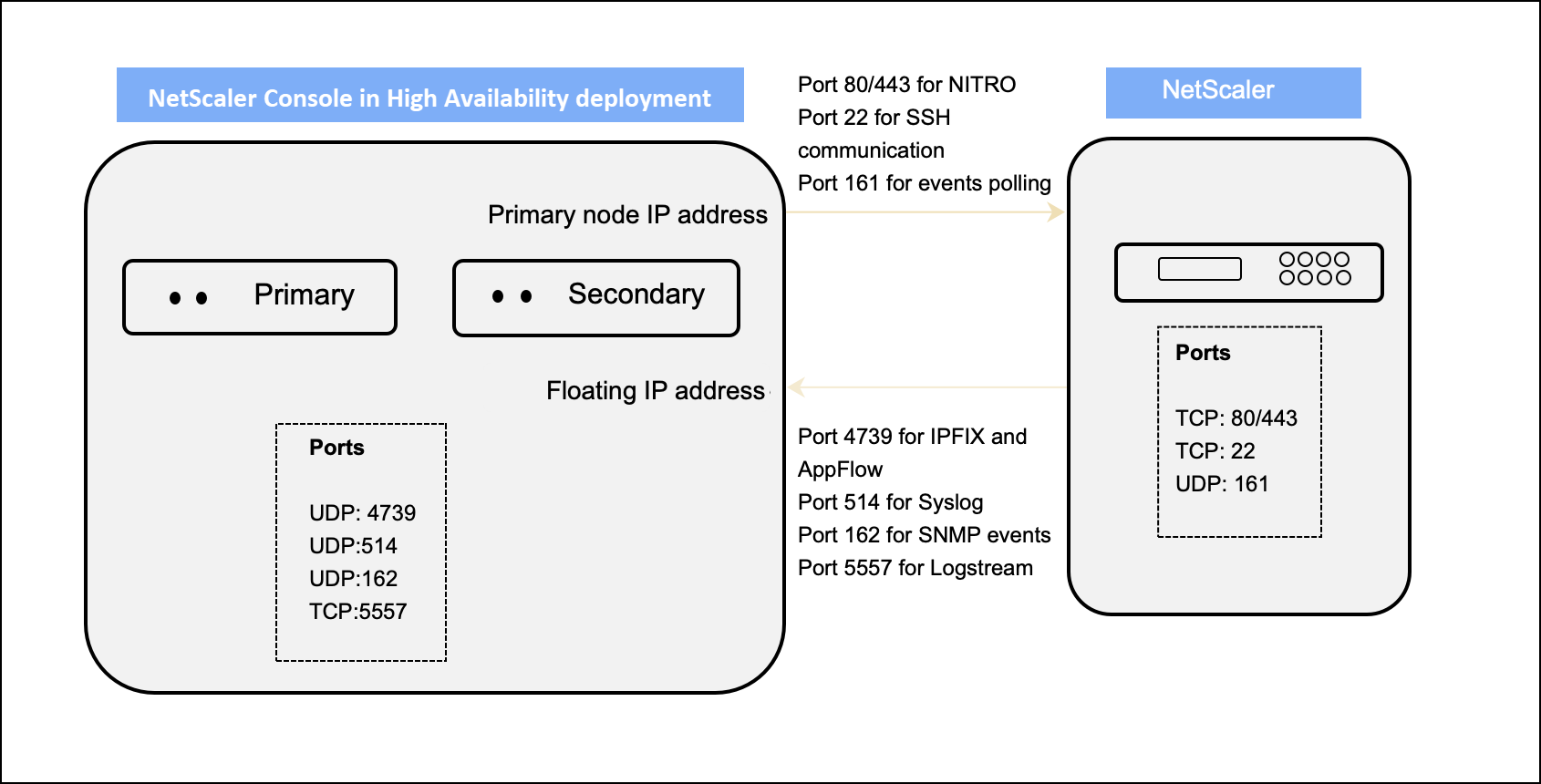
If two NetScaler Console servers are set up in high availability mode, when adding an instance:
- NetScaler Console communicates with NetScaler through the Primary IP address.
- NetScaler establishes connectivity with NetScaler Console through the NetScaler Console floating IP address. This implies that NetScaler directs all SNMP, Syslog, and Analytics traffic to the NetScaler Console floating IP address.
The following sections explain the required ports and their purpose:
Ports for the NetScaler Console server
The following table explains the required ports that must be open on the NetScaler Console server.
| Port | Type | Details | Direction of communication |
|---|---|---|---|
| 80/443/5454/22 | TCP | Default port for communication, and database synchronization in between NetScaler Console nodes in high availability mode. Note: This port is also used for NetScaler telemetry. | NetScaler Console primary node to NetScaler Console secondary node |
| 443/8443/7443 | TCP | Port for communication between NetScaler agent and NetScaler Console. | NetScaler agent initiates the communication with NetScaler Console. Then, NetScaler Console and agent interact with each other. |
| 27000 and 7279 | TCP | License ports for communication between NetScaler Console license server and NetScaler instance. These ports are also used for NetScaler pooled licenses. | NetScaler to NetScaler Console |
| 5005 | UDP | Port to exchange heartbeats between HA nodes. | NetScaler Console primary node to secondary node. NetScaler Console secondary node to primary node. |
| 5140 | UDP | Port to receive NetScaler Gateway telemetry data. | NetScaler to NetScaler Console |
If the NetScaler Console and NetScaler instances do not use an agent for communication, open the following ports on the NetScaler Console server:
| Port | Type | Details | Direction of communication |
|---|---|---|---|
| 80/443 | TCP | For NITRO communication from NetScaler Console to NetScaler instance. | NetScaler agent to NetScaler and NetScaler to NetScaler agent |
| 4739 | UDP | For AppFlow communication from NetScaler instance to NetScaler Console. | NetScaler to NetScaler agent |
| 162 | UDP | To receive SNMP events from NetScaler instance to NetScaler Console. | NetScaler to NetScaler agent |
| 514 | UDP | To receive syslog messages from NetScaler instance to NetScaler Console. | NetScaler to NetScaler agent |
| 5557/5558 | TCP | For logstream communication (for WAF Security Violations, Web Insight, and HDX Insight) from NetScaler to NetScaler Console. | NetScaler to NetScaler Console |
| 5563 | TCP | To receive NetScaler metrics (counters), system events, and Audit Log messages from NetScaler instance to NetScaler Console | NetScaler to NetScaler Console |
Ports for the agent
The following table explains the required ports that must be open on the agent.
| Port | Type | Details | Direction of communication |
|---|---|---|---|
| 80/443 | TCP | For NITRO communication from NetScaler Console to NetScaler instance. | NetScaler agent to NetScaler and NetScaler to NetScaler agent |
| 4739 | UDP | For AppFlow communication from NetScaler instance to NetScaler Console. | NetScaler to NetScaler agent |
| 162 | UDP | To receive SNMP events from NetScaler instance to NetScaler Console. | NetScaler to NetScaler agent |
| 514 | UDP | To receive syslog messages from NetScaler instance to NetScaler Console. | NetScaler to NetScaler agent |
| 5557/5558 | TCP | For logstream communication (for WAF Security Violations, Web Insight, and HDX Insight) from NetScaler to NetScaler Console. | NetScaler to NetScaler Console |
Ports for NetScaler instances
The following table explains the required ports that must be open on NetScaler instances.
| Port | Type | Details | Direction of communication |
|---|---|---|---|
| 80/443 | TCP | For NITRO communication from NetScaler Console to NetScaler instance. For NITRO communication between NetScaler Console servers in high availability mode. | NetScaler Console to NetScaler and NetScaler to NetScaler Console |
| 22 | TCP | For SSH communication from NetScaler Console to NetScaler instance. For synchronization between NetScaler Console servers deployed in high availability mode. And, this port is required for the SSH communication between the NetScaler Console agent and NetScaler. | NetScaler Console to NetScaler. Or, NetScaler agent to NetScaler. |
| No reserved port | ICMP | To detect network reachability between NetScaler Console and NetScaler instances, or the secondary NetScaler Console server deployed in high availability mode. | NetScaler Console to NetScaler |
| 161 | UDP | To poll events from NetScaler instances. | NetScaler Console to NetScaler |
Ports for NetScaler built-in agent
The following table explains the required ports that must be open for a NetScaler built-in agent.
| Port | Type | Details | Direction of communication |
|---|---|---|---|
| 443 | TCP | For all communication from NetScaler Console to NetScaler built-in agent | NetScaler Console to NetScaler built-in agent and NetScaler built-in agent to NetScaler Console |
Note:
In NetScaler Console high-availability deployment, all communications from NetScaler Console use the primary node IP address.
Ports for external servers
The following table explains the required ports that must be open on external servers:
| Port | Type | Details | Direction of communication |
|---|---|---|---|
| 25 | TCP | To send SMTP notifications from NetScaler Console to users. | NetScaler Console to users. |
| 389/636 | TCP | Default port for authentication protocol. For communication between NetScaler Console and LDAP external authentication server. | NetScaler Console to LDAP external authentication server |
| 123 | UDP | Default NTP server port for synchronizing with multiple time sources. | NetScaler Console to NTP server |
| 1812 | RADIUS | Default port for authentication protocol. For communication between NetScaler Console and RADIUS external authentication server. | NetScaler Console to RADIUS external authentication server |
| 49 | TACACS | Default port for authentication protocol. For communication between NetScaler Console and TACACS external authentication server. | NetScaler Console to TACACS external authentication server |
Limitations
From NetScaler ADM 12.1 or later, the IPv6 format of IP addresses is supported. To configure IPv6, navigate to Settings > Administration, select IP Address, Second NIC, Host Name and Proxy Server under Network Configurations, enable IPv6, provide the IPv6 configuration details, and click Save.
The following table describes the supported and not supported list of features for IPv6:
| IPv6 supported features | IPv6 not supported features |
|---|---|
| Management access for NetScaler ADM GUI | High availability floating IP |
| Management access for NetScaler | Syslogs received from ADCs that support IPv6 |
| Registration and inventory | StyleBooks on ADCs that support IPv6 |
| Network dashboard | Analytics |
| SSL dashboard | Pooled licensing |
| Config jobs | |
| Config audit | |
| Network functions | |
| Network reporting | |
| Backup and restore of ADC instances | |
| SNMP events from NetScaler instances | |
In this article
- Requirements for NetScaler Console
- Requirements for NetScaler Console on-prem agent
- Minimum NetScaler version required for NetScaler Console features
- Requirements for NetScaler Console analytics
- Supported hypervisors
- Supported operating systems and Workspace versions
- Supported browsers
- Supported ports